Help Quick Please!!!!
Ann sent out a business letter three weeks ago, hoping to increase sales. However, she has not seen an increase. She thinks that making the communication more impressive will increase the business. Ann should _____.
Answers
Related Questions
1. Using the open function in python, read the file info.txt. You should use try/except for error handling. If the file is not found, show a message that says "File not found"
2. Read the data from the file using readlines method. Make sure to close the file after reading it
3. Take the data and place it into a list. The data in the list will look like the list below
['ankylosaurus\n', 'carnotaurus\n', 'spinosaurus\n', 'mosasaurus\n', ]
5. Create a function called modify_animal_names(list) and uppercase the first letter of each word.
6. Create a function called find_replace_name(list, name) that finds the word "Mosasaurus" and replace it with your name. DO NOT use the replace function. Do this manually by looping (for loop).
The words in the info.text:
ankylosaurus
carnotaurus
spinosaurus
mosasaurus
Answers
try:
f = open('info.txt', 'r')
except:
print('File not found')
dino_list = []
for line in f.readlines():
dino_list.append(line)
f.close()
def modify_animal_names(list):
for i in range(len(list)):
list[i] = list[i].capitalize().replace('\n', '')
modify_animal_names(dino_list)
def find_replace_name(list, name):
for i in range(len(list)):
if list[i] == name:
list[i] = 'NAME'
find_replace_name(dino_list, 'Ankylosaurus')
This will print out:
['Ankylosaurus', 'Carnotaurus', 'Spinosaurus', 'NAME']
(If you have any more questions, feel free to message me back)
In order to protect your computer from the newest virues which of the following should you do after you installed virus scan software
Answers
In order to protect your computer from the newest viruses, you should update the antivirus software and virus definition on a regular basis.
What is a virus?A virus can be defined as a malicious software program that moves through computer networks and the operating systems (OS) installed on a computer (host), specifically by attaching themselves to different software programs, links and databases.
This ultimately implies that, you should update the antivirus software and virus definition on a regular basis, so as to protect your computer from the newest viruses.
Read more on a virus here: brainly.com/question/26128220
#SPJ1
In a team if someone gets stuck with the selected tasks for the iteration, what is the immediate next step?
Answers
Answer:
The team member has to immediately inform the lead or onsite coordinator without wasting time and take up another task
Explanation:
In a situation where someone in a team is unable to move further to another tasks the next step is for the team member to immediately inform the onsite coordinator in order for them to take up another task reason been that the onsite coordinator sole responsibility is to ensure the completion of tasks without any flaw and Secondly if the team members did not inform the onsite coordinator immediately it will eventually lead to waste of time due to the time spent on the tasks thereby affecting the next tasks.
Therefore the immediate next step is for the team member to immediately inform the lead or onsite coordinator without wasting time and take up another task.
Most of the devices on the network are connected to least two other nodes or processing
centers. Which type of network topology is being described?
bus
data
mesh
star
Answers
Read and Answer the Question.
After several years of driving long-haul trucks, Joe Blanka
founded his own trucking company, Blanka Transport Inc.
(BTI), which specialized in less-than-truckload shipments in the
midwestern part of the United States. Joe developed a successful
method for scheduling BTI’s runs that met or exceeded the
delivery expectations of its customers. As a result, BTI shipments were growing at a rate between 15 and 20 percent per
year. The growth, however, was not evenly distributed across
BTI’s territory. On some routes, capacity was overloaded in one
direction and underloaded in the other.
Joe noticed that the imbalance problem was not stable
across time. In some months, capacity was short in one direction, and in other months, it was short in another direction. He
thought that one way of solving the problem would be through
marketing, by offering incentives to customers whose shipments
would improve load balance. Another approach to the problem
was to analyze and restructure the route–equipment combinations. He also thought that it might be possible to warehouse
some less-urgent shipments for short periods in order to help
the balance.
Joe’s son, the first member of the Blanka family to attend
college, was a senior in engineering school. He had just completed a course in project management, and after briefly describing some of the basic concepts to his father, he suggested that a
process improvement project might be a good way to deal with
the balance problem. He thought that the Marketing Manager
and the Route Manager could serve as project co-managers. He
also felt that some of the older, more experienced drivers might
be helpful. The objective of the project would be to decrease the
size of the route imbalances by 75 percent in 1 year.
Questions: Is this a proper approach to the problem? Is this a “project”; if
so, what are the three triple constraints? What, if any, helpful
suggestions would you make to Joe?
Answers
Yes, the process improvement project suggested by Joe's son is a proper approach to address the balance problem in the trucking company. It can help decrease the route imbalances by 75 percent in one year.
What are the constraints?The three triple constraints in this project would be scope (reducing route imbalances), time (1 year), and resources (including the Marketing Manager, Route Manager, and experienced drivers).
Some helpful suggestions for Joe would be to consider implementing a combination of marketing incentives, route restructuring, and short-term warehousing to achieve better load balance.
Additionally, he should ensure effective communication and collaboration between the project co-managers and team members to maximize the project's success.
Read more about project development here:
https://brainly.com/question/27995740
#SPJ1
Write a program that will prompt the user for the number of dozens (12 cookies in a dozen) that they use.
Calculate and print the cost to buy from Otis Spunkmeyer, the cost to buy from Crazy About Cookies, and which option is the least expensive (conditional statement).
There are four formulas and each is worth
Use relational operators in your formulas for the calculations. 1
Use two conditional execution (if/else if)
One for Otis cost (if dozen is less than or equal to 250 for example)
One that compares which costs less
Appropriate execution and output: print a complete sentence with correct results (see sample output below)
As always, use proper naming of your variables and correct types. 1
Comments: your name, purpose of the program and major parts of the program.
Spelling and grammar
Your algorithm flowchart or pseudocode
Pricing for Otis Spunkmeyer
Number of Dozens Cost Per Dozen
First 100 $4.59
Next 150 $3.99
Each additional dozen over 250 $3.59
Pricing for Crazy About Cookies
Each dozen cost $4.09
Answers
Python that asks the user for the quantity of dozens and figures out the price for Crazy About Cookies and Otis Spunkmeyer.
How is Otis Spunkmeyer baked?Set oven to 325 degrees Fahrenheit. Take the pre-formed cookie dough by Otis Spunkmeyer out of the freezer. On a cookie sheet that has not been greased, space each cookie 1 1/2 inches apart. Bake for 18 to 20 minutes, or until the edges are golden (temperature and baking time may vary by oven).
Cookie Cost Calculator # Software # Author: [Your Name]
# Ask the user how many dozens there are.
"Enter the number of dozens you want to purchase:" num dozens = int
# If num dozens = 100, calculate the cost for Otis Spunkmeyer:
If num dozens is greater than 250, otis cost is equal to 100. otis cost = 100 if *4.59 + (num dozens - 100)*3.99 (num dozens - 250) * 4.59 * 150 * 3.99 * 3.59
# Determine the price for Crazy About Cookies
insane price equals num dozens * 4.09 # Choose the more affordable choice if otis cost > crazy cost:
(otis cost, num dozens) print("Buying from Otis Spunkmeyer is cheaper at $%.2f for%d dozens.")
If not, print ((crazy cost, num dozens)) "Buying from Crazy About Cookies is cheaper at $%.2f for%d dozens."
To know more about Python visit:-
https://brainly.com/question/30427047
#SPJ1
What’s the output of this code?

Answers
Answer:
1
Explanation:
console.log: mystery isn't anything necessary because it doesn't have anything to do with the code. The only option for this is 1 because the mystery says a, b and c. As this c < a & c > b gives the number 1.
Have a wonderful day! :-)
A photographer stores digital photographs on her computer. In this case the photographs are considered the data. Each photograph also includes multiple pieces of metadata including:
Date: The date the photograph was taken
Time: The time the photograph was taken
Location: The location where the photograph was taken
Device: Which camera the photo was taken with
Which of the following could the photographer NOT do based on this metadata?
Answers
Answer:D
Explanation:
Answer:
C filter photos to those taken of buildings
Explanation:
she wouldn't be able to tell which pictures are of buildings using that metadata.
Directions: Read the article about IRS and Tax Scams. Then write a well-thought-out and well-written summary of the article on page 2. To get full credit, your summary must be at least 1 paragraph. Check your punctuation - spelling & grammar counts!!!!
Every year, the bad guys take advantage of innocent taxpayers, like you, who are patiently waiting on their tax returns.
Last year, the IRS noticed a significant increase in phishing attempts to steal money or tax data, therefore you must be on high alert.
How it Happens: Tax Scams and Malicious Activity
The bad guys have a number of tax-related tricks up their sleeves when it comes to stealing your money and/or sensitive information. Here are a few examples of sophisticated tax scams that have been found in the wild:
Scammers send emails posing as tax service companies by spoofing emails and using stolen logos. Once you respond to the email with personal data or tax information, they can pocket your hard-earned money. Similar to the scam above, the bad guys send look-alike emails containing hyperlinks that lead you to malicious websites or fake PDF attachments that download malware or viruses to your computer.
Tax scams aren’t limited to emails! Be on the lookout for callers posing as IRS representatives claiming you owe money that must be paid immediately. The callers typically threaten arrests, deportation, or suspension of business or driver’s license.
Keep in mind, these are only a few examples and these scam artists are constantly coming up with new ways to fool you.
How Do I Know It's a Scam?
Always remember the following during tax season, and all year long:
The IRS will always mail a bill before calling you about taxes owed.
The IRS will never ask for credit or debit card numbers over the phone.
The IRS will never immediately threaten to arrest you for not paying taxes owed.
The IRS will always offer the opportunity to question or appeal the amount owed before demanding your payment.
The IRS does not use emails or text messages to discuss personal tax matters, such as taxes owed or tax refunds. Only share sensitive data over email when there is no other alternative and you’re certain the recipient is valid.
Answers
Answer:
ohhh okkaayyy
Explanation:
Selet the correct answer.
In the field of audio production, which recording technology was the first to make overdubbing possible?
A.
acoustic
B.
digital
C.
electrical
D.
magnetic
E.
thermal
Answers
Answer:
magnetic
Explanation:
With tapes, you can selectively overwrite parts of a recording with new content.
What special responsibilities do computer professionals have with respect to understanding and protecting the privacy rights of their fellow citizens?
Answers
Explanation:
There are ethical responsibilities that must be linked to the use of technological systems by computer professionals in relation to the protection of the privacy rights of their fellow citizens.
Exercising ethical behavior is essential for computing to be used for its central benefits, which is to make life and tasks simpler and more dynamic, and not for technical knowledge about computer science to be used for personal or other benefits. , therefore, it is ideal that there is ethical responsibility for computer professionals so that ethical decisions are taken so that knowledge is used for the benefit of society and not to commit illegal acts.
Functions of a DVD in computer
Answers
DVD is a digital optical disc storage format that are commonly used to store large amounts of data, such as high-quality videos and movies. A DVD-ROM drive and DVD player software are required to read and play DVDs on a computer.
What exactly is a DVD?
DVD (digital video disc) is an optical data storage technology similar to compact disc (CD). Optical data storage is a technique that stores digital information (1's and 0's) by reading the information with light.
A DVD movie is depicted in the image of the Matrix DVD movie disc. It is also where the operating system is kept. In 1995, four companies named Philips, Sony, Toshiba, and Panasonic invented and developed it. The first DVD-ROM drives that used these discs were sold in 1997.
To learn more about DVD
https://brainly.com/question/26223221
#SPJ9
Write a program that calculates an adult's fat-burning heart rate, which is 70% of 220 minus the person's age. Complete fat_burning_heart_rate() to calculate the fat burning heart rate. The adult's age must be between the ages of 18 and 75 inclusive. If the age entered is not in this range, raise a ValueError exception in get_age() with the message "Invalid age." Handle the exception in __main__ and print the ValueError message along with "Could not calculate heart rate info."
Answers
Answer:
bwhwbw ebsbs s shsjsb ebsbsbe ebsbebe
Explanation:
nsbs shsjs sbjs sbsjs sbdjd ebdjee bdjd dbdbd d d
sksknd djdjs djdjd edbd dd
skdjd. djsd d
The following table describes the required fields for two classes and typical values stored in those fields.
You are required to create a base class Printer and its child class PrinterCumScanner. Each of these classes should have user defined constructor and overridden Display() method so that the following test driver can work properly.
Answers
Answer:
hope this helps,if it did pls mark my ans as brainliest
Explanation:
using System;
class Printer{ string companyName; int pagesOutput;
double price;
public Printer(string companyName,int pagesOutput,double price){
this.companyName=companyName; this.pagesOutput=pagesOutput; this.price=price;
}
public virtual void Display(){ Console.WriteLine("companyName: "+companyName+" pagesOutput: "+pagesOutput+" price: "+price);
}
}
class PrinterCumScanner:Printer{ int imageDpi;
public PrinterCumScanner(string companyName,int pagesOutput,double price,int imageDpi):base(companyName,pagesOutput,price){ this.imageDpi=imageDpi; }
public override void Display(){ base.Display(); Console.WriteLine("imageDpi: "+imageDpi);
}
}
public class Program { static void Main(string[] args) { const int NUM_PRINTERS=3;
Printer []stock=new Printer[NUM_PRINTERS];
stock[0]=new Printer("HP",40,89.50);
stock[1]=new PrinterCumScanner("HP",40,215.0,320); stock[2]=new PrinterCumScanner("Cannon",30,175.0,240);
foreach(Printer aPrinter in stock){ aPrinter.Display();
}
}
}
Can I please get an answer, it's for computer science.

Answers
Answer:
I believe the answer would be B. C. and D. A, wouldnt make sense, as GitHub doesn't have that as a feature. I hope this helps! :)
Answer:
ok im not 100% sure this is right but i also don't pay attention in any of my classes except music so i would maybe say options D,B, and A
Explanation:
The purpose of post market surveillance is to make regulation more effective and recalls easier
True or false
Answers
Answer:True
Explanation:
The purpose of post-market surveillance is to make regulation more effective and recalls easier. Post-market surveillance plays a crucial role in monitoring the safety and effectiveness of products after they have been approved and made available in the market. It helps regulatory authorities identify and address any issues or risks associated with the product's use, leading to more effective regulation. Additionally, by monitoring products in the market, post-market surveillance facilitates the identification of potential problems, which can make recalls easier if necessary to protect public health and safety.
QUESTION 11
Which expression for YYY will result in an output of "Pass" only if x is exactly 32?
if YYY:
print('Pass')
else:
print('Fail')
a. x != 32
b.x == 32
OC. x >= 32
d. x <= 32
Answers
Answer:
x == 32
Explanation:
CODE in Java:
int x = 32;
if(x == 32){
System.out.println("Pass");
}
else{
System.out.println("Fail");
}
OUTPUT:
Pass
LANGUAGE IS PYTHON PLEASE HELP.
Write a while loop that repeats while user_num ≥ 1. In each loop iteration, divide user_num by 2, then print user_num.
Sample output with input: 20
10.0
5.0
2.5
1.25
0.625
Answers
a study was sponsored by an organization dedicated to the health and well-being of domesticated canines and felines. for the study, a large pet store chain distributed surveys to a random sampling of customers. one of the questions asked people how many cats and dogs they had. the results of a sample of 32 answers are included below. create the dot plot of the dataset using excel, and then interpret the plot. choose the correct answer below. number of cats and dogs 2 2 2 1 1 2 2 2 3 helpcopy to clipboarddownload csv select the correct answer below: the dot plot shows an approximately symmetric distribution with a median of 2 and a mode of 2, indicating that most customers of the pet store cluster around having 2 cats or dogs. the dot plot shows a right-skewed distribution with a median of 2 and a mode of 2, indicating that while most customers of the pet store cluster around having 2 cats or dogs, some customers have a large amount of cats or dogs. the dot plot shows a left-skewed distribution with a median of 2 and a mode of 2, indicating that while most customers of the pet store cluster around having 2 cats or dogs, some customers have no cats or dogs. the dot plot shows a bi-modal distribution with a median of 2 and two modes, 0 and 4. this indicates that the customers of the pet store tend to have either very few pets or a large amount of pets.
Answers
The dot plot displays a roughly symmetric distribution with a median and mode of 2, indicating that the majority of the pet store's clients are most likely to own two cats or dogs each.
How to these instructions to create a dot plot in Excel?A large pet store chain distributed surveys to a random sampling of customers.
1. Launch Excel and enter the information in column A, beginning at A1.
2. Enter "=COUNTIF($A$2:$A2,A2)" in cell B2.
3. To each cell below B2 that is next to the information in column A, copy B2 and paste it there. This tracks the number of times each value appears in the dataset.
4. Make a scatter plot with a vertical axis for the count and a horizontal axis for the values.
Count an equal number of dots from the left and right sides to get the median, then locate that dot. If there are two middle dots, their values should be averaged. The position(s) on the horizontal axis of the tallest column of dots is/are the mode(s).The middle dot for the dataset supplied is above 2. Consequently, 2 is the median. Above 2, there are 14 dots in the highest dot column. Consequently, the mode is 2.The distribution is roughly symmetric since the length of the right and left tails of the distribution are equal. This demonstrates that the majority of the pet store's customers cluster around owning two cats or dogs.To learn more about random sampling refer to:
https://brainly.com/question/14604186
#SPJ4
1.Create a function that accepts any number of numerical (int and
float) variables as positional arguments and returns the sum ofthose variables.
2.Modify the above function to accept a keyword argument
'multiplier'. Modify the function to return an additional variable
that is the product of the sum and the multiplier.
3.Modify the above function to accept an additional keyword
argument 'divisor'. Modify the function to return an additional
variable that is the quotient of the sum and the divisor.
Answers
Answer:
This function accepts any number of numerical variables as positional arguments and returns their sum:
python
Copy code
def sum_numbers(*args):
return sum(args)
This function accepts a multiplier keyword argument and returns the product of the sum and the multiplier:
python
Copy code
def sum_numbers(*args, multiplier=1):
total_sum = sum(args)
return total_sum * multiplier
This function accepts an additional divisor keyword argument and returns the quotient of the sum and the divisor:
python
Copy code
def sum_numbers(*args, multiplier=1, divisor=1):
total_sum = sum(args)
return total_sum * multiplier, total_sum / divisor
You can call these functions with any number of numerical arguments and specify the multiplier and divisor keyword arguments as needed. Here are some examples:
python
# Example 1
print(sum_numbers(1, 2, 3)) # Output: 6
# Example 2
print(sum_numbers(1, 2, 3, multiplier=2)) # Output: 12
# Example 3
print(sum_numbers(1, 2, 3, multiplier=2, divisor=4)) # Output: (8, 3.0)
For each of the descriptions below, perform the following tasks:
i) Identify the degree and cardinalities of the relationship.
ii) Express the entities and the relationships with attributes in each description graphically with an E-R diagram
A piano manufacturer wants to keep track of all the pianos it makes individually. Each piano has an identifying serial number and a manufacturing completion date. Each instrument represents exactly one piano model, all of which have an identification number and a name. In addition, the company wants to maintain information about the designer of the model. Over time, the company often manufactures thousands of pianos of a certain model, and the model design is specified before any single piano exists. (20p)
A piano manufacturer (see (e) above) employs piano technicians who are responsible for inspecting the instruments before they are shipped to the customers. Each piano is inspected by at least two technicians (identified by their employee number). For each separate inspection, the company needs to record its date and a quality evaluation grade. (14p)
The piano technicians (see (f) above) have a hierarchy of reporting relationships: some of them have supervisory responsibilities in addition to their inspection role and have multiple other technicians report to them. The supervisors themselves report to the chief technician of the company. (10p)
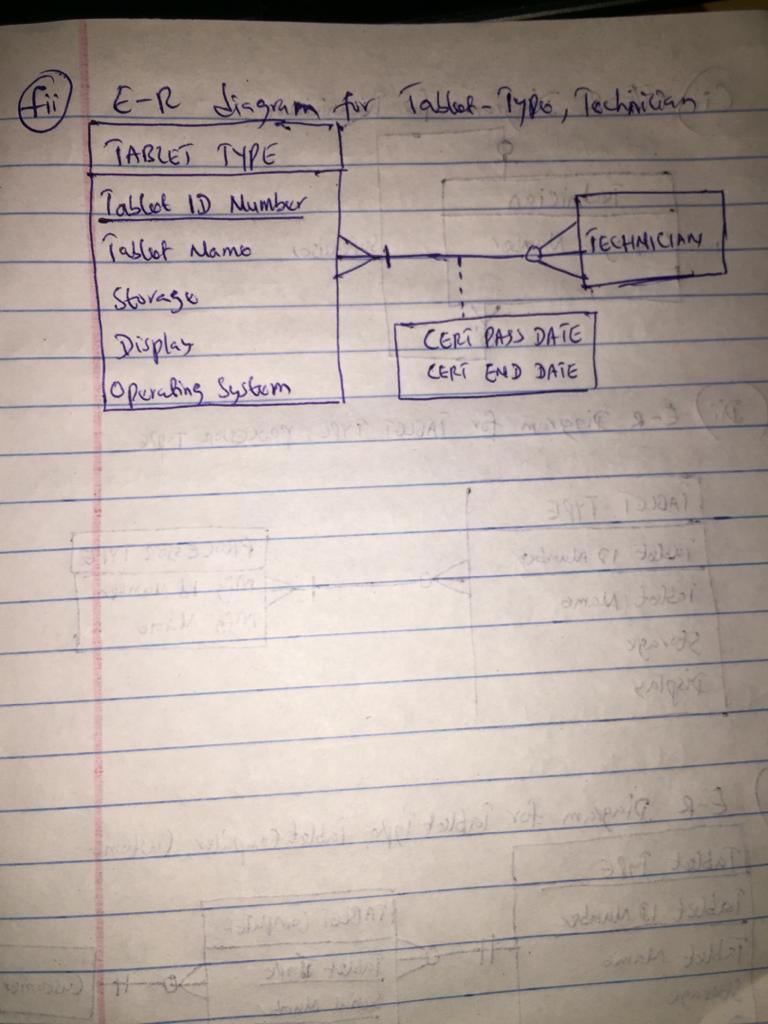
A vendor builds multiple types of tablet computers. Each type has a type identification number and a name. The key specifications for each type include amount of storage space and display type. The company uses multiple processor types, exactly one of which is used for a specific tablet computer type; obviously, the same processor can be used in multiple types of tablets. Each processor has a manufacturer and a manufacturerâs unique code that identifies it. (13p)
Each individual tablet computer manufactured by the vendor (see h above) is identified by the type identification number and a serial number that is unique within the type identification. The vendor wants to maintain information about when each tablet is shipped to a customer. (17p)
Each of the tablet computer types (see (h) above) has a specific operating system. Each technician the company employs is certified to assemble a specific tablet type â operating system combination. The validity of a certification starts on the day the employee passes a certification examination for the combination, and the certification is valid for a specific period of time that varies depending on tablet type â operating system combination. (11p)
Grading Schema:
1)Correct answer for degree in i) â 1p
2)Correct answer for cardinalities in i) â 1p
3)Entity with complete set of attributes including key attributes +4p
4)Incomplete set of attributes â (minus)-1p
5)Absence of key attributes if they defined â (minus)-1p
6)No or wrong attributes â (minus)-1p
7)Relationship with attributes +4p
8)Wrong left arrowhead â (minus)-1p
9)Wrong right arrowhead â (minus)-1p
10)Absence of relationship attributes â (minus)-1p
11)Relationship without attributes +3p
12)Wrong left arrowhead â (minus)-1p
13)Wrong right arrowhead â (minus)-1p
Answers
Answer:
attached below in the explanation and the diagrams attached
Explanation:
question
i) identify the degree and cardinality of the relationship
ii) Express the entities and the relationships with attributes in each description graphically with an E-R diagram
A)
i) The degree and cardinality of the relationship
The entities PIANO, MODEL and DESIGNER have a degree of two i.e. Binary relationship The cardinality of the entities PIANO, MODEL and DESIGNER have a relationship of ONE-to-manyii) description graphically with an E-R diagram
The E-R diagrams show that The degree of the relationship for the entities PIANO, MODEL, and DESIGNER is two(2). and also shows that there is a One-to-Many cardinality available in the entities PIANO, MODEL, and DESIGNER
E-R diagram Attached below
B)
i) The degree and cardinality of the relationship
entities PIANO and Technician have a degree of two ( 2 ) ; i.e. a Binary relationship The cardinality of the entities PIANO, and TECHNICIAN have a relationship of Many-to-Many.ii) Graphical description with an E-R diagram
The diagram describes/ shows that, entities PIANO and Technician have a degree of two ( 2 ) ; i.e. a Binary relationship and also The cardinality of the entities PIANO, and TECHNICIAN have a relationship of Many-to-Many.
E-R diagram attached below
C)
i) Degree and cardinality of the entity Technician
The entity TECHNICIAN has a degree one, i.e. a unary relationship. The cardinality of the entity TECHNICIAN have the relationship of One-to-Many.ii) E-R diagram attached below
D)
i) Degree and cardinality of the relationship
The entities TABLET TYPE and PROCESSOR TYPE have a degree of two(2) , i.e. a binary relationship The cardinality these entities TABLET TYPE, and PROCESSOR TYPE have is a Many-to-Many relationshipii) E-R diagram attached for TABLET TYPE, PROCESSOR TYPE is attached below
E)
i) Degree and cardinality of the relationship
The entities TABLET TYPE, TABLET COMPUTER, and CUSTOMER have a degree of two(2) ; i.e. a binary relationship. The cardinality these entities TABLET TYPE, TABLET COMPUTER, and CUSTOMER have is a One-to-Many relationshipalso the shipment to the customer is multiple hence the relationship can be said to be Many-to-Many relationship
also The attribute Shipping Date will become an attribute of that M: M relationship.
ii) The E-R diagram for TABLET TYPE, TABLET COMPUTER, CUSTOMER is attached below
F)
i) Degree and cardinality of the relationship between TABLET TYPE, TECHNICIAN
The entities TABLET TYPE, and TECHNICIAN have a degree of two(2); i.e. a binary relationship. The cardinality these entities TABLET TYPE, and TECHNICIAN have is a Many-to-Many relationshipii) E-R diagram attached below


Is Bob Lazar telling a lie/withholding information?
Answers
Answer:
I think he may be a nut, but I'm not sure, there's little evidence of what he says to be true.
What are the basic characteristics of the linear structure in data structure
Answers
Explanation:
A Linear data structure have data elements arranged in sequential manner and each member element is connected to its previous and next element. This connection helps to traverse a linear data structure in a single level and in single run. Such data structures are easy to implement as computer memory is also sequential.
1. What characteristics are common among operating systems? List types of operating systems, and
examples of each. How does the device affect the functionality of an operating system?
Answers
The fundamental software applications running upon that hardware allow unauthorized to the interface so much with the equipment because then instructions may be sent and result obtained.
Some characteristics of OS are provided below:
Developers provide technology that could be suitable, mismatched, or otherwise completely at odds with several other OS categories throughout various versions of the same similar OS.Throughout two different versions, the OS's are often 32 as well as 64-Bit.
Type of OS:
Distributed OS.Time-sharing OS.Batch OS.
Learn more about the operating system here:
https://brainly.com/question/2126669

PLEASE HURRY!!!!
Rowan bought a new laptop. What will protect the computer from viruses A.application software
B.up to date hardware
C. A new camera
D. System software
Answers
Answer:
D
Explanation:
Use Norton Sercrity link below
https://us.norton.com
Answer:
D
Explanation:
What are software applications?

Answers
Answer:
the first option is obviously the correct answer
In Java, write a method swapArrayEnds() that swaps the first and last elements of its array parameter. Ex: sortArray = {10, 20, 30, 40} becomes {40, 20, 30, 10}.
import java.util.Scanner;
public class ModifyArray {
/* Your solution goes here */
public static void main (String [] args) {
Scanner scnr = new Scanner(System.in);
int numElem = 4;
int[] sortArray = new int[numElem];
int i;
int userNum;
for (i = 0; i < sortArray.length; ++i) {
sortArray[i] = scnr.nextInt();
}
swapArrayEnds(sortArray);
for (i = 0; i < sortArray.length; ++i) {
System.out.print(sortArray[i]);
System.out.print(" ");
}
System.out.println("");
}
}
Answers
Answer:
Explanation:
To write the swapArrayEnds() method that swaps the first and last elements of an array in Java, you can do the following:
Create a new method with the following signature:
Copy code
public static void swapArrayEnds(int[] arr) {
// Your code goes here
}
Inside the method, create a temporary variable to store the value of the first element of the array.
Assign the value of the last element of the array to the first element.
Assign the value stored in the temporary variable to the last element of the array.
Your method should now look like this:
Copy code
public static void swapArrayEnds(int[] arr) {
int temp = arr[0];
arr[0] = arr[arr.length - 1];
arr[arr.length - 1] = temp;
}
This method will swap the first and last elements of the array. You can then call this method from your main method, passing in the array as an argument. The array will be modified in place, so you don't need to return anything from the method.
I hope this helps! Let me know if you have any questions.
Your friend Alicia says to you, “It took me so long to just write my resume. I can’t imagine tailoring it each time I apply for a job. I don’t think I’m going to do that.” How would you respond to Alicia? Explain.
Answers
Since my friend said “It took me so long to just write my resume. I can’t imagine tailoring it each time I apply for a job. I will respond to Alicia that it is very easy that it does not have to be hard and there are a lot of resume template that are online that can help her to create a task free resume.
What is a resume builder?A resume builder is seen as a form of online app or kind of software that helps to provides a lot of people with interactive forms as well as templates for creating a resume quickly and very easily.
There is the use of Zety Resume Maker as an example that helps to offers tips as well as suggestions to help you make each resume section fast.
Note that the Resume Builder often helps to formats your documents in an automatic way every time you make any change.
Learn more about resume template from
https://brainly.com/question/14218463
#SPJ1
In a library database, where would you have the potential for repeating groups? What are the potential problems? Explain.
Answers
In a library database, repeating groups can potentially occur in the following scenarios:
A book can have multiple authors
A book can have multiple subjects
A patron can borrow multiple books
A patron can have multiple addresses or phone numbers on file
The potential problem with repeating groups is that they can lead to data redundancy and inconsistency. For instance, if a book has multiple authors, the title and other book-related data may need to be repeated for each author. This can lead to inconsistencies in data, as any changes made to the book data may not be reflected accurately for each author. Similarly, if a patron has multiple addresses on file, changes made to one address may not be reflected for the other address.
Another problem with repeating groups is that they can lead to difficulties in searching and querying the database. For instance, if a book has multiple subjects, it may be difficult to search for all books related to a particular subject. In such cases, normalization techniques may be used to reduce the redundancy and inconsistencies associated with repeating groups.
mark me as brainliest if that helps
similarities between incremental and
prototyping models of SDLC
Answers
Prototype Model is a software development life cycle model which is used when the client is not known completely about how the end outcome should be and its requirements.
Incremental Model is a model of software consequence where the product is, analyzed, developed, implemented and tested incrementally until the development is finished.
What is incremental model in SDLC?
The incremental Model is a process of software development where conditions are divided into multiple standalone modules of the software development cycle. In this model, each module goes through the conditions, design, implementation and testing phases.
The spiral model is equivalent to the incremental model, with more emphasis placed on risk analysis. The spiral model has four stages: Planning, Risk Analysis, Engineering, and Evaluation. A software project frequently passes through these phases in iterations
To learn more about Prototype Model , refer
https://brainly.com/question/7509258
#SPJ9