Hi;
I need to build a darts scoring app for an assignment in Java
language
Can anyone help?
The game needs to ask for 2 players names, and then let each
player have a turn to throw. the game needs to
Answers
To develop a darts scoring app, keep the classes modular so that they can be modified easily if required. One can follow the below-given steps:
STEP 1: Ask for the names of the two players by prompting each player to enter their names. Save the entered names for use in scoring the game. In Java, a Scanner class can be used to prompt the user to input data.
STEP 2: Develop a scoring class that is responsible for keeping track of each player's score and providing a mechanism for reducing the score as darts are thrown. This class should have the following methods:
a. Reduce score
b. Is bust?
c. Is winner?
STEP 3: Build the Game class that should maintain the game's state, such as keeping track of each player's turn and the number of legs played so far. The Game class should have methods like:
a. Start game
b. Switch players
c. End leg
STEP 4: Create a Player class, which should be used to keep track of the player's name, score, and total number of legs won. The Player class should have methods like:
a. Get name
b. Get score
c. Get legs
d. Get winner
STEP 5: Now that the classes have been built, the Main class should be used to bring them together. Create the main function and call the methods from other classes, such as Game, Player, and Scoring, to execute the app. If the player types 'x' to quit the game, the application should stop. Use Inheritance to extend the Game class to the Player class, as it is required in the problem statement. Also, try to keep the classes modular so that they can be modified easily if required. This is how one can build a darts scoring app in Java programming language.
Learn more about Scanner class here:
https://brainly.com/question/30023269
#SPJ11
The question provided does not cover everything. Here is your full query:
Below are the instructions to build a darts scoring app for an assignment in Java language:
The game needs to ask for 2 players names, and then let each player have a turn to throw. the game needs to count 501 down to zero, but a player can only win if he finishes his last score to match zero, otherwise the score is a bust if it goes past zero. the game should ask to select best of any amount of legs to play, for example best of 13 legs and player can type x to quit the game. It should also contain classes like Main, Game, player, scoring class etc, inheritance or implements can be used
Related Questions
typically provide students with a general understanding of information technology, including computer platform technologies, data management systems, and basic programming. A Master Degree programs B Cisco degree programs C Associate degree programs D CertaPort degree programs
Answers
Answer:
the correct answer is ''associate degree programs"
Explanation:
because i took the test and got this answer right. hope this helps :)
by how much will the effort increase if MA become 4
Answers
Answer:
The Salton Sea is a shallow, saline, endorheic rift lake on the San Andreas Fault at the southern end of the U.S. state of California. It lies between, and within, the Imperial and Coachella valleys, all of which lie within the larger Salton Trough, a pull-apart basin that stretches to the Gulf of California in Mexico. The lake occupies the lowest elevations of the trough, known as the Salton Sink, where the lake surface is 236.0 ft (71.9 m) below sea level as of January 2018.[1] The deepest point of the lake is only 5 ft (1.5 m) higher than the lowest point of Death Valley. The New, Whitewater, and Alamo rivers, combined with agricultural runoff, are the primary sources that feed the lake.
Over millions of years, the Colorado River has flowed into the Imperial Valley and deposited alluvium (soil) creating fertile farmland, building up the terrain and constantly moving its main (or only) river delta. For thousands of years, the river has alternately flowed into and out of the valley, alternately creating a freshwater lake, an increasingly saline lake, and a dry desert basin, depending on river flows and the balance between inflow and evaporative loss. The cycle of filling has been about every 400–500 years and has repeated many times.
One such most notable instance took place around 700 AD – great flows of water into the basin, creating Lake Cahuilla, which at its peak was 115 miles (185 km) long, 35 miles (56 km) wide, and 314 feet (96 m) deep, making it one of the largest lakes in North America. This watering of the basin, during extended severe drought, benefited hunter-gatherers who lived there: although the water was too saline to drink, its presence attracted fish and waterfowl to the area.[2] The lake existed for over 600 years until the intake silted up, leaving a closed basin that dried up in around 50 years.
The latest natural cycle occurred around 1600–1700 AD, according to Native Americans who spoke with the first European settlers. Fish traps still exist at many locations, and the Native Americans evidently moved the traps depending upon the cycle.
The inflow of water from the now heavily controlled Colorado River was accidentally created by the engineers of the California Development Company in 1905. To provide water to the Imperial Valley for farming, beginning in 1900, an irrigation canal was dug from the Colorado River to the old Alamo River channel, directing the water west and then north near Mexicali. The headgates and canals suffered silt buildup, so a series of cuts were made in the bank of the Colorado River to further increase the water flow. The resulting outflow overwhelmed the third intake, "Mexican Cut", near Yuma, Arizona, and the river flowed into the Salton Basin for two years, filling what was then a dry lake bed and creating the modern sea, before repairs were completed.[3][4][5]
While it varies in dimensions and area with fluctuations in agricultural runoff and rainfall, the Salton Sea is about 15 by 35 miles (24 by 56 km). With an estimated surface area of 343 square miles (890 km2) or 350 square miles (910 km2), the Salton Sea is the largest lake in California by surface area.[6][7][8] The average annual inflow is less than 1.2 million acre⋅ft (1.5 km3), which is enough to maintain a maximum depth of 43 feet (13 m) and a total volume of about 6 million acre⋅ft (7.4 km3). However, due to changes in water apportionments agreed upon for the Colorado River under the Quantification Settlement Agreement of 2003, the surface area of the sea is expected to decrease by 60% between 2013 and 2021.[9][10][needs update]
The lake's salinity, about 56 grams per litre (7.5 oz/US gal), is greater than that of the Pacific Ocean (35 g/l (4.7 oz/US gal)), but less than that of the Great Salt Lake (which ranges from 50 to 270 g/l (6.7 to 36.1 oz/US gal)). The concentration has been increasing at a rate of about 3% per year.[11] About 4 million short tons (3.6 million t) of salt are deposited in the valley each year.[12]
Explanation:
mark as brainliest
in a spreadsheet program how is data organized quizlet
Answers
In a spreadsheet program, data is organized into rows and columns, forming cells where individual pieces of data can be entered.
These cells can be formatted to contain various types of data, such as numbers, dates, and text. The data can then be manipulated and analyzed using formulas and functions within the program. Additionally, the program may allow for sorting and filtering of the data based on certain criteria. Overall, the spreadsheet program provides a structured and organized way to store and analyze data.
Learn more about spreadsheet:https://brainly.com/question/26919847
#SPJ11
the use of which method would be most effective as the first line of defense in providing data protection from entry by outsiders?
Answers
The most effective method as the first line of defense in providing data protection from entry by outsiders is the use of strong access controls, such as passwords and two-factor authentication, or firewall.
A firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. It acts as a barrier between a private internal network and external networks such as the Internet. It establishes a barrier between a trusted, secure internal network and another network, usually an untrusted, insecure external network such as the internet. Firewalls are the first line of defense against unauthorized access to computer systems and are therefore essential for protecting data from entry by outsiders.
Learn more about data protection: https://brainly.com/question/27034337
#SPJ11
an snmp ____ is a simple message providing status information about the monitored device.
Answers
An SNMP "trap" is a simple message providing status information about the monitored device. A trap is sent by the SNMP agent to the network management system (NMS) to notify it about specific events or issues occurring in the device, allowing the NMS to take appropriate action or track the device's performance.
Learn more about SNMP: https://brainly.com/question/14553493
#SPJ11
Which two of these are functions of the power supply? Choose all answers that are
correct.
increase the voltage
convert DC to AC
convert AC to DC
decrease the voltage
Answers
Answer:
AC to DC
Explanation: Heres Why
your power supply is what converts AC to DC
Effective planning for information security involves:a.collecting information about an organization's objectives.b.collecting information about an organization's information security environment.c.collecting information about an organization's technical architecture.d.All of the above
Answers
The answer to the question is Option (d). The choices listed above are all accurate.
How do you define organization?An group is a collection of people who interact, such as a firm, homeowners association, charity, or labor. The term "organization" can be used to describe a person, a group, a company, or the process of creating or developing anything.
What are 3 types of organization?The organisations utilized by the majority of organizations today can be divided into three types functional, departmental, and matrix. Before choosing which of these forms to use for their company, owners must assess the benefits and drawbacks of each.
To know more about organization visit :
brainly.com/question/12825206
#SPJ4
Effective planning for information security involves collecting information about an organization's objectives, collecting information about an organization's information security environment, and collecting information about an organization's technical architecture.
Thus option D is correct.
Here,
1. Collecting information about an organization's objectives:
In order to effectively plan for information security, it is important to understand the goals and objectives of the organization. This includes understanding what the organization wants to achieve, its priorities, and its long-term plans.
2. Collecting information about an organization's information security environment:
Understanding the information security environment of an organization is crucial for effective planning. This includes assessing the current security measures in place, identifying any vulnerabilities or weaknesses, and evaluating the overall security posture of the organization.
3. Collecting information about an organization's technical architecture:
The technical architecture of an organization refers to the infrastructure, systems, and technologies used to support its operations. This includes hardware, software, networks, and data storage systems.
Collecting information about the technical architecture is essential for planning information security because it allows organizations to assess the security controls in place, identify any gaps or vulnerabilities in the infrastructure, and determine the best strategies to protect critical assets and data.
Therefore, effective planning for information security involves collecting information about an organization's objectives, information security environment, and technical architecture.
Thus option D is correct.
Know more about effective planning,
https://brainly.com/question/11228483
#SPJ6
Some SPICY memes anyone?
Answers
Answer: LoL
Explanation: THIS IS FUNNY!

Answer:
I gotta spicy memes
Explanation:

Nia would like to learn the basics of how to write a computer program. Which of the following languages is often used in schools and teaches students important programming concepts?
A. Java
B. Python
C. HTML
D. Block-based
Answers
Answer:
Block-based
Explanation:
Usually Block-based is used in schools because it doesn't really require any coding experience and is just drag-and-drop.
free ten points,, it would be batter if you answered though
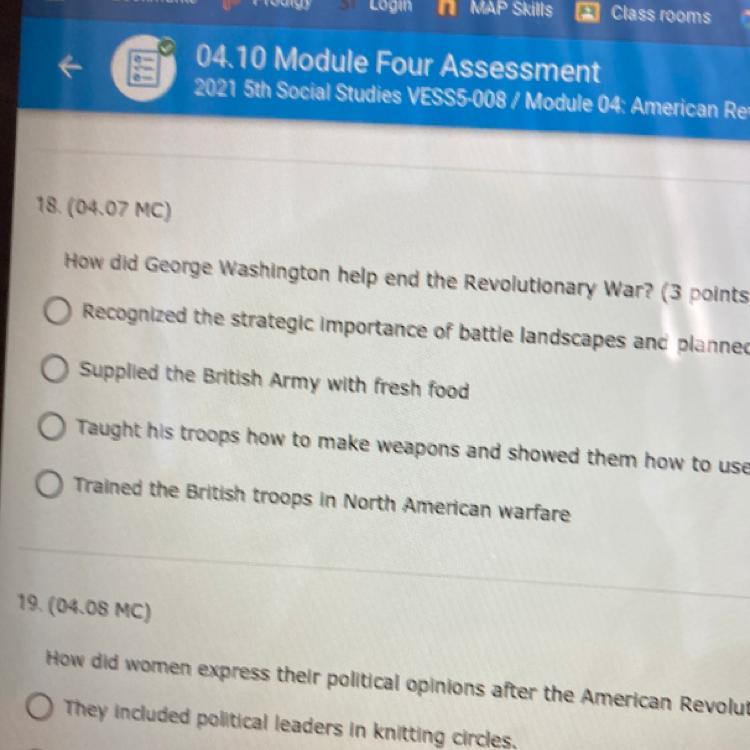
Answers
Answer:
I think A
Explanation:
Answer:
I think it's A
Hope it helps :D
In order to animate a parameter in the effect control tab, one must first click the:
Answers
In order to animate a parameter in the Effect Controls tab of Adobe Premiere Pro, one must first click on the stopwatch icon next to the parameter name.
This will activate keyframe animation for that parameter, allowing you to create changes over time.
Once the stopwatch icon is clicked, a keyframe will appear at the current time indicator (CTI) on the timeline. You can then move the CTI to a different point in time, adjust the value of the parameter, and add another keyframe. Premiere Pro will automatically interpolate between the two keyframes to create a smooth transition from one value to the next over time.
You can continue adding keyframes and adjusting parameters to create complex animations. And if you ever want to remove a keyframe, simply select it on the timeline and press the Delete key.
Animating parameters in Premiere Pro's Effect Controls tab allows you to create dynamic visual effects, transitions, and motion graphics that can enhance the production value of your video projects.
Learn more about Adobe here:
https://brainly.com/question/31044840
#SPJ11
What is required before securing the car
Answers
Answer:
Seatbelt
Explanation:
9) WAp to display the given series
1 2
1 2 3
1 2 3 4
1 2 3 4 5
Answers
The program that displays the given series is exemplified below. Also, see the meaning of Java.
What is Java?Java is a class-based, object-oriented general-purpose programming language.
The programming language is designed so that developers may write code anywhere and run it anywhere, regardless of the underlying computer architecture.
It is also known as write once, run anywhere (WORA)
Sample program:
public class KboatPattern
{
public static void main(String args[]) {
for (int i = 1; i <= 5; i++) {
for (int j = i; j >= 1; j--) {
System.out.print(j + " ");
}
System.out.println();
}
}
}
Learn more about Java at;
https://brainly.com/question/26642771
#SPJ1
when evaluating patients’ profile, surgeons usually note the lack of the chin projection and may suggest chin augmentation, but they rarely discuss reduction of an over-projecting chin. this is unfortunate, since there are quite many individuals who have macrogenia and would aesthetically benefit from corrective surgery, but the chin reduction is seldom offered. the reason for this is the lack of experience, lack of the technical equipment necessary, or sometimes lack of knowledge. the present study conveys 25 years of experience with the reduction genioplasty.
Answers
Surgeons often focus on chin augmentation when evaluating patients' profiles, but they rarely discuss the possibility of reducing an over-projecting chin. This is unfortunate because there are many individuals who have macrogenia, or an over-projecting chin, and would benefit from corrective surgery.
However, a present study has conveyed 25 years of experience with reduction genioplasty, which is the surgical procedure used to reduce the size or projection of the chin. This study aims to address the aesthetic concerns of individuals with macrogenia by offering chin reduction surgery as a potential solution.
By introducing chin reduction as a viable option, surgeons can provide comprehensive care to patients with different chin profiles, offering them the opportunity to achieve their desired aesthetic outcomes. This procedure involves reshaping the chin bone and possibly adjusting the soft tissues surrounding the chin to achieve a more balanced facial appearance.
To know more about augmentation visit:
brainly.com/question/13241481
#SPJ11
Graphical elements called ____ can be placed on a Windows Form object when you are designing the user interface.
Answers
Graphical elements called controls can be placed on a Windows Form object when designing the user interface.
When designing the user interface in Windows Forms, you can add graphical elements called controls to a Form object. Controls are visual components that allow users to interact with the application. They provide various functionalities such as displaying text, accepting user input, and triggering events.
There are different types of controls available in Windows Forms, including buttons, labels, text boxes, checkboxes, radio buttons, list boxes, and many more. These controls can be dragged and dropped onto the Form object in a visual design environment like Visual Studio.
Once placed on the Form, you can customize the appearance and behavior of the controls using properties and events. Properties define the characteristics of the control, such as its size, position, color, and text. Events, on the other hand, allow you to respond to user actions, such as button clicks or text input.
By placing and configuring these controls on a Windows Form, you can create a visually appealing and interactive user interface for your application.
Learn more about Windows Form object here:
https://brainly.com/question/32653842
#SPJ11
If, in a recursive solution, function A calls function B which calls function C, this is called ________ recursion. indirect three function call direct continuous
Answers
If, in a recursive solution, function A calls function B which calls function C, this is called Indirect recursion.
A recursive algorithm is said to be recursive if such an algorithm calls itself with smaller input values and get current result for implementing basic operations on those simple inputs.
Indirect recursion occurs when a function A invokes another function B which in turn makes it the original function and calls another function C.
Learn more about recursion here:
https://brainly.com/question/3169485?referrer=searchResults
Select all statements from the given choices that are the negation of the statement:
Michael's PC runs Linux.
Select one or more:
a. It is not true that Michael's PC runs Linux.
b. It is not the case that Michael's PC runs Linux.
c. None of these
d. Michael's PC runs Mac OS software.
e. Michael's PC runs Mac OS software and windows.
f. It is false that Michael's PC runs Linux.
g. Michael's PC doesn't run Linux.
h. Michael's PC runs Mac OS software or windows.
i. Michael's PC runs Windows
Answers
The statements that are the negation of "Michael's PC runs Linux" are: a. It is not true that Michael's PC runs Linux. b. It is not the case that Michael's PC runs Linux. d. Michael's PC runs Mac OS software. e. Michael's PC runs Mac OS software and windows. f. It is false that Michael's PC runs Linux. g. Michael's PC doesn't run Linux. h. Michael's PC runs Mac OS software or windows. i. Michael's PC runs Windows.
The negation of a statement is the opposite or contradictory statement. In this case, the statement "Michael's PC runs Linux" can be negated in multiple ways.
Options a, b, f, and g all express the negation by denying the truth of the original statement. Option d states that Michael's PC runs Mac OS software, which contradicts the statement that it runs Linux. Option e extends the negation by adding the condition that Michael's PC runs both Mac OS software and Windows, further diverging from the original statement. Option h also offers a contradictory statement by stating that Michael's PC runs either Mac OS software or Windows, but not Linux. Finally, option i simply states that Michael's PC runs Windows, which excludes Linux.
In summary, options a, b, d, e, f, g, h, and i all provide statements that negate the original claim that Michael's PC runs Linux.
Learn more about software.
brainly.com/question/32393976
#SPJ11
in the relational data model associations between tables are defined through the use of primary keys
Answers
In the relational data model, associations between tables are defined through the use of primary keys. The primary key in a relational database is a column or combination of columns that uniquely identifies each row in a table.
A primary key is used to establish a relationship between tables in a relational database. It serves as a link between two tables, allowing data to be queried and manipulated in a meaningful way. The primary key is used to identify a specific record in a table, and it can be used to search for and retrieve data from the table. The primary key is also used to enforce referential integrity between tables.
Referential integrity ensures that data in one table is related to data in another table in a consistent and meaningful way. If a primary key is changed or deleted, the corresponding data in any related tables will also be changed or deleted. This helps to maintain data consistency and accuracy across the database. In conclusion, primary keys are an important component of the relational data model, and they play a critical role in establishing relationships between tables and enforcing referential integrity.
To know more about database visit:
https://brainly.com/question/30163202
#SPJ11
add a viewport tag with user-scalable set to no, width set to device-width, and initial-scale set to 1.
Answers
To add a viewport tag with specific attributes, you can simply include the following line of code within the head section of your HTML document:
This will ensure that the viewport is set to the width of the device and that the initial scale is set to 1, preventing any unwanted zooming on mobile devices. Additionally, the user-scalable attribute is set to "no," which will disable any zooming functionality that may be present on certain mobile devices.
Overall, including a viewport tag in your HTML is an important aspect of responsive web design, as it helps to ensure that your website looks and functions correctly on all devices. By setting the width and scale attributes, you can control how your website is displayed on different screen sizes and prevent any unwanted behavior.
To know more about HTML visit :
https://brainly.com/question/15093505
#SPJ11
T/FIt is common practice to reserve memory in amount equal to 20 percent of the physical server memory for the exclusive use of the hypervisor.
Answers
True.It is common practice to reserve a portion of the physical server's memory, typically around 20 percent, for the hypervisor to ensure efficient virtual machine management and performance.
This reserved memory is not available for use by any virtual machines running on the hypervisor.It is common practice to reserve approximately 20 percent of the physical server memory for the exclusive use of the hypervisor. This helps ensure efficient virtualization and system performance.
Controlling access to hardware, including memory, is a hypervisor's main function. Each virtual machine's memory is partitioned up such that each one "sees" its memory in the same manner as a real computer does.
To know more about hypervisor visit:-
https://brainly.com/question/31257671
#SPJ11
A software development team needs to upgrade a program, but the team members are having trouble understanding the program code and how it works. What could be the reason?
a. missing prototype
b. incomplete documentation
c. unfinished system proposal
d. inadequate feasibility study
Answers
Hey there mate :)
As per question,
Question:- A software development team needs to upgrade a program, but the team members are having trouble understanding the program code and how it works. What could be the reason?
To find:- Write the correct option
Answer:- Option B. incomplete documentation
Answer per sentence:-
A software development team needs to upgrade a program, but the team members are having trouble understanding the program code and how it works. This is due to incomplete documentation.
How could a large number of hosts (with no login access) be used in a Smurf attack?
Answers
In a distributed denial-of-service (DDoS) assault known as a "Smurf," a victim's network is bombarded with ICMP echo requests (pings). A Smurf attack involves the attacker sending many ICMP messages.
How is the Smurf attack carried out?In a distributed denial-of-service (DDoS) assault known as a "Smurf," the victim's server is bombarded with fictitious Internet Control Message Protocol (ICMP) and Internet Protocol (IP) packets. The target's system is thereby made unusable. A DDoS is where this kind of attack gets its name.
How can Smurf attacks be stopped?- Setup network firewalls or specific web application firewalls to secure your servers, together with an antivirus and anti-malware solution. You might give HeimdalTM Next-Gen Endpoint Antivirus a shot.
To know more about DDoS visit:-
https://brainly.com/question/29238912
#SPJ1
Match the learning styles with the example.
Column B
Column A
a. Visual
1.
b. Auditory
2.
C. Kinesthetic
3.
Angela likes to review graphs and articles.
Which learning style do you think best matches
this student?
Helga likes to take notes and do fun activities.
Which learning style do you think best matches
this student?
Armando creates pictures to help remember his
math concepts. Which learning style do you
think best matches this student?
Hannah likes group discussions and oral
presentations from her teacher. Which learning
style do you think best matches this student?
Enjoy discussions and talking things through
and listening to others.
Benefit from illustrations and presentations,
and especially those in color.
Likes to move around a lot.
4.
5.
6
7
Answers
Answer
it would be c
Explanation:
Which key do you hold down to select a group of contiguous files?
Shift
Cntrl
File image
Answers
The key you hold down to select a group of contiguous files is the Shift key. So, the first option is correct.
When you want to select multiple files that are adjacent to each other, you can use the Shift key to make the selection process faster and more convenient.
To select a group of contiguous files using the Shift key, you follow these steps:
1. Start by clicking on the first file in the series that you want to select.
2. Hold down the Shift key on your keyboard.
3. While keeping the Shift key pressed, click on the last file in the series.
4. All the files between the first and last file you selected will now be highlighted or selected.
Using the Shift key allows you to quickly select a range of files without having to individually click on each one.
This feature is particularly useful when you have a large number of files listed consecutively and want to select them all at once.
On the other hand, the Ctrl (Control) key is used for non-contiguous or individual file selection.
With the Ctrl key, you can select multiple files one by one by clicking on each file while holding down the Ctrl key. This method is useful when the files you want to select are scattered throughout the file list.
In summary, the Shift key is used to select a group of contiguous files, while the Ctrl key is used for non-contiguous or individual file selection.
So, the first option is correct.
Learn more about files:
https://brainly.com/question/29511206
#SPJ11
Which component is likely to be a performance bottleneck on a workstation used to edit digital movies
Answers
Explanation:
The disk subsystem - the files will be too large to be stored completely in system memory and so must be streamed from the disk, which will need to be both large and fast.
uppose we have the instruction lda 800. given memory as follows: what would be loaded into the ac if the addressing mode for the operating is immediate?
Answers
If the addressing mode for the LDA operation is immediate, then the value at memory location 800 will be loaded directly into the accumulator (AC). In this case, the value at memory location 800 is 20.
In the LDA instruction with immediate addressing mode, the operand is given directly in the instruction, instead of fetching it from a specified memory location. After the execution of the instruction, the accumulator (AC) will contain the value 20. Immediate addressing mode is useful when the operand is a constant value or a small amount of data that can be easily included in the instruction. This method saves time and memory, as the processor does not need to access a memory location to obtain the operand value, making it a more efficient way to execute certain instructions..
To know more about LDA operation visit:
brainly.com/question/29999718
#SPJ11
help please hurrry asap I WILL MARK BRAINLEST
Adam has decided to add a table in a Word doc to organize the information better.
Where will he find this option?
1 Insert tab, Illustrations group
2 Insert tab, Symbols group
3 Insert tab, Tables group
4 Design tab, Page Layout group
Answers
Answer:
4) design tab, Page layout group
Explanation:
Answer:
3 insert tab, tables group
Write a program in the if statement that sets the variable hours to 10 when the flag variable minimum is set.
Answers
Answer:
I am using normally using conditions it will suit for all programming language
Explanation:
if(minimum){
hours=10
}
Which document is issued by the state real estate commissioner to help protect purchasers of subdivision plots?
Answers
Public report is a document that the state real estate commissioner issues to assist in protecting buyers of subdivision plots.
The state real estate commissioner issues a public report following application and approval to satisfy the disclosure requirements of the Subdivided Land Laws to stop fraud and misrepresentation when selling subdivided land to buyers.
The Public Report will typically include information about the applicant's name, the subdivision's location and size, utility, school, tax, management, maintenance, and operational costs, as well as any unusual easements, rights of way, setback requirements for vacant land offerings, and restrictions or conditions.
Learn more about public report https://brainly.com/question/28455254
#SPJ4
Find H.C.F of 4,5,10 by all the three methods.
Answers
Answer:
1. Factorization Method
2. Prime Factorization Method
3. Division Method