If an exception occurs in a try-catch block, the code in the finally clause ________. is executed is not executed may be executed is not executed if the exception is caught
Answers
If an exception occurs in a try-catch block, the code in the final clause is executed.
The primary purpose of the final block is to include code that should be executed regardless of whether an exception occurred or not. It serves to ensure that essential cleanup or finalization tasks, such as closing open resources (files, database connections, etc.), releasing acquired locks, or restoring the program state, are performed reliably.
Even if an exception is caught and the appropriate catch block is executed, the control flow will still reach the final block after the catch block has finished executing. Therefore, the code within the final block is always executed, irrespective of whether the exception is caught or not.
To learn more about try-catch block,
https://brainly.com/question/32114956
Related Questions
What are some tasks for which you can use the VBA Editor? Check all that apply.
typing code to create a new macro
sharing a macro with another person
viewing the code that makes a macro work
starting and stopping the recording of a macro
modifying a macro to include an additional action
jk its a c e
Answers
Answer:
typing code to create a new macro
viewing the code that makes a macro work
modifying a macro to include an additional action
Explanation:
Typing code to create a new macro, viewing the code that makes a macro work and modifying a macro to include an additional action are some tasks for which you can use the VBA Editor. Hence, option A, C and D are correct.
What is Typing code?
In computer science and computer programming, a data type is a group of probable values and a set of allowed operations. By examining the data type, the compiler or interpreter can determine how the programmer plans to use the data.
If a variable is highly typed, it won't immediately change from one type to another. By automatically converting a string like "123" into the int 123, Perl allows for the usage of such a string in a numeric context. The opposite of weakly typed is this. Python won't work for this because it is a strongly typed language.
The symbol used to create the typecode for the array. the internal representation of the size in bytes of a single array item. Create a new element and give it the value.
Thus, option A, C and D are correct.
For more information about Typing code, click here:
https://brainly.com/question/11947128
#SPJ2
Write a note on the hardware parts required to establish a network.
Answers
1. Network Interface Card (NIC): A NIC is a hardware component that is installed in a computer to allow it to connect to a network. It provides the physical connection between the computer and the network.
2. Switches: A switch is a networking device that connects multiple devices together on a network. It allows devices to communicate with each other and facilitates the transfer of data between them.
3. Router: A router is a networking device that connects multiple networks together. It directs traffic between networks and provides a gateway to the internet.
4. Cables: Cables are used to connect devices to the network. There are different types of cables, such as Ethernet cables, which are used to connect devices to switches and routers.
5. Wireless Access Points: Wireless access points are devices that allow wireless devices to connect to a network. They provide wireless connectivity to devices such as laptops, smartphones, and tablets.
6. Servers: Servers are computers that provide services to other devices on the network. They can provide services such as file sharing, email, and web hosting.
Overall, these are some of the hardware components that are required to establish a network. The specific components required will depend on the size and complexity of the network.
Pleaseeee hellppp!!!!!
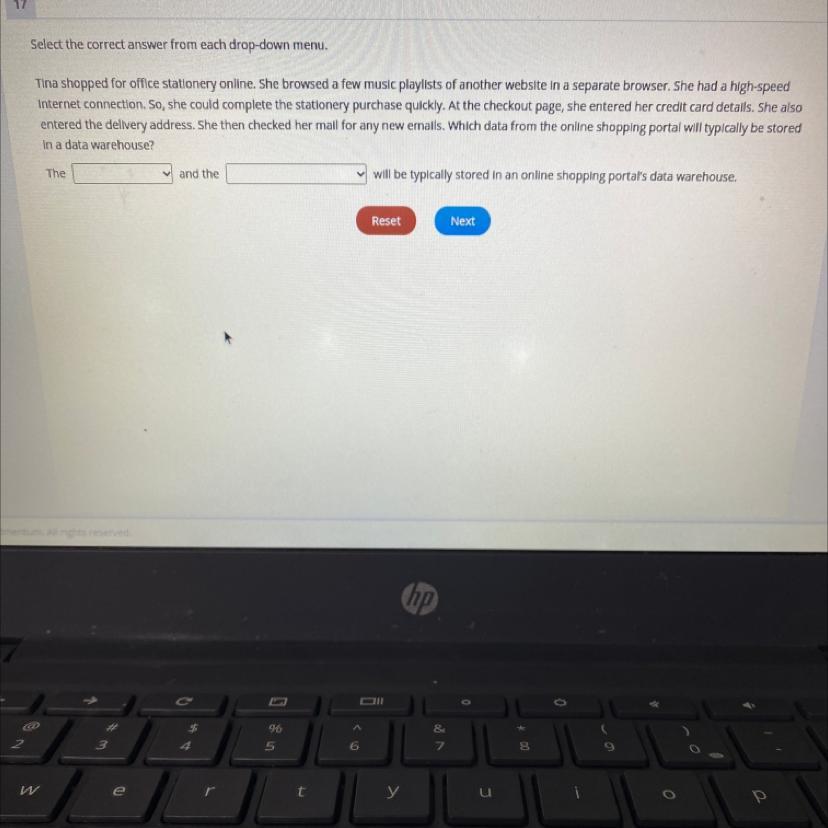
Answers
Answer:
credit card info and delivery address
Explanation:
#9: A persistent store of organized data useful for storing large quantities of data with a user-friendly method of retrieval is called: (A) The Home button (B) a worksheet (C) a database (D) a workbook
#10: Which type of database uses just one table to store data? (A) Flat File (B) Relational (C) Database interaction (D) Query
#11: Which of the following uniquely identifies one entity (object, person, thing) in a table? (A) Query (B) Record (C) Field (D) Schema
#12: The logical way tables are linked is known as the database: (A) Access (B) Primary Key (C) Schema (D) Justification
#13: Which of the following is the field that uniquely identifies a record? (A) Primary Key (B) Schema (C) Number (D) Table Link
#14: Requests to retrieve data written in a language such as SQL are called? (A) Numbers (B) Data (C) Databases (D) Queries
#15: The database program for Microsoft Office is called: (A) Access (B) MS Databases (C) Obvibase (D) Queries
PLEASE ANSWER RIGHT ANSWERS DONT ANSWER JUST FOR POINTS I RLLY NEED THIS
Answers
Suppose you wanted to quickly take a photograph of a dew drop on a rose petal before it rolled off. Which camera mode would be most
appropriate?
A: landscape
B: L
C: macro
D: M
Answers
Or search up the difference of those camera modes to see which one is better but I’m going with C
Answer:
The answer is M
Explanation:
EDGE 2022
List the four HIPAA Standards and briefly describe their purpose?
Answers
I'm happy to help you with your question about the four HIPAA standards. Here they are along with their purposes:
1. Privacy Rule: This standard aims to protect individuals' medical records and personal health information. It sets the conditions under which healthcare providers and other covered entities can use or disclose a patient's protected health information (PHI).
2. Security Rule: This standard focuses on safeguarding electronic PHI (ePHI) by establishing guidelines for administrative, physical, and technical safeguards. The Security Rule ensures that ePHI is kept secure and confidential, while allowing access to authorized personnel.
3. Transactions and Code Sets Rule: This standard simplifies and standardizes electronic data interchange (EDI) in healthcare transactions, such as claims, enrollment, eligibility, and payment information. By adopting a common set of code sets and formats, it streamlines processes and reduces administrative costs.
4. Unique Identifiers Rule: This standard assigns unique identifiers to healthcare providers (National Provider Identifier, or NPI), health plans (Health Plan Identifier, or HPID), and other entities to facilitate efficient and accurate electronic transactions. These identifiers help maintain consistency and accuracy in healthcare data exchange.I hope this answers your question! Let me know if you need any further clarification.
Learn more about safeguarding here
https://brainly.in/question/8965643
#SPJ11
You are working as a project manager. One of the web developers regularly creates dynamic pages with a half dozen parameters. Another developer regularly complains that this will harm the project’s search rankings. How would you handle this dispute?
Answers
From the planning stage up to the deployment of such initiatives live online, web project managers oversee their creation.They oversee teams that build websites, work with stakeholders to determine the scope of web-based projects, and produce project status report.
What techniques are used to raise search rankings?
If you follow these suggestions, your website will become more search engine optimized and will rank better in search engine results (SEO).Publish Knowledgeable, Useful Content.Update Your Content Frequently.facts about facts.possess a link-worthy website.Use alt tags.Workplace Conflict Resolution Techniques.Talk about it with the other person.Pay more attention to events and behavior than to individuals.Take note of everything.Determine the points of agreement and disagreement.Prioritize the problem areas first.Make a plan to resolve each issue.Put your plan into action and profit from your victory.Project managers are in charge of overseeing the planning, execution, monitoring, control, and closure of projects.They are accountable for the project's overall scope, team and resources, budget, and success or failure at the end of the process.Due to the agility of the Agile methodology, projects are broken into cycles or sprints.This enables development leads to design challenging launches by dividing various project life cycle stages while taking on a significant quantity of additional labor.We can use CSS to change the page's background color each time a user clicks a button.Using JavaScript, we can ask the user for their name, and the website will then dynamically display it.A dynamic list page: This page functions as a menu from which users can access the product pages and presents a list of all your products.It appears as "Collection Name" in your website's Pages section.To learn more about search rankings. refer
https://brainly.com/question/14024902
#SPJ1
Identify the negative impact of social media
Answers
1. Addiction: Many people can become addicted to social media and spend excessive amounts of time scrolling through their feeds, which can lead to problems with productivity and social interactions.
2. Mental health problems: Social media use has been linked to an increase in mental health problems such as depression, anxiety, and low self-esteem. This can be due to a number of factors, including comparing oneself to others, cyberbullying, and the constant stream of negative news and information.
3. Spread of misinformation: Social media can be a breeding ground for misinformation, as it is easy for false information to spread quickly through networks of people. This can have serious consequences, as people may make decisions based on incorrect information.
4. Decreased privacy: Social media platforms often collect and use personal data for targeted advertising and other purposes, which can lead to a loss of privacy for users.
5. Cyberbullying: Social media can also be a platform for cyberbullying, which is when someone is harassed, threatened, or embarrassed online. This can have serious consequences for the victim, including mental health problems and even sui cide.
your network uses the following backup strategy. you create: full backups every sunday night. differential backups monday night through saturday night. on thursday morning, the storage system fails. how many restore operations would you need to perform to recover all of the data? answer one two three four
Answers
The answer is two. To recover all of the data, you would need to perform two restore operations: one for the most recent full backup (Sunday night) and one for the most recent differential backup before the failure (Wednesday night).
The full backup on Sunday night contains all of the data, while the differential backups contain all changes since the last full backup. Restoring the full backup followed by the differential backup will bring the system up to the state it was in before the failure.
For more question on backup click on
https://brainly.com/question/30826635
#SPJ11
Pls help me!!!!!!!!!!!!!!!!!

Answers
Answer:
500
Explanation:
and 50
How much weight does a headgear need to carry
Answers
Answer:
The model will have a mine winch, shaft headgear, and a lift cage.
Explanation:
With most forms of media, you can use up to _____% under “fair use” guidelines.
Answers
Answer:
With most forms of media, you can use up to 10% under “fair use” guidelines.
PLEASE HELP WITH MY COMPUTER
this thing is popped up and it's annoying. I'm on a HP laptop how do i get rid of it?

Answers
Answer:
Escape or turn it off then back on??
Explanation:
I'm not very sure what is going on but idfk
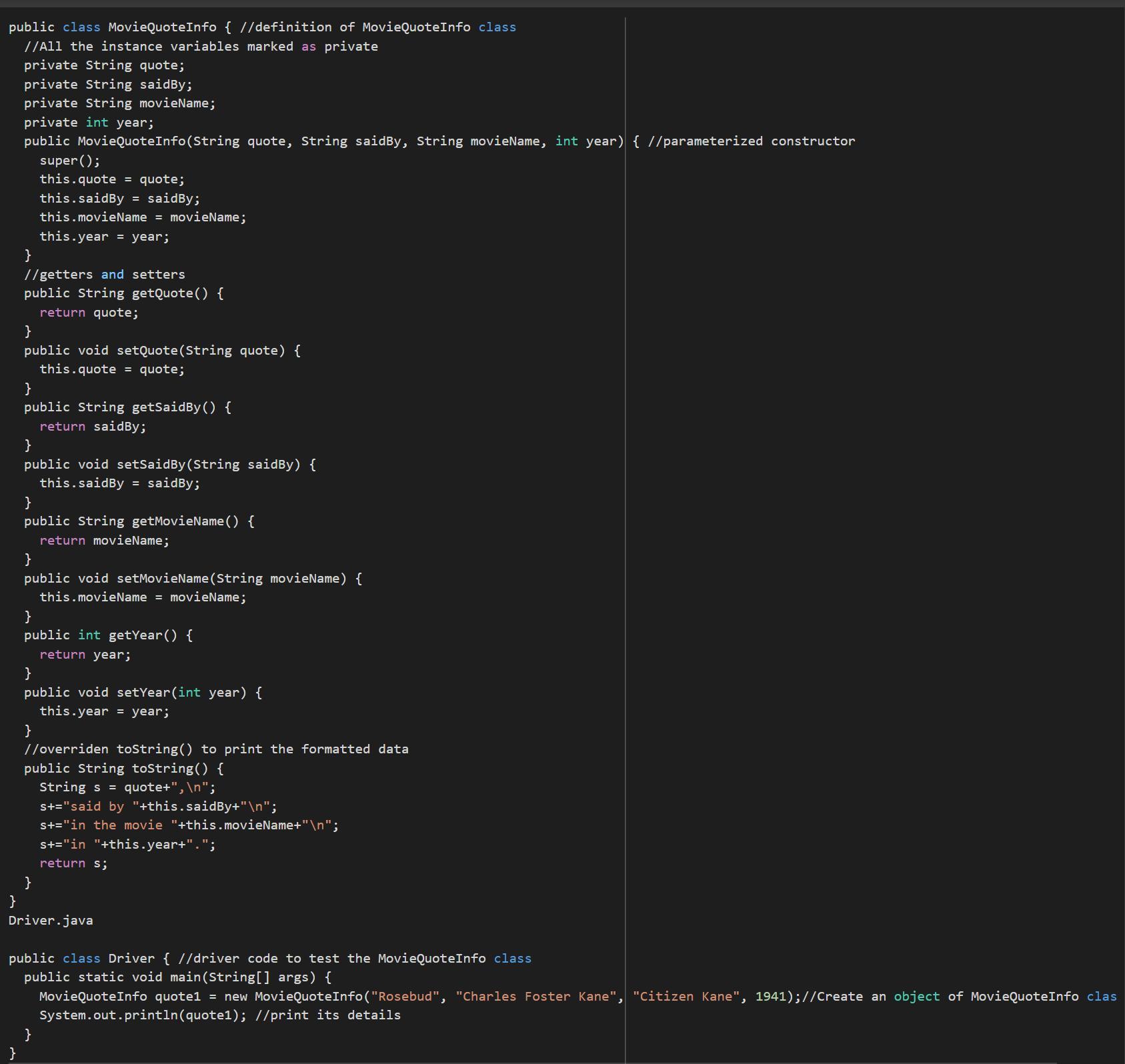
Write, compile, and test the MovieQuoteInfo class so that it displays your favorite movie quote, the movie it comes from, the character who said it, and the year of the movie: I GOT IT DONT WATCH AD.
class MovieQuoteInfo {
public static void main(String[] args) {
System.out.println("Rosebud,");
System.out.println("said by Charles Foster Kane");
System.out.println("in the movie Citizen Kane");
System.out.println("in 1941.");
}
}
Answers
Using the knowledge of computational language in JAVA it is possible to write a code that removes your favorite phrase from the movie. It consists of two classes in which one is driver code to test the MovieQuoteInfo class.
Writing code in JAVA:
public class MovieQuoteInfo { //definition of MovieQuoteInfo class
//All the instance variables marked as private
private String quote;
private String saidBy;
private String movieName;
private int year;
public MovieQuoteInfo(String quote, String saidBy, String movieName, int year) { //parameterized constructor
super();
this.quote = quote;
this.saidBy = saidBy;
this.movieName = movieName;
this.year = year;
}
//getters and setters
public String getQuote() {
return quote;
}
public void setQuote(String quote) {
this.quote = quote;
}
public String getSaidBy() {
return saidBy;
}
public void setSaidBy(String saidBy) {
this.saidBy = saidBy;
}
public String getMovieName() {
return movieName;
}
public void setMovieName(String movieName) {
this.movieName = movieName;
}
public int getYear() {
return year;
}
public void setYear(int year) {
this.year = year;
}
//overriden toString() to print the formatted data
public String toString() {
String s = quote+",\n";
s+="said by "+this.saidBy+"\n";
s+="in the movie "+this.movieName+"\n";
s+="in "+this.year+".";
return s;
}
}
Driver.java
public class Driver { //driver code to test the MovieQuoteInfo class
public static void main(String[] args) {
MovieQuoteInfo quote1 = new MovieQuoteInfo("Rosebud", "Charles Foster Kane", "Citizen Kane", 1941);//Create an object of MovieQuoteInfo class
System.out.println(quote1); //print its details
}
}
See more about JAVA at brainly.com/question/12975450
#SPJ1
which two packet filters could a network administrator use on an ipv4 extended acl? (choose two.)
Answers
The two packet filters that a network administrator could use on an IPv4 extended ACL are source IP address and destination port.
How to filter packet on an IPv4 extended ACL? (Two filters)Two packet filters that a network administrator could use on an IPv4 extended ACL (Access Control List) are:
Source IP Address: An extended ACL can filter packets based on the source IP address. This allows the network administrator to control access based on the specific source IP addresses or ranges.Destination Port: An extended ACL can also filter packets based on the destination port number. This allows the network administrator to control access to specific services or applications based on the destination port being used.By using these packet filters in an extended ACL, network administrators can enhance network security and control the flow of traffic based on specific criteria such as source IP addresses and destination ports.
Learn more about packet
brainly.com/question/13901314
#SPJ11
Multiple computers configured to be able to communicate and share information with each other form a ____________.
Answers
Multiple computers configured to be able to communicate and share information with each other form a network.
In the field of computers, a computer network can be described as a network that contains multiple computers connected to each other so that data or information can be shared among these computers.
Local-area networks, also referred to as LAN and wide-area networks also referred to as WAN are two major forms of forming a computer network.
However, certain communication protocols are set for computer networking in order to keep check of the privacy of data that a user doesn't want to share.
In computer networking, nodes and links are used for making connections among the computers.
To learn more about network, click here:
https://brainly.com/question/1167985
#SPJ4
Which of the following is a visual thinking tool that aids students in organizing ideas through analysis, synthesis, and comprehension? outline outliner mind map drawing
Answers
Answer:
The answer is "mind map drawing".
Explanation:
In the given-question, the above given choice is correct because it includes the use of texts and images to understand the creation, explain, communicate, and resolve issues.
Its resources can help students of all ages with progress learning skills through all academic areas. The map draws visual thought resources is used to help students create ideas via analysis, synthesis, and understanding.Answer:
mind map
Explanation:
For ul elements nested within the nav element, set the list-style-type to none and set the line-height to 2em.
For all hypertext links in the document, set the font-color to ivory and set the text-decoration to none.
(CSS)
Answers
Using the knowledge in computational language in html it is possible to write a code that For ul elements nested within the nav element, set the list-style-type to none and set the line-height to 2em.
Writting the code:<!doctype html>
<html lang="en">
<head>
<!--
<meta charset="utf-8">
<title>Coding Challenge 2-2</title>
</head>
<body>
<header>
<h1>Sports Talk</h1>
</header>
<nav>
<h1>Top Ten Sports Websites</h1>
<ul>
</ul>
</nav>
<article>
<h1>Jenkins on Ice</h1>
<p>Retired NBA star Dennis Jenkins announced today that he has signed
a contract with Long Sleep to have his body frozen before death, to
be revived only when medical science has discovered a cure to the
aging process.</p>
always-entertaining Jenkins, 'I just want to return once they can give
me back my eternal youth.' [sic] Perhaps Jenkins is also hoping medical
science can cure his free-throw shooting - 47% and falling during his
last year in the league.</p>
<p>A reader tells us that Jenkins may not be aware that part of the
least-valuable asset.</p>
</article>
</body>
</html>
See more about html at brainly.com/question/15093505
#SPJ1


if ur computer is runing slowly what is most likey to slove the problem
Answers
list = [1,2,3,'a','b','c'] ... write a code to output b * (python)
Answers
Answer:
please tell me if you find the answer i have the same q for my IT med term
Answer:
print(list[4])
Explanation:
Complete breakdown:
The command 'print' shows what command is displayed on the screen
The 'list' shows that Python should print something inside a list
The '4' is the index number of list. Index numbers start from 0 so
'1' - 0
'2'- 1
'3' - 2
'a' - 3
'b' - 4
'c' - 5
How can I use ai to create teaching materials?
Answers
Answer:
Almost every modern appliance, device, and vehicle have improved performance and functionality thanks to artificial intelligence (AI). To succeed now and in the future, students must learn to comprehend and manage AI and related technologies.
To enable them to use technology responsibly and effectively, students will need to acquire digital skills, knowledge, and understanding. The skill sets, toolkits, and mindsets put together under the umbrella of "digital readiness" will equip students for the future.
Q: what is the addressing mode for the following instruction: (B139), BL Immediate mode Register Mode Indirect mode Direct mode O Indexed Addressing Mode MOV* 2 points
Answers
The addressing mode for the instruction (B139) is immediate mode.
Immediate mode is an addressing mode in which the operand value is directly specified in the instruction itself. In this mode, the instruction contains a constant value or an immediate data that is used as the operand. The value is typically specified using a numeric or symbolic representation. In the given instruction (B139), the value "B139" is directly specified as the operand, indicating an immediate mode addressing.
Immediate mode is commonly used when the operand value is known at compile time or when there is a need to perform immediate calculations or comparisons. It allows for efficient and concise coding by eliminating the need for extra memory accesses or register usage. However, it also has limitations as the immediate value is fixed and cannot be modified during program execution.
In the context of assembly language programming, understanding different addressing modes is essential for effective program design and optimization. Each addressing mode offers unique benefits and trade-offs in terms of code efficiency, memory usage, and flexibility. By choosing the appropriate addressing mode, programmers can tailor their instructions to efficiently manipulate data and perform desired operations.
To learn more about programming click here:
brainly.com/question/14368396
#SPJ11
Shira’s Shoes sold 875,000 pairs of sandals in June, which was 70% of the total number of shoes sold. How many shoes did the company sell in June? Analyze Emily’s calculations. What error did she make?
Answers
Explanation:
Emily solved for a part when she should have solved for the whole. 875,000 should be the numerator of the equivalent ratio. 70 x 12,500 is 875,000. So the answer is 100 x 12,500 which is 1,250,000.
Answer:
Emily solved for a part when she should have solved for the whole. 875,000 should be the numerator of the equivalent ratio. 70 x 12,500 is 875,000. So the answer is 100 x 12,500 which is 1,250,000.
For this assignment, you will create a calendar program that allows the user
to enter a day, month, and year in three separate variables as shown below.
Day:
Month:
Year:
Then, your program should ask the user to select from a menu of choices
using this formatting
Menu:
1) Calculate the number of days in the given month.
2) calculate the number of days left in the given year.
I would really appreciate it if someone could help me on this.

Answers
Following are the program to the given question:
Program Explanation:
Defining three methods "leap_year, number_of_days, and days_left " is declared. In the "leap_year" method, it accepts the year variable, which calculates the year is the leap year and returns its value that is 1. In the next method "number_of_days", it is define which accepts the "year and month" variable in the parameter and calculate and returns its value. In the last "days_left" method, it calculates the left days and returns its value, and outside the method, two dictionary variable days_31 and days_30 is declared. It initilized a value by using 3 input variable "day, month, and year" variable which accepts user-input value. In the next step, a "c" variable is declared, that input values and calls and print its value accordingly.Program:
def leap_year(y):#defining a method leap_year that takes one parameter
l= 0#defining l variable that holds an integer
if y % 4 == 0:#using if block that check year value module by 4 equal to 0
l = 1#holding value in l variable
if y % 100 == 0:#using if block that check year value module by 100 equal to 0
l = 0#holding value in l variable
if y % 400 == 0:#using if block that check year value module by 400 equal to 0
l= 1#holding value in l variable
return l#return l value
def number_of_days(m, y):#defining a method number_of_days that takes two parameters
months = {1: 31, 3: 31, 4: 30, 5: 31, 6: 30, 7: 31, 8: 31, 9: 30, 10: 31, 11: 30, 12: 31}#defining months variable that hold value in ictionary
l = leap_year(y)#defining l variable that calls leap_year method and holds its value
if l == 1 and m == 2:#use if that check l value equal to 1 and 2
return 29#return value 29
if m == 2:#use if that check month value equal to 2
return 28#return value 29
return months[m]#return months value
def days_left(d, m, y):#defining a method days_left that takes three variable in parameter
l = leap_year(y)#defining l variable that hold leap_year method value
days = 0#defining days variable that hold integer value
months = {1: 31, 3: 31, 4: 30, 5: 31, 6: 30, 7: 31, 8: 31, 9: 30, 10: 31, 11: 30, 12: 31}#defining months variable that hold value in ictionary
if l== 1:#using if that check l equal to 1
if m > 2:#defining if that check m value greater than 2
days += (29 + 31)#using days variable that Calculate holds its value
i = m#defining i variable that holds months value
while i > 2:#defining while loop that checks other days
days += months[i]#defining a days variable that holds months value
i -= 1#decreasing i value
days -= (months[m] - d)#defining days that subtracts leap value
elif m == 2:#defining elif block that checks m equal to 2
days += (29 - d) + 31#holding value in days variable
else:#defining else block
days = 31 - d#Calculating days value
return 366 - days#using return keyword that Calculates days value
else:#defining else block
if m > 2:#using if that checks m value greater than 2
days += (28 + 31)#Calculating and store value in days
i = m#holding months value in i
while i > 2:#defining while loop that checks i value greater than 2
days += months[i]#holding list value in days
i -= 1#decreasing i value
days -= (months[m] - d)#defining days that subtracts leap value
elif m == 2:#using elif block that checks m value equal to 2
days += (28 - d) + 31#Calculating and store value in days
else:#defining else block
days = 31 - d##Calculating and store value in days
return 365 - days#return total days
print("Please enter a date")#print message
day = int(input("Day: "))#input value
month = int(input("Month: "))#input value
year = int(input("Year: "))#input value
print("Menu: ")#print message
print("1) Calculate the number of days in the given month.")#print message
print("2) Calculate the number of days left in the given year.")#print message
c = int(input())#input value
if c == 1:#using if that checks c value equal to 1
print(number_of_days(month, year))#calling method and print its return value
elif c == 2:#using if that checks c value equal to 2
print(days_left(day, month, year))#calling method and print its return value
Output:
Please find the attached file.
Learn more:
brainly.com/question/16728668
quick question;
In two to three sentences, describe how a business can benefit from data mining.
Answers
A company could benefit from data mining finding valuables in said data. They could use it to earn bitcoin which can be cashed out. Also they can find hidden items unreleased in files.
hope this helps! :D
Why do you need to install application program/software in your computer?
Answers
Answer:
Also called a "setup program" or "installer," it is software that prepares an application (software package) to run in the computer. Unless the application is a single function utility program, it is made up of many individual files that are often stored in several levels of folders in the user's computer.
Explanation:
Answer:
Why should you install operating system (OS) and software updates? Updates are "patches" that fix problems in your operating system (the basic program that runs your computer) or in applications and programs that you use. Unpatched computers are especially vulnerable to viruses and hackers.
Explanation:
write 3 different functions in c to create an array of 10 integers on the heap without causing a memory leak. hint: you will need to assign the address to a pointer that was created outside the function. remember, you can return an address or change what a pointer points to (the contents of a pointer) in a function by passing the pointer by reference or by passing the address of the pointer.
Answers
In order to prevent memory leaks, it is a good idea to write the free() statement right after the malloc() or calloc() method.
What procedure can be applied to prevent a memory leak? In order to prevent memory leaks, it is a good idea to write the free() statement right after the malloc() or calloc() method.To prevent dangling pointers, the free() statement should be followed by assigning NULL to the pointer variable.There are a few causes of memory leaks in C/C++:When the pointer loses its initial allocated value in C/C++ programming, a memory leak typically happens.Due to the allocated object's unavailability and inability to be deallocated, it becomes the source of the memory leak.Memory Leakage Factors.Using Unwanted Object Reference: These are object references that are no longer required.The garbage collector was unable to free up the memory because another object was still making references to the undesired object.Using long-lived static objects causes a memory leak as well.To learn more about memory leaks refer
https://brainly.com/question/30052440
#SPJ4
what is the term for sending emails that imitate legitimate companies?
Answers
Answer:
phishing,,,, it imitates the company email so that when you get on the mail it can collect all your data and then can begin to hack using your information such as password
Phishing refers to the malicious attack method by attackers who imitate legitimate companies in sending emails in order to entice people to share their passwords, credit card or other sensitive personal information. ... If you do surrender such information, the attacker will immediately capture your personal information.
5 functions of an operating system
Answers
Answer:
1. Memory Management: Managing primary and secondary memory, allocating and deallocating memory, and organizing how data is stored in memory.
2. Processor Management: Managing the processor, coordination of multiple processors, and scheduling tasks.
3. Device Management: Managing input/output devices such as printers, keyboards, and disks.
4. File Management: Creating, viewing, and managing files, as well as organizing data into folders.
5. Security Management: Enforcing security protocols, preventing unauthorized access, and implementing user authentication.
Explanation:
who like the videos where is clown is from :)

Answers
Answer:
i hate clowns alot especially pennywise lol
Explanation: