In some database programs, a data file is referred to as a(n) ______. group of answer choices
Answers
In some database programs, a data file is referred to as a **table**. A table is a fundamental concept in database management systems (DBMS) that represents a structured collection of data organized in rows and columns. It serves as a container for storing related data entities or records.
A table consists of columns, also known as fields or attributes, which define the different types of data that can be stored. Each row in the table represents a specific instance or record that holds values for each column. These values correspond to the data associated with the record.
Tables provide a structured way to organize and store data, allowing for efficient data retrieval, manipulation, and querying. They offer a logical representation of real-world entities, such as customers, products, orders, or employees, and their relationships.
By defining the columns and their data types, a table specifies the structure and constraints of the data it holds. It provides a consistent and standardized format for storing information, enabling data integrity and facilitating data analysis and reporting.
In summary, in the context of database programs, a data file is commonly referred to as a table, which serves as a structured container for storing related data entities or records. Tables form the backbone of a database, enabling efficient data organization and manipulation.
Learn more about database programs here:
https://brainly.com/question/32028338
#SPJ11
Related Questions
ethics are the standard or guidelines that help people determine what is right or wrong.
Answers
Ethics are the standards or guidelines that help people determine what is right or wrong. These standards apply to people, groups, and professions in the determination of what is considered acceptable behavior or conduct.
Ethics provide the main answer for questions of what is right and wrong. Ethics is a system of moral principles and values that help people make decisions and judgements in a variety of situations. It is a tool used to promote and encourage responsible behavior and conduct that is acceptable to society at large .Ethics is a central component of many professions and industries.
These guidelines help ensure that people act in an ethical and responsible manner, especially in cases where their actions may have far-reaching or significant consequences. For example, medical professionals must abide by ethical guidelines in order to ensure the safety and well-being of their patients .Ethics are often used in situations where there is no clear-cut answer or solution to a problem.
To know more about ethics visit:
https://brainly.com/question/33635997
#SPJ11
describe the process of stp from implementation to convergence.
Answers
Spanning Tree Protocol (STP) is a networking protocol that was created to prevent network loops in a Layer 2 switched network. STP helps in controlling the flood of traffic in a switched network by organizing the network topology. In this regard, the process of STP from implementation to convergence involves a series of steps as described below:
Step 1: STP Implementation
The first step in the process of STP implementation is to enable STP on all switches in the network. This ensures that all switches can participate in the STP process. After enabling STP on all switches, the switches must then be configured with a unique Bridge ID.
Step 2: Root Bridge Election
The next step is to elect a Root Bridge. The Root Bridge is the most important bridge in the STP topology as it provides the basis for the entire network's logical topology. To elect the Root Bridge, the switches compare their Bridge IDs, with the switch with the lowest Bridge ID being elected as the Root Bridge.
Step 3: Calculating Path Costs
The next step is to calculate the path costs from each switch to the Root Bridge. Path costs are calculated by adding the cost of each link between a switch and the Root Bridge.
Step 4: Determining the STP Topology
Using the Root Bridge and the path costs, STP then determines the topology of the network. STP calculates the shortest path from each switch to the Root Bridge, and blocks any redundant links.
Step 5: STP Convergence
After STP has determined the topology of the network, it then begins to converge. During convergence, switches change their port states until all ports are either in the forwarding or blocking state.
In conclusion, STP is an essential protocol for maintaining a stable and efficient network. By following the above process, STP helps prevent network loops and ensures that traffic flows efficiently throughout the network.
To know more about maintaining visit:
https://brainly.com/question/28341570
#SPJ11
How do you send a file to someone in an email? (Choose all that apply). A. Select Send File and choose the file you need. B. Select the paperclip icon and choose the file you need. C. Open the file and then select Send in your email. D. Select Attach and choose the file you need.
Answers
Answer:
C. Open the file and then select Send in your email.
D. Select Attach and choose the file you need.
Explanation:
Communication can be defined as a process which typically involves the transfer of information from one person (sender) to another (recipient), through the use of semiotics, symbols and signs that are mutually understood by both parties.
One of the most widely used communication channel or medium around the world is an e-mail (electronic mail).
An e-mail is an acronym for electronic mail and it is a software application or program designed to let users send and receive texts and multimedia messages over the internet.
A file can be defined as a computer resource that avails end users the ability to store or record data as a single unit on a computer storage device.
The following documents or files such as soft copy attachments, web links and web pages may be sent from one user to another through the use of an email.
On a related note, some of the methods used for sending a file to someone in an email are;
I. Open the file and then select Send in your email.
II. Select Attach and choose the file you need.
which of the following information technology career fields generally requires the lowest level of education for an entry level position?
Answers
Answer:
C
Explanation:
does trend in computing important for organization management?
Answers
Answer:
yes it is...................
how can we protect ourselves from exploits
Answers
Answer:Stay up-to-date. Do you regularly update your operating system and all the various applications you have installed? ...
Upgrade your software. In some cases, a software application becomes so old and unwieldy the software maker stops supporting it ( abandonware ), which means any additional bugs that are discovered will not be fixed. ...
Stay safe online. ...
Use it or lose it. ...
Install authorized apps. ...
Explanation:
what are the functions of online gaming communities?
Answers
Answer:
As a high-quality communication system, online games provide a virtual world where gamers communicate with each other by using rich interactive multimedia. This would facilitate communication among online gamers and enhance the development and maintenance of interpersonal relationships.
An end-user has reported that a legitimate sender sent an unexpected email stating the user needed to urgently update the password account information to a vendor website. Once the user clicked on the URL in the email, the user was taken to a landing page to update the user's credentials. The user entered the credentials, despite noticing the URL was slightly misspelled. What happened in this situation
Answers
Group of answer choices.
A) The attacker has sniffed the user's packets on the user's local network and has captured the user's credentials in plain text.
B) The user is a victim of a pharming attack by using social engineering to trick the user into clicking a link that redirected their traffic to a spoof website.
C) The user is the victim of an impersonation attack, where the attacker used intimidation by coaxing the target and engaging with them by putting them at ease.
D) The user is a victim of a phishing scam, and the attacker spoofed or compromised the sender's email address and spoofed the website.
Answer:
D) The user is a victim of a phishing scam, and the attacker spoofed or compromised the sender's email address and spoofed the website.
Explanation:
Social engineering can be defined as an art of manipulating people, especially the vulnerable to divulge confidential information or performing actions that compromises their security.
Basically, it is a manipulative strategy or technique that involves the use of deceptive and malicious activities on unsuspecting victims in order to gain unauthorized access to their confidential or private information for fraud-related purposes. Some examples of social engineering attacks include quid pro quo, spear phishing, baiting, tailgating, water-holing, vishing, pretexting, phishing, etc.
Phishing is an attempt to obtain sensitive information such as usernames, passwords and credit card details or bank account details by disguising oneself as a trustworthy entity in an electronic communication usually over the internet.
Furthermore, phishing is a type of fraudulent or social engineering attack used to lure unsuspecting individuals to click on a link that looks like that of a genuine website and then taken to a fraudulent web site which asks for personal information.
This ultimately implies that, the user in this scenario is a victim of a phishing scam, and the attacker spoofed or compromised the sender's email address and spoofed the website to make it look like a credible, authentic and original one.
Answer:
D) The user is a victim of a phishing scam, and the attacker spoofed or compromised the sender's email address and spoofed the website.
Project: Design and Development Research Project
a team at work
A team (Imagery supplied by RicardoImagen/iStock via Getty)
Your Task
Your teacher may ask you to work in groups. Check with your teacher to see if this is required.
Choose a topic from the unit.
Identify a problem or issue to research.
Write a question (or questions) to be answered by your research.
Find at least four sources; these can be a journal article, a website from a reputable organization, an encyclopedia, a newspaper, or a documentary. When in doubt, ask your teacher.
Unacceptable sources include Wikipedia, an individual’s blog, and social media, except as examples not counted as sources.
Create a document using Word (or a similar word-processing application) as described below.
Your Word Document Requirements
Part 1: Name
Your name
Names of your partner(s) (Include the names of people in your group if this is a group project.)
Part 2: Title
Part 3: Questions to Answer
Part 4: Introduction
A paragraph that introduces your topic and the question(s) to be answered
Part 5: Exposition
An explanation of how you answered the question(s); give credit to your sources, whether using direct quotes or not
Part 6: Conclusion
A paragraph summarizing your analysis
Part 7: Bibliography
Part 8: Partner Participation (only included for those working in groups)
Describe the role and responsibilities of each member of the group.
What to Submit
You will submit the Word document described above. You can use this rubric to evaluate your project before you submit it.
Answers
The correct steps which are used to make a research are as follows:
Choose a topicFind out what problem needs to be fixed about the topicWrite your research questionsMake use of reputable sourcesWrite out your conclusionsWhat is a Research?This refers to the systematic study of a particular thing or phenomena to find out why it occurs and why it occurs the way it does and the frequency of occurrence.
With this in mind, we can see that making a research requires meticulous steps and some sources for research should not be considered because they are not reputable and this can include; individual blogs, social media, etc.
Read more about research here:
https://brainly.com/question/968894
Answer:
sorry i know this is late, but hopefully it will help someone else!
have a lovely day <3
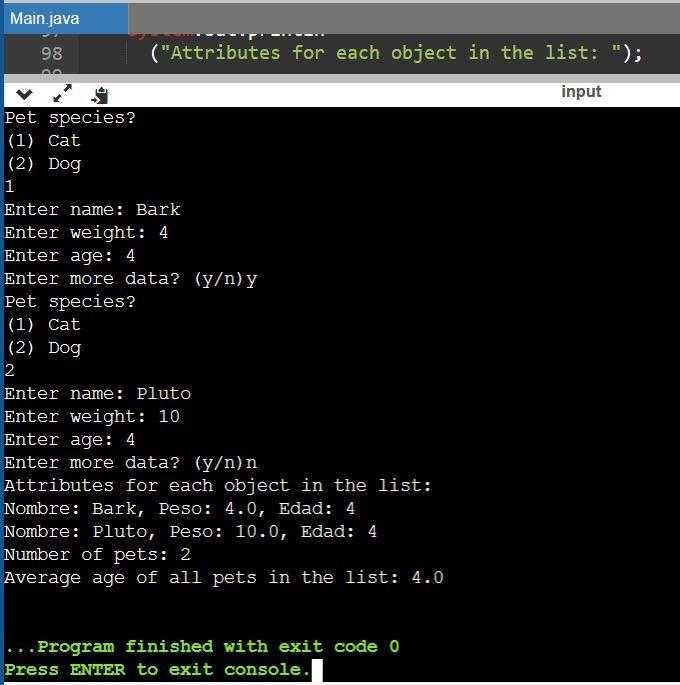
In an earlier assignment you modeled an inheritance hierarchy for dog and cat pets. You can reuse the code for that hierarchy in this assignment. Write a program that prompts the user to enter data (name, weight, age) for several Dog and Cat objects and stores the objects in an array list. The program should display the attributes for each object in the list, and then calculate and display the average age of all pets in the list using a method as indicated below:
public static double calculateAverage( ArrayList list )
{
... provide missing code ...
}
previous code
chihuahua
public class Chihuahua extends Dog
{
public void bark()
{
System.out.println("Bow wow");
}
}
dog
public class Dog
{
private String name;
private double weight;
private int age;
public String getname(String n)
{
name = n;
return n;
}
public double getweight(double w)
{
weight = w;
return w;
}
public int getage(int a)
{
age = a;
return a;
}
public void bark()
{
}
}
import java.util.Scanner;
public class DogCatTest
{
public static void main( String [] args)
{
Scanner scan = new Scanner(System.in);
System.out.println("Enter name");
String name = scan.nextLine();
System.out.println("Enter weight");
double weight = scan.nextDouble();
System.out.println("Enter age");
int age = scan.nextInt();
Dog [] dogCollection = { new Chihuahua(), new GoldenRetriever()};
for( int i = 0; i < dogCollection.length; i++ )
dogCollection[ i ].getname(name);
System.out.println(name);
for( int i = 0; i < dogCollection.length; i++ )
dogCollection[ i ].getweight(weight);
System.out.println(weight);
for( int i = 0; i < dogCollection.length; i++ )
dogCollection[ i ].getage(age);
System.out.println(age);
for( int i = 0; i < dogCollection.length; i++ )
dogCollection[ i ].bark();
System.out.println("Enter name");
String cname = scan.nextLine();
System.out.println("Enter weight");
double cweight = scan.nextDouble();
System.out.println("Enter age");
int cage = scan.nextInt();
Cat1 [] catCollection = { new SiameseCat(), new SiberianCat() };
for( int i = 0; i < catCollection.length; i++ )
catCollection[ i ].getname(cname);
System.out.println(cname);
for( int i = 0; i < catCollection.length; i++ )
catCollection[ i ].getweight(cweight);
System.out.println(cweight);
for( int i = 0; i < catCollection.length; i++ )
catCollection[ i ].getage(cage);
System.out.println(cage);
for( int i = 0; i < catCollection.length; i++ )
catCollection[ i ].meow();
}
}
public class GoldenRetriever extends Dog
{
public void bark()
{
System.out.println("Bow wow");
}
}
public class SiameseCat extends Cat1
{
public void meow()
{
System.out.println("Meow");
}
}
public class SiberianCat extends Cat1
{
public void meow()
{
System.out.println("Meow");
}
}
public class Cat1
{
private String name;
private double weight;
private int age;
public String getname(String n)
{
name = n;
return n;
}
public double getweight(double w)
{
weight = w;
return w;
}
public int getage(int a)
{
age = a;
return a;
}
public void meow()
{
}
}
Answers
Java program that shows the use of inheritance hierarchy, the code reuses the attributes of the class objects.
Importance of applying inheritance:In this case of pets (dogs and cats), applying inheritance allows a much shorter and more structured code. Also, reusable since we can add classes of other pets such as birds, rabbits, etc., all of them also belonging to the Pet superclass.
Reserved words in a java code that enforces inheritance:extendsprotectedSuperHere is an example:
Java codeimport java. io.*;
import java.util.ArrayList;
import java.io.BufferedReader;
public class Main
{
// ArrayList of Pet objetspublic static ArrayList < Pets > arraypets = new ArrayList < Pets > ();
public static void main (String args[]) throws IOException
{
BufferedReader data =
new BufferedReader (new InputStreamReader (System. in));
//Define variablesString aws;
String str;
double w;
String n;
int a;
double average;
do
{
//Data entry System.out.println ("Pet species? ");System.out.println ("(1) Cat ");
System.out.println ("(2) Dog ");
aws = data.readLine ();
System.out.print ("Enter name: ");
n = data.readLine ();
System.out.print ("Enter weight: ");
str = data.readLine ();
w = Double.valueOf (str);
System.out.print ("Enter age: ");
str = data.readLine ();
a = Integer.valueOf (str);
if (aws.equals ("1"))
{
Cat cat = new Cat (n, w, a);
arraypets.add (cat);
average = cat.averageAges (a);
}
else
{
Dog dog = new Dog (n, w, a);
arraypets.add (dog);
average = dog.averageAges (a);
}
System.out.print ("Enter more data? (y/n)");
aws = data.readLine ();
aws = aws.toLowerCase ();
}
while (!aws.equals ("n"));
//Calculate average of pets ageaverage = average / arraypets.size ();
average = Math.round (average * 100.0) / 100.0;
// OutputSystem.out.println ("Attributes for each object in the list: ");
for (Pets arraypet:arraypets)
{
System.out.println (arraypet);
}
System.out.println ("Number of pets: " + arraypets.size ());
System.out.println ("Average age of all pets in the list: " + average);
}
}
class Pets
{
protected String Name;
protected double Weight;
protected int Age;
public Pets ()
{
}
public Pets (String name, double weight, int age)
{
this.Name = name;
this.Weight = weight;
this.Age = age;
}
//Returning values formatted by tostring methodpublic String toString ()
{
return "Nombre: " + this.Name + ", Peso: " + this.Weight + ", Edad: " +
this.Age;
}
public void CalculateAverage ()
{
}
}
class Dog extends Pets
{
public Dog ()
{
super ();
}
public Dog (String name, double weight, int age)
{
super (name, weight, age);
}
//Adding the ages of the pets double averageAges (double a){
a += a;
return a;
}
}
class Cat extends Pets
{
public Cat ()
{
super ();
}
public Cat (String name, double weight, int age)
{
super (name, weight, age);
}
//Adding the ages of the petsdouble averageAges (double a)
{
a += a;
return a;
}
}
To learn more about inheritance hierarchy in java see: https://brainly.com/question/15700365
#SPJ4


virtual conections with science and technology. Explain , what are being revealed and what are being concealed
Answers
Some people believe that there is a spiritual connection between science and technology. They believe that science is a way of understanding the natural world, and that technology is a way of using that knowledge to improve the human condition. Others believe that science and technology are two separate disciplines, and that there is no spiritual connection between them.
What is technology?
Technology is the use of knowledge in a specific, repeatable manner to achieve useful aims. The outcome of such an effort may also be referred to as technology. Technology is widely used in daily life, as well as in the fields of science, industry, communication, and transportation. Society has changed as a result of numerous technological advances. The earliest known technology is indeed the stone tool, which was employed in the prehistoric past. This was followed by the use of fire, which helped fuel the Ice Age development of language and the expansion of the human brain. The Bronze Age wheel's development paved the way for longer journeys and the development of more sophisticated devices.
To learn more about technology
https://brainly.com/question/25110079
#SPJ13
Which of the themes is the best category for information about family and kinship?
1
2
3
4
Answers
Without the provided themes, it is not possible to determine the best category for information about family and kinship.
Which of the themes is the best category for information about family and kinship?Without any description or context provided for each of the themes, it is not possible to determine the best category for information about family and kinship among the options 1, 2, 3, and 4.
Each theme could potentially include aspects related to family and kinship, but without further information, it is impossible to make a definitive choice.
To determine the most suitable category, it would be helpful to have additional details or descriptions of the themes to understand their relevance to family and kinship topics.
Learn more about category
brainly.com/question/23029959
#SPJ11
PLATO ANSWERS PLS!!
Type the correct answer in the box. Spell all words correctly.
What should the timing of transition slides be per minute?
Maintain the flow of the presentation to
Reset
slides per minute.
Answers
The timing of transition slides per minute can vary depending on the content and pace of the presentation.
What is transition slide?A slide transition is the visual effect that happens as you switch from one slide to the next during a presentation. The pace, sound, and appearance of transition effects can all be adjusted.
Depending on the presentation's content and pacing, the number of transition slides every minute may change.
It is advised to keep the presentation's pace at roughly 1-2 minutes each slide as a general rule.
As a result, if your presentation lasts for 10 minutes, you should aim for 5–10 slides.
But, it's crucial to put the presentation's flow first and to refrain from speeding or dragging out slides in order to stick to a strict time limit. The timing of transition slides should ultimately be changed to better serve the presentation's content and purpose.
Thus, this is the timing of transition slides be per minute.
For more details regarding transition slide, visit:
https://brainly.com/question/19217934
#SPJ9
printers connected to the internet that provide printing services to others on the internet are called ________. group of answer choices plotters thermal printers dot-matrix printers cloud printers
Answers
Printers connected to the internet that provide printing services to others on the internet are called cloud printers.
A cloud printer is a printing device that is connected to the internet and can provide printing services to other people on the internet. These printers are integrated with cloud technology that allows users to send printing jobs from anywhere and at any time.
They can print documents, photos, or anything else from a remote location. It is known as cloud printers. Cloud printing enables users to access the printer from any place and at any time using a device like a phone, tablet, or laptop.
Users can also share the printer with others, allowing them to print directly to the printer via the internet.
Know more about cloud printers:
https://brainly.com/question/29218542
#SPJ4
According to forrester, what emerging technology is likely to improve service and create efficiencies by replacing many tasks that depend upon humans, such as customer service representatives, truck drivers, and taxi drivers?
Answers
According to forrester, the emerging technology that is likely to improve service and create efficiencies by replacing many tasks that depend upon humans, such as customer service representatives, truck drivers, and taxi drivers is Augmented and Virtual Reality.
What exactly is augmented reality?A computer-generated perception of the real world is enhanced through an interactive experience called augmented reality. Augmented reality uses software, apps, and hardware like AR glasses to superimpose digital material over actual settings and objects.
Therefore, AR enhances a real-world scene, while VR provides an immersive virtual experience. While just 25% of AR is virtual, VR is 75% virtual. Unlike AR, VR requires a headgear device. While AR users interact with the real world, VR users navigate through a wholly made-up environment.
Learn more about Augmented and Virtual Reality from
https://brainly.com/question/22621708
#SPJ1
To create a new document using a template, navigate to the _____ tab.
File
Home
New
Page Layout
Answers
Answer:
uhh...
Explanation:
i think it might be the new tab.
What is one way interpreted programming languages differ from compiled programming languages? (3 points)
Interpreted languages produce translated machine code that can be saved and run later, while compiled languages cannot be saved.
Interpreted languages translate all lines of code together and execute them all at once, while compiled languages translate one line of code at a time and then execute that line before moving on.
Programs written with interpreted languages are ready to be run, but programs written with compiled languages require interpreter software to be run.
Programs written with interpreted languages require the original source code, but programs written with compiled languages can be shared with others while keeping the source code private
Answers
Interpreted programming languages distinguish themselves from compiled programming languages in that they translate and execute code continuously.
Why is this so ?Interpreted progra ming languages distinguish themselves from compiled programming languages in that they translate and execute code continuously while the program runs.
Whereas compiled languages transform code into machine code that computers can execute directly.
In contrast to compiled languages, interpreted languages lack a distinct executable file and interpret the language itself during runtime. Interpreted programming offers increased flexibility and reduced debugging complexity, while compiled programs create more efficient code with improved speed.
Learn more about compiled programming languages at:
https://brainly.com/question/30498060
#SPJ1
Which of the following statements are true of software engineers? Check all of the boxes that apply. They are responsible for writing programming code. They are usually strong problem-solvers. They spend most of their work hours running experiments in a laboratory. They must hold advanced degrees in computer science.
Answers
Answer:
First two statements: yes. Last two: not so much.
But many of the better ones do have advanced degrees, but some don't.
The laboratory statement is silly; they sit behind a set of screens figuring out stuff and writing code.
It should be noted that statements are true about software engineers are;
They are responsible for writing programming code. They are usually strong problem-solvers.Software engineering can be regarded as branch of computer science which is responsible for the development as well as the building of computer softwares, these could be applications software or system software.
The engineers that carry out this process is referred to as software engineers and they are responsible for responsible for writing programming code.
We can conclude that software engineers are strong problem-solvers.
Learn more about software engineer at:https://brainly.com/question/25757629
1.Choose the best answer.:
a) Broadly, computers are of ................ purpose and ................ purpose
(i) specific, general (ii) specific, broad (iii) precise, broad (iv) None of them
b) .................. computers works on continuous signals
(i) Analog (ii) Digital (iii) PS/2 (iv) None of them
c) ................ computers are the largest and most expensive digital computers.
(i) Mainframe (ii) Mini (iii) Super (iv) Apple
d) .................. is the example of mainframe computer.
(i) CYBER 205 (ii) IBM 3081 (iii) VAX (iv) IBM 9375
e) Macintosh is the OS used in .................. computer.
(i) IBM (ii) mainframe (iii) super (iv) apple
f) .............. was mainframe computer brought first time to process census data in Nepal.
i) IBM 1400 ii) IBM1401 iii) IBM1402
g) ……… computer are used in hospital for Ultra Sound.
i) Analog ii) Digital iii)Laptop iv) Hybrid
h) Nowadays, most powerful super commuter is Sunway taihulight from .......................
i) India ii) Germany iii) China iv) Nepal
Answers
Answer:
specific, generaldigitalminiCYBER 205IBMIBM1401digitalGermanypls help
Question 2 (1 point)
True or false: when you use someone's copyrighted work in something you are
selling, you only have to cite them.
Answers
The given statement of copyrighted work is false.
What do you mean by copyright?
A copyright is a type of intellectual property that grants the owner the exclusive right to copy, distribute, adapt, display, and perform a creative work for a specific period of time. The creative work could be literary, artistic, educational, or musical in nature. The purpose of copyright is to protect the original expression of an idea in the form of a creative work, not the idea itself. A copyright is subject to public interest limitations, such as the fair use doctrine in the United States.
When you use someone's copyrighted work in something you are selling, you must get their permission first.
To learn more about copyright
https://brainly.com/question/357686
#SPJ13
Choose the option that best matches the description given. The older term, social service, referred to advancing human welfare. The new term, meaning to provide for the needs of various people and groups, is ____.
A. social assistance
B.social welfare
C.social media
For everyone that doesn't wanna watch the ads, The answer is A, social assistance.
Answers
Answer:
Social Assistance
Explanation:
Provision and disbursement of intervention in other to palliate the suffering and want of an individual, group or community can be described as rendering social assistance. Assistance which also means helping people fulfill their needs could be offered by the government, non-governmental organizations or individuals personnels. Rendering social assistance could be in the form of cash or gift offerings, provision of food for the hungry, shelter for the homeless, medical interventions for the sick and catering for other touch points of the needy.
Answer:
Social Assistance
Explanation:
BIG POINTS! BIG POINTS! BIG POINTS!
Does someone know how to fix a A s u s computer that won't turn on. Computer is all the way charged. Here is some screenshots of how it looks. Can this be an easy way to fix it because I can't really take out a battery or use tools. Thanks!



Answers
Try and hold the power button for a little while, and if it doesn't turn on then you might have to contact customer support.
Answer:
take the bottom of take out the battery and putt it back in
Explanation:
The mathematical rule that Excel follows to perform calculations in a formula in the proper order is called the:
Answers
The mathematical rule that Excel follows to perform calculations in a formula in the proper order is called the order of operations"
Excel calculates according to the acronym PEMDAS, which stands for Parentheses, Exponents, Multiplication and Division, and Addition and Subtraction. This computation order can be changed by using parenthesis.
Using specified data in a particular order, a function is a preset formula that conducts calculations. Common functions that can be used to rapidly determine the sum, average, count, maximum value, and minimum value for a range of cells are included in all spreadsheet systems.
Thus, order of operations.
For more information about Excel, click here:
https://brainly.com/question/30911293
#SPJ4
Question #5
Multiple Choice
What is used within an HTML tag for additional information?
O attribute
O anchor
O hyperlink
metadata
Answers
Answer: Attribute
Explanation: Attribute is used in HTML tags for additional information. Correct on Edg 2021.
Answer: attribute
Edge '23
Question: 11
Which of the following rules is the least specific?
#info
p.info.important
.info
p.info
Answers
Answer:
The detail answer to this question is given in the explanation section.
The correct answer is .info
Explanation:
Let look as each statement
p.info.important
this is a specific because it says
go to important property which is inside info property which is inside P
.info is less specific
because it will go to .info No function is given whose property is this.
p.info
This is some what specific. As it says select .info property which is inside p
When inputting a formula into excel or other spreadsheet software, what components are required for the formula to function properly? lab flow
Answers
The components that are required for the formula to function properly are:
There should be a Closing parentheses for every opening form of parentheses.There should be an equal sign at the start of the formula.What is a spreadsheet software?A spreadsheet is known to be a kind of a computer program that is one that functions by helping to take in, display as well as alter data that are arranged in rows and columns.
Note that the Spreadsheets are said to be part of the most famous tools available for every personal computers.
Hence, The components that are required for the formula to function properly are:
There should be a Closing parentheses for every opening form of parentheses.There should be an equal sign at the start of the formula.Learn more about spreadsheet from
https://brainly.com/question/4965119
#SPJ1
Can somebody help me and make a code for this in PYTHON, please? I would be very thankful!
Find sum of the first n even numbers.
Without using formula (n*(n+1)).
Answers
Answer:
number = int(input())
x = 0
y = 0
for n in range(number):
if n % 2 == 0:
x += n
else:
y += n
print(x)
print(y)
which of the following are benefits of parallel and distributed computing? i. distributed computing improves the speed at which an individual computer executes a program ii. parallel computing scales more effectively than sequential computing iii. distributed computing allows larger problems to be solved quicker
Answers
By setting up these networked computers to collaborate on a problem, parallel or distributed computing can take advantage of them and speed up the process of finding solutions.
What is distributed and parallel computing?The basic purposes of parallel and distributed computing differ significantly from one another.
By splitting up a computational activity into smaller jobs and distributing them among various processors inside a single computer, parallel computing, also known as parallel processing, speeds up the process. On the other side, distributed computing makes advantage of a distributed system, like the internet, to expand the amount of computing power available and make it possible for larger, more sophisticated activities to be carried out across several workstations.
A type of computation known as parallel computing involves running several tasks or processes concurrently. Distributed computing, in contrast, is a form of computing in which the parts are spread across multiple networked systems and communicate with one another to coordinate their operations.
To know more about Parallel Computing, visit:
https://brainly.com/question/20769806
#SPJ4
in ICT what is the difference between Save and Save As
Answers
Choosing "Save As..." brings up a prompt to save your work as a file with a different name. For example, you might choose to save a document called "Paper - rev. 3" as "Paper - rev. 4". This way, you can save you file at different stages and keep multiple versions on your hard drive.
Choosing "Save" and then "Save As..." is also a good way to make a backup of your file. Just be sure to rename the file something new when you choose "Save As..." or you will overwrite the current saved version, just like choosing the "Save" command would do.
Answer:
Save updates the files that are already created.
Save as creates a new file or store the existing file in a new location.
Teens are more likely to access the news online or by watching the news on TV.
OA. True
OB. False