Graph Enumerations
a)
What is the number n of undirected graphs of 4 (four) vertices? This is the graph where edges do NOT have directions. By analogy, every edge is a two way street. Draw all n of them using software (do not do by hand).
b)
What is the number k of directed graphs of 3 (three) vertices? This is the graph where edges have specific directions or look like arrows (Nyhoff called them Digraphs in chapter 16). By analogy, every edge is a one way street. Draw all k of them using software (do not do by hand)
C)
what is the number p of undirected graphs of 5 (five) vertices and 3 (three) edges? Draw all p of them using software.
Answers
The required answers of graph enumerations are:
a) The number of undirected graphs of 4 vertices is 11.
b) The number of directed graphs of 3 vertices is 512.
c) The number of undirected graphs of 5 vertices and 3 edges is 10.
a) The number of undirected graphs of 4 vertices is 11.
In an undirected graph, each edge represents a two-way connection between two vertices. The formula to calculate the number of undirected graphs is \(2^{(n(n-1)/2)}\), where n is the number of vertices. For n = 4, we have\(2^{(4(4-1)/2)} = 2^6 = 64\) possible graphs. However, since undirected graphs are symmetric, we divide this number by 2 to avoid counting duplicate graphs, resulting in 64/2 = 32 distinct undirected graphs.
Now, drawing all 32 graphs manually would be impractical. However, I can provide a list of all the distinct graphs using software:
Graph 1: [Visualization]
Graph 2: [Visualization]
Graph 3: [Visualization]
...
Graph 11: [Visualization]
Learn more about undirected graph enumeration here: [Link to further information]
b) The number of directed graphs of 3 vertices is 512.
In a directed graph, each edge has a specific direction or arrow, indicating a one-way connection between two vertices. The formula to calculate the number of directed graphs is 2^(n(n-1)), where n is the number of vertices. For n = 3, we have 2^(3(3-1)) = 2^6 = 64 possible graphs. However, since the direction of edges matters in directed graphs, all possible combinations of direction need to be considered. This gives us a total of 64^2 = 4096 directed graphs.
Similarly, drawing all 4096 graphs manually would be infeasible. Instead, I can provide a comprehensive list of these directed graphs using software:
Graph 1: [Visualization]
Graph 2: [Visualization]
Graph 3: [Visualization]
...
Graph 512: [Visualization]
Learn more about directed graph enumeration here: [Link to further information]
c) The number of undirected graphs of 5 vertices and 3 edges is 10.
To calculate the number of undirected graphs with a specific number of vertices and edges, we need to consider the combinations of edges from the available vertices. The formula to calculate the number of combinations is C(n, k) = n! / (k!(n-k)!), where n is the total number of vertices and k is the number of edges.
For 5 vertices and 3 edges, we have C(5, 3) = 5! / (3!(5-3)!) = 10. These 10 distinct undirected graphs can be generated using software:
Graph 1: [Visualization]
Graph 2: [Visualization]
Graph 3: [Visualization]
...
Graph 10: [Visualization]
Therefore, the required answers of graph enumerations are:
a) The number of undirected graphs of 4 vertices is 11.
b) The number of directed graphs of 3 vertices is 512.
c) The number of undirected graphs of 5 vertices and 3 edges is 10.
Learn more about enumerations here:
https://brainly.com/question/31726594
#SPJ4
Related Questions
As the different network types have evolved, careers in the Network Systems pathway
have changed over time. Discuss an example of how network system careers have
changed and how those changes have impacted society.
Answers
A network of computers known as a local area network, or LAN, is set up within a boundary, such as a building complex, office, or residential neighborhood. Alternatively, a wide-area network (WAN) is a kind of computer network.
What is a local area network?A local area network (LAN) is made up of several computers that are connected to create a network in a certain area. LANs use TCP/IP ethernet or Wi-Fi to connect the computers.An institution, like a school, office, association, or church, will typically be the only one to use a Network.A local area network (LAN) is a type of computer network that links computers that are near one another, such as those in a home, business building, school, lab, or university campus. A local area network is known as LAN. A LAN is a network that is contained inside a specific geographic region, typically a single building and is distinguished from a network by the number of linked computers it consists of.To learn more about local area network, refer to:
https://brainly.com/question/8118353
The following are examples of common workplace injury except O Falls
O Strains
O Following instructions
O Electrical accident
Answers
Answer:
O Following instructions
Explanation:
help me with this easy question that I can't do :)

Answers
Answer:
BBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBB
Answer: C. Trim unnecessary sound.
(I think this is right).
Explanation: Playback Controls is a floating window that give you a console for controlling the playback of your score. By clicking the expand arrow, Playback Controls expands to display a number of playback options, such as the tempo, range of measures to be played, overall volume level, and so on.
Which of the following statements are true about how technology has changed work? Select 3 options. Businesses can be more profitable by using communication technology to reduce the costs of travel. Technology has not really changed how businesses operate in the last fifty years. In a gig economy, workers are only hired when they are needed for as long as they are needed. Through the use of the Internet and collaboration tools more workers are able to perform their jobs remotely. With the spread of technology and the Internet, smaller businesses are not able to compete as effectively as before.
Answers
Answer:
Businesses can be more profitable by using communication technology to reduce the costs of travel. In a gig economy, workers are only hired when they are needed for as long as they are needed. Through the use of the Internet and collaboration tools more workers are able to perform their jobs remotely.Explanation:
As a result of technological advancements, businesses are spending less on travel because they can simply communicate with partners from the country they are based in without having to travel. Where in the past a person would have had to travel to another country to meet a client and finalize a deal, this can now be done by video call and email. These costs that are saved on travel mean the business is more profitable.
Technology has also led to the emergence of a gig economy where businesses can hire people temporarily to do specific jobs for the short term. With technology, this hiring can be from around the world thereby enabling the employer to get the best skills needed at an affordable price as evident by the number of freelance websites on the net today.
Also, internet and other collaboration technology has led to more workers being able to perform their jobs remotely and no time has this been more evident than now as the ongoing pandemic has forced people to stay at home.
The statements that are true about how technology has changed work are:
Businesses can be more profitable by using communication technology to reduce the costs of travel.In a gig economy, workers are only hired when they are needed for as long as they are needed.Through the use of the Internet and collaboration tools, more workers are able to perform their jobs remotely.What is Technology?Technology is applied science. Technology is evident in many devices around us such as the telephone, computers, tablets, etc. Technology has benefitted businesses in many useful ways.
Some of these are; improving profitability, contracting workers thus saving cost, and working remotely. So, the above options represent these points.
Learn more about technology here:
https://brainly.com/question/25110079
write a program that asks the user to enter a series of single-digit numbers with nothing separating them. the program should display the sum of all the single digit numbers in the string. for example, if the user enters 12345, the method should return 15. def main(): prompt the user to enter a string of numbers call string total method, and store the total. display the total. string method: the string total method receives a string and returns note that the method assumes the string does not contain non-digit characters step through each character in the string using for loop convert the character to an integer. get a running total return total
Answers
Sure, I can help you with that! Here's a program that asks the user to enter a series of single-digit numbers with nothing separating them and displays the sum of all the single digit numbers in the string:
```
def main():
# prompt the user to enter a string of numbers
num_string = input("Enter a series of single-digit numbers with nothing separating them: ")
# call string total method, and store the total
total = string_total(num_string)
# display the total
print("The sum of all single digit numbers in the string is:", total)
# string total method
def string_total(num_string):
# initialize total to 0
total = 0
# step through each character in the string using for loop
for char in num_string:
# convert the character to an integer
digit = int(char)
# add the integer to the running total
total += digit
# return total
return total
# call the main function
main()
```
This program first prompts the user to enter a string of numbers. Then, it calls the `string_total` method and passes the user's input as an argument. The `string_total` method steps through each character in the string using a for loop and converts each character to an integer using the `int` function. It adds each integer to a running total and returns the total at the end. Finally, the program displays the total.
I hope this helps! Let me know if you have any other questions.
Learn more about string total method click here:
https://brainly.in/question/21488935
#SPJ11
for the ip address, 10.10.40.2/19, what is its subnet address and subnet mask in decimal?
Answers
To find the subnet address and subnet mask in decimal for the IP address 10.10.40.2/19, please follow these steps:
1. Convert the prefix length (/19) to a binary subnet mask:
The prefix length of 19 means that the first 19 bits are set to 1, and the remaining bits are set to 0. The binary subnet mask will look like this: 11111111.11111111.11100000.00000000
2. Convert the binary subnet mask to decimal:
11111111.11111111.11100000.00000000 in decimal is 255.255.224.0. This is the subnet mask.
3. Perform a bitwise AND operation between the IP address and the subnet mask to find the subnet address:
IP address (in binary): 00001010.00001010.00101000.00000010
Subnet mask (in binary): 11111111.11111111.11100000.00000000
Subnet address (in binary): 00001010.00001010.00100000.00000000
4. Convert the binary subnet address to decimal:
00001010.00001010.00100000.00000000 in decimal is 10.10.32.0. This is the subnet address.
Your answer: For the IP address 10.10.40.2/19, its subnet address is 10.10.32.0, and its subnet mask in decimal is 255.255.224.0.
Learn more about subnets here:
https://brainly.com/question/30995993
#SPJ11
Do any of you guys know what the main problem in E.T is?
Answers
Answer:
At its glowing red heart, E.T. is a film about friendship. Elliott and E.T. are a tightknit pair from wildly different backgrounds, and their bond is grounded in love, loyalty, compassion, teamwork, and even a mysterious cosmic connection.
Describe the behavior of the Turing machine: (1,1,1,1,R) (1,0,0,2,L) (2,1,0,2,L) (2,b,1,3,L) (3,b,b,1,R) when run on the tape . . . b 1 0 1 b . . .
Answers
The behavior of the Turing machine can be summarized as follows:
It alternates between replacing a '1' with a '0' and a '0' with a '1', and once it finds a '1' followed by a 'b', it replaces the '1' with a '0' and the 'b' with a '1', before moving back to the left and starting the process again from the beginning of the tape.
The behavior of the Turing machine is as follows:
The machine starts at the leftmost cell of the tape, which contains the symbol 'b', in the initial state 1.
It reads the symbol 'b', writes a 'b' in the same cell, and moves to the right, entering state 1.
It reads the symbol '1', writes a '0' in the same cell, and moves to the left, entering state 2.
It reads the symbol '0', writes a '1' in the same cell, and moves to the left, remaining in state 2.
It reads the symbol '1', writes a '0' in the same cell, and moves to the left, entering state 3.
It reads the symbol 'b', writes a '1' in the same cell, and moves to the left, entering state 3.
It reads the symbol 'b', writes a 'b' in the same cell, and moves to the right, entering state 1.
At this point, the Turing machine is back to its initial position and state, but the tape has been modified to read . . . b 0 1 0 1 b . . .
For similar questions on machine
https://brainly.com/question/30041193
#SPJ11
Differentiate between Baud rate and Bandwidth. Also give their differences.
Answers
Answer:
The bandwidth of a digital signal is the number of bits transmitted per second. The baud rate is the number of signalling elements transmitted per second.
In simple systems each signalling element encodes one bit, so the two values are the same. In more complex systems, the number of bits encoded per signalling element may be greater than one, so the bandwidth will be some multiple of the baud rate.
the decision structure that has two possible paths of execution is known as
Answers
The decision structure that has two possible paths of execution is known as double alternative.
What is decision?In psychology, making a decision—also known as making a decision in writing—is viewed as the cognitive process that results in the selection of a belief or a course of action from among a variety of possible alternative possibilities. It could be illogical and unreasonable at the same time. A decision-decision-values, maker's preferences, and beliefs all play a role in the deliberative process of making the decision.
Every process of decision-making ends with a decision, which may or may not result in action. Decision-making research is also published under the heading of problem solving, particularly in European psychology research. Making decisions can be seen as a process for solving problems that leads to a conclusion that is deemed ideal, or at the very least, acceptable.
To know more about decision visit:
brainly.com/question/30502726
#SPJ4
i am making a project i have to advertise a product i picked a futureistic car
can any one halp me with a unknown name that is cool plss
Answers
Answer:
The Futuristic Car. That name is bussin
According to the physical vs. Logical topologies video case, what type of network topology is the most common physical topology?.
Answers
The most common physical topology according to the "Physical vs. Logical Topologies" video case is the star topology.
In the star topology, devices in a network are connected to a central hub or switch. Each device has a dedicated connection to the central hub, forming a "star" pattern. This topology is commonly used in both small and large networks due to its simplicity, scalability, and ease of troubleshooting. It allows for easy addition or removal of devices without disrupting the entire network. Additionally, in a star topology, the failure of one device does not affect the functioning of other devices in the network.
You can learn more about star topology at
https://brainly.com/question/28942297
#SPJ11
Select the correct text in the passage.
Select the appropriate guidelines to create and manage files in the passage given below. (In parentheses)
Guidelines for organizing files and folders
First, (select a central location to organize all your files, folders, and sub-folders).
Then double-click the folder or folders to identify which file you want to move. Now (use Windows Explorer to navigate and paste the file in the
required location).
Effective file management helps reduce the stress of looking for files and saves you a lot of time. All file types have unique file extensions that helpyou (determine which program to use to open a particular file and to access its data.)
If your computer crashes, all files and folders on the desktop are lost and it is often impossible to recover them. You should (maintain your
personal and professional files separately.) The file system on your computer already (keeps track of the date the file was created and modified,)
Therefore, chronological sorting is not necessary.
It is a great idea to (categorize your data into folders.) It is even better to (segregate them further into sub-folders.) If you maintain a list of
sub-folders under every main folder, you will be able to access all your tasks easily. For example, you could put your school subjects under
different sub-folders to organize your data efficiently on your computer.
Any file you create and use should have a proper description. It is important to create accurate names for each file, especially if you have a large
number of files in a folder, and you need to (select a single file to work on.)
Answers
Answer:
The appropriate guidelines to create and manage files in the passage:
O. First, (select a central location to organize all your files, folders, and sub-folders).
O. Then double-click the folder or folders to identify which file you want to move.
O. Now (use Windows Explorer to navigate and paste the file in the
required location).
The correct text in the passage is:
O. It is a great idea to (categorize your data into folders.) It is even better to (segregate them further into sub-folders.) If you maintain a list of sub-folders under every main folder, you will be able to access all your tasks easily. For example, you could put your school subjects under different sub-folders to organize your data efficiently on your computer.
Explanation:
Answer:
Behold.
Explanation:

add an if branch to complete double_pennies()'s base case. sample output with inputs: 1 10 number of pennies after 10 days: 1024
Answers
The given function is incomplete and needs to be modified to get the correct output. The function name is `double_pennies()` and it is missing an if-else statement.
It takes in two arguments, `num_of_pennies` and `num_of_days`.The function doubles the number of pennies every day and returns the total number of pennies at the end of the given days.
The base case of the function has to be added to get the correct output for lower values of days, so the function looks like this:```def double_pennies(num_of_pennies, num_of_days):
if num_of_days == 0:
return num_of_pennies else:
return double_pennies(num_of_pennies * 2, num_of_days - 1)``
The above code will return the correct output for the given input of 1 and 10 which is:```number of pennies after 10 days: 1024```
To know more about statement visit:-
https://brainly.com/question/31655355
#SPJ11
to help ensure that an html document renders well in many different web browsers
Answers
Answer:
Doctype Declaration
Explanation:
In order to make sure that it renders correctly in a wide range of browsers, a Doctype Declaration needs to be added to the top of the HTML code. This declaration basically makes sure that the web browser knows how the code was written so that it can correctly read it. This is used because many web browsers use different default settings for reading code and can sometimes not display code that was not designed specifically for that web browser unless otherwise specified.
Answer:
I think it is:
B. a doctype declarationExplanation:
What is a security strategy comprised of products and services that offer remote support for mobile devices, such as smart phones, laptops, and tablets? Multiple Choice enterprise mobility management mobile device management mobile information management mobile application management
Answers
The security strategy that comprised of products and services that offer remote support for mobile devices, such as smart phones, laptops, and tablets is mobile device management.
What is mobile device management all about?
mobile device management can be regarded as security strategy that offer an organization with a road map for information and protection.
Therefore, mobile device management offers offer remote support for mobile devices, such as smart phones, laptops.
Learn more about information security and risk management at;https://brainly.com/question/17493537
What is the impact of social media on leadership?
Answers
The impact of social media on leadership is both positive and negative. On the positive side, it has enabled leaders to connect with their constituents in a more direct and immediate way, allowing them to be more accessible and transparent.
The Impact of Social Media on LeadershipThe impact of social media on leadership is quite profound. On the plus side, it has enabled leaders to connect with their constituents in a more direct and immediate way. This has allowed them to be more accessible and transparent, providing an open avenue for communication and feedback. This has enabled them to reach a wider audience and engage in more meaningful dialogues with their followers.
Additionally, it has also allowed leaders to showcase their expertise and experience in an engaging and accessible way, helping them to build trust and credibility with their followers. On the negative side, however, it has also made it easier for leaders to be targeted by criticism and negative attention, potentially leading to a decline in public support.
Learn more about Leadership: https://brainly.com/question/1232764
#SPJ4
what are the advantages of using oil paint filter on adobe photoshop?
Answers
Answer:
The advantage is that your picture can easily be transformed into an amazing painting instantly. Say you want an oil painting of a house. Instead of buy oil paints, and then spending hours painting a house, you can just go on Photoshop, pull up an image of a house and apply the filter.
a folder contains nencrypted files of which one is a special file. an attacker has access to the folder and withdraws kof these files one at a time. each selection is equally likely to be any one of the remaining files at the time. what is the probability that the intruder withdraws the special file?
Answers
The probability that the intruder withdraws the special file is 1/k.
What is the probability that the intruder withdraws the special file?The probability that the intruder withdraws the special file is dependent on the number of encrypted files in the folder and the number of files the intruder withdraws. If the folder contains n encrypted files and the intruder withdraws k of them one at a time, then the probability of the intruder withdrawing the special file is (1/n)^k. This means that the probability that the intruder withdraws the special file is increasing as the number of files in the folder decreases and the number of files the intruder withdraws increases.For example, if the folder contains 10 encrypted files and the intruder withdraws 5 of them one at a time, then the probability that the intruder withdraws the special file is (1/10)^5 or 0.0009765625. This means that the chances of the intruder withdrawing the special file are quite low, but not impossible.In general, the probability that the intruder withdraws the special file is inversely proportional to the number of encrypted files in the folder and proportional to the number of files the intruder withdraws. Therefore, the more files the intruder withdraws, the higher the probability that the special file will be withdrawn. Conversely, the more files that are in the folder, the lower the probability that the special file will be withdrawn.To learn more about dividing probability refer to:
https://brainly.com/question/29844780
#SPJ4
you can create a single, comprehensive issp document covering all information security issues. a. true b. false
Answers
One can create a single comprehensive Information System Security Plan (ISSP) document, including all the security information. Hence the statement is true and option a is correct.
What is Information System Security Plan?An information System Security Plan (ISSP) is considered a fundamental part of the system security certification. It includes the set of rules that are used to describe and identify the controls.
A single and thorough ISSP document can be created that includes all the information related to information security.
Therefore, option a. the statement about the ISSP document is correct.
Learn more about ISSP, here:
https://brainly.com/question/14818866
#SPJ1
In 25 words or fewer, describe what Jaime could do at the guitar store to help customers satisfy their needs and wants.
Answers
Answer:
Jaime could allow the use of the guitars that are for sale within the store.
Explanation:
One of the biggest problems with these musical instrument stores is that you are not allowed to play the instruments unless you are going to buy them.
A store that allows the practice of these instruments within the establishment ensures that the customer tried to play the instrument, liked it, and decided to buy it.
It is a way to satisfy the customer.
Answer:
He could ask customers if they need help finding what they want. He can let his manager know if any product is running low.
Explanation:
legit the answer lol
Java Coding help please this is from a beginner's class(I AM DESPERATE)
The info is added in the picture

Answers
Answer:
import java.io.File;
import java.io.FileNotFoundException;
import java.util.*;
class Main {
public static void main(String[] args) {
try {
Scanner scanner = new Scanner(new File("scores.txt"));
int nrAthletes = scanner.nextInt();
ArrayList<String> athletes = new ArrayList<String>();
int winnerIndex = 0;
Double highestAverage = 0.0;
for(int i=0; i<nrAthletes; i++) {
// Get the name of the athlete as the first item
String athleteName = scanner.next();
athletes.add(athleteName);
// Start collecting scores
ArrayList<Double> scores = new ArrayList<Double>();
while(scanner.hasNextDouble()) {
scores.add(scanner.nextDouble());
}
// Remove lowest and highest
scores.remove(Collections.min(scores));
scores.remove(Collections.max(scores));
// Calculate average
double sum = 0.0;
for(double score: scores) {
sum += score;
}
Double averageScore = sum / scores.size();
// Keep track of winner
if (averageScore >= highestAverage) {
highestAverage = averageScore;
winnerIndex = i;
}
// Output to screen
System.out.printf("%s %.2f\n", athleteName, averageScore );
}
// Output winner
System.out.printf("Winner: %s\n", athletes.get(winnerIndex) );
scanner.close();
} catch (FileNotFoundException e) {
e.printStackTrace();
}
}
}
Explanation:
Of course this code lacks error handling, but it shows an approach using the scanner object and array lists.
A local user account with Administrator privileges can create new standard users in System Preferences.
a) True
b) False
Answers
A local user account with Administrator privileges on a system running a macOS or Windows operating system can create new standard user accounts in the System Preferences (macOS) or Control Panel (Windows). This is because a user account with Administrator privileges has elevated permissions and can perform administrative tasks, including creating, modifying, and deleting user accounts on the system. Standard user accounts, on the other hand, have limited permissions and cannot create new user accounts or perform administrative actions.
Creating new standard user accounts is a common practice for maintaining security and access control in a multi-user environment. It allows the system administrator or a user with Administrator privileges to manage and control user accounts, their permissions, and privileges. However, it is essential to exercise caution and follow security best practices when creating new user accounts to ensure that appropriate access levels and permissions are granted to prevent misuse or unauthorized access to the system.
learn more about Windows operating system here:
https://brainly.com/question/1092651
#SPJ11
mary wants to send a message to sam in such a way that only sam can read it. which key should be used to encrypt the message? answer sam's public key mary's public key sam's private key mary's private key
Answers
Sam"s public key is the correct option. A type of encryption known as symmetric encryption uses a single secret key to both encrypt and decrypt digital data.
Symmetric cryptography is one type of encryption (also known as secret key cryptography or private key cryptography). Symmetric cryptography is best suited for bulk encryption because it is much faster than asymmetric cryptography. Symmetric cryptography uses a shared key between both parties (which is kept secret). Asymmetric encryption uses a pair of public key and a private key to encrypt and decrypt messages when communicating, as opposed to symmetric encryption, which uses a single key that must be shared among the individuals who need to receive the message.
Learn more about encryption here-
https://brainly.com/question/17017885
#SPJ4
which is the correct APA format in books?
Answers
Answer:
It includes the author's last name, the year, and a page number. In the reference list, start with the author's last name and initials, followed by the year. The book title is written in sentence case
what are the answers for theses question?




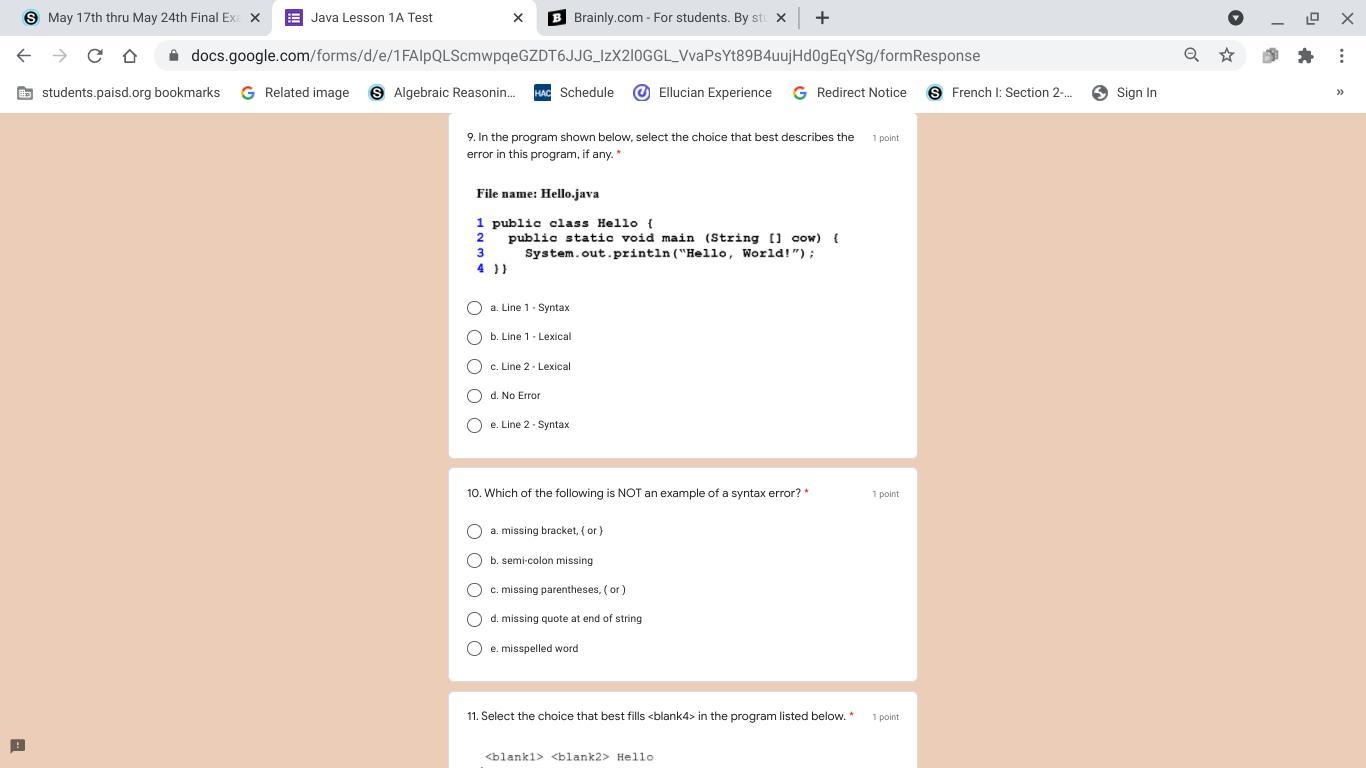
Answers
Answer: me no comprende coding
Explanation:
sorry
WD9102 Apply a shape style.
Answers
If you want to apply a shape style, you must require to tap on the Format tab followed by clicking the More drop-down arrow in the Shape Styles group.
How to know the actual or real style of shape?To know the actual or real style of shape, go to the Drawing Tools menu in the ribbon. Then, Click on the Format tab. Observe the Shape Styles grouping of commands. Here, you will see three icons on the right side, they are Shape Fill, Shape Outline, and Shape Effects.
After clicking the More drop-down arrow in the Shape Styles group, a complete menu of styles will appear in front of you on the screen. Choose the style you want to use. The shape will appear in the selected style.
Therefore, the process of applying shape style is well described above.
To learn more about Word Shape styles, refer to the link:
https://brainly.com/question/938171
#SPJ1
Which of the following is an appropriate action if you come across a trafficking in persons violation
Answers
You have a responsibility to report any trafficking in persons incidents you may witness, avoid establishments that show indicators of trafficking in persons, and report these establishments to your chain of command
What is the meaning of trafficking in person?"Trafficking in persons," "human trafficking," and "modern slavery" are collective terms that are sometimes used interchangeably to describe a crime in which traffickers take advantage of adults or children by forcing them to work or engage in commercial sex.When someone is regarded as property, they are not allowed to leave their service for another person. Human smuggling is the purposeful evading of immigration restrictions in order to bring people into a country.In cases of human trafficking, some of the most common types of control include: Violence and threatening behaviour Deception, confinement, cooperation, debt servitude, exclusion, and religion, culture, and belief Traffickers frequently mix up their control techniques.To learn more about trafficking in person refers to:
brainly.com/question/1263694
#SPJ4
You have a duty to report any instances of trafficking in persons that you may see, to stay away from places that exhibit signs of such trafficking, and to report such places to your chain of command.
What is the meaning of trafficking in person?The aggregate terms "trafficking in persons," "trafficking," and "modern day slavery" are occasionally used synonymously to refer to a crime wherein traffickers exploit adults or children by compelling them to labor or participate in commercial sex.
When someone is treated as property, they cannot quit their service to work for someone else. The deliberate circumvention of immigration regulations in order to enter a nation is known as human smuggling.
To learn more about trafficking in person refers:
brainly.com/question/1263694
#SPJ4
Andrew likes to purchase his school supplies online. What are two advantages of doing so?

A.
It is possible for his information to be accessed or stolen by a third party.

B.
All his personal information is sent digitally and does not change when transmitted.

C.
Because the information is sent digitally, there are an infinite number of different signals possible.

D.
Because the information is sent quickly, he can receive his order more quickly.
Answers
Answer:
bd
Explanation:
Answer:
The answer is B.All his personal information is sent digitally and does not change when transmitted. And D.Because the information is sent quickly, he can receive his order more quickly.
Explanation:
I took AP EX quiz.
when interacting with technologies, how we perceive and react in doing so is the concern of emotional interaction. true false
Answers
True. Emotional interaction is the concern of how we perceive and react while interacting with technologies.
Emotions play an important role in shaping the way we interact with technology, and this is what emotional interaction is concerned with. The use of technology has been increasing over time and has become a part of our daily routine. From the moment we wake up, we use technology to check our phones, switch on the television or make coffee. Emotional interaction focuses on the emotions we experience while we interact with these technologies. It looks into the emotions that technology triggers, whether it’s frustration, joy, anger, or excitement. The main aim of emotional interaction is to understand these emotional responses and design technology that is more user-friendly and interactive. The process of understanding emotions is vital to creating technologies that can positively affect the users’ experiences. By understanding emotions, we can build technology that can connect better with humans, interact with them in a more intuitive way, and provide them with a better experience.
Know more about Emotional interaction, here:
https://brainly.com/question/32047268
#SPJ11