In a masm program I have to calculate an average grade of 4 tests, the array values are already declared so no inputs are needed. How do I do that without needing a loop since I’m not allowed to
Answers
\( \bf \red {Answer}\)
If you're not allowed to use a loop, one way to calculate the average grade of 4 tests is to add up all the values in the array and then divide by 4. Here's an example MASM program that does this:
```
.586
.model flat,stdcall
.stack 4096
ExitProcess PROTO,dwExitCode:DWORD
.data
tests DWORD 80, 90, 85, 95
numTests DWORD 4
average DWORD ?
.code
main PROC
; Calculate the sum of all test scores
mov eax, 0
add eax, tests[0]
add eax, tests[4]
add eax, tests[8]
add eax, tests[12]
; Divide sum by 4 to get average
mov ebx, numTests
cdq
idiv ebx
mov average, eax
; Display the average
mov eax, average
call DumpRegs ; Replace with your own code to display the average
; Exit the program
INVOKE ExitProcess,0
main ENDP
END main
```
The program declares an array `tests` with 4 values, a variable `numTests` with the number of tests (4), and a variable `average` to store the calculated average grade. It then calculates the sum of all test scores by adding up the values in the array using the `add` instruction. It divides the sum by 4 to get the average using the `idiv` instruction, which divides the double-word in `edx:eax` by the value in `ebx`, storing the quotient in `eax` and the remainder in `edx`. It stores the calculated average in the `average` variable and displays it using `DumpRegs`. Finally, it exits the program using the `ExitProcess` function.
Note that this program assumes that the array `tests` contains exactly 4 values. If you have a different number of values or if the number of values can vary, you will need to modify the program accordingly.
Related Questions
TEST 2
DESCRIPTION
This test case checks your HTML contains a red color style.
PASS?
x
MESSAGE
Ensure you are using red, #f00, #ff0000, or rgb(255, 0, 0) to style your element
red.
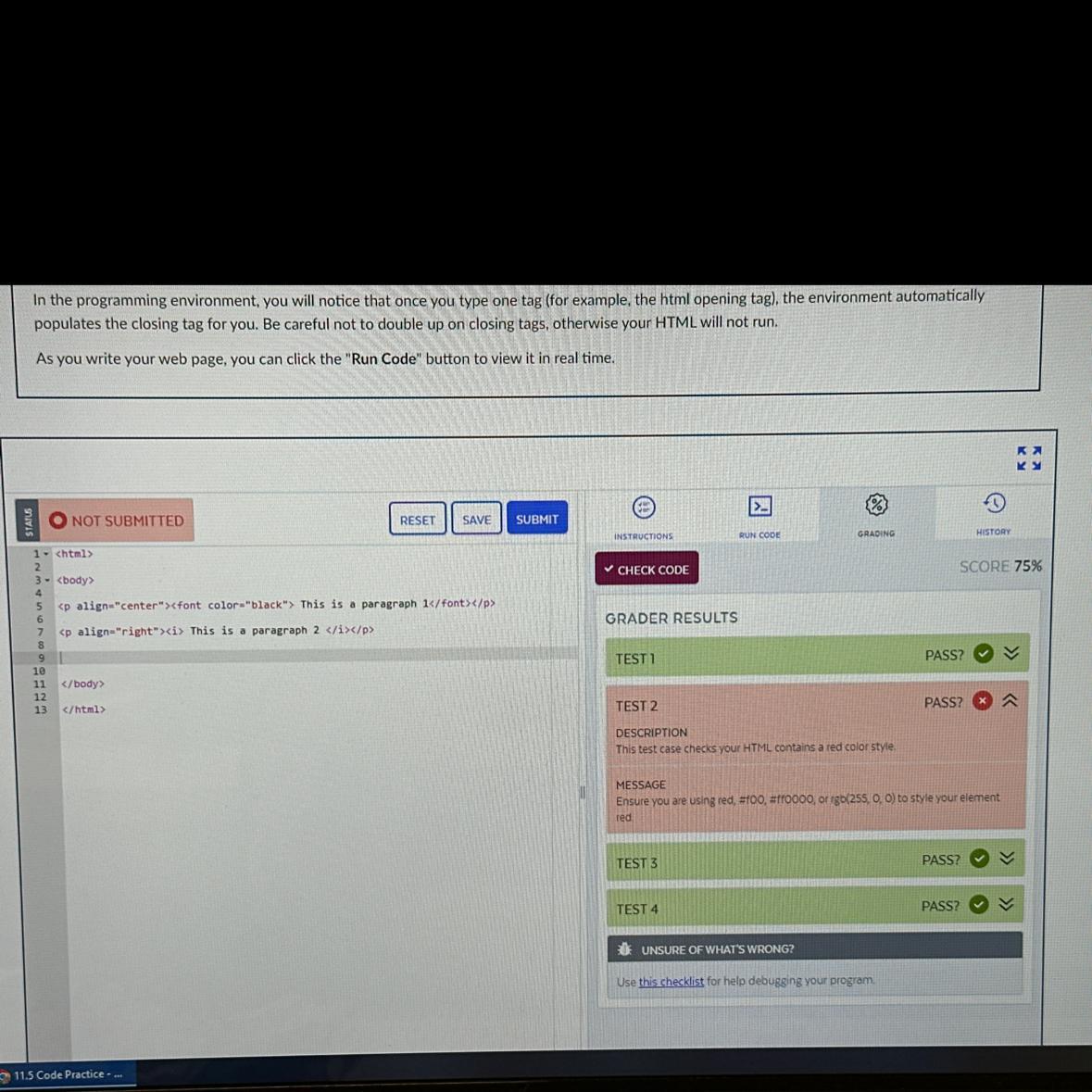
Answers
The test case has failed, as indicated by the 'x' in the 'PASS?' field. The message suggests that the HTML element should be styled using the color red, either through the color keyword 'red', or using one of the specified color codes (#f00, #ff0000) or the RGB value (rgb(255, 0, 0)).
What is the solution to the above problem?To fix the issue, the HTML element needs to be styled with one of the specified color codes or keywords. For example, to style a text element in red using the color keyword, the following CSS rule can be used:
color: red;
Alternatively, to use the hex color code #f00, the following rule can be used:
color: #f00;
Once the element has been styled correctly, the test case should be rerun to confirm that it passes.
Learn more about HTML on:
https://brainly.com/question/17959015
#SPJ1
will a printer with a usb 3.0 port work on a usb 2.0 port?
Answers
Answer:
Yes
Explanation:
USB 3.0 backwards is compatible—meaning it's designed to work with older USB versions including USB 2.0 and USB 1.1. ... So, if you plug a USB 3.0 flash drive into a USB 2.0 port, it would only run as quickly as the USB 2.0 port can transfer data and vice versa.
Creating a company culture for security design document
Answers
Use strict access control methods: Limit access to cardholder data to those who "need to know." Identify and authenticate system access. Limit physical access to cardholder information.
Networks should be monitored and tested on a regular basis. Maintain a policy for information security.
What is a healthy security culture?Security culture refers to a set of practises employed by activists, most notably contemporary anarchists, to avoid or mitigate the effects of police surveillance and harassment, as well as state control.
Your security policies, as well as how your security team communicates, enables, and enforces those policies, are frequently the most important drivers of your security culture. You will have a strong security culture if you have relatively simple, common sense policies communicated by an engaging and supportive security team.
What topics can be discussed, in what context, and with whom is governed by security culture. It forbids speaking with law enforcement, and certain media and locations are identified as security risks; the Internet, telephone and mail, people's homes and vehicles, and community meeting places are all assumed to have covert listening devices.
To learn more about security culture refer :
https://brainly.com/question/14293154
#SPJ1
in terms of computer what does mie mean
Answers
Answer:
Microsoft Internet explorer
Microsoft Internet Explorer.
Hope this answers your question! :)
para que se emplean los operando en una formula
Answers
Explanation:
what are you mobile-gws-wiz-serp now and black and son in a new medicine that is not the only way that we know you are in a
One suggested means of gaining eye contact before reversing is to:____.
Answers
Answer:
hit the vehicle horn
Explanation:
Remember, a driver reversing may easily go unnoticed by pedestrians as the driver may be coming from behind. Thus, a suggested means of gaining the eye contact of pedestrians before reversing is to hit the vehicle horn.
When designing, the first thing you need to consider is ________ you are designing for.
Answers
Answer:
The Constrains and Limitations or what is the problem you are trying to solve.
Explanation:
What part of a computer stores all the digital content on a computer?
Motherboard
Hard disk drive
SD card
CPU
Answers
Answer:
Its (B) Hard disk drive
Explanation:
Its B since in a computer the hard disk drive stores digital content like video's, word documents, photos, programs, etc.
Which types of online reading tools are available within the CloseReader? Check all that apply.
an interactive tool
an encyclopedia tool
a reference tool
a note-taking tool
a periodical tool
a text-to-speech tool
Answers
Answer:
A, C, D, & F
Explanation:
A - an interactive tool
C - a reference tool
D - a note taking tool
F - a text-to-speech tool
Got it right! Hope this helps.
What precautions should be taken to make a computer more secure?
Install anti-virus software
Turn on Windows automatic updates
Install a firewall
All of the above
None of the above
Answers
Answer:
D. All of the above.
Explanation:
To make a computer the most secure, it's recommended to install an anti-virus software, turn on Windows automatic updates, and install a firewall.
However, modern Windows computers come preinstall with Windows Defender which includes anti-virus and firewall and auto updates are ON by default. And E. None of the above can be correct.
However, it's asking for more secure, no other answer is more secure than D) All of the above.
Draw a third domain model class diagram that assumes a listing might have multiple owners. Additionally, a listing might be shared by two or more agents, and the percentage of the com- mission that cach agent gets from the sale can be different for cach agent
Answers
The required third domain model class diagram is attached accordingly.
What is the explanation of the diagram?The third domain model class diagram represents a system where a listing can have multiple owners and can be shared by multiple agents.
Each agent may receive a different percentage of the commission from the sale.
The key elements in this diagram include Author, Library, Book, Account, and Patron. This model allows for more flexibility in managing listings, ownership, and commission distribution within the system.
Learn more about domain model:
https://brainly.com/question/32249278
#SPJ1

You need to migrate an on-premises SQL Server database to Azure. The solution must include support for SQL Server Agent.
Which Azure SQL architecture should you recommend?
Select only one answer.
Azure SQL Database with the General Purpose service tier
Azure SQL Database with the Business Critical service tier
Azure SQL Managed Instance with the General Purpose service tier
Azure SQL Database with the Hyperscale service tier
Answers
The recommended architecture would be the Azure SQL Managed Instance with the General Purpose service tier.
Why this?Azure SQL Managed Instance is a fully managed SQL Server instance hosted in Azure that provides the compatibility and agility of an instance with the full control and management options of a traditional SQL Server on-premises deployment.
Azure SQL Managed Instance supports SQL Server Agent, which is important for scheduling and automating administrative tasks and maintenance operations.
This would be the best option for the needed migration of dB.
Read more about SQL server here:
https://brainly.com/question/5385952
#SPJ1
which statements describes the size of an atom
Answers
answer:
A statement that I always think about to understand the size of an atom. If you squish a person down to the size of an atom. It will make a black hole. and if you squish the whole Earth. down to the size of a jelly bean it will also make a black hole. This is just a approximation.
-----------------------
I use the scale to understand how small that is I am open to hear more principles if you were talking about math wise that would be glad to help.
if you have anymore questions I will try to answer your questions to what I know.
.
NG STOCK MARKET FRAUD
Assignment Directions
1. For this assignment, you will explore securities or stock market fraud. Title your assignment "Stock Fraud" and ther
list the case you analyzed.
2. Visit the SEC Web site. Select and read through one of the actions against Enron.
Submission Requirements
1. Write a summary of the facts of the case, your understanding of all security law violations, and any settlement or
payment made to the stock-holders or others. Explore her online sources to get additional information.
2. The paper must be between one and two pages in length, double spaced, and with one-inch margins. Be sure to
include a reference page.
e.owschools.com/owsoo/studentAssignment/index?eh-390541091 #section Tab you like to do next?
Answers
Stock market fraud refers to the fraudulent practice of manipulating stock prices and the market. The Nigerian Stock Market Fraud, also known as the N14 billion stock fraud, is one of the most notorious cases of stock market fraud that happened in Nigeria.
It occurred between 2001 and 2002 and involved some of Nigeria’s most influential figures, including stockbrokers, top executives of blue-chip companies, and bankers.The Nigerian Stock Market Fraud is one of the largest stock market scandals in the world. It was the result of a lack of regulation and oversight in the Nigerian stock market, which allowed fraudulent practices to thrive.
The Securities and Exchange Commission (SEC) is the regulatory body responsible for regulating the Nigerian Stock Exchange. However, the SEC was ineffective in preventing the fraud from occurring, and many of its officials were implicated in the scandal.The N14 billion stock fraud involved the manipulation of stock prices, insider trading, and market rigging.
The fraudsters would inflate the price of stocks artificially, then sell the stocks to unsuspecting investors at inflated prices. They would then use the proceeds from the sale of the stocks to buy more stocks, further inflating the prices.
The fraudsters also engaged in insider trading, where they would use insider information to make trades in the stock market. This gave them an unfair advantage over other investors and allowed them to make huge profits from their trades.
In conclusion, the Nigerian Stock Market Fraud was a result of a lack of regulation and oversight in the Nigerian stock market. The SEC was ineffective in preventing the fraud from occurring, and many of its officials were implicated in the scandal. The fraudsters engaged in the manipulation of stock prices, insider trading, and market rigging.
For more such questions on Stock market, click on:
https://brainly.com/question/690070
#SPJ8
it is important organic mineral that is found in the soil as ash
Answers
Answer:
Calcium is the most abundant element in wood ash and gives ash properties similar to agricultural lime. Ash is also a good source of potassium, phosphorus, and magnesium.
The code repeat 3 [forward 50 right 120] creates which shape?
a square
a circle
a pentagon
a triangle
Answers
Answer:
Triangle. D
Explanation:
I have no Idea, I was searching for the answer like most of you guys are doing. But my best guess is Triangle
Answer:
D. A triangle is your answer
Explanation:
The triangle is the only shape in this list that has 3 sides.
Answerer's Note:
Hope this helped :)
A group of 8 bits of information produces a ____.
Answers
Answer: Byte
Explanation: Eight bits constitute a byte.
Write a program that will read in a line of text and output the number of words in the line and the number of occurrences of each letter. Define a word to b any string of letters that is delimited at each end by either whitespace, a period, a comma, or the beginning or end of the line. You can assume that the input consists entirely of letters, whitespace, commas, and periods. When outputting the number of letters that occur in a line, be sure to count upper and lowercase versions of a letters as the same letter. Output the letters I alphabetical order and list only those letters that do occur in the input line.
Answers
Answer:
Here is the C++ program:
#include<iostream> //to use input output functions
#include <algorithm> //to use tolower() function
using namespace std; //to identify objects like cin cout
int main() { //start of main function
string text; // to hold text input
cout<<"Enter a line of text: "; // prompts user to enter a string
getline(cin,text); // reads the input string (text) from user
transform(text.begin(), text.end(), text.begin(), ::tolower); //converts the text into lower case
int letter[26] = {0}; //to hold the letters
int i; // used as a loop variable
int words=0; // to hold the count of words
for(i = 0; i< text.size();i++){ // iterates through the text
if(isalpha(text[i])&&(text[i+1]=='.'||text[i+1]==','||text[i+1]==' ')) //checks if the character at i-th index of text is a letter, and checks if i+1 index position of text is a period, comma or a space
words++; // adds 1 to the count of words
if(isalpha(text[i])) // if the character at the i-th index of text is a letter
letter[text[i]-'a']++; } // counts the occurrences of each letter
char j = text[text.size()-1]; // sets j to the last character of text
if(j != '.' && j!= ' '&& j!=',' &&j!= '\0') //if the last character is not a period or empty space or comma or end of lone
words++; //add 1 to the count of words
cout<<"Number of words: "<<words<<endl; //display the number of words in the text
for(i=0; i<26; i++) { //iterates 25 times
if(letter[i]>0) //if letter at index i is greater than 0
cout<<(char)('a'+i)<<" : "<<letter[i]<<endl; }} //displays each letters and its number of occurrences in the text
Explanation:
The program is explained in the attached document with an example.

Which core business etiquette is missing in Jane
Answers
Answer:
As the question does not provide any context about who Jane is and what she has done, I cannot provide a specific answer about which core business etiquette is missing in Jane. However, in general, some of the key core business etiquettes that are important to follow in a professional setting include:
Punctuality: Arriving on time for meetings and appointments is a sign of respect for others and their time.
Professionalism: Maintaining a professional demeanor, dressing appropriately, and using appropriate language and tone of voice are important in projecting a positive image and establishing credibility.
Communication: Effective communication skills such as active listening, clear speaking, and appropriate use of technology are essential for building relationships and achieving business goals.
Respect: Treating others with respect, including acknowledging their opinions and perspectives, is key to building positive relationships and fostering a positive work environment.
Business etiquette: Familiarity with and adherence to appropriate business etiquette, such as proper introductions, handshakes, and business card exchanges, can help establish a positive first impression and build relationships.
It is important to note that specific business etiquettes may vary depending on the cultural and social norms of the particular workplace or industry.
Most operating system have GUI as part of the system, which is the following best describes an operating system GUI
Answers
A Graphical User Interface (GUI) is the component of an operating system that allows users to communicate with the system using graphical elements. GUIs are generally used to give end-users an efficient and intuitive way to interact with a computer.
They provide an easy-to-use interface that allows users to manipulate various objects on the screen with the use of a mouse, keyboard, or other input device.The primary function of an operating system GUI is to make it easier for users to interact with the system.
This is done by providing visual feedback and a simple way to access various system functions. GUIs can be customized to suit the user's preferences, which means that they can be tailored to meet the specific needs of different users.Some of the key features of a GUI include the use of windows, icons, menus, and buttons.
Windows are used to display information and applications, while icons are used to represent various objects or applications on the screen. Menus and buttons are used to provide users with a way to access various system functions, such as saving a file or printing a document.
The use of a GUI has become a standard feature of most operating systems. This is because GUIs make it easier for users to interact with computers, and they provide an efficient and intuitive way to access various system functions.
For more such questions on Graphical User Interface, click on:
https://brainly.com/question/28901718
#SPJ8
For what specific purpose is the TM9400 P25 Mobile designed? What is the benefit of having a mobile communications device that allows for multiple modes of operation? What features make this mobile device durable enough for use in the field? In your opinion, what feature(s) of the P25 Mobile makes it ideal for police work?
Answers
Answer:
The specific purpose for the design of the TM9400 P25 Mobile is its use for efficient communication with other emergency-handling jurisdictions, especially in challenging environments.
When a law enforcement officer requires a dedicated mobile network for communication in emergency situations, the TM9400 P25 Mobile comes handy. It enables the officer to communicate under multiple operational modes from remote locations.
Encryption, together with its high quality audio and rugged build, ensures the durability of the TM9400 P25 Mobile.
The ability to communicate from many places, embedded into its interoperability, allows different law enforcement jurisdictions to seamlessly exchange intelligence. It also has remote network management features, which enhance its spectral efficiency and effectiveness.
Explanation:
The TM9400 P25 Mobile is a high-performance, flexible, and robust radio specially designed for emergency situations. It is widely used by law enforcement officers to communicate with others from remote locations.
Things are created to meet a purpose. The Tait TM9400 is known to be a very high-performing, flexible and robust mobile. It was set up for use in difficult environments while helping to give high quality audio and brilliant operation to the first responders all over the world.
The purpose of TM9400 P25 mobile designed is Challenging environment for effective communication use along with other emergency-handling cases.
It is often used by law enforcement officer because of emergency situation as it comes in handy. It helps the officer to communicate under a lot of operational modes from remote areas.
Learn more about Phones from
https://brainly.com/question/917245
Support technicians are expected to maintain documentation for each computer for which they are responsible. Create a document that a technician can use when installing Windows and performing all the chores mentioned in the module that are needed before and after the installation. The document needs a checklist of what to do before the installation and a checklist of what to do after the installation. It also needs a place to record decisions made during the installation, the applications and hardware devices installed, user accounts created, and any other important information that might be useful for future maintenance or troubleshooting. Don’t forget to include a way to identify the computer, the name of the technician doing the work, and when the work was done.
HELP!!
Answers
Answer: Computer Installation and Maintenance Documentation
Computer Identification:
- Computer Name:
- Serial Number:
- Model:
- Operating System:
Technician Information:
- Name:
- Date:
Before Installation Checklist:
- Backup important data
- Verify system requirements
- Check for BIOS updates
- Disconnect all peripherals and external devices
- Record hardware and software components
- Verify network connectivity
During Installation Checklist:
- Record decisions made during installation
- Select appropriate partition for installation
- Install necessary drivers
- Configure network settings
- Install Windows updates
After Installation Checklist:
- Install necessary software and applications
- Install necessary hardware devices
- Configure user accounts
- Install additional Windows updates
- Install antivirus software
Important Information:
- Hardware Components:
- Software Components:
- Network Configuration:
- Notes:
By signing below, I certify that I have completed the installation and maintenance checklist for the specified computer.
Technician Signature: ______________________________
Date: ____________________
1 2 3
4
5
Question #5
Dropdown
Suppose you are writing a program to sell tickets to a concert. The maximum number of tickets available is 400.
You created your own error type.
class Over400Error(Exception):
pass
What is the missing term in the code that handles that error?
if tickets > 400:
(Raise, Catch, detect) over400Error
Answers
Answer:
raise
Explanation:
You created your own error type class Over400Error(Exception) pass. The missing term in the code is raise. The correct option is a.
What are error codes?Error codes are the codes that are given when there is an error on the site. For example, 404 for the page is deleted or not present currently. A reserved nonstandard response status code for HTTP is 402, which means "Payment Required."
The requested material won't be available until the client makes a payment, according to this status code, which was developed to support digital cash or (micro)payment systems. To look for errors and correct them, two blocks are used: try and catch.
The catch block is used to catch such exceptions, and the try block is used to include code that may cause exceptions.
Therefore, the correct option is a. raise.
To learn more about error codes, refer to the link:
https://brainly.com/question/14927489
#SPJ5
HURRY GANG 100points!!!! How can you determine which hardware brands and models are the most reliable?
O read the information on the device's packaging
O find out how many of them are being sold per year
O read the manufacturer's website
O find customer reviews online
Answers
Answer: A, read the information on the device's packaging
Explanation:
The info in the packaging has to be accurate because it goes through tests and they cannot make up info on there. This means any info about the materials used is accurate.
Answer:
A. read the information on the device's packaging
Explanation:
Any information that's on packaging is made separately from the product manufacturers and needed to be checked and correct. If there is anything out of the ordinary on the device's packaging, then it is a good way to tell it's reliableness.
Write the code for the following problem.
Add a function to problem to display the last name and highest, last name and lowest and average exam score. Hint: for highest initialize a variable to 0 (high_var). If the array value is higher than the high_var then set high_var to the array value and set high_index to the position of the array. Proceed through the array until you get to the end. Do the same for finding the lowest using low_var set to 999 (higher than the highest value). For the average score, sum all the exam scores as you proceed through the loop. Use a for loop to go through each occurrence of the arrays. Note you can do all this with one for loop but if it makes more sense to you to use multiple for loops that is ok too.
Answers
Answer:
no
Explanation:
Assignment
Write the algorithm for solving the
f problems
1. Perimeter of a rectangle
2 Average of five (5) numbers
Answers
B.Add both lengths
C.Add both widths
D.sum up the value had on both length and width
How did the case Cubby v. CompuServe affect hosted digital content and the contracts that surround it?
Answers
Although CompuServe did post libellous content on its forums, the court determined that CompuServe was just a distributor of the content and not its publisher. As a distributor, CompuServe could only be held accountable for defamation if it had actual knowledge of the content's offensive character.
What is CompuServe ?As the first significant commercial online service provider and "the oldest of the Big Three information services," CompuServe was an American company. It dominated the industry in the 1980s and continued to exert significant impact into the mid-1990s.
CompuServe serves a crucial function as a member of the AOL Web Properties group by offering Internet connections to budget-conscious customers looking for both a dependable connection to the Internet and all the features and capabilities of an online service.
Thus, CompuServe could only be held accountable for defamation if it had actual knowledge of the content's offensive character.
To learn more about CompuServe, follow the link;
https://brainly.com/question/12096912
#SPJ1
A partition is the _____.
an application that makes an operating system easier to use, also known as a shell
section of a hard drive
the core of an operating system that controls the basic functions
software that can be downloaded from the Internet at no cost
Answers
Write a program that reads a file name from the keyboard. The file contains integers, each on a separate line. The first line of the input file will contain the number of integers in the file. You then create a corresponding array and fill the array with integers from the remaining lines. If the input file does not exist, give an appropriate error message and terminate the program. After integers are stored in an array, your program should call the following methods in order, output the intermediate results and count statistics on screen, and at end output even integers and odd integers to two different files called even.out and odd.out.
Implement the following methods in the program:
* public static int[] inputData() – This method will ask user for a file name, create an array, and store the integers read from the file into the array. If input file does not exist, give an appropriate error message and terminate the program.
* public static void printArray(int[] array) – This method will display the content of the array on screen. Print 10 integers per line and use printf method to align columns of numbers.
public static void reverseArray(int[] array) – This method will reverse the elements of the array so that the 1st element becomes the last, the 2nd element becomes the 2nd to the last, and so on.
* public static int sum(int[] array) – This method should compute and return the sum of all elements in the array.
* public static double average(int[] array) – This method should compute and return the average of all elements in the array.
* public static int max(int[] array) – This method should find and return the largest value in the array.
* public static int min(int[] array) – This method should find and return the smallest value in the array.
* public static void ascendingSelectionSortArray(int[] array) – This method will use Selection Sort to sort (in ascending order) the elements of the array so that the 1st element becomes the smallest, the 2nd element becomes the 2nd smallest, and so on.
* public static void desendingBubbleSortArray(int[] array) – This method will Bubble Sort to sort (in descending order) the elements of the array so that the 1st element becomes the largest, the 2nd element becomes the 2nd largest, and so on.
* public static void outputData(int[] array) – This method will create two output files called even.out and odd.out. Scan through the entire array, if an element is even, print it to even.out. If it is odd, print the element to odd.out.
Answers
Answer:
Explanation:
import java.util.Scanner;
import java.io.*;
public class ArrayProcessing
{
public static void main(String[] args) throws IOException
{
Scanner kb = new Scanner(System.in);
String fileName;
System.out.print("Enter input filename: ");
fileName = kb.nextLine();
File file = new File(fileName);
if(!file.exists())
{
System.out.println("There is no input file called : " + fileName);
return;
}
int[] numbers = inputData(file);
printArray(numbers);
}
public static int[] inputData(File file) throws IOException
{
Scanner inputFile = new Scanner(file);
int index = 1;
int size = inputFile.nextInt();
int[] values = new int[size];
while(inputFile.hasNextInt() && index < values.length)
{
values[index] = inputFile.nextInt();
index++;
}
inputFile.close();
return values;
}
public static void printArray(int[] array)
{
int count = 1;
for (int ndx = 1; ndx < array.length; ndx++)
{
System.out.printf("%5.f\n", array[ndx]);
count++;
}
if(count == 10)
System.out.println("");
}
}
Read the scenario and then answer the question using only the information provided.
A report titled “Dog Breeds” contains information about four breeds of dogs. Information about each breed is contained in a separate table. Which best describes how the report is organized?
The report is grouped and sorted.
The report is sorted only.
The report is grouped only.
Answers
Answer:
The report is grouped and sorted.
Answer:
C. the report is grouped only
Explanation: