Flavia is focused on making fewer mistakes when she types. what is she trying to improve most
Answers
Flavia is primarily trying to improve her typing accuracy. By focusing on making fewer mistakes when typing, she aims to minimize errors in her written work, enhance productivity, and improve the overall quality of her typing.
This could include reducing typographical errors, misspellings, punctuation mistakes, or other inaccuracies that may occur while typing. By honing her typing skills and striving for precision, Flavia can become more efficient and produce more polished written content.
Flavia is trying to improve her typing accuracy and reduce the number of mistakes she makes while typing. She wants to minimize errors such as typos, misspellings, and incorrect keystrokes. By focusing on making fewer mistakes, Flavia aims to enhance her overall typing speed and efficiency.
Learn more about typographical errors on:
https://brainly.com/question/14470831
#SPJ1
Related Questions
Help please I'm making you the brainliest!!! please answer it seriously thank you have a nice day..(You don't have to answer all questions but please answer most of it thank you!)

Answers
Answer:
7. Relevancy
8. Contextualization
9. Directness
10. Efficiency
11. Maximizing
12. Organization
13. Underscoring
Explanation:
I answered the questions based on my knowledge and additional research. Hope this helps.
a democratic government has to respect some rules after winning the elections. Which of these points is not a part of those rules
Answers
After coming to power, a democratic administration is bound to follow certainrules and regulations. And Office-bearers are not accountable is not a part of those rules.
How is this so?In a democratic administration,office-bearers are indeed accountable as they are bound by rules and regulations.
The accountability ensures transparency,ethical conduct, and adherence to the principles of democracy.
Office-bearers are expected to uphold the laws and serve the interests of the people they represent.
Learn more about democratic administration at:
https://brainly.com/question/31766921
#SPJ1
Which strategies should be used to answer short answer or essay questions? Check all that apply
D comparing items
O looking tor key words such as 'compare" or "contrast
Oallowing extra time to answer
Oidentifying warning words such as "absolutes"
D checking the space for writing the answer
Answers
Answer:
B
Explanation:
correct me if im wrong
The strategies that should be used to answer short answer or essay questions are as follows:
Looking for keywords such as 'compare" or "contrast.Checking the space for writing the answer.Thus, the correct options for this question are B and D.
What do you mean by writing strategy?The writing strategy may be defined as the entire sequence in which a writer engages in planning, composing, revising, and other writing-related activities in any literary work. In their opinion, writing strategies are a sequence of activities instead of a single one.
There are five writing strategies for writing simply but authoritatively and effectively are as follows:
Use simpler words and phrases.Minimize the number of negatives in a sentence.Write shorter sentences, but avoid choppiness.Use important key terms consistently.Balance the use of simple and sophisticated language.Therefore, the correct options for this question are B and D.
To learn more about Writing strategies, refer to the link:
https://brainly.com/question/27836380
#SPJ2
Convert the following to CNF: S→SS|AB|B A→aAAa B→ bBb|bb|Ꜫ C→ CC|a D→ aC|bb
Answers
To convert the given grammar into Chomsky Normal Form (CNF), we need to rewrite the rules and ensure that each production has only two non-terminals or one terminal on the right-hand side. Here is the converted CNF grammar:
1. S → SS | AB | B
2. A → AA
3. A → a
4. B → bBb | bb | ε
5. C → CC | a
6. D → aC | bb
Explanation:
1. The production S → SS has been retained as it is.
2. The production A → aAAa has been split into A → AA and A → a.
3. The production B → bBb has been split into B → bB and B → b.
4. The production B → bb has been kept as it is.
5. The production B → ε (empty string) has been denoted as B → ε.
6. The production C → CC has been retained as it is.
7. The production C → a has been kept as it is.
8. The production D → aC has been kept as it is.
9. The production D → bb has been kept as it is.
In summary, the given grammar has been converted into Chomsky Normal Form (CNF), where each production has either two non-terminals or one terminal on the right-hand side. This form is useful in various parsing and analysis algorithms.
For more questions on parsing, click on:
https://brainly.com/question/13211785
#SPJ8
Answer:
Explanation:
To convert the given grammar to Chomsky Normal Form (CNF), we need to follow a few steps:
Step 1: Eliminate ε-productions (productions that derive the empty string).
Step 2: Eliminate unit productions (productions of the form A → B).
Step 3: Convert long productions (productions with more than two non-terminals) into multiple productions.
Step 4: Convert terminals in remaining productions to new non-terminals.
Step 5: Ensure all productions are in the form A → BC (binary productions).
Applying these steps to the given grammar:
Step 1: Eliminate ε-productions
The given grammar doesn't have any ε-productions.
Step 2: Eliminate unit productions
The given grammar doesn't have any unit productions.
Step 3: Convert long productions
S → SS (Remains the same)
S → AB
A → aAAa
B → bBb
B → bb
C → CC
C → a
D → aC
D → bb
Step 4: Convert terminals
No changes are needed in this step as all terminals are already in the grammar.
Step 5: Ensure binary productions
The given grammar already consists of binary productions.
The converted grammar in Chomsky Normal Form (CNF) is:
S → SS | AB
A → aAAa
B → bBb | bb
C → CC | a
D → aC | bb
Note: The original grammar didn't include the production rules for the non-terminals 'S', 'C', and 'D'. I assumed the missing production rules based on the provided information.
9.3 code practice
Write a program that creates a 4 x 5 array called numbers. The elements in your array should all be random numbers between -30 and 30, inclusive. Then, print the array as a grid.
For instance, the 2 x 2 array [[1,2],[3,4]] as a grid could be printed as:
1 2
3 4
Sample Output
18 -18 10 0 -7
-20 0 17 29 -26
14 20 27 4 19
-14 12 -29 25 28
Note: the numbers generated in your program will not match the sample output, as they will be randomly generated.
pls help
Answers
The program is an illustration of arrays; Arrays are variables that are used to hold multiple values of the same data type
The main programThe program written in C++, where comments are used to explain each action is as follows:
#include <iostream>
#include <cstdlib>
#include <ctime>
using namespace std;
int main(){
//This declares the array
int myArray[4][5];
//This seeds the time
srand(time(NULL));
//The following loop generates the array elements
for(int i = 0; i< 4;i++){
for(int j = 0; j< 5;j++){
myArray[i][j] = rand()%(61)-30;
}
}
//The following loop prints the array elements as grid
for(int i = 0; i< 4;i++){
for(int j = 0; j< 5;j++){
cout<<myArray[i][j]<<" ";
}
cout<<"\n";
}
return 0;
}
Read more about arrays at:
https://brainly.com/question/22364342
xamine the following output:
Reply from 64.78.193.84: bytes=32 time=86ms TTL=115
Reply from 64.78.193.84: bytes=32 time=43ms TTL=115
Reply from 64.78.193.84: bytes=32 time=44ms TTL=115
Reply from 64.78.193.84: bytes=32 time=47ms TTL=115
Reply from 64.78.193.84: bytes=32 time=44ms TTL=115
Reply from 64.78.193.84: bytes=32 time=44ms TTL=115
Reply from 64.78.193.84: bytes=32 time=73ms TTL=115
Reply from 64.78.193.84: bytes=32 time=46ms TTL=115
Which of the following utilities produced this output?
Answers
The output provided appears to be from the "ping" utility.
How is this so?Ping is a network diagnostic tool used to test the connectivity between two network devices,typically using the Internet Control Message Protocol (ICMP).
In this case, the output shows the successful replies received from the IP address 64.78.193.84,along with the response time and time-to-live (TTL) value.
Ping is commonly used to troubleshoot network connectivity issues and measureround-trip times to a specific destination.
Learn more about utilities at:
https://brainly.com/question/30049978
#SPJ1
3.6 Code Practice on Edhesive
** Python Language **
This is an algorithm code problem but we didn't learn anything in this lesson. Please keep it simple and not super complicated because I and many people who need to know this are new coders to Python. Thanks!
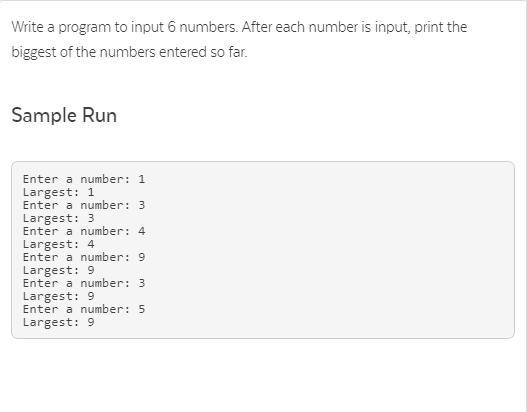
Answers
I've included my code in the picture below. Best of luck.

Programs for embedded devices are often written in assembly language. Some embedded processors have limited instructions, like MARIE. Create a MARIE program which determines whether a given address is a cache hit or not. For this assignment, the cache is 2-way set associative, addresses are 8 bits, blocks are 8 bytes, and the cache has 8 blocks.
Requirements
1. The program must be written in MARIE.
2. The input is a hex address (2 hex digits), the output is 1 for a cache hit and 0 for a cache miss.
3. The cache table is
Set 0 1 5
Set 1 2 4
Set 2 3 2
Set 3 6 0
4. Unlike a real memory system, for this assignment, the cache table won’t change on a cache miss.
Hints: 1.
You have already written a multiply subroutine for MARIE. You could use a similar integer divide subroutine for this. It could return both a quotient and a remainder.
2. I recommend writing this in Java or C++ first to test your algorithm. Write the divide method using repeated subtraction as you will in MARIE.
3. The textbook describes the LoadI instruction, but the MARIE simulator does not recognize that. You can accomplish the same thing using Clear and AddI.
Upload: Your MARIE source file (.mas)
Sample Output
Input: B5, Output: 0
Input: A5, Output: 1
Input: 6C, Output: 0
Input: 7D, Output: 0
Input: 8B, Output: 1
Answers
Answer:
#include <iostream>
using namespace std;
int main()
{
char address[2];
int tag, firstBit, secondBit, setNumber;
int cache[4][2]={{1,5}, {2,4}, {3,2}, {6,0}};
cout << "Enter the address as hex(in small letters: "<
cin >> address;
for (int i < 0; i < 8; i++){
if (address[0] == '0'){
tag = 0;
firstBit = 0;
} else if (address[0] == '1'){
tag = 0;
firstBit = 1;
} else if (address[0] == '2'){
tag =1;
firstBit = 0;
} else if (address[0] == '3'){
tag = 1;
firstBit = 1;
} else if (address[0] == '4'){
tag = 2;
firstBit = 0;
} else if (address[0] == '5'){
tag = 2;
firstBit = 1;
} else if (address[0] == '6'){
tag = 3;
firstBit = 0;
} else if (address[0] == '7'){
tag = 3;
firstBit = 1;
} else if (address[0] == '8'){
tag = 4;
firstBit = 0;
} else if (address[0] == '9'){
tag = 4;
firstBit = 1;
} else if (address[0] == 'A'){
tag = 5;
firstBit = 0;
} else if (address[0] == 'B'){
tag = 5;
firstBit = 1;
} else if (address[0] == 'C'){
tag = 6;
firstBit = 0;
} else if (address[0] == 'D'){
tag = 6;
firstBit = 1;
} else if (address[0] == 'E'){
tag = 7;
firstBit = 0;
} else if (address[0] == 'F'){
tag = 7;
firstBit = 1;
} else{
cout<<"The Hex number is not valid"<< endl;
}
}
if(address[1]>='0' && address[1]<'8'){
secondBit = 0;
} else if(address[1]=='8'|| address[1]=='9'||(address[1]>='a' && address[1]<='f')){
secondBit = 1;
} else{
cout<<"The Hex number is not valid"<< endl;
return 0;
}
setNumber = firstBit * 2 + secondBit;
if(cache[setNumber][0]==tag || cache[setNumber][1]==tag){
cout<<"There is a hit";
} else{
cout<< "There is a miss";
}
return 0;
}
Explanation:
The C++ source code prompts the user for an input for the address variable, then the nested if statement is used to assign the value of the firstBit value given the value in the first index in the address character array. Another if statement is used to assign the value for the secondBit and then the setNumber is calculated.
If the setNumber is equal to the tag bit, Then the hit message is printed but a miss message is printed if not.
savannah is studying agriscience in class and needs to list three challenged facing agricultural industry today. which of the following would best complete her list?
A.soil depletion
B.improvements in irrigation
C.new hybrid crops
D.advancements in technology
Answers
Answer: A,C,D
Explanation:
will a printer with a usb 3.0 port work on a usb 2.0 port?
Answers
Answer:
Yes
Explanation:
USB 3.0 backwards is compatible—meaning it's designed to work with older USB versions including USB 2.0 and USB 1.1. ... So, if you plug a USB 3.0 flash drive into a USB 2.0 port, it would only run as quickly as the USB 2.0 port can transfer data and vice versa.
Onsite Services for Ruggedized Notebooks are limited to CRU parts and Service Assembly
Parts.
True
False
Answers
Onsite Services for Ruggedized Notebooks are limited to CRU parts and Service Assembly is a false statement.
What are Onsite Services?In an On-Site Service, a Service Provider is one that carry out any kind of repair or exchange of a product at given location that is the location of the customer.
Onsite Services for Ruggedized Notebooks is not limited to CRU parts and Service Assembly as one can do any form of system repairs there most especially based on customer preference or what is wrong with the system.
Learn more about Onsite Services from
https://brainly.com/question/11218668
Question 8 A data analyst is working with a data frame named stores. It has separate columns for city (city) and state (state). The analyst wants to combine the two columns into a single column named location, with the city and state separated by a comma. What code chunk lets the analyst create the location column
Answers
The programing language, R has a unite unite function in the tidyr package. Hence, the code chunk which let's the analyst create the location column is; unite (stores, "location”, city, state, sep=",")
The syntax for the unite function is ; unite(data,col,..., sep)data = dataframe from which data is to be extracted `; stores col = name of the new column ;" location"... = dataframes to be merged ; city, statesep = seperator ; ","Hence, the required syntax goes thus :
unite (stores, "location”, city, state, sep=",")Learn more : https://brainly.com/question/25534959
chrome explorer firefox are the examples of
Answers
Answer: Browsers
Explanation: They are all Search Engines, also called browsers.
Which type of game is least likely to need a structured narrative?
a first-person shooter, ,
an adventure game ,
a role-playing game ,
a sports game
Question 4
Answers
Answer:
an adventure game
Explanation:
It is this because people explore more than rather have certain dialouge or storylines like perspective games. so in that case i hope this answer helps!!!
Identify two stages of processing instructions
Answers
Answer:
1. Fetch instruction from memory.
2. Decode the instruction.
What Is OpenShift Deployment?
Answers
Deploying applications on OpenShift, a Red Hat-designed container application platform, is an involved process that compiles the lifecycle management of the application, its horizontal and vertical scaling abilities, updates rolling out, and ensuring the application’s health and reliability.
How to explain the informationUnlocking these toolsets can be made easier with OpenShift's powerful selection of programmes and features which automate deployment while also monitoring and logging.
It also provides essential Continuous Integration and Deployment (CI/CD) pipelines to streamline the development process.
Learn more about deployment on
https://brainly.com/question/30259268
#SPJ1
System testing – During this stage, the software design is realized as a set of programs units. Unit testing involves verifying that each unit meets its specificatio
Answers
System testing is a crucial stage where the software design is implemented as a collection of program units.
What is Unit testing?Unit testing plays a vital role during this phase as it focuses on validating each unit's compliance with its specifications. Unit testing entails testing individual units or components of the software to ensure their functionality, reliability, and correctness.
It involves executing test cases, evaluating inputs and outputs, and verifying if the units perform as expected. By conducting unit testing, developers can identify and rectify any defects or issues within individual units before integrating them into the larger system, promoting overall software quality.
Read more about System testing here:
https://brainly.com/question/29511803
#SPJ1
Describe a situation in which there could be a conflict of interest between an IT worker’s self-interest and the interests of a client. How should this potential conflict be addressed?
Answers
A situation in which there could be a conflict of interest between an IT worker’s self-interest and the interests of a client this potential conflict be addressed state of affairs wherein there may be a battle of hobby among an IT worker.
Which of the subsequent conditions might doubtlessly provide upward thrust to a battle of hobby?A battle of hobbies takes place whilst an individual's non-public hobbies – family, friendships, economic, or social factors – ought to compromise his or her judgment, decisions, or moves withinside the workplace. Government businesses take conflicts of hobby so critically that they're regulated.
A state of affairs wherein there may be a battle of hobby among an IT worker self-hobby and the hobbies of a purchaser is the transport of the product can be uncertain. The purchaser might also additionally need the product early at the same time as employees can not enforce the product withinside the time frame.
Read more about the potential :
https://brainly.com/question/14427111
#SPJ1
tools used to type text on Ms paint
Answers

Which software programs should students avoid using to create and submit course work? (Choose all that apply).
Word
Pages
Numbers
Keynote
Answers
The instructions for the OS provided by application software are known as _____.
interfaces
GUIs
system calls
RAMs
Answers
hope this helps out with anything it can
What is the Web of Trust?
A.
a group of experts who rate reviews as good or bad
a group of experts who analyze reviews before they go online
O B.
C.
a group of reviewers who review products frequently
D.
a group of reviewers with your highest ratings
Answers
Answer:
A will be the answer because the people who analyze the reviews are building a trust between the people
By using your own data, search engines and other sites try to make your web experience more personalized. However, by doing this, certain information is being hidden from you. Which of the following terms is used to describe the virtual environment a person ends up in when sites choose to show them only certain, customized information?
A filter bubble
A clustered circle
A relational table
An indexed environment
Answers
Answer:
A filter bubble
Explanation:
You are going on vacation and want to take some work files. You need a storage device that is small enough to fit in your bag and preferably one that does not have plugs. Which device should you bring?
hard drive bus
flash drive
external hard drive
storage card
Answers
Answer:
Flash drive
Explanation:
In Java only please:
4.15 LAB: Mad Lib - loops
Mad Libs are activities that have a person provide various words, which are then used to complete a short story in unexpected (and hopefully funny) ways.
Write a program that takes a string and an integer as input, and outputs a sentence using the input values as shown in the example below. The program repeats until the input string is quit and disregards the integer input that follows.
Ex: If the input is:
apples 5
shoes 2
quit 0
the output is:
Eating 5 apples a day keeps you happy and healthy.
Eating 2 shoes a day keeps you happy and healthy
Answers
Answer:
Explanation:
import java.util.Scanner;
public class MadLibs {
public static void main(String[] args) {
Scanner input = new Scanner(System.in);
String word;
int number;
do {
System.out.print("Enter a word: ");
word = input.next();
if (word.equals("quit")) {
break;
}
System.out.print("Enter a number: ");
number = input.nextInt();
System.out.println("Eating " + number + " " + word + " a day keeps you happy and healthy.");
} while (true);
System.out.println("Goodbye!");
}
}
In this program, we use a do-while loop to repeatedly ask the user for a word and a number. The loop continues until the user enters the word "quit". Inside the loop, we read the input values using Scanner and then output the sentence using the input values.
Make sure to save the program with the filename "MadLibs.java" and compile and run it using a Java compiler or IDE.
Display “Welcome to (your name)’s fuel cost calculator.”
Ask the user to enter name of a trip destination.
Ask the user to enter the distance to that trip destination (in miles) and the fuel efficiency of their car (in mpg or miles per gallon).
Calculate the fuel required to get to destination and display it.
Use the formula: Fuel amount = Distance / Fuel efficiency, where Fuel is in gallons, Distance is in miles and Fuel efficiency is in miles per gallon.
Your program should follow Java convention for variable names (camelCase).
Ask the user to enter fuel price (in dollars per gallon) in their area.
Compute trip cost to get to destination and display it.
Use the formula: Trip fuel cost = Fuel amount x Fuel price, where trip fuel cost is in dollar amount, fuel is in gallons, and fuel price is in dollars per gallon.
You need to convert this mathematical formula to a Java statement. Be sure to use the right operator symbols! And, as before, follow Java convention for variables names (camelCase).
Compute and display total fuel cost for round trip, to reach and return from destination, using the formula: Round Trip Fuel Cost = 2 x Trip fuel cost
You need to convert this mathematical formula to a Java statement!
Compute and display number of round trips possible to Nashville, 50 miles away, with $40 worth of fuel. Use the fuel efficiency and fuel price entered by user earlier. Perform the computation in parts:
One can compute how much fuel can be bought with $40 from:
Fuel bought = Money available / Fuel cost = 40 / Fuel price, where fuel bought is in gallons and fuel price is in dollars per gallon.
One can compute fuel required for one round trip:
Fuel round trip = 2 * distance / fuel efficiency = 2 * 50 / fuel efficiency, where fuel round trip is in gallons and fuel efficiency is in miles per gallon
Compute number of round trips possible by dividing the amount of fuel that can be bought by the amount of fuel required for each round trip (Formula: round trips = fuel bought / fuel round trip).
Note that this value should be a whole number, and not a fraction.
Use integer division! Type cast the division quotient into int by writing (int) in front of the parenthesized division.
Display “Thank you for using (your name)’s fuel cost calculator.”
Answers
The code required is given as follows:
public class FuelCostCalculator {
public static void main(String[] args) {
System.out.println("Welcome to ChatGPT's fuel cost calculator.");
// Get user input
Scanner scanner = new Scanner(System.in);
System.out.print("Enter the name of the trip destination: ");
String destination = scanner.nextLine();
System.out.print("Enter the distance to " + destination + " (in miles): ");
double distance = scanner.nextDouble();
System.out.print("Enter your car's fuel efficiency (in miles per gallon): ");
double fuelEfficiency = scanner.nextDouble();
System.out.print("Enter the fuel price in your area (in dollars per gallon): ");
double fuelPrice = scanner.nextDouble();
// Calculate fuel required and trip cost
double fuelAmount = distance / fuelEfficiency;
double tripFuelCost = fuelAmount * fuelPrice;
double roundTripFuelCost = 2 * tripFuelCost;
// Calculate number of round trips possible to Nashville
double fuelBought = 40 / fuelPrice;
double fuelRoundTrip = 2 * 50 / fuelEfficiency;
int roundTrips = (int) (fuelBought / fuelRoundTrip);
// Display results
System.out.println("Fuel required to get to " + destination + ": " + fuelAmount + " gallons");
System.out.println("Trip fuel cost to " + destination + ": $" + tripFuelCost);
System.out.println("Round trip fuel cost to " + destination + ": $" + roundTripFuelCost);
System.out.println("Number of round trips possible to Nashville: " + roundTrips);
System.out.println("Thank you for using ChatGPT's fuel cost calculator.");
}
}
What is the rationale for the above response?The above Java code is a simple console application that calculates fuel costs for a trip based on user input. It takes in user inputs such as the destination name, distance, fuel efficiency, and fuel price.
The program then uses these inputs to calculate the fuel required to reach the destination, the trip fuel cost, round trip fuel cost, and the number of round trips possible to a nearby location. Finally, it outputs the results to the console. The code uses basic arithmetic operations and variable assignments to perform the calculations.
Learn more about Java at:
https://brainly.com/question/29897053
#SPJ1
Your goals as the IT architect and IT security specialist are to: Develop solutions to the issues that the specified location of IDI is facing. Develop plans to implement corporate-wide information access methods to ensure confidentiality, integrity, and availability. Assess risks and vulnerabilities with operating IT facilities in the disparate locations where IDI now functions and develop mitigation plans and implementation methods. Analyze the strengths and weaknesses in the current systems of IDI. Address remote user and Web site user’s secure access requirements. Develop a proposed budget for the project—consider hardware, software, upgrades/replacements, and consulting services. Prepare detailed network and configuration diagrams outlining the proposed change to be able to present it to the management. Develop and submit a comprehensive report addressing the learning objectives and your solutions to the issues within the scenario. Prepare a 10- to 15-slide PowerPoint presentation that addresses important access control, infrastructure, and management aspects from each location.
Answers
Te chequen casa para ver en su mouse hombre de doble
Name some areas in which computer are being used
Answers
Answer:
Computers play a role in every field of life. They are used in homes, business, educational institutions, research organizations, medical field, government offices, entertainment, etc.
Explanation:
Home
Computers are used at homes for several purposes like online bill payment, watching movies or shows at home, home tutoring, social media access, playing games, internet access, etc. They provide communication through electronic mail. They help to avail work from home facility for corporate employees. Computers help the student community to avail online educational support.
Medical Field
Computers are used in hospitals to maintain a database of patients’ history, diagnosis, X-rays, live monitoring of patients, etc. Surgeons nowadays use robotic surgical devices to perform delicate operations, and conduct surgeries remotely. Virtual reality technologies are also used for training purposes. It also helps to monitor the fetus inside the mother’s womb.
Entertainment
Computers help to watch movies online, play games online; act as a virtual entertainer in playing games, listening to music, etc. MIDI instruments greatly help people in the entertainment industry in recording music with artificial instruments. Videos can be fed from computers to full screen televisions. Photo editors are available with fabulous features.
Industry
Computers are used to perform several tasks in industries like managing inventory, designing purpose, creating virtual sample products, interior designing, video conferencing, etc. Online marketing has seen a great revolution in its ability to sell various products to inaccessible corners like interior or rural areas. Stock markets have seen phenomenal participation from different levels of people through the use of computers.
Education
Computers are used in education sector through online classes, online examinations, referring e-books, online tutoring, etc. They help in increased use of audio-visual aids in the education field.
Government
In government sectors, computers are used in data processing, maintaining a database of citizens and supporting a paperless environment. The country’s defense organizations have greatly benefitted from computers in their use for missile development, satellites, rocket launches, etc.
Banking
In the banking sector, computers are used to store details of customers and conduct transactions, such as withdrawal and deposit of money through ATMs. Banks have reduced manual errors and expenses to a great extent through extensive use of computers.
Business
Nowadays, computers are totally integrated into business. The main objective of business is transaction processing, which involves transactions with suppliers, employees or customers. Computers can make these transactions easy and accurate. People can analyze investments, sales, expenses, markets and other aspects of business using computers.
Training
Many organizations use computer-based training to train their employees, to save money and improve performance. Video conferencing through computers allows saving of time and travelling costs by being able to connect people in various locations.
Arts
Computers are extensively used in dance, photography, arts and culture. The fluid movement of dance can be shown live via animation. Photos can be digitized using computers.
Science and Engineering
Computers with high performance are used to stimulate dynamic process in Science and Engineering. Supercomputers have numerous applications in area of Research and Development (R&D). Topographic images can be created through computers. Scientists use computers to plot and analyze data to have a better understanding of earthquakes.
Malaysia..HP,Lenovo,dell
India,Asser,Asus
apple,ibm, Microsoft
Find the product solution of
Dr(r, θ) =
∂2u
∂r2
+
1
r
∂u
∂r
+
1
r
2
∂2u
∂θ2
= 0
Answers
R(r)Θ(θ)
where R(r) is the radial component and Θ(θ) is the angular component.
We can assume that the second term of the equation is separable, meaning that we can rewrite it as:
∂2u
∂θ2
= -λu
where λ is a separation constant.
Substituting this into the original equation, we get:
∂2u
∂r2
1
r
∂u
∂r
λ
r
2
u
= 0
Multiplying both sides by r^2, we get:
r^2
∂2u
∂r2
r
∂u
∂r
λu
= 0
This is a form of the Bessel differential equation, which has solutions of the form:
u(r) = AJv(√λr) + BYv(√λr)
where Jv and Yv are Bessel functions of the first and second kind, respectively, and A and B are constants determined by the boundary conditions.
Substituting this back into the product solution, we get:
Dr(r, θ) = (d^2/dt^2 + λ) [R(r)Θ(θ)]
This shows that the product solution is a linear combination of functions that satisfy the partial differential equation.
Bob is the HR manager at an IT firm. What kind of résumé would Bob like to look at?
O A.
OB.
C.
O D.
a résumé with a decorative font
a long, detailed résumé
a colorful résumé
a résumé that addresses their advertised needs
Reset
Next
Answers
Since Bob is the HR manager at an IT firm. The kind of résumé that Bob like to look at is option D. a résumé that addresses their advertised needs.
What is a résumé about?A résumé that addresses the advertised needs of the company will focus on the skills, experiences, and qualifications that are most relevant to the position being applied for.
It will also be clearly organized and easy to read, and will highlight the most important information in a way that is relevant to the company's needs.
In all, a résumé that addresses the advertised needs of the company is likely to be the most effective in communicating the candidate's skills and qualifications to Bob and other HR managers at the IT firm.
Learn more about résumé from
https://brainly.com/question/14218463
#SPJ1