Given the variables taxable_purchases and tax_free_purchases (which already have been defined), write an expression corresponding to the total amount purchased.
Answers
The expression to calculate the total amount purchased is, taxable_purchases + tax_free_purchases. To calculate the total amount purchased, we need to add the amounts of taxable and tax-free purchases.
This can be achieved by using the addition operator + between the two variables, which will give us the sum of the two amounts. Therefore, the expression taxable_purchases + tax_free_purchases will give us the total amount purchased.
It is important to note that the variables taxable_purchases and tax_free_purchases must have been previously defined and assigned a numerical value for this expression to work correctly. If either of these variables has not been defined, an error will occur when attempting to use this expression. This expression calculates the total amount purchased by combining both taxable and tax-free purchases.
To know more about taxable_purchases visit:
https://brainly.com/question/30439441?
#SPJ11
Related Questions
a company set up controls to allow only a specific set of software and tools to install on workstations. a user navigates to a software library to make a selection. what type of method prevents installation of software that is not a part of a library
Answers
Allow list is type of method prevents installation of software that is not a part of a library.
What is Allow list?
A list of domains or email addresses that you want to receive emails from is referred to as a whitelist or an allow list. You can instruct the email system not to filter email from a certain address or domain by adding it to your list of allowed addresses or domains.What does whitelist being enabled mean?
An email address, IP address, domain name, or application can be approved while all others are rejected using a cybersecurity technique known as a whitelist (allowlist).
What is Allowlist in phone?
From a security perspective, allowlisting is a useful tool for preventing PHAs from devices because the allowlist of programs ultimately gets quite small.
Learn more about allow list.
brainly.com/question/13850709
#SPJ4
Python programmers use the Else statement to run code
Answers
Answer:
the answer is True
Explanation:
when you use an if statement it has to end with an else statement because the if statement is used to give opinions in a code but if the option doesn't fit the need of the function then the else statement is expected.
Answer:
A. An else statement runs when all the conditions in the preceding if and elif statements evaluate as False.
Explanation:
Hope it helps! =D What I got on edge!
your boss has asked you to set up automated reactions to detected suspicious actions to protect and secure users' identities. which feature can you use to accomplish the given task?
Answers
Since your boss has asked you to set up automated reactions to detected suspicious actions to protect and secure users' identities. the feature that can you use to accomplish the given task is AD Identity Protection service.
What user profile options can be used to assist in spotting or stopping suspicious behavior on an Azure AD account?Set up alerts and monitoring. It's crucial to monitor and audit your logs to find unusual activity. Azure AD logs can be integrated with other tools, such as Microsoft Sentinel, Azure Monitor, and other SIEM solutions, in a number of different ways through the Azure portal. 22 Aug 2022
Hence, The user risk level that causes this email to be generated is - The risk level is by default set to "High" risk. Users with the Global Administrator, Security Administrator, or Security Reader responsibilities are automatically added to this list as receivers of this email.
Learn more about Identity Protection service from
https://brainly.com/question/28528467
#SPJ1
to recognize users across different devices, what is required for user id?
Answers
Answer:
To recognize users across different devices, Sign-in is required for User IDHope it helps
Using a while loop, write a C++ program that, beginning from 1, computes and displays the square roots of the first 25 odd positive integers.
Answers
Answer:
#include <iostream>
#include <cmath>
using namespace std;
int main()
{
int i = 1;
while (i <= 25)
{
cout << sqrt(i * 2 - 1) << endl;
i++;
}
return 0;
}
Passing an argument by ___ means that only a copy of the arguments value is passed into the parameter variable and not the addrtess of the item
Answers
Passing an argument by Value compromises that only a copy of the arguments value exists passed into the parameter variable and not the address of the item
What is Parameter variable?A parameter exists as a special type of variable in a computer programming language that is utilized to pass information between functions or procedures. The actual information passed exists called an argument. A parameter exists as a named variable passed into a function. Parameter variables exist used to import arguments into functions.
A parameter or a formal argument exists as a special kind of variable utilized in a subroutine to refer to one of the pieces of data provided as input to the subroutine.
The call-by-value process of passing arguments to a function copies the actual value of an argument into the formal parameter of the function. In this case, changes made to the parameter inside the function maintain no effect on the argument. By default, C++ utilizes call-by-value to pass arguments.
Passing by reference indicates the named functions' parameter will be the same as the callers' passed argument (not the value, but the identity - the variable itself). Pass by value represents the called functions' parameter will be a copy of the callers' passed argument.
Hence, Passing an argument by Value compromises that only a copy of the arguments value exists passed into the parameter variable and not the address of the item
To learn more about Parameter variable refer to:
https://brainly.com/question/15242521
#SPJ4
You replaced the ink cartridges in a color inkjet printer. Users are now complaining that print quality has degraded, lines are fuzzy, and the colored areas in images are starting or stopping before they should. Which inkjet maintenance task do you need to perform
Answers
100 POINTS FOR ANYONE WHO CAN DO THIS!
Make the following modifications to the original sentence-generator program:
The prepositional phrase is optional. (It can appear with a certain probability.)
A conjunction and a second independent clause are optional: "The boy took a drink and the girl played baseball".
An adjective is optional, it may or may not be added to the sentence to describe a noun: "The girl kicked the red ball with a sore foot".
"Optional" is implying that the program should include these elements in a semi-random frequency.
You should add new variables for the sets of adjectives and conjunctions.

Answers
Let's check what can be modified
Before calling def we need adjective and conjunctions stored inside variables
Store them(You may change according to your choice)
\(\tt adjectives=("foolish","bad","long","hard")\)
\(\tt conjunctions=("and","but","for","after")\)
We have to make optional ,easy way ask the user to do instead of yourself .
\(\tt con=input("Enter\: yes\: if \:you \:want \:to \:use \:conjunctions:")\)
\(\tt adj=input("Enter\:yes\:if\:you\:want\:to\:use\: adjectives:")\)
If they click then we can proceed else no problem let the program run
\(\tt def\: conjunctionPhrase():\)
\(\quad\tt if\: con=="yes":\)
\(\quad\quad\tt return\:random.choice(conjunctions)+"\:"+nounPhrase()\)
\(\quad\tt else:\)
\(\quad\quad\tt continue\)
You may use pass also\(\tt def\: adjectivePhrase():\)
\(\quad\tt if\:adj=="yes":\)
\(\quad\quad\tt return\:random.choice(adjectives)+"\:"+nounPhrase()\)
\(\quad\tt else:\)
\(\quad\quad\tt continue\)
An important part of the development of transport is safety. how can you, when you get around in different ways, contribute to making it safer on the roads
Answers
Answer:
I need help I don't get a this questions please asap?
Explanation: Head-on collisions. Some simple solutions can help to reduce the risk of head-on crashes. ...
Run-off road crashes. This is when a vehicle collides with a stationary object, such as a sign or lamppost, after leaving the road. ...
Intersection crashes. ...
Vulnerable road users. ...
Much work to be done.
Aug 31, 2018
Please help me with this


Answers
Answer:
Explanation:
what?
there is a linux command called uname. when executed, the uname command will output important information about the system. which uname command option will output only the kernel version?
Answers
Linux command Uname has numerous other settings that enable us to isolate only the data we require. The -r or --kernel-release option, which solely displays details on the kernel release, is one such instance.
$ uname -r
output: 5.8.0-59-generic
The name of the operating system you are using is printed on standard output by the uname command. The machine ID number is made up of 12 characters and is formatted as xxyyyyyymmss. The system is shown by the xx positions, which are always zero. The system's unique ID number can be found in the yyyyy positions.
Syntax: uname [OPTION]
Use the -v or --kernel-version option to print information about the kernel version.
$ uname -v
#88~20.05.1-Ubuntu SMP Thu Jan 19 12:00:10 UTC 2022
To learn more about Linux click here:
brainly.com/question/28591010
#SPJ4
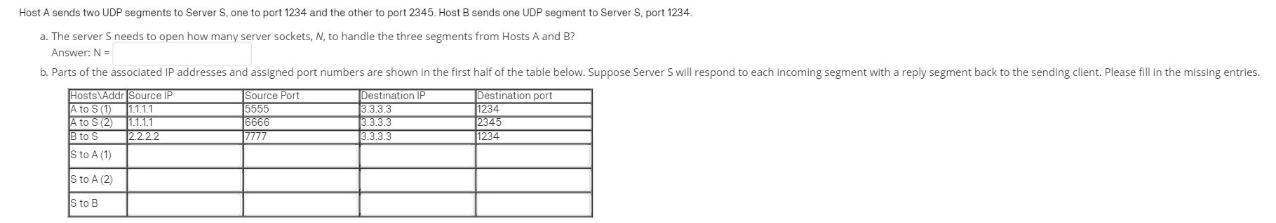
Host a sends two udp segments to server s, one to port 1234 and the other to port 2345. host b sends one udp segment to server s, port 1234.
a)
the server s needs to open how many server sockets, n, to handle the three segments from hosts a and b?
n = ?
b)
see attachment
Answers
The server s needs to open two server sockets to handle the three segments from hosts a and b.
In order for servers to handle the three segments from hosts a and b, there must be two server sockets. The first socket will handle the two segments from host a, one sent to port 1234 and the other sent to port 2345.
The second socket will handle the one segment from host b, sent to port 1234. Therefore, the server s needs to open two server sockets, n = 2 to handle the three segments from hosts a and b.
For more questions like Socket click the link below:
https://brainly.com/question/15007996
#SPJ4
what type of malware prevents you from accessing files
Answers
How to fix my pc from this

Answers
Answer:
Restart it
Explanation:
Answer:
break it and throw it away
Explanation:
cuz why not
It is the way to convey a message,an idea,a picture,or speech that is received and understood clearly and correctly by the person for whom it is sent.
Answers
Answer:
Communication.
Explanation:
Communication can be defined as a process which typically involves the transfer of information from one person (sender) to another (recipient), through the use of semiotics, symbols and signs that are mutually understood by both parties.
In this context, communication is the way to convey a message, an idea, a picture, or speech that is received and understood clearly and correctly by the person for whom it is sent.
Generally, the linear model of communication comprises of four (4) main components and these are;
1. Sender (S): this is typically the source of information (message) or the originator of a message that is being sent to a receiver. Thus, they are simply the producer of a message.
2. Channel (C): this is the medium used by the sender for the dissemination or transmission of the message to the recipient. For example, telephone, television, radio, newspapers, billboards etc.
3. Message (M): this is the information or data that is being sent to a recipient by a sender. It could be in the form of a video, audio, text message etc.
4. Receiver (R): this is typically the destination of information (message) or the recipient of a message that is being sent from a sender.
Messing around is driven by the user's:
A. need to have friends.
B. love of fighting games.
C. initiative and interests.
D. obsession with a project.
Answers
Answer:
The answer is C
Explanation:
I hope that the answer
What is Web 2.0 in the Internet ?
Answers
Answer:
Anser Below
Explanation:
Web 2.0 (also known as Participative (or Participatory) and Social Web) refers to websites that emphasize user-generated content, ease of use, participatory culture and interoperability (i.e., compatible with other products, systems, and devices) for end users.
Your company has just acquired a company that has an Active Directory forest with one Windows 2008 domain named southsim.com. The current structure of both forests must be retained for now.You need to design trusts between the domains or forests to meet the following requirements:- Users in the northsim.com domain must be able to use the resources in the southsim.com domain.- Users in the southsim.com domain should not be able to use resources in the northsim.com domain, with the exception of selected management personnel who will be allowed access to reports on one of the servers in the northsim.com domain.- You would like to minimize the number of trusts created and the amount of effort needed to maintain the trusts.What should you do? (Choose two.)- Create a two-way shortcut trust between the northsim.com domain and the southsim.com domain.- Create a two-way forest trust between the northsim.com forest and the southsim.com forest.- Create a two-way realm trust between the northsim.com domain and the southsim.com domain.- Enable Selective Authentication for the southsim.com forest.- Create a one-way external trust pointing from the northsim.com domain to the southsim.com domain.- Enable Selective Authentication for the northsim.com forest.
Answers
Establish a two-way forest trust between the forests of northsim.com and southsim.com.
Selective Authentication should be enabled for the northsim.com forest.
What is the purpose of Windows Server 2008?The fourth iteration of Microsoft's Windows Server operating system, code-named "Longhorn Server," is a member of the Windows NT family of operating systems and is referred to as Windows Server 2008. On February 4, 2008, it became available for manufacture, and on February 27, it became readily available for purchase at retail. On January 14, 2020, Microsoft will no longer provide security updates for Windows Server 2008 and Windows Server 2008 R2. On October 10, 2023, Windows Server 2012 and Windows Server 2012 R2's extended support will come to an end. It's clear that the product is actually Windows Server 7 despite the "2008 R2" branding. Also serving as a different kind of server is Windows Server 2008.To lean more about Windows 2008, refer to:
https://brainly.com/question/29956982
What is the full form of MOS
Answers
Answer:
Military occupational speciality
_____ provide(s) an interface to the services provided by an operating system.
a. shared memory
b. system calls
c. simulators
d. system programs
Answers
The correct answer is (b) system calls.System calls provide an interface to the services provided by an operating system.
They allow user programs to request services from the operating system, such as creating or deleting files, allocating memory, or accessing hardware devices.
When a user program wants to perform a certain operation that requires the assistance of the operating system, it makes a system call. The system call acts as a bridge between the user program and the operating system, allowing the program to access the desired service.
For example, if a program wants to read data from a file, it will make a system call to request the operating system to perform the file read operation on its behalf. The operating system will then handle the request and provide the necessary functionality to read data from the file.
In summary, system calls provide an essential interface for user programs to access and utilize the services provided by an operating system.
To know more about operating system visit:
https://brainly.com/question/6689423
#SPJ11
________ is a human-computer interaction method whereby inputs to and outputs from a computer-based application are in a conventional spoken language such as English.
Answers
\(\sf\purple{Natural\: language\: interaction}\) is a human-computer interaction method whereby inputs to and outputs from a computer-based application are in a conventional spoken language such as English.
\(\circ \: \: { \underline{ \boxed{ \sf{ \color{green}{Happy\:learning.}}}}}∘\)
Often, a single source does not contain the data needed to draw a conclusion. It may be necessary to combine data from a variety of sources to formulate a conclusion. How could you do this in this situation of measuring pollution on a particular river?
Answers
To measure the pollution of a particular river, one must take the sample of the river and take the sample of pure water, then draw the conclusion, it will tell the amount of pollution in the river water.
What is pollution?Pollution is the mixing of unwanted or harmful things in any substance or compound.
Water pollution is the mixing of toxics and chemicals in water.
Thus, to measure the pollution of a particular river, one must take the sample of the river and take the sample of pure water, then draw the conclusion, it will tell the amount of pollution in the river water.
Learn more about pollution
https://brainly.com/question/23857736
#SPJ1
An accenture technology team located in the us has added a new feature to an existing online ticketing platform. the team would like to have the new feature reviewed by other global teams using individual instances of the platform. which technology, when combined with agile and devops, will help the team receive real-time feedback?
Answers
The technology, when combined with agile and devops, will help the team receive real-time feedback is artificial intelligence (ai).
What is AI artificial intelligence?Artificial intelligence is known to be a form of simulation that regards to human intelligence acts by machines, mostly computer systems.
Note that in the above case, The technology, when combined with agile and devops, will help the team receive real-time feedback is artificial intelligence (ai).
See options below
intelligent apps
artificial intelligence (ai)
internet of things (lot)
cloud computing
I don't know this yet.
Learn more about Accenture technology from
https://brainly.com/question/25682883
#SPJ1
why ada lovelace is known as first computer programmer ?
Answers
Answer:
Ada Lovelace, is known as the fist computer programmer because she was the one who proposed / invented computer programming.
Basically the first person to realize that the analytical engine could "perform arbitrary tasks and wrote programs for those arbitrary task, beyond computational operations."
Hope this helps :)
examine how industrialization and manufacturing altered rural consumption practices. which statement best reflects rural consumption practices in the late 19th century?
Answers
Rural consumption practices in the late 19th century were significantly altered by industrialization and manufacturing, leading to increased availability of consumer goods and changes in consumption patterns.
The statement that best reflects rural consumption practices in the late 19th century is that rural communities experienced an expansion in the range of available consumer goods and witnessed a shift towards a more market-oriented economy. As industrialization and manufacturing advanced, rural areas gained better access to manufactured products through improved transportation networks and the proliferation of general stores and mail-order catalogs. This resulted in a greater variety of goods being available to rural consumers, including clothing, household items, and food products. The increasing availability of consumer goods led to changes in consumption patterns, with rural communities becoming more engaged in market-based exchanges and relying less on self-sufficiency or local production. This shift marked a transformation in rural consumption practices, bringing them closer to the consumption patterns observed in urban areas.
learn more about transportation networks here:
https://brainly.com/question/26969063
#SPJ11
2
Type the correct answer in the box. Spell all words correctly.
Lella needs to submit her research paper next week. She is collating all information and dividing it into sections. In which section should she include
the results of her research?
Lella should include the results of her research in the
section of the research paper.
Reset
Next
2022 Edmentum. All rights reserved.
Answers
Lella should include the results of her research in the "Results" section of the research paper.
The "Results" section of a research paper is where the findings of the research study are presented. This section typically includes the data collected, statistical analyses, and any other relevant information that directly supports or contradicts the research hypothesis. It provides a clear and organized presentation of the results obtained from the research methodology.
By including the results in a separate section, Lella can present her findings in a structured and comprehensive manner, allowing readers to understand and evaluate the outcomes of her research. This section is crucial for conveying the key findings and supporting evidence, which contributes to the overall credibility and impact of the research paper.
You can learn more about research paper at
https://brainly.com/question/26441547
#SPJ11
what kind of imagery and language did the historical posters use? do you think that style would be effective today? why or why not
Answers
Answer:
yes that style will be effective today
Explanation:
it is effective today in the case where you are looking for someone. This means when someone is missing or the police is looking for somebody it will be effective in that case
the most powerful computers, , can evaluate complex data very quickly. many of these computers in the united states are owned by the government or major research institutions and can cost $1 million dollars or more.
Answers
The most powerful computers, supercomputers, can evaluate complex data very quickly. Many of these computers in the United States are owned by the government or major research institutions and can cost $1 million dollars or more.
What is a computer?A computer can be defined as an electronic device that is designed and developed to receive data in its raw form as an input and processes these data through the central processing unit (CPU) into an output (information) that could be seen and used by an end user.
What is a supercomputer?A supercomputer simply refers to one of the most powerful computers that is designed and developed for handling, evaluating, and solving very complicated problems or tasks. Additionally, supercomputers have the ability to carry out trillions of calculations per second.
Read more on supercomputer here: https://brainly.com/question/14883920
#SPJ1
Complete Question:
The most powerful computers, _____, can evaluate complex data very quickly. Many of these computers in the United States are owned by the government or major research institutions and can cost $1 million dollars or more.
why should you not deploy a wireless network using wep for security?
Answers
WEP or Wired Equivalent Privacy is an encryption protocol designed to secure wireless computer networks. Despite its widespread use, WEP has several flaws that make it easy to hack. Because of these vulnerabilities, deploying WEP for security is not recommended.
The reasons why you shouldn't deploy a wireless network using WEP for security are:Weak SecurityWEP is vulnerable to hacking. This is due to the fact that it uses a flawed algorithm to encrypt wireless data, which can be easily decoded using a packet sniffing tool. Even novice hackers can break into WEP-protected networks using freely available tools like Aircrack-ng.Slow Network SpeedsWEP is not only weak, but it's also slow.
WEP's encryption protocol is inefficient and consumes a lot of bandwidth. As a result, the network slows down significantly when encryption is enabled. This makes it difficult for businesses to maintain a fast and reliable wireless network.Poor Device CompatibilityModern devices are not compatible with WEP security protocol, which makes it ineffective for securing a wireless network.
To know more about encryption visit:
https://brainly.com/question/30225557
#SPJ11
what is the main purpose of the circulatory system
Answers
The network of blood vessels and the heart that carries blood throughout the body. This system helps tissues get the right amount of nutrients, oxygen, and waste disposal.
The most important component of the circulatory system?The primary function of the circulatory system is to carry oxygen, nutrients, and hormones to the muscles, tissues, and organs throughout the body. Another role of the circulatory system is to remove waste from cells and organs so that your body can eliminate it.
What is the primary goal of this quiz about the circulatory system?The circulatory system's job is to provide nutrients and oxygen to body cells while returning carbon dioxide and oxygen-poor blood to the heart and lungs.
To know more about circulatory system visit:-
https://brainly.com/question/29259710
#SPJ4