for a single connection we need to have an average TCP throughput = 6Gbps . assume , RTT = 10 msec and no error
first, the average TCP throughput in GBps is ?
second, How many bytes are traveling per RTT? (unist bytes)
third, assume that all segments have a size of 1800 bytes, what will be the window size?
Answers
In the given scenario, we aim to achieve an average TCP throughput of 6 Gbps (Gigabits per second) with an RTT (Round Trip Time) of 10 milliseconds and no errors.
We need to determine the average TCP throughput in GBps, the number of bytes traveling per RTT, and the window size assuming all segments have a size of 1800 bytes.
To calculate the average TCP throughput in GBps, we divide the given throughput in Gbps by 8 since there are 8 bits in a byte. Therefore, the average TCP throughput is 6 Gbps / 8 = 0.75 GBps.
To find the number of bytes traveling per RTT, we multiply the average TCP throughput in GBps by the RTT in seconds. In this case, it would be 0.75 GBps * 0.010 seconds = 0.0075 GB or 7500 bytes.
The window size determines the number of unacknowledged segments that can be sent before receiving an acknowledgment. To calculate the window size, we divide the number of bytes traveling per RTT by the segment size. In this case, it would be 7500 bytes / 1800 bytes = 4.1667 segments. Since the window size should be an integer, we would round it down to the nearest whole number, resulting in a window size of 4 segments.
To know more about TCP click here: brainly.com/question/27975075
#SPJ11
Related Questions
T or F. MFT stands for Master File Table.
Answers
True. The NTFS file system in Windows uses the MFT, or Master File Table, database to store data about files and directories on a drive.
In the context of the NTFS (New Technology File System) used by Windows operating systems, MFT stands for "Master File Table". An NTFS volume's MFT is a unique file that houses metadata for all of the volume's files and folders. However, depending on the profession or industry, MFT can be used to refer to several things in a more general context. In banking, MFT can stand for "Management Fee Table," whereas in telecoms, it might mean "Multi-Fiber Termination." As a result, the context in which MFT is employed determines its meaning.
learn more about Master File here:
https://brainly.com/question/29730665
#SPJ11
lab 9 - circular motion lab purpose: the purpose of this lab is to look at the connection between the radius of a circle and the distance it will roll for a given number of rotations, and relation between diameter and the linear distance of circle.
Answers
The purpose of Lab 9 on circular motion is to examine the relationship between the radius of a circle and the distance it rolls for a given number of rotations, as well as the connection between the diameter and the linear distance traveled by the circle.
What is the purpose of Lab 9 on circular motion?The purpose of Lab 9 on circular motion is to investigate the relationship between the radius of a circle and the distance it will roll for a specific number of rotations.
By conducting experiments, the lab aims to explore how changes in the radius affect the linear distance traveled by the circle.
Additionally, the lab seeks to establish a connection between the diameter of the circle and the corresponding linear distance covered.
This investigation will provide insights into the fundamental principles of circular motion and further understanding of the relationship between geometric properties of circles and their motion characteristics.
Learn more about circular motion
brainly.com/question/14625932
#SPJ11
1. Are you aware about ICT technologies, online platforms and functions?
2. If you are to create a microblogging page, what will be your theme or content about?
1. Pick five (5) rules from the core rules of netiquette and cite a scenario which this rule is
violated and explain how will you address or correct this bad practice?
2. List down at least five (5) things you should do or not do to avoid internet threats such as
malwares and spams?
Answers
I am aware about ICT technologies, online platforms and functions.
2. If i create a microblogging page, the theme or content will be about Health and wholeness of the mind.
What is the five (5) rules from the core rules of netiquette?The Core Rules of Netiquette are:
Always Remember that you are Human. Do stand and keep the same standards of behavior online and in real life. Do Know where you are in regards to cyberspace. .Do Respect other people's time as well as their bandwidth. Do make yourself to appear good online. .Do and always Share expert knowledge.Therefore, I am aware about ICT technologies, online platforms and functions. If i create a microblogging page, the theme or content will be about Health and wholeness of the mind.
Learn more about ICT technologies from
https://brainly.com/question/20717870
#SPJ1
which word means the pattern of beats in a poem a personification b simile c rhythm d onomatopoeia
Answers
Answer:
C. rhythm
Explanation:
The easy defintion of rhythm is the following:
Pattern of beats or a series of stressed and. unstressed syllables in poem. • Poets create rhythm by using words in which. parts are emphasized or not emphasized
So hope this helps.
Answer:
rhythrm
Explanation:
In order to avoid slipping in the shop, your footwear should ___________.
Answers
Answer:
Be sticky or not slippery
Explanation:
List two forms of personal information that will need to be provided when purchasing something online?
Answers
Answer:
You can divide primary data into two categories: quantitative and qualitative.
Explanation:
Hope this helps
Answer please in order

Answers
Answer:
analogue; discrete; sampled; sample rate; bit depth; bit rate; quality; larger; file size.
Explanation:
Sound are mechanical waves that are highly dependent on matter for their propagation and transmission.
Generally, it travels faster through solids than it does through either liquids or gases.
Sound is a continuously varying, or analogue value. To record sound onto a computer it must be turned into a digital, or discrete variable. To do this, the sound is sampled at regular intervals; the number of times this is done per second is called the sample rate. The quality of the sound depends on the number of bits stored each time - the bit depth. The number of bits stored for each second of sound is the bit rate and is calculated by multiplying these two values (sample rate and bit depth) together - kilobits per seconds (kbps). The higher these values, the better the quality of the sound stored, but also the larger the file size.
you are developing an azure-based application that stores all application settings in the azure app configuration service. you provision a standard tier azure app configuration instance and enable the customer-managed key capability on the instance. you need to allow the azure app configuration instance to use an azure key vault key. which two actions should you perform? each correct answer presents part of the solution. a. enable the purge-protection feature on the azure key vault. b. assign a managed identity to the azure app configuration instance. c. configure a private endpoint for the azure app configuration instance. d. configure managed identity permission to access the azure key vault. e. create a dns cname resource record for the azure app configuration instance.
Answers
(b) assign a managed identity to the azure app configuration instance and (d) configure managed identity permission to access the azure key vault are the two actions that need to perform for this situation.
What is the azure key vault?
By leveraging keys that are guarded by hardware security modules, Microsoft Azure Key Vault, a cloud-hosted management solution, enables customers to encrypt keys and tiny secrets (HSMs). Small secrets include passwords and other data that is less than 10 KB in size. PFX documents
Both managed hardware security module (HSM) pools and vaults are supported by the Key Vault service. Keys, secrets, and certificates secured by an HSM can be stored in vaults. Managed HSM pools only accept keys with an HSM backup.
To learn more about the azure key vault, use the link given
https://brainly.com/question/29433704
#SPJ1
In which situation would an ESD strike potentially cause harm to the PC?
when replacing a mechanical hard drive with an M.2 SSD
when installing an additional display in a workplace cubicle
when using a grounded mat and working on a computer on an ungrounded workbench
when installing a dual-voltage power supply
Answers
An ESD strike could potentially cause harm to a PC when using a grounded mat and working on a computer on an ungrounded workbench. ESD occurs when there is a sudden flow of electricity between two objects that have different electric potentials. So the third option is correct answer.
ESD(electrostatic Discharge) discharge can happen when there is a build-up of static electricity on a person or an object, and then that charged object comes into contact with an electronic component. Without proper grounding, the buildup of static electricity can discharge through the PC components, causing damage to sensitive electronic parts.
It is important to always use proper grounding techniques and equipment when working on electronics to prevent potential damage from ESD strikes. So the correct answer is third option "when using a grounded mat and working on a computer on an ungrounded workbench"
To learn more about potential: https://brainly.com/question/26978411
#SPJ11
These statements describe a network server.
assigns MACs
manages network resources
provides network security
translates data sent between networks
Answers
Answer:
The statement that describes a network server is:
manages network resources
Explanation:
A server is a computer built and programmed to fulfill network needs. They might be able to perform regular computer tasks, but they are designed specially to connect several computers, create a space those computers can share, provide connectivity management to them and be able to receive, send, create, and copy data inside that network. In other words, it creates a space of interaction, allows interaction, and transfer data from this network to other networks and from other networks for its managed network.
What would you fix or improve in our current technology to make life better for all?
Answers
Based on the following quote from Leonardo Da Vinci, what would be his definition of a fine artist? “Principles for the Development of a Complete Mind: Study the science of art. Study the art of science. Develop your senses- especially learn how to see. Realize that everything connects to everything else.” - Leonardo da Vinci
A fine artist must discover the world for herself and not listen to others’ interpretations.
A fine artist is one who sees things others don’t see and makes connections others don’t make.
A fine artist is a scientific genius who cultivates the power of observation.
A fine artist must first be scientist and use science to improve his art.
Please hurry :(
Answers
Answer:
A fine artist is one who sees the things other don't see and make connections other don't make.
Answer:
I think it is
A fine artist is one who sees things others don’t see and makes connections others don’t make.
(50 POINTS)Look at the code in the example below, and then answer the question.
In the example code, what does the title attribute create?
a tool tip
an element
a source
a markup
Answers
Answer:
I think it is:
B. An ElementExplanation:
1. Which is NOT a type of file that InDesign cannot use.
a. Graphics
b. Text Files
c. InDesign Files
d. None of the above
2. You cannot resize a graphic once you put an image in InDesign.
true or false
Answers
Answer: 1. InDesign 2. False
Explanation:
A type of file that InDesign cannot use is known as InDesign File. Thus, the correct option for this question is C.
The statement "You cannot resize a graphic once you put an image in InDesign" is absolutely false.
What do you mean by an InDesign file?An InDesign file may be defined as a type of desktop publishing software application that is significantly utilized for creating flyers, brochures, magazines, newspapers, books, and other publications.
The types of files that InDesign can remarkably use for operating its well-known function of constructing literary works like magazines, newspapers, books, etc. are graphics, text files, editing files, animation files, etc.
In the InDesign application software, you can generally resize or modify a graphic once you put an image in InDesign. This is facilitated by a tool known as an editing tool.
Therefore, both the questions given above are well described.
To learn more about InDesign application software, refer to the link:
https://brainly.com/question/14478872
#SPJ2
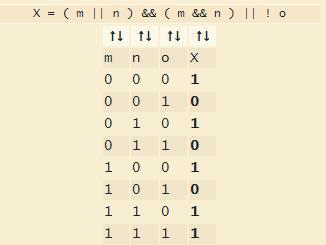
Draw a truth table & logic circuit corresponding to the following logic statement
X = 1 if ( ( M is 1 OR N is 1 ) AND ( M is 1 AND N is 1 ) ) OR ( O is NOT 1 )
Answers
Answer:
The truth table, as well as the logic circuit of the given statement, is attached below.
Explanation:
Logical gates seem to be the essential building blocks of just about any computerized signal. It becomes a digital device with one or even more inputs and therefore only single output. The arrangement among outputs and inputs would be focused on this kind of logic. Upon that basis, logic gates were already called as AND, NOT, OR gate, etc.

Please give answers between 500 words.
What have been the major issues and benefits in
Electronic Data Interchanges (EDI) and Web-Based/Internet
Tools?
Answers
The major issues and benefits of electronic data interchange (EDI) and web-based/Internet tools, such as compatibility and standardization, privacy, cost, dependence on internet connectivity, etc.,
One of the challenges of EDI is that it is ensuring compatibility between different systems and also establishing standardized formats for data exchange. It requires agreement and coordination among trading partners in order to ensure the seamless communication, while there are many benefits that include EDI and web-based tools that enable faster and more efficient exchange of information, eliminating manual processes, paperwork, and potential errors. Real-time data exchange improves operational efficiency and enables faster decision-making. Apart from this, there are many other benefits to these.
Learn more about EDI here
https://brainly.com/question/29755779
#SPJ4
1.
The correct way to use a seat belt is
Answers
Answer:
4 steps
Explanation:
Step 1: Pull belt across body
Sit in any of your vehicle's seats and secure the three-point harness in its buckle by pulling it across your body.
If the seatbelt is too short, consider an aftermarket restraint and extender. Make sure they meet federal safety standards and are installed professionally.
Step 2: Adjust lower belt
Adjust the lower belt snuggly across your lap and pelvis area – never your stomach.
Pregnant women should wear the lap belt below their belly, not on or above it.
Step 3: Adjust shoulder belt
Adjust the shoulder belt to fit comfortably across the collarbone and chest. It should never rub on your neck or face. Never put the shoulder belt behind your back or under your arm.
Step 4: Check before driving
Check that the belt is secure before driving.
Answer: across your hips, and across your body over your collar bone
Explanation:
that’s how a seat belt should be worn
Refer to the exhibit. Baseline documentation for a small company had ping round trip time statistics of 36/97/132 between hosts H1 and H3. Today the network administrator checked connectivity by pinging between hosts H1 and H3 that resulted in a round trip time of 1458/2390/6066. What does this indicate to the network administrator
Answers
Answer:
Explanation:
https://examict.com/refer-to-the-exhibit-baseline-documentation-for-a-small-company-had-ping-round-trip-time-statistics-of-36-97-132-between-hosts-h1-and-h3-today-the-network-administrator-checked-connectivity-by-pingi/
How do you write mathematical expressions that combine variable and literal data
Answers
Variables, literal values (text or integers), and operators specify how the expression's other elements are to be evaluated. Expressions in Miva Script can generally be applied in one of two ways: Add a fresh value.
What connection exists between literals and variables?Literals are unprocessed data or values that are kept in a constant or variable. Variables can have their values updated and modified since they are changeable. Because constants are immutable, their values can never be updated or changed. Depending on the type of literal employed, literals can be changed or remain unchanged.
What kind of expression has one or more variables?The concept of algebraic expressions is the use of letters or alphabets to represent numbers without providing their precise values. We learned how to express an unknown value using letters like x, y, and z in the fundamentals of algebra. Here, we refer to these letters as variables.
to know more about mathematical expressions here:
brainly.com/question/28980347
#SPJ1
1. A Bitonic Merge network of size n takes a bitonic sequence of length n elements as input and produces a monotonic sequence of length n. Derive an exact expression for the total number of comparisons performed in a Bitonic Merge network of size n. Explain. n 2. A Bitonic Sorting network of size n takes an arbitrary sequence of length n as input and produces a sorted sequence. Derive an exact expression for the number of comparisons performed in a Bitonic Sorting network of size n. Explain.
Answers
The number of comparisons performed by a Bitonic Sorting network of size n is proportional to n*log2^2(n).
What is a Bitonic Merge network, and what is its input and output?For a Bitonic Merge network of size n, the total number of comparisons performed can be derived as follows:First, we note that a bitonic sequence of length n can be obtained by sorting two bitonic sequences of length n/2 in opposite orders and then concatenating them. Therefore, a Bitonic Merge network of size n can be constructed recursively by combining two Bitonic Merge networks of size n/2, each performing n/2 comparisons, and then performing n/2 additional comparisons to merge the two resulting bitonic sequences.
Let C(n) be the total number of comparisons performed by a Bitonic Merge network of size n. Then we have:
C(n) = 2*C(n/2) + n/2
This recurrence relation can be solved using the Master Theorem, which gives us the following expression for C(n):
C(n) = O(n*log2(n))
Therefore, the total number of comparisons performed by a Bitonic Merge network of size n is proportional to n*log2(n).
For a Bitonic Sorting network of size n, the number of comparisons performed can be derived as follows:A Bitonic Sorting network of size n can be constructed recursively by sorting two sub-sequences of length n/2 in opposite orders, and then merging them using a Bitonic Merge network of size n. Therefore, the total number of comparisons performed by a Bitonic Sorting network of size n can be expressed as:
C(n) = 2*C(n/2) + n*log2(n)
The first term on the right-hand side accounts for the number of comparisons performed by the two recursive calls to sort the sub-sequences, and the second term accounts for the number of comparisons performed by the Bitonic Merge network of size n.
Using the Master Theorem, we can solve this recurrence relation to obtain the following expression for C(n):
C(n) = O(n*log2^2(n))
The number of comparisons performed by a Bitonic Sorting network of size n is proportional to n*log2^2(n).
Learn more about Bitonic Sorting network
brainly.com/question/31430899
#SPJ11
____ includes) all tools that capture, store, process, exchange, and use information.
. information technology
b. business technology
c. information systems
d. data systems
Answers
Information systems includes all tools that capture, store, process, exchange, and use information.
What is Information technology?Information technology (IT) exists the usage of any computers, storage, networking, and other physical devices, infrastructure, and techniques to create, process, store, secure, and exchange all formats of electronic data. The most basic information technology definition exists that it's the application of technology to translate business or organizational problems on a broad scale.
Information technology exists through the use of computers to create, process, store, retrieve, and exchange all types of data and information. IT is commonly used within the context of business operations as objected to personal or entertainment technologies. IT includes part of information and communications technology.
Hence, Information systems includes all tools that capture, store, process, exchange, and use information. Option C is correct.
To learn more about Information technology refer to:
https://brainly.com/question/28245605
#SPJ4
describe what is the generative adversarial net and how it works
Answers
A generative adversarial network (GAN) is a type of machine learning model in which two neural networks work together to generate new data.
The GAN consists of a generator and a discriminator network that is used to create artificial data that looks like it came from a real dataset. The generator network is the one that produces the fake data while the discriminator network evaluates it. The two networks play a "cat-and-mouse" game as they try to outsmart one another. The generator takes a random input and creates new examples of data. The discriminator examines the generated data and compares it to the real dataset. It tries to determine whether the generated data is real or fake. The generator uses the feedback it gets from the discriminator to improve the next batch of generated data, while the discriminator also learns from its mistakes and becomes better at distinguishing between real and fake data.
The generator's goal is to create artificial data that is similar to the real data so that the discriminator will be fooled into thinking it is real. On the other hand, the discriminator's goal is to correctly identify whether the data is real or fake. By playing this game, both networks improve their abilities, and the result is a generator that can create realistic artificial data.
Learn more about generative adversarial network (GAN) here: https://brainly.com/question/30072351
#SPJ11
As with most professions, photography comes with its own unique set of terms and jargon. Identify at least four different words related to photography, define, and use them in a sentence that expresses their meaning in relation to the field.
Answers
Answer: See explanation
Explanation:
The words associated with photography include:
1. Filter: It is a device that is used to remove a certain form of light. It is usually placed on the lens of the camera when one wants to change the light or color.
John used different filter on his camera.
2. Camera : This is an equipment that is used to take photographs or make movies.
A new camera was bought by Ruth.
3. Photo book: This is a published book that contains photographs.
Bob knows a website where one can order photo books that are custom made.
4. Picture: This is a photograph or an image that can be seen on the television.
John took a picture of Tom when he was dancing.
5. Air brush: A machine that isused for painting or to improve the work done on a photograph.
The wrinkles on my grandma's face were airbrushed out.
Answer:(Aperture) is the first common photography term you should learn. Simply put, aperture is the size of the opening in the lens. Think of the lens as a window—large windows or wide angles let in more light, while small windows let in less light. A wide open aperture will let more light into the image for a brighter photo, while a smaller aperture lets in less light. (Aspect Ratio) If you’ve ever printed images before, you’ve probably noticed that an 8 x 10 usually crops from the original image. That’s due to aspect ratio (Bokeh) is the orbs created when lights are out of focus in an image.
Terrance is looking for a storage device to be used for backup storage. The device has to have a large storage capacity and be portable. What is the best device for Terrance's needs?
External hard drive
Disk drive
Hard drive
USB flash drive
Answers
Answer:
its external hard drive and flash drive
Your welcome
Explanation:
what do you call a setup where microsoft access is stored on a file server and three trusted users access the database from their local computers?
Answers
The setup where Microsoft Access is stored on a file server and three trusted users access the database from their local computers is commonly referred to as a client-server configuration.
In this configuration, the file server acts as the central location where the Microsoft Access database file is stored, while the local computers of the trusted users act as the clients that connect to and interact with the database.
The users can access and manipulate the database remotely by establishing a connection to the file server over a network, allowing them to work with the database concurrently and share data and resources.
To learn more about Microsoft Access: https://brainly.com/question/24643423
#SPJ11
Households can save approximately 6% off their electricity bill by running their dishwasher and washing machines off peak. On average how much can they cut off their bill if the bill for the year is $1000.
Answers
Answer: like up to 75%
Which of the follow efficiencies would be considered unreasonable?
Answers
Answer:
Exponential or factorial efficiencies algorithms
Explanation:
In a computer engineering system, the efficiencies that would be considered unreasonable is the "Exponential or factorial efficiencies algorithms"
This is unlike Algorithms with a polynomial efficiency that is considered to have Reasonable Time.
David is repairing a desktop that has begun to overheat. upon inspection, he found that the cpu cooling fan has a buildup of dust blocking air flow. david corrected this issue and the fan is now working properly, but after long periods of use overheating still occurs. which factors would you change to resolve this issue?
Answers
Despite cleaning the CPU cooling fan, if David's desktop is still heating up, then there are multiple aspects that might be contributing to the issue.
To assist him in resolving it, here are a few possible solutions he could attempt:Inspect the thermal paste: An absence of thermal paste between the heatsink and CPU may block heat from being dissipated away from the processor. If so, reapplying it carefully may address the problem.
Augment air flow: The inadequate air passage inside David's computer case could be exacerbating overheating. For this, adding further ventilation fans or advancing the cable management within his enclosure may alleviate circulation.
Substitute the heatsink: Too little of an efficient heatsink, as well as improper assembly, may also contribute to affecting his CPU temperature. To counter this, David can consider exchanging his current one with a more proficient model while making sure to set it up conveniently.
Evaluate CPU usage: Prolonged, strenuous use of his processor could generate immense amounts of heat, as well. Thus, David should systematically assess the utilization of his CPU by closely monitoring it, potentially upgrading the component or integrating more cooling apparatuses if necessary.
Read more about troubleshooting here:
https://brainly.com/question/25953942
#SPJ1
what do you think of the FNAF plus trailer? if you have seen it tell me who looks better

Answers
Answer:
Explanation:
bonnie looks the best, freddy looks better, and chica looks awsome, in my opinion this looks better than the original fnaf
Answer:
honestly Bonnie looks best
Explanation:
kelsan informatics has its client computers connected to a router through which the clients can access the organization's servers in the dmz. the dmz is connected to a nat router that is connected to the internet. in addition to providing access to the internet, the nat router also offers additional capabilities, such as traffic throttling, intrusion prevention, and malware filtering. what is the term for this type of nat router?
Answers
The type of NAT router that Kelsan Informatics has connected its client to is this: Security Gateway router.
What is the Security Gateway router?The security gateway router is a form of router that not only serves the function of providing an internet connection but can also proof the devices from harmful connections.
Other functionalities of this router include traffic throttling and intrusion prevention. So, the security architecture is designed to prevent breaches from external sources.
Learn more about NAT routers here:
https://brainly.com/question/30532554
#SPJ1