If you’re using the default route, which action does the following URL call?
https:/localhost:5001/
a. The Index action of the Home controller
b. The List action of the Customer controller
c. The List action of the Home controller
d. The Index action of the Customer controller
Answers
If you're using the default route, the following URL call, "https:/localhost:5001/", would execute the Index action of the Home controller.
When using the default routing configuration in ASP.NET MVC or a similar framework, the URL pattern typically follows the convention of "{controller}/{action}/{id}". In this case, the URL doesn't specify a controller or an action, so the framework will use the default values. The default route configuration usually maps the root URL "/" to the Index action of the Home controller. Therefore, when accessing "https:/localhost:5001/", it would invoke the Index action of the Home controller, presenting the default page or the starting point of the application.
Know more about URL call here:
https://brainly.com/question/1084646
#SPJ11
Related Questions
codehs python 4.7.6 Powers of Two
it says I'm wrong because I need


Answers
\(\huge\fbox\orange{A} \huge\fbox\red{N}\huge\fbox\blue{S}\huge\fbox\green{W}\huge\fbox\gray{E}\huge\fbox\purple{R}\)
\(\huge\underline\mathtt\colorbox{cyan}{in attachment}\)

Following are the program to calculate the power of two:
Program Explanation:
Defining an integer variable "i" that hold an integer value.Defining a for loop that checks "i" value in between 20, inside this it calculates power of two.At the last use print method to print its value.Program:
i=1#holding integer value in i
for i in range(20):#defining a for that starts 1 to 20
i = 2 ** i#calculate power of 2 in i variable
print(i)#print value
Output:
Please find the attached file.
Learn more:
brainly.com/question/23170807

(Interest Calculator) The simple interest on a loan is calculated by the formula interest = principal * rate * days / 365;
The preceding formula assumes that rate is the annual interest rate, and therefore includes the division by 365 (days). Develop a program that will input principal, rate and days for several loans, and will calculate and display the simple interest for each loan, using the preceding formula. Here is a sample input/output dialog:
Enter loan principal (-1 to end): 1000.00 Enter interest rate: .1
Enter term of the loan in days: 365
The interest charge is $100.00
Enter loan principal (-1 to end): 1000.00 Enter interest rate: .08375
Enter term of the loan in days: 224
The interest charge is $51.40
Enter loan principal (-1 to end): -1
Answers
The program calculates and displays the simple interest in Python for several loans by taking input of principal, rate, and days, and using the formula interest = principal * rate * days / 365.
What is Python?
Python is a high-level, interpreted programming language that is widely used for various purposes such as web development, data analysis, machine learning, and artificial intelligence.
Here's the Python code to implement the interest calculator:
while True:
principal = float(input("Enter loan principal (-1 to end): "))
if principal == -1:
break
rate = float(input("Enter interest rate: "))
days = int(input("Enter term of the loan in days: "))
interest = principal * rate * days / 365
print("The interest charge is ${:.2f}".format(interest))
1) The program uses a while loop to repeatedly prompt the user for input until they enter -1 to end the program.
2) Inside the loop, the program uses input() to get the principal, interest rate, and loan term in days from the user, and stores them in variables.
3) The program then calculates the simple interest using the formula given in the problem statement: interest = principal * rate * days / 365.
4) Finally, the program uses print() to display the calculated interest to the user.
Sample output:
Enter loan principal (-1 to end): 1000.00
Enter interest rate: .1
Enter term of the loan in days: 365
The interest charge is $100.00
Enter loan principal (-1 to end): 1000.00
Enter interest rate: .08375
Enter term of the loan in days: 224
The interest charge is $51.40
Enter loan principal (-1 to end): -1
To know more about loans visit:
https://brainly.com/question/9471571
#SPJ1
the researcher was not part of the original database creation and the database was originally created to monitor public health and not for research purposes. the database is publicly available. the database does not include any identifiers. consent from the patients is not required because:
Answers
Consent from the patients is not required because the database is publicly available.
Protected health information :
Under US law, protected health information is any information about a person's health status, provision of health care, or payment for health care that is created or collected by a Covered Entity and can be linked to a specific individual. PHI is frequently sought out in datasets for de-identification rather than anonymization before researchers share the dataset publicly. To protect the privacy of research participants, researchers remove individually identifiable PHI from a dataset. Physical storage in the form of paper-based personal health records is the most common form of PHI (PHR). Electronic health records, wearable technology, and mobile applications are examples of PHI. In recent years, there has been an increase in the number of concerns about the security and privacy of PHI.
In general, the law governing PHI in the United States applies to data collected during the course of providing and paying for health care. Privacy and security laws govern how healthcare professionals, hospitals, health insurers, and other Covered Entities collect, use, and safeguard data. When determining whether information is PHI under US law, it is critical to understand that the source of the data is just as important as the data itself. Sharing information about someone on the street who has a visible medical condition, such as an amputation, is not prohibited under US law. Obtaining information about the amputation solely from a protected source, such as an electronic medical record, would, however, violate HIPAA regulations.
To learn more about Protected health information refer :
https://brainly.com/question/7416382
#SPJ4
2
ng and Upgrading Computers: Mastery Test
Select the correct answer.
Which of the following can computer maintenance software determine?
O A.
O B.
O C.
O D.
whether your hard drive is about to fail
whether your monitor or screen is drawing too much power
the humidity inside your desktop computer
the amount of dust inside your laptop
Reset
Next
Answers
whether your hard drive is about to fail can computer maintenance software determine.
What is computer maintenance software ?
Software that centralises maintenance data and streamlines maintenance operations is known as a computerised maintenance management system, or CMMS. It aids in maximising the use and accessibility of tangible assets like machines, transportation, communications, plant infrastructures, and other assets. CMMS systems, also known as computerised maintenance management information systems (CMMIS), are used in the manufacturing, energy, transportation, building, and other sectors where physical infrastructure is essential.
A CMMS's database is its fundamental component. The information regarding the assets that a maintenance organisation is responsible for maintaining, as well as the tools, supplies, and other resources needed to do so, are organised using a data model.
Read more about computer maintenance software:
https://brainly.com/question/28561690
#SPJ1
4. suppose a computer running tcp/ip (with ipv4) needs to transfer a 1024 bytes file to a host. a. [4 pts] how many megabytes, including all of the tcp/ip overhead, would be sent? assume a payload size of 64 bytes. b. [2 pts] what is the protocol overhead, stated as a percentage? c. [4 pts] how small would the overhead have to be in kb for the overhead to be lowered to 10% of all data transmitted?
Answers
The Transmission Control Protocol and Internet Protocol (TCP/IP) is a popular network protocol. TCP/IP packets feature a little amount of protocol overhead, typically between 40 and 80 bytes in each packet.
What megabytes, including all the overhead?The actual data payload is often between 46 and 1500 bytes. The headers, which make up the overhead regardless of the payload size, total 26 bytes: 7 bytes for the Preamble. One byte SOF (Start of Frame)
Therefore, TCP/IP packets feature a little amount of protocol overhead, typically between 40 and 80 bytes in each packet.
Learn more about TCP/IP here:
https://brainly.com/question/27742993
#SPJ1
which of the following is unsolicited and unwanted software that takes up stealthy unauthorized and uninvited residence on a computer in order to gather information?
Answers
The unsolicited and unwanted software that takes up stealthy unauthorized and uninvited residence on a computer to gather information is known as Spyware.
Spyware is a type of malicious software that secretly monitors and collects user data from a computer without the user's consent. It often gets installed on a computer through deceptive tactics such as bundling with seemingly legitimate software or through phishing attacks. Once installed, spyware can track a user's browsing habits, keystrokes, personal information, and other activities, sending this data to a third party.
This gathered information can then be used for targeted advertising, identity theft, or other malicious purposes. To prevent spyware, it is essential to use reliable security software and be cautious when downloading and installing new applications.
Learn more about software here:
https://brainly.com/question/985406
#SPJ11
Jack is a forensic specialist who wants to examine a network router for potential evidence in a case. What is the first step he should take to safely examine the router
Answers
The step that can be carried by Jack for the safe examination of the router as the case evidence is connecting the router to the network.
What is a network router?The network router is given as the connection between the two networks that mediate the delivery of the packed information.
The safety of the router in the forensic evidence is important as the incorrect connection resulting in corruption and deletes all the data.
Being the specialist, to check the router, the first step to be followed by Jack was connecting the router to the network.
Learn more about routers, here:
https://brainly.com/question/15851772
#SPJ1
which is the best software program
Answers
Answer:
The question "which is the best software program" is quite broad, as the answer can depend on the context and what you're specifically looking for in a software program. Software can be developed for a myriad of purposes and tasks, including but not limited to:
- Word processing (e.g., Microsoft Word)
- Spreadsheet management (e.g., Microsoft Excel)
- Graphic design (e.g., Adobe Photoshop)
- Video editing (e.g., Adobe Premiere Pro)
- Programming (e.g., Visual Studio Code)
- 3D modeling and animation (e.g., Autodesk Maya)
- Database management (e.g., MySQL)
- Music production (e.g., Ableton Live)
The "best" software often depends on your specific needs, your budget, your experience level, and your personal preferences. Therefore, it would be helpful if you could provide more details about what kind of software you're interested in, and for what purpose you plan to use it.
If your daily commute time is 1 hour and today you worked an hour of overtime, how much time is added to your commute time for the day?
Answers
Answer:
1 hour is added
Explanation:
duhhhh
Answer:
Its 10 hours
Explanation:
its ten Because it takes you an hour to get there then an hour to get back, so thats 2 hours and then you times that by the total days you work which is 5 and you get 10
Which is government departments fund the Global Positioning System
The Global Positioning System is funded by the department of
Answers
Answer:
The department of defense
Explanation:
Research an IoT device on the internet and share the research with your classmates. I suggest searching by industry such as Health, Manufacturing, Construction, etc. Here are the rules: Do NOT research Fitbit! In your initial post, answer the following questions: How will 5G transform developments in the IoT? What are two potential issues associated with the expansion of the IoT? Your Initial post should be two full paragraphs in length. The rest of the normal forum rules apply.
Answers
The advent of 5G technology is expected to significantly transform developments in the Internet of Things (IoT), enabling faster and more reliable connectivity, lower latency, and support for a greater number of connected devices.
However, this expansion of the IoT also presents potential issues related to security and privacy vulnerabilities, as well as the need for robust infrastructure and standards.
The deployment of 5G networks is poised to revolutionize the IoT landscape by addressing some of the limitations of existing connectivity options. With its ultra-fast speeds, low latency, and high capacity, 5G technology will enable more efficient and seamless communication between IoT devices. This will facilitate real-time data transmission, enhance the responsiveness of IoT applications, and unlock new possibilities in various industries such as healthcare, manufacturing, and smart cities.
However, the expansion of the IoT also brings forth certain challenges. One major concern is the security and privacy of IoT devices and the data they generate. With an increasing number of connected devices, the attack surface expands, making it more difficult to ensure robust security measures across the entire ecosystem. Additionally, privacy concerns arise due to the massive amounts of data collected by IoT devices, requiring careful management and protection of personal information.
Another issue associated with the IoT's expansion is the need for infrastructure development and standardized protocols. 5G networks require the dense deployment of small cells and robust network infrastructure to support the vast number of connected devices. Additionally, standardized protocols and frameworks are necessary to ensure interoperability and seamless integration of diverse IoT devices and systems.
In conclusion, 5G technology is set to transform developments in the IoT by enabling faster, more reliable connectivity and supporting a larger number of connected devices. However, this expansion also poses challenges in terms of security, privacy, and the need for infrastructure development and standardization. Addressing these issues will be crucial for the successful and widespread adoption of IoT technologies across various industries.
Learn more about Internet of Things here:
https://brainly.com/question/29767247
#SPJ11
Need answer ASAP
In which phrase does software coding and testing happen in the spiral model?
The spiral model does not have a separate testing phase. Both software coding and testing occurs during the _____ phase.
Answers
both software coding and testing occurs during Engineering phase
What is the BYP algorithm? How it is used in Computational
Biology? Describe all the steps of this algorithm. Mention the time
and space complexities for the best case, the average case, and the
worst
Answers
The algorithm is a computational biology algorithm used for sequence alignment. It efficiently aligns biological sequences by considering both the primary sequence and secondary structure information. The algorithm consists of several steps, including base-pairing matrix computation, seed selection, seed extension, and final alignment. The time and space complexities vary depending on the specific implementation and the characteristics of the sequences being aligned.
The BYP algorithm is widely used in computational biology to align biological sequences, such as DNA or RNA, by incorporating information about their secondary structures. It improves upon traditional sequence alignment methods by considering both primary sequence and structural information, leading to more accurate alignments.
The algorithm operates in several steps. First, a base-pairing matrix is computed for the sequences, representing the potential base pairs between nucleotides. This matrix is used to identify potential seeds, which are short regions of high similarity between the sequences. These seeds are selected based on certain criteria, such as minimum seed length and minimum number of base pairs.
Next, the selected seeds are extended to find longer regions of similarity. This step involves iteratively extending the seeds in both directions, considering the base-pairing information and penalizing gaps and mismatches. The extensions continue until a certain threshold is reached or no further extension is possible.
Finally, the algorithm generates the final alignment by combining the extended seeds and filling in gaps to optimize a scoring function. The scoring function takes into account the similarity of bases, penalties for gaps and mismatches, and the base-pairing information.
The time and space complexities of the BYP algorithm depend on various factors, including the length and complexity of the sequences being aligned, the specific implementation of the algorithm, and the available computational resources. In the best case scenario, where the sequences are very similar and have low complexity, the algorithm can achieve linear time and space complexities. However, in the worst case, where the sequences are highly dissimilar and have complex secondary structures, the time and space complexities can approach quadratic or cubic orders.
Learn more about algorithm
brainly.com/question/22984934
#SPJ11
11.5 Code Practice Edhesive??
In this code practice, we will continue to employ W3Schools tools to practice writing HTML. You should have already read through the tutorials for the four HTML topics below, found in Lesson 11.5. Now, complete the exercises linked below for each topic. Once you complete these exercises, move onto the next set of instructions below.
HTML Styles (Links to an external site.)
HTML Formatting (Links to an external site.)
HTML CSS (Links to an external site.)
HTML Links (Links to an external site.)
Create a web page that has two paragraphs. One of the paragraphs should be aligned to the center and have red text. The other paragraph should be aligned to the right and be in italics. Refer to the sample below for clarification.
11.5 Code Practice example
Your program should begin and end with the following tags:
# Insert your code here!
In the programming environment, you will notice that once you type one tag (for example, the html opening tag), the environment automatically populates the closing tag for you. Be careful not to double up on closing tags, otherwise your HTML will not run.
As you write your web page, you can click the "Run Code" button to view it in real time.
Answers
Answer:
<html>
<body>
<p style="text-align:center;color:red;">This is a paragraph.</p>
<p><i> "This text is italic</i></p>
</body>
</html>
Explanation:
I got a 75%. Hope this helps.
HTML codes are placed in segments called tags.
Tags are divided into two
The opening tagThe closing tagTake for instance, the opening and closing tags of the paragraph tag are <p> and </p>, respectively.
Having explained what tags are, the required HTML code is as follows:
<html>
<body>
<p align="center"><font color="black"> This is a paragraph 1</font></p>
<p align="right"><i> This is a paragraph 2 </i></p>
</body>
</html>
The paragraphs are aligned using center and right alignments, while the text in the first paragraph is colored using the color tag
Read more about HTML at:
https://brainly.com/question/25055825
_drugs have side effects
Answers
Answer:
yes
Explanation:
Java Coding help please this is from a beginner's class(PLEASE HELP)
Prior to completing a challenge, insert a COMMENT with the appropriate number.

Answers
Given in the images are the completed method that one can be able to use for a linear search on an array:
What is the Java Coding?The given text provides several programming code that bear completing the work of different styles.
Note tnat Each system has a specific set of conditions that need to be met in order to give the anticipated affair.
Therefore, code range from simple codes similar as performing a direct hunt on an array or publishing a board with a given size and pattern, to more complex codes similar as checking if one array contains another array in a successive and ordered manner.
Learn more about Java Coding from
https://brainly.com/question/18554491
#SPJ1
See text below
1) Complete the method: public static int simpleSearch(int[] nums, int value), that performs a linear (sequential) search on the array parameter, and returns the index of the first occurrence the of value parameter. Return -1 if value doesn't exist in nums.
simpleSearch(new int[] {8, 6, 7, 4, 3, 6, 5), 7) >>> 2
//2 is index of the value 7
2) Complete the method: public static void squareBoard(int num), that prints an num by num board with a '#' character in every position.
squareBoard(2) >>>
3) Complete the method: public static void checkerBoard(int num), that prints an num by num board with a '# character in every position in a 'checkerboard' fashion.
checker Board(3) >>>
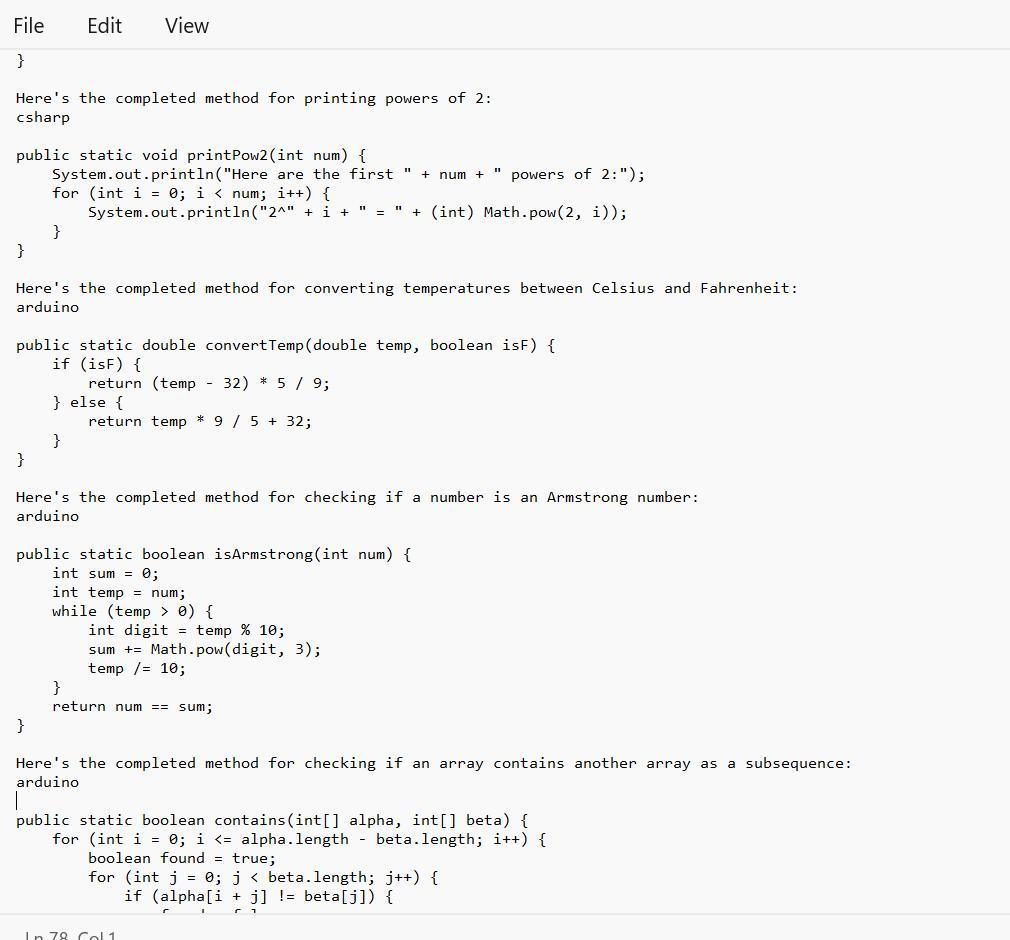
4) Complete the method: public static void printPow2(int num), that prints num powers of 2 (including O), given the supplied number. Use String concatenation to print like this:
//with a call of printPow2(4):
Here are the first 4 powers of 2:
2^8 = 1
2^1 = 2
2^2 = 4
238
5) Complete the method: public static double convertTemp/double temp, boolean isF), that performs a Celsius to Fahrenheit conversion (and vice versa) when called. The parameter isF will be supplied as true if temp is in Fahrenheit.
6) Complete the method: public static boolean isArmstrong(int num), that returns true if the supplied number is an "Armstrong number". An Armstrong number is a number for which the sum of the cubes of its digits is equal to the number itself. Modulus and integer division will help.
IsArmstrong (371) >>> true //3*3*3+7*7*7+ 1*1*1 == 371
7) Difficulty level HIGH: Complete the method: public static boolean contains(int[] alpha, int[] beta). that returns true if the sequence of elements in beta appear anywhere in alpha. They must appear consecutively and in the same order. You'll need nested loops for this.
contains(new int[] {1, 2, 1, 2, 3), new int[] {1, 2, 3}) >>> true
contains (new int[] 1, 2, 1, 2, 3, 1), new intf (1, 1, 3, 1)) >>> false


Of the seven types of normal forms, how many are considered the most critical for creating a working database?
A. 5
B. 3
C. 2
D. 4
Answers
Answer:3
Explanation:
favorite rappers22???
Answers
There are so many rappers that I love and I can't choose.
And there are K-pop singers who are also good at rap.
QUESTION 5 (a) A 3-SAT Boolean formula is a conjunction (an "and") of a number of clauses, each of which is a disjunction (an "or") of exactly three literals. An example of a 3-SAT formula, using four
Answers
A 3-SAT Boolean formula consists of multiple clauses, each containing a disjunction of exactly three literals, and the entire formula is a conjunction of these clauses. For example, consider a 3-SAT formula with four clauses:
How can a 3-SAT Boolean formula be defined?A 3-SAT Boolean formula is a logical expression that represents a problem in boolean satisfiability. It is composed of multiple clauses, where each clause contains three literals combined with an "or" operator. The formula as a whole is formed by joining these clauses with an "and" operator. This type of formula is often used in computer science and mathematics to study the complexity of solving boolean satisfiability problems.
Learn more about 3-SAT
brainly.com/question/15088390
#SPJ11
Explain the expression below
volume = 3.14 * (radius ** 2) * height
Answers
Answer:
Explanation:
Cylinder base area:
A = π·R²
Cylinder volume:
V = π·R²·h
π = 3.14
R - Cylinder base radius
h - Cylinder height
what is the result obtained after data processing called?
Answers
Answer:
the result after data processing is called output
Answer:
The meaningful result obtained after processing is known as information. The collection of computer programs and related data that provide the instructions telling a computer what to do is called software
What is the keyboard shortcut to show formulas in a worksheet (as opposed to the value)? OCTRL+S OCTRL + Z CTRL- There is no shortcut for showing formulas
Answers
CTRL + (tilde) is a keyboard shortcut to show formulas instead of values in Excel spreadsheets. It can be found in the upper-left corner of most keyboards, below the Escape key or just left of the 1 key.
The keyboard shortcut to show formulas in a worksheet (as opposed to the value) is `CTRL + ~` (tilde).When working with Excel spreadsheets, you might want to display the formulas instead of the values in your cells. This could be done by using the "Show Formulas" button. But, if you're doing this frequently, it's easier to use a keyboard shortcut. To do this, press `CTRL + ~` (tilde) and it will show all of the formulas in your spreadsheet instead of the values.
The tilde symbol, ~, can be found in the upper-left corner of most keyboards. It is usually located below the Escape key or just left of the 1 key. It's worth noting that pressing the `CTRL + ~` (tilde) keyboard shortcut again will switch back to displaying the values.
To know more about Excel spreadsheets Visit:
https://brainly.com/question/10541795
#SPJ11
what is authenticity
Answers
Answer:
the quality of being authentic
Explanation:
Need help Plz i have only 20 min





Answers
Answer:
1. tripod
2.srry i don't know
3. true
4. sorry i don't know
5. prob true
Answer:
Tripod
2. The pixel
3. True
4. Goo_____gle Slides
5. True
7. Write a Qbasic program to read the value
of P T and A Find simple interest and total.
amount
Answers
Answer:
PRINT "Values for Principal (P), Rate (A) and Time (T)"
INPUT P, A, T
I = P * A * T/100
Amount = P + I
PRINT "Interest: ", I
PRINT "Amount: ", Amount
Explanation:
This prompts the user for values for Principal, Rate and Time
PRINT "Values for Principal (P), Rate (A) and Time (T)"
This gets values for Principal (P), Rate (R) and Time (T)
INPUT P, A, T
This calculates the interest (I)
I = P * A * T/100
This calculates the amount (A)
Amount = P + I
This prints the interest (I)
PRINT "Interest: ", I
This prints the amount (A)
PRINT "Amount: ", Amount
Which of the following is constantly changing and advancing?
Innovation
Cell phones
Technology
Computers
Answers
Answer:
Technology
Explanation:
This is because Cell phones ,Innovation ,and Computers ARE changing although they are in the same group of "Technology" so it would be technology.
Any questions?
A business might want to use virtual machine to
allow outside customers access to files
completely eliminate physical servers
easily secure the company intranet
remotely maintain servers
Answers
Answer:
Allow outside customers to access files
Explanation:
A VM doesn't eliminate the need for additional load balancing hardware, an intranet is maintained with multiple computers typically, and remotely maintaining servers can be accomplished with SSH.
The reason you would want a VM for outside customer access is so that they can't interfere with anything outside of the sandboxed environment, this helps to mitigate hacking and easily isolate specific customer information.
A business might want to use virtual machine to allow outside customers access to files, completely eliminate physical servers, easily secure the company intranet, and remotely maintain servers.
What is virtual machine?A virtual machine (VM) is a software-based emulation of a computer system, allowing a physical computer to run multiple operating systems and applications simultaneously.
A business might want to use virtual machines to:
Allow outside customers access to files: A virtual machine can be set up to provide external customers access to specific files or applications without compromising the security of the company's internal network.
Completely eliminate physical servers: Virtual machines allow multiple operating systems to run on a single physical server, reducing the need for physical hardware and saving costs on maintenance and power consumption.
Easily secure the company intranet: Virtual machines can be used to create a secure network environment that can be easily managed and isolated from the rest of the network.
Remotely maintain servers: Virtual machines can be managed and maintained remotely, which allows IT staff to perform tasks without having to be physically present at the server location. This can save time and reduce costs associated with travel and on-site maintenance.
Thus, all options are correct.
For more details regarding business, visit:
https://brainly.com/question/15826604
#SPJ2
hris has received an email that was entirely written using capitalization. He needs to paste this text into another document but also ensure that the capitalization is removed.
What should Chris do?
Answers
Computer Systems Servicing
what are the steps in 5s program
Answers
you can just search that up on googl and it will show up
\hope I helped :)
PLS HELP ASAP ILL GIVE BRAINLKEST THANKS ITS FOR TODAY
