In three to five sentences, describe why adding special effects are beneficial and what guidelines should be followed when using them.
Answers
Adding special effects can greatly enhance the visual appeal and impact of a video or film. They can make scenes more realistic, immersive, and engaging for viewers. However, it is important to use them wisely and in moderation, as overuse can make them distracting and take away from the overall storytelling. Additionally, special effects should be used in a way that complements and supports the narrative, rather than being added simply for the sake of visual spectacle.
Illusions or visual tricks are called special effects (also known as SFX, F/X, or simply FX) and are used in the theatre, film, television, video game, amusement park, and simulator industries to reenact imagined events in a story or virtual world.
Embellishments are customarily partitioned into the classes of mechanical impacts and optical impacts. The term "special effects" refers to mechanical effects, whereas the term "visual effects" refers to digital post-production and optical effects. This distinction between special effects and visual effects has grown as digital filmmaking has become more common.
Know more about Special Effects, here:
https://brainly.com/question/26414872
#SPJ11
Related Questions
Binary division 10101*101 with process please
Answers
Answer:
1101001
Explanation:
10101×101 = 10101+000000+1010100= 1101001
8.6 Code Practice: Question 2
Instructions
Copy and paste your code from the previous code practice. If you did not successfully complete it yet, please do that first before completing this code practice.
After your program has prompted the user for how many values should be in the array, generated those values, and printed the whole list, create and call a new function named sumArray. In this method, accept the array as the parameter. Inside, you should sum together all values and then return that value back to the original method call. Finally, print that sum of values.
Sample Run
How many values to add to the array:
8
[17, 99, 54, 88, 55, 47, 11, 97]
Total 468
Answers
Answer:
import random
def buildArray(a, n):
for i in range (n):
a.append(random.randint(10,99))
arr = []
def sumArray(a):
tot = 0
for i in range(len(a)):
tot = tot + a [i]
return tot
arr = []
numbers = int(input("How many values to add to the array:\n"))
buildArray(arr, numbers)
print(arr)
print("Total " + str(sumArray(arr)) )
Explanation:
The program is an illustration of lists
ListsLists are variables that are used to hold multiple values in one variable name
Python ProgramThe program in Python, where comments are used to explain each line is as follows:
#This gets the number of inputs to the array
n = int(input("How many values to add to the array: "))
#This initializes the sum to 0
sumArray = 0
#This initializes a list
myList = []
#This iterates through n
for i in range(n):
#This gets input for the list elements
num = int(input())
#This appends the input to the list
myList.Append(num)
#This calculates the sum
sumArray+=num
#This prints the list elements
print(myList)
#This prints the sum of the list elements
print("Total",sumArray)
Read more about lists at:
https://brainly.com/question/24941798
Write about Alarm System and evacuation protocol in detail
( WRITE BY USING COMPUTER PLEASE !!! )
Answers
Alarm systems and evacuation protocols play a vital role in ensuring the safety of individuals by promptly detecting hazards and facilitating organized evacuations during emergencies.
An alarm system is a mechanism that uses an alert to warn people of a potential danger. The most frequent use of an alarm system is to warn of a fire, but it may also be used for other purposes, such as notifying of a break-in or detecting dangerous gasses.
The system may be designed to detect the occurrence of an event or to provide an audible or visual signal when a predetermined threshold has been surpassed, such as when a sensor registers a certain level of heat or smoke. An evacuation protocol, on the other hand, is a sequence of procedures that are followed in the event of an emergency or catastrophe, such as a fire or gas leak. The goal of an evacuation protocol is to safely and efficiently evacuate individuals from a hazardous area and to provide them with the appropriate care and assistance.
The procedures in an evacuation protocol vary depending on the nature of the emergency, but the general process typically includes a warning signal, an assessment of the situation, and a plan to evacuate. For example, if a fire alarm system is activated, the evacuation protocol may involve sounding an alarm, alerting emergency personnel, and evacuating individuals to a designated safe area.
To know more about Alarm systems visit :
https://brainly.com/question/29834691
#SPJ11
11. after applying a regularization penalty in linear regression, you find that some of the coefficients of θn are zeroed out. which of the following penalties might have been used?
A. Lasso
B. Ridge
C. Any of the above
D. None of the above
Answers
When some of the coefficients of θn are zeroed out after applying a regularization penalty in linear regression, then the penalty that might have been used is Lasso (Option A).
Regularization is a method for adding a penalty term to the cost function to avoid overfitting by restricting the size of the coefficient estimate, which can lead to an increase in bias in exchange for a decrease in variance. There are two types of regularization: Lasso and Ridge.
Lasso regularization uses an L1 penalty, which introduces a sparsity constraint, allowing the coefficients to be zero. Ridge regularization uses an L2 penalty, which shrinks the coefficient estimates toward zero but doesn't force them to be exactly zero. So, when some of the coefficients of θn are zeroed out after applying a regularization penalty in linear regression, then the penalty that might have been used is Lasso. The correct answer is A. Lasso.
You can learn more about penalty at: brainly.com/question/32309074
#SPJ11
Sasha's new company has told her that she will be required to move at her own expense in two years. What should she consider before making her decision?
Answers
To make her decision, Sasha should consider cost of living, job market, quality of life, social network, and career advancement before moving for her new job.
What is the rationale for the above response?
Before deciding whether or not to move for her new job, Sasha should consider several key factors.
Firstly, she should research the cost of living in the area where she will be moving to, as well as job opportunities, salaries and stability of the job market. Secondly, she should consider the overall quality of life, including climate, recreational opportunities and community atmosphere.
Note as well that, Sasha should consider her current social network and the opportunity to build a new one in the area where she will be moving to. Finally, she should weigh the potential benefits and costs of the move in terms of her personal and professional goals to determine if it is the right decision for her.
Learn more about Decision Making at:
https://brainly.com/question/13244895
#SPJ1
which meaning does the abbreviation c/c represent?
Answers
The phrase "carbon copy" alludes to the message's recipient whose location appears after Cc: header.
What does CC stand for?Carbon copies: To let the recipients of a business letter know who else received it, a cc designation would be placed at the bottom of the letter, followed by the names of those who received carbon copies of the original. The term "cc" in emails refers to the additional recipients who received the message.
A typical email will have a "To" box, a "CC" field, and only a "BCC" section that allows you to enter email addresses. The abbreviation for carbon copy is CC. "Blind carbon copy" is what BCC stands for. The abbreviation BCC stands in blind carbon copy, while Cc stands for carbon copy. When copying someone's email, use Cc for copy them openly or Bcc to copy them secretly.
To learn more about carbon copy refer to :
brainly.com/question/11513369
#SPJ4
Explain why computer professionals are engaged in technical services
Answers
Answer: It's probably because they love computers and they know what they are doing. Also they can write specs for new computers.
Explanation: Hope this helps.
Complete the sentence.
A(n)
A. Accessibility document
B. User manual
C. Code library
D. Version control document keeps track of the version numbers of an app and what changes were made váth each
version
Answers
Answer: D Version control document
Explanation: right on cs
A version control document keeps track of the version numbers of an application and what changes were made in each version.
What is version control?Version control can be defined as a process through which changes to a document, file, application and software codes over time, are tracked, recorded and managed, especially for easy recall and modification of specific versions in the future.
In Computer technology, an example of a version control system that is commonly used by software developers across the world is Git.
Read more on version control here: https://brainly.com/question/22938019
#SPJ2
Please HELP
Which of the following is not a method of data management?
A- sorting
b- filtering
c- formula's
d- graphing
Answers
formula's, Data management does not involve formulas.
What is formula?
A formula is a statement that instructs the computer what mathematical operation to carry out on a given value. Formulas are most frequently used in spreadsheet software, like Microsoft Excel, when referring to computer programs.
What is Data Management?
Data management is the process of gathering, storing, and using data in a cost-effective, efficient, and secure manner. In order to make decisions and take actions that will benefit the organization as much as possible, data management aims to assist individuals, organizations, and connected things in optimizing the use of data within the constraints of policy and regulation. An effective data management strategy is more crucial than ever as businesses depend more on intangible assets to generate value.
To know more about Data Management, check out:
https://brainly.com/question/29310787
#SPJ1
Based on current and upcoming gaming technologies, what changes do you expect to see in the next generation of gaming consoles? If you were designing a future game console, what technical innovations would you incorporate? Include at least TWO concrete technological innovations or developments in your answer.
Answers
you are the network administrator for your organization. you have a reference computer that runs windows 10. you need to create and deploy an image of the windows 10 computer. you create an answer file named answer.xml. you have to make sure that the installation applies the answer file after you deploy the image. which command should you run before you capture the image?
Answers
The command to run before capturing the image is Sysprep.exe /generalize /oobe /unattend:answer.xml
You would make use of the Sysprep program. Whereby The generalized options prevent the inclusion of system-specific information in the image. The Sysprep/generalize command gets rid of unique data from your Windows installation so that you can safely use that image on another computer. The specialized and advanced technical configuation entry can be implemented the very next time users restart the Windows image.
Your question is incomplete, the possible question can be
You are the network administrator for your organization. You have a reference computer that runs Windows 10. You need to create and deploy an image of the Windows 10 computer. You create an answer file named answer.xml. You have to make sure the installation applies the answer file after you deploy the image.
Which command should you run before you capture the image?
A. ICD.exe /append answer.xml /check
B. ICD.exe /mount answer.xml /verify
C. Sysprep.exe /reboot /audit /unattend:answer.xml
D. Sysprep.exe /generalize /oobe /unattend:answer.xml
Learn more about the command used to run before you capture the image here:https://brainly.com/question/15072298
#SPJ4
Kelly is fond of pebbles, during summer, her favorite past-time is to cellect peblles of the same shape and size
Answers
The java code for the Kelly is fond of pebbles is given below.
What is the java code about?import java.util.Arrays;
public class PebbleBuckets {
public static int minBuckets(int numOfPebbles, int[] bucketSizes) {
// Sort the bucket sizes in ascending order
Arrays.sort(bucketSizes);
// Initialize the minimum number of buckets to the maximum integer value
int minBuckets = Integer.MAX_VALUE;
// Loop through the bucket sizes and find the minimum number of buckets needed
for (int i = 0; i < bucketSizes.length; i++) {
int numBuckets = 0;
int remainingPebbles = numOfPebbles;
// Count the number of buckets needed for each size
while (remainingPebbles > 0) {
remainingPebbles -= bucketSizes[i];
numBuckets++;
}
// Update the minimum number of buckets if needed
if (remainingPebbles == 0 && numBuckets < minBuckets) {
minBuckets = numBuckets;
}
}
// If the minimum number of buckets is still the maximum integer value, return -1
if (minBuckets == Integer.MAX_VALUE) {
return -1;
}
return minBuckets;
}
public static void main(String[] args) {
// Test the minBuckets function
int numOfPebbles = 5;
int[] bucketSizes = {3, 5};
int minBuckets = minBuckets(numOfPebbles, bucketSizes);
System.out.println("Minimum number of buckets: " + minBuckets);
}
}
Learn more about java code from
https://brainly.com/question/18554491
#SPJ1
See full question below
Write a java code for the following Kelly is fond of pebbles. During summer, her favorite past-time is to collect pebbles of same shape and size. To collect these pebbles, she has buckets of different sizes. Every bucket can hold a certain number of pebbles. Given the number of pebbles and a list of bucket sizes, determine the minimum number of buckets required to collect exactly the number of pebbles given, and no more. If there is no combination that covers exactly that number of pebbles, return -1. Example numOfPebbles = 5 bucketSizes = [3, 5] One bucket can cover exactly 5 pebbles, so the function should return 1.
Chose the devices you think you should use in order to…
Go to my friend’s house and watch some movies.
A. DVD
B.CD
C.Memory card
D. USB flash memory
Listen to music while I’m running..
A. DVD
B.CD
C.Memory card
D. USB flash memory
Save photos to my computer ..
A. DVD
B.CD
C.Memory card
D. USB flash memory
Answers
Answer:
I think it's B, D, C
Explanation:
Cd for movies
Usb for the phone music and
Memory card to be inserted into the computer
Answer:
USB flash memory is the answer of all these question.
Explanation:
USB flash memory is the answer of all these question because it is small in size so you can easily carry it anywhere in your pocket. Below is the photo of USB flash drive

explain two ways of searching information using a search engine.
Answers
answer:
navigational search queries · for example, “how to make cake?”
informational search · for example, “y-o-u-t-u-b-e” or “apple"
explanation:
navigational — these requests establish that the user wants to visit a specific site or find a certain vendorinformational — in these instances, the user is looking for certain informationWhen you install drives what type of connection can be used to connect SSD’s, HDD’s and Optical drive?
Answers
Answer:
Two drives: one being an SSD and one being an HDD
Explanation:
SSHD is a hybrid of the SSD and HDD. It has the capacity of a HHD and the speed close to that of a SSD. Frequently used software are stored in the SSD part for quick access and everything else is stored in the HDD.
Explanation:
write the algorithms for the problem How to post a letter ? you can put pictures for the steps
Answers
❖ Step 1: Start
❖ Step 2: Write a letter
❖ Step 3: Put in envelope
❖ Step 4: Paste stamp
❖ Step 5: Put it in the letter box
❖ Step 6: Stop
\(\frak{\fcolorbox{black}{pink}{Black Pink in your area$~$}}\) ~←(>▽<)ノ
Do you have to reinstall windows with a new motherboard.
Answers
Answer:
Explanation: one must reinstall Windows when they change the motherboard of their PC.
a lw is to load register $5 from location 0x0040000c in memory. register $10 contains 0x00400000. write the assembly language instruction:
Answers
Assembly-language enables programmers to write code that corresponds to the machine instructions that a given processor may execute.
What kinds of instructions can you write in assembly language?In an assembly language, program operations are defined by one of three types of instruction statements: Opcode abbreviations. Definitions of data. assembly resolutions.
What are the four fundamental components of instruction in assembly language?Label, mnemonic, operand, and comment are its four component parts; not all of these are found in every line. The first component, in this case LOOP, is a label—a term the programmer created to designate this place in the program. The value of the address at which this instruction is stored will be used to set it.
To know more about Assembly-language visit:-
https://brainly.com/question/14728681
#SPJ4
I use the wrap text feature in Excel daily. What is the difference in how this behaves or is used in Excel versus Word? Please explain in detail the differences and similarities.
Answers
The wrap text feature is an essential tool used to format text, particularly long texts or data within a cell in Microsoft Excel. In this question, we need to explain the difference between how wrap text behaves in Microsoft Excel versus how it is used in Microsoft Word.
Wrap Text in Microsoft Excel: Wrap text in Excel is a formatting option that is used to adjust text or data within a cell. When the text entered exceeds the size of the cell, it can be hard to read, and this is where wrap text comes in handy. Wrap text in Excel automatically formats the data within the cell and adjusts the text size to fit the cell's width. If a cell contains too much data to fit in the column, the cell's text wraps to the next line within the same cell.
To wrap text in Excel, follow these simple steps:
Select the cell or range of cells containing the text that needs wrapping. Right-click on the selected cell and click Format Cells. In the Format Cells dialog box, click on the Alignment tab. Click the Wrap text option and then click OK.Wrap Text in Microsoft Word: In Microsoft Word, the Wrap Text feature is used to format text around images and graphics. It is used to change the way the text flows around the image, allowing users to position images and graphics in the document. Wrap Text in Microsoft Word does not adjust the font size of the text to fit the width of the cell like in Excel.
To wrap text in Microsoft Word, follow these simple steps:
Insert the image in the document. Select the image and go to the Picture Format tab. Click on Wrap Text, and you can choose how you want the text to wrap around the image.The main difference between the use of Wrap Text in Microsoft Excel and Microsoft Word is that Wrap Text in Excel is used to format long data and adjust text size to fit the width of the cell while Wrap Text in Microsoft Word is used to format text around images and graphics.
To learn more about wrap text, visit:
https://brainly.com/question/27962229
#SPJ11
What is the initial condition are to be applied for a forced
vibrational system?
Answers
The initial conditions to be applied for a forced vibrational system typically consist of the initial displacement, initial velocity, and initial acceleration of the system. These initial conditions describe the starting state of the system at time t=0.
The initial displacement refers to the distance or position of the system from its equilibrium position at the beginning of the forced vibration. It represents the initial deformation or displacement of the system from its rest position.
The initial velocity represents the rate at which the system is moving away from or towards its equilibrium position at t=0. It determines the initial speed and direction of the system's motion.
The initial acceleration represents the rate at which the velocity of the system is changing at t=0. It affects the system's response to the external force and determines how quickly the system accelerates or decelerates.
By specifying these initial conditions, we can determine the behavior and response of the forced vibrational system over time. They serve as the starting point for solving the equations of motion and analyzing the system's dynamics and transient response.
In conclusion, the initial conditions for a forced vibrational system include the initial displacement, initial velocity, and initial acceleration, which define the system's starting state at t=0 and are essential for analyzing its response to external forces.
To know more about Initial Velocity visit-
brainly.com/question/29153562
#SPJ11
what is the correct binary form of the decimal ip address 192.168.1.1?
Answers
In binary form, it is expressed as 11000000.10101000. 00000001.00000001 and in decimal form, as 192.168.1.1.
An example of a class C private address is 192.168.1.1. Sunnet's standard mask is therefore 255.255.255.0. The gateway is located at the network's perimeter. When a data packet departs our network, that is the last place it meets before leaving the network. When a packet enters our network, here is the first place it encounters.
The IP address of a router serves as the default gateway (of Ethernet port). Depending on the needs and the necessity of the network, this might be changed. Understanding how to convert numbers from decimal to binary is crucial for understanding IP addressing and Subnetting. One of today's fundamental networking functions is IP addressing.
Any competent network engineer must be able to assign IP addresses and identify networks or hosts using subnets. It is easier to complete more difficult jobs when one has a thorough understanding of the fundamentals. Here are the methods for memorizing-free binary conversion of a decimal IP address.
To know more about decimal click on the link:
https://brainly.com/question/548650
#SPJ4
Hello guys where's bios chip in this motherboard help me

Answers
Answer:
Explanation:
Hey there!
Do you see the lower corner?
on the right beside the anti surge thingy
its rectangular, its also black from the center its here
a new technician sees the following syntax in a batch file: \\server1\accounting. he is unfamiliar with the syntax and asks you what it is called. what do you tell him?
Answers
The syntax that the new technician sees in the batch file: \\server1\accounting is called a UNC path.
UNC PathUniversal Naming Convention (UNC) Path is a naming convention used to identify network resources, such as servers, shared printers, and shared files. UNC paths provide a way to access shared folders and files on a network-based computer or server by using a common syntax.UNC path comprises two backslashes that precede the network name or IP address, followed by the name of the shared resource or folder.In this case, \\server1\accounting is a UNC path that represents the accounting shared folder on server1.
To learn more about syntax visit: https://brainly.com/question/831003
#SPJ11
Which of these is NOT a way that technology can solve problems?
Group of answer choices
sorting quickly through data
storing data so that it is easily accessible
making value judgments
automating repetitive tasks
Answers
Answer:
making value judgements
Explanation:
honestly this is just a guess if there is any others pick that but this is just what I'm thinking
Greg is looking around an art exhibition displaying American art from different ages. He spots the works of some famous artists. Match the
artists to the era of which they belong.
Benjamin West
Georgia O'Keeffe
Native Americans
Thomas Crawford
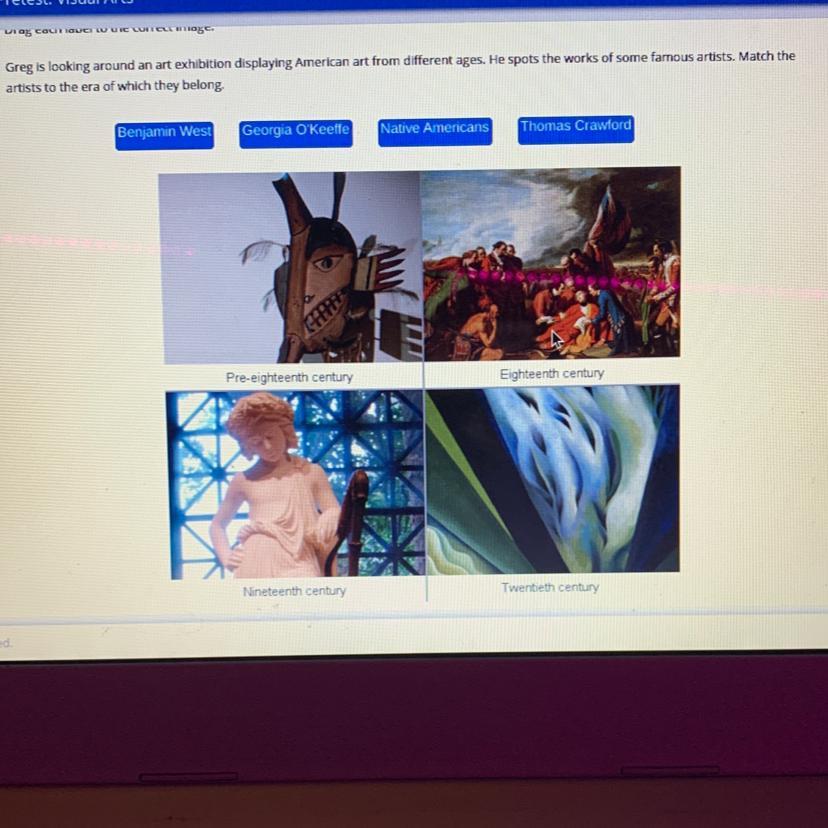
Answers
Answer:
Benjamin west is 18th century
Thomas Crawford is 19th century
Native Americans is pre-18th century
Georgia O'Keeffe is 20th century
Explanation:
At the time of creation of cui material the authorized holder is responsible for?
Answers
If so, the authorized holder is responsible for applying CUI markings and dissemination instructions accordingly.
At the time of creation of cui material the authorized holder is responsible for?The thing which the authorized holder is responsible for determining at the time of creation of CUI material is:
Whether information in a document or material falls into a CUI category.According to the given question, we are asked to state the thing which the authorized holder is responsible for determining at the time of creation of CUI material.
As a result of this, we can see that there is an agency which is in charge of managing the CUI material in the federal government and this is called the National Archives and Records Administration (NARA) as they manage the Controlled Unclassified Information (CUI) and the authorized holder determines whether the information in a document falls under the CUI category.
To learn more about cui material refers to;
https://brainly.com/question/25780301
#SPJ4
What is the difference between the complete scan and the resident shield?
Answers
A complete scan and resident shield are two types of antivirus scans. The main difference between them is that a complete scan checks all files and folders on your computer, while a resident shield scans only files as they are accessed or modified.
A complete scan is a thorough antivirus scan that checks all files and folders on your computer's hard drive. This scan examines all of your system's files to detect viruses, malware, and other threats that may be present. A complete scan is time-consuming and can take several hours to complete, depending on the size of your hard drive.
As you work on your computer and open or modify files, the resident shield scans the files for malicious code and alerts you if any are found. This type of scan is very useful because it provides immediate protection against threats that may try to infect your computer while you're working on it.
To know more about antivirus visit:
https://brainly.com/question/29356216
#SPJ11
Which cloud storage architecture enchances the opportunity for data policy enforcement such as data loss prevention?
Answers
Answer:
DRM or DLP.
Explanation:
Play a role of an IT employee and explain how you will solve
business problems and provide decision support for a school by
establishing a database.
Write it clearly. thank you!
Answers
As an IT employee, I would solve business problems and provide decision support for the school by establishing a database. A database would help in organizing and managing various school-related data effectively, enabling informed decision-making and streamlining processes.
To establish a database for the school, I would follow the following steps:
Requirement Gathering: I would meet with key stakeholders, such as school administrators, teachers, and staff, to understand their data management needs and identify the specific problems they are facing. This could include areas such as student records, attendance, academic performance, curriculum management, financial data, and more.Database Design: Based on the requirements gathered, I would design the database schema, which includes defining the tables, fields, and relationships between them. This step involves careful consideration of data normalization techniques to ensure efficient data storage and retrieval.Database Implementation: Using appropriate database management software, such as MySQL, Oracle, or Microsoft SQL Server, I would create the database and tables as per the design. I would also establish necessary security measures, such as user access controls and data encryption, to protect sensitive information.Data Migration and Integration: If the school already has existing data in different formats (e.g., spreadsheets, paper-based records), I would develop a strategy to migrate and integrate that data into the new database. This process may involve data cleansing, transformation, and validation to ensure accuracy and consistency.Application Development: Depending on the school's requirements, I may develop customized software applications or use existing solutions to interact with the database. These applications could include student information systems, attendance trackers, gradebook systems, or financial management tools. Integration with other existing systems, such as learning management systems or communication platforms, may also be considered.Training and Support: I would provide training sessions and documentation to school staff, ensuring they understand how to use the database effectively and efficiently. Ongoing support and maintenance would be provided to address any issues or evolving needs that may arise.By establishing a database for the school, we can centralize and organize various data sets, enabling efficient data management and decision-making processes. The database would improve data accuracy, accessibility, and integrity, leading to better insights and informed decision support for school administrators, teachers, and staff. It would streamline administrative tasks, enhance collaboration among different departments, and ultimately contribute to an improved overall school management system.
Learn more about database visit:
https://brainly.com/question/29412324
#SPJ11
why is it important to be part of a team in times you fail and in times you succeed?
Answers
Answer:
well you will feel better when you lose and have a better time winning with friends?
Explanation: