Examples of the triple AAA's covered in the course lecture, which are used to grant access to a database or system containing Pll data, verifying a user's "need to know" includes: O Automation, Accounting and Autonomous O Authentication, Authorization and Auditing O Automation, Authentication and Encryption
Answers
The correct answer is: Authentication, Authorization, and Auditing.
Examples of the triple AAA's covered in the course lecture, which are used to grant access to a database or system containing Pll data, verifying a user's "need to know" includes: Authentication, Authorization, and Auditing.
1. Authentication: This is the process of verifying the identity of a user or system attempting to gain access. Common methods include usernames and passwords, biometrics, or multi-factor authentication.
2. Authorization: After authentication, this step determines what level of access and permissions the authenticated user has within the database or system. It helps to ensure that users can only access the data and resources they have a "need to know."
3. Auditing: This involves monitoring and recording user activities within the database or system to ensure compliance with security policies and to detect any unauthorized access or suspicious activities.
Learn more about the Authentication, Authorization, and Auditing :
https://brainly.com/question/29637182
#SPJ11
Related Questions
Where does the revolver get the IP address of a site not visited before?
the file server
the name server
the IP provider
the print spooler
Answers
Answer: The name server
Explanation:
Nameservers are part of a large database called the Domain Name System (DNS), which acts like a directory for devices and the IP addresses attached to them. What nameservers do is use this information to translate domain names into numerical IP addresses – the language our computers understand
can someone tell me why it says that and how i can fix it pls


Answers
View the image below for the answer.

Choose one skill needed to become Computer Network Administrator?
The ability to Drive.
The ability to Plan.
The ability to Code Software.
Answers
Answer:
I think 1 is ans of this question
what are the differences between desktop apps and cloud-based apps?
Answers
Cloud-Based Software (Advantages:)
Data is stored on the cloud, giving users access anytime and anywhere, as long as there is an Internet connection
It provides almost unlimited storage capacity; backing up files is made easier
Customers subscribe for software access instead of purchasing it; they pay for as little as they need
Provide multiple users access to information or systems from any device
May allow the offline option for users, increasing its flexibility
Enables utilization of only the features that will suit one’s business needs
(Disadvantages:)
Performance depends on the capacity of the Internet connection
May encounter network and connectivity problems
Poor internet connectivity may lower productivity levels
Lacks other functionalities and features which are present in their desktop versions
Storing company information on the cloud also makes data vulnerable to hackers and other cybersecurity threats
Ensuring data privacy may mean spending more for the implementation of security meas
Desktop Apps: (Advantages:)
An on-premise application that does not require an Internet connection
No connectivity problems that may slow down the process
Allows users to add more features because it runs locally
Some software works the same offline as it does online
(Disadvantages:)
Works only on the computer where it was installed; requires separate installation for every computer
The user is given the responsibility to make updates and upgrades
Need to contact software provider to help install and maintain the software (for the not off-the-shelf type of software)
Within a word processing program, predesigned files that have layout and some page elements already completed are called
text boxes
templates.
frames
typography
Answers
Answer:
I think it's B) templates
Sorry if it's wrong I'm not sure!!
Explanation:
Within a word processing program, predesigned files that have layout and some page elements already completed are called: B. templates.
In Computers and Technology, word processor can be defined as a processing software program that is typically designed for typing and formatting text-based documents. Thus, it is an application software that avail end users the ability to type, format and save text-based documents such as .docx, .txt, and .doc files.
A template refers to a predesigned file or sample in which some of its page elements and layout have already completed by the software developer.
In this context, predesigned files in a word processing program, that have layout and some page elements already completed by the software developer is referred to as a template.
Read more on template here: https://brainly.com/question/13859569
1)When the liquid is spun rapidly, the denser particles are forced to the bottom and the lighter particles stay at the top. This principle is used in:
Answers
Answer:
Centrifugation.
Explanation:
When the liquid is spun rapidly, the denser particles are forced to the bottom and the lighter particles stay at the top. This principle is used in centrifugation.
Centrifugation can be defined as the process of separating particles from a liquid solution according to density, shape, size, viscosity through the use of a centrifugal force. In order to separate these particles, the particles are poured into a liquid and placed in a centrifuge tube. A centrifuge is an electronic device used for the separation of particles in liquid through the application of centrifugal force. Once the centrifuge tube is mounted on the rotor of the centrifuge, it is spun rapidly at a specific speed thereby separating the solution; denser particles are forced to the bottom (by moving outward in the radial direction) and the lighter particles stay at the top as a result of their low density.
true/false. graphics or microsoft powerpoint includes facilities for making a wide variety of charts and graphs and for adding titles, legends, and explanatory text anywhere in the chart or graph.
Answers
Graphics or Microsoft PowerPoint do include facilities for making a wide variety of charts and graphs, and for adding titles, legends, and explanatory text anywhere in the chart or graph. These tools are commonly used for creating visual aids for presentations and reports. The statement is True.
Graphics and Microsoft PowerPoint are software applications that provide users with tools to create and edit visual content, including charts and graphs. These tools allow users to select from a variety of chart types, such as bar charts, line charts, pie charts, and more, and customize them by adding titles, labels, legends, and explanatory text.
For example, to create a chart in Microsoft PowerPoint, a user can select the Insert tab and then click on Chart. This opens a dialog box that allows the user to select the type of chart they want to create, such as a column chart or a line chart. Once the user has selected the chart type, they can then enter their data into a spreadsheet-like interface, and customize the chart by adding titles, axis labels, legends, and other elements.
Similarly, in graphics software like Adobe Illustrator or Canva, users can create custom charts and graphs by selecting from pre-built templates or creating their own from scratch. They can then customize the chart by changing colors, fonts, and other design elements, and adding explanatory text or annotations.
To get a similar answer on Microsoft PowerPoint:
https://brainly.com/question/7471158
#SPJ11
each browser has its own ______ style sheet that specifies the appearance of different html elements.
Answers
Each browser has its own default style sheet that specifies the appearance of different HTML elements.
The default style sheet, also known as the user agent style sheet, is a built-in set of CSS rules that define how different HTML elements should be displayed by default. When a web page is loaded, the browser applies its default style sheet to the document, and then any additional style sheets included in the page are applied on top of it.
The user agent style sheet is created by the browser developer and is specific to that browser. As a result, different browsers may have slightly different default styles for the same HTML elements. This can cause inconsistencies in the appearance of web pages across different browsers and platforms.
To ensure consistency and control over the appearance of web pages, web developers often use their own custom style sheets, known as author style sheets, to override or supplement the default styles provided by the browser.
To learn more about HTML elements, visit:
https://brainly.com/question/11569274
#SPJ11
How can I log in to my Macy's Credit Card account online?
Answers
Using a mobile app: Install the app on iOS or Android. After logging in, select "My Account." To view your balance, choose the Macy's Credit Card option from there.
How do I access my Macy's credit card online?If you haven't already, go to Macy's login page and click "Create Account." To establish a macys.com account, next provide your name, email address, birthday, and password.
Click "Create Account" after that.
Open your Macy's account and log in.
Create your security questions, then click "Save."
In order to complete attaching your Macy's Credit Card to your Macy's account, select your choices, click "Next," and then confirm your selections
Log into your Macy's accounts, click "My Account" from the fall menu in the top right corner, and then choose "Macy's Credit Card" once your Macy's Credit Card has been added.
To know more about Credit Card, visit:
https://brainly.com/question/26857829
#SPJ4
coment on this if your user starts with dida
Answers
Answer:
oh sorry i needed points but i have a friend whos user starts with dida
Explanation:
With respect to iot security, what term is used to describe the digital and physical vulnerabilities of the iot hardware and software environment?
a. Traffic Congestion
b. Device Manipulation
c. Attack Surface
d. Environmental Monitoring
Answers
Answer: Answer Surface
Explanation:
As you are analyzing a website, what is one indicator of relevance?
how often individuals promote a site
how often women select a site
how often men select a site
how often individuals select a site
Answers
(iii) If 1 GB = 2x
then what is the
value of x?
Answers
UNLESS, it wants the Windows way of storage, because one Gigabyte in Windows terms is actually 1024 megabytes... then it’d be 2(512MB) because 512MB and 512MB equals one windows storage gigabyte.
7.6 lesson practice edhesive
Answers
an appropriate datatype for one wanting a fixed-length type for last name would include: a) Varchar
b) Chat
c) Blob
d) Date
Answers
The appropriate datatype for a fixed-length type for last name would be "Char".
In database design, the datatype of a column determines the type of data that can be stored in that column.
The "Char" datatype is used to store fixed-length character strings. It requires the specification of the maximum number of characters that can be stored in the column, and any shorter values are padded with spaces to the specified length.
This makes it an appropriate choice for storing last names, as they typically have a fixed length. In contrast, the "Varchar" datatype is used for variable-length character strings, which is not ideal for storing fixed-length data.
The "Blob" datatype is used for storing binary data, while the "Date" datatype is used for storing date and time values. Therefore, the most appropriate datatype for a fixed-length type for last name would be "Char".
To know more about datatype: https://brainly.com/question/179886
#SPJ11
contoh ralat sintaks
Answers
What is the mistake in this python code
emotion = input("How are you feeling today?")
print(f"Im feeling {emotion} too!")
if == sad:
print("I hope you have a good day")
if == happy:
print("Me too")
Answers
You will need to set the if statements to:
if emotion == "sad":
print("I hope you have a good day")
if emotion == "happy":
print("Me too")
Make sure to indent the print code, and the first part of your code is correct!
The mistake in this Python code is that the if statements are missing the variable name that they should be checking. The correct syntax for an if statement is `if condition:` where `condition` is some expression that evaluates to either True or False.
Also, the values `sad` and `happy` are not defined as strings in the code, so the comparison with these values will result in a NameError.
Here's the corrected code:
emotion = input("How are you feeling today?")
print(f"I'm feeling {emotion} too!")
if emotion == "sad":
print("I hope you have a good day.")
if emotion == "happy":
print("Me too.")
Note that I've added the variable name `emotion` to the if statements, and defined the comparison values as strings. Also, I've added indentation to the print statements so they are executed only when the condition is true.
brielle is researching substitution ciphers. she came across a cipher in which the entire alphabet was rotated 13 steps. what type of cipher is this?
Answers
Caesar cipher is a very common type of substitution cipher where each letter in the plaintext is moved or shifted to a known number of places down the alphabet.
The type of cipher is this is ROT13
ROT13ROT13 is a simple letter substitution cipher. It functions by the replacement of a letter with the 13th letter after it in the alphabet. It is commonly known as Caesar cipher used in ancient RomeConclusively we can say that ROT13 is a commonly known Caesar cipher that replaces a letter with the 13th letter after it in the alphabet.
Learn more from
https://brainly.com/question/15300028
How can you tell if a website is credible?
a. Anything on the web is automatically credible
b. You must review aspects of the site such as the author’s credibility
c. If it has a top-level domain of .com, it is credible
d. All of the above
Answers
Answer:
b
Explanation:
you must review everything, creditability , certificates, domains, etc
i want pizzzzzzzaaaaaaaaaaa
Answers
How do cell phones negatively affect students in the classroom?
Answers
Cell phones negatively affect students with a divert attention and have a detrimental effect on cognitive ability, reaction times, performance, and enjoyment of focused tasks.
What is cognitive ability?Any task, no matter how simple or difficult, requires cognitive abilities, which are brain-based skills. They are less concerned with actual knowledge and more with the processes by which we learn, remember, solve problems, and pay attention.
For instance, picking up the phone requires motor skills (lifting the receiver), language skills (talking and understanding language), perception (hearing the ring tone), decision-making (answering or not), and social skills.
Particular neuronal networks provide support for cognitive abilities or skills. For instance, the temporal lobes and some parts of the frontal lobes are primarily responsible for memory functions. Due to damaged neuronal regions and networks, people with traumatic brain injuries may have lower cognitive function.
Learn more about cognitive abilities
https://brainly.com/question/9741540
#SPJ4
the ________ is used to give notification that the drawing will be changed in the future.
Answers
The revision cloud is used to provide a notification indicating that changes will be made to a drawing in the future.
In the field of technical drawing and drafting, a revision cloud is a graphical symbol or annotation used to highlight areas of a drawing that will be modified or revised at a later stage. It is typically represented as a freehand sketch in the shape of a cloud, enclosing the specific area or section that requires revision.
The revision cloud serves as a visual indicator to inform viewers that changes are planned for that particular part of the drawing. It helps to draw attention to the portions that need revision, ensuring that stakeholders and other individuals involved in the project are aware of the intended modifications.
By using revision clouds, it becomes easier to communicate and track changes throughout the drafting process, facilitating effective collaboration and ensuring that everyone is on the same page regarding the upcoming alterations.
learn more about revision cloud here:
https://brainly.com/question/11066834
#SPJ11
define computer ethics
Answers
Answer:
Computer ethics deals with the procedures, values and practices that govern the process of consuming computing technology and its related disciplines without damaging or violating the moral values and beliefs of any individual, organization or entity.
Computer ethics is a concept in ethics that addresses the ethical issues and constraints that arise from the use of computers, and how they can be mitigated or prevented.
Computer ethics primarily enforces the ethical implementation and use of computing resources. It includes methods and procedures to avoid infringing copyrights, trademarks and the unauthorized distribution of digital content. Computer ethics also entails the behavior and approach of a human operator, workplace ethics and compliance with the ethical standards that surround computer use.
The core issues surrounding computer ethics are based on the scenarios arising from the use of the Internet, such as Internet privacy, the publication of copyrighted content and user interaction with websites, software and related services.
You want to develop a system that will allow employers to develop better punctuality habits for employees. The employer doesn’t want employees to come either too early or too late. Employees clock in their times. Your employer has told you that coming in 10 minutes late or early is within tolerable limits.
Develop a sliding scale that uses linguistic variables. This scale helps employers determine seven levels, starting from extremely early to extremely late and just-on-time right in the middle.
Answers
Answer:
To develop a system that will allow employers to develop better punctuality habits for employees, a sliding scale can be used that uses linguistic variables. This scale would help employers to determine seven levels for punctuality, starting from extremely early to extremely late and just-on-time right in the middle. The employer has stated that coming in 10 minutes early or late is within tolerable limits, so the scale could be set up with the following levels:
• Extremely Early: 0-5 minutes • Early: 6-10 minutes • On Time: 11-15 minutes • Late: 16-20 minutes • Very Late: 21-25 minutes • Extremely Late: 26-30 minutes • Unacceptable: 31+ minutes.
This scale will help employers to determine acceptable levels of punctuality for employees, and ensure that they are not coming in too early or too late.
Explanation:
see above
Which of the following is an example of machine learning?

Answers
Answer: auto correct
Explanation: The iPhone can determine what you are going to type because of your past history.
An example of machine learning is autocorrect. The correct option is c.
What is machine learning?Machine learning is a branch of artificial intelligence that is widely described as a machine's ability to mimic intelligent human behavior.
Autocorrect is a word processing technology that detects misspelled words and utilizes algorithms to identify the words most likely to have been intended before editing the text.
In the context of machine learning, autocorrect relies solely on Natural Language Processing (NLP). It is programmed to fix spellings and errors when inputting text, as the name implies. Auto-Correction spellchecks your keyboard dictionary as you type, automatically fixing misspelled words. Simply enter text into a text area to use it.
Therefore, the correct option is C, autocorrect.
To learn more about machine learning, refer to the link:
https://brainly.com/question/16042499
#SPJ2
Hello can someone help me with this, please
1) What kinds of siding does the house from “Up” have?
2) What type of roof does our house have?
3) How many gables/hips does the roof have? :
4) Look at the following styles of houses. What style home do you think the house from up is?
5) How do you know?




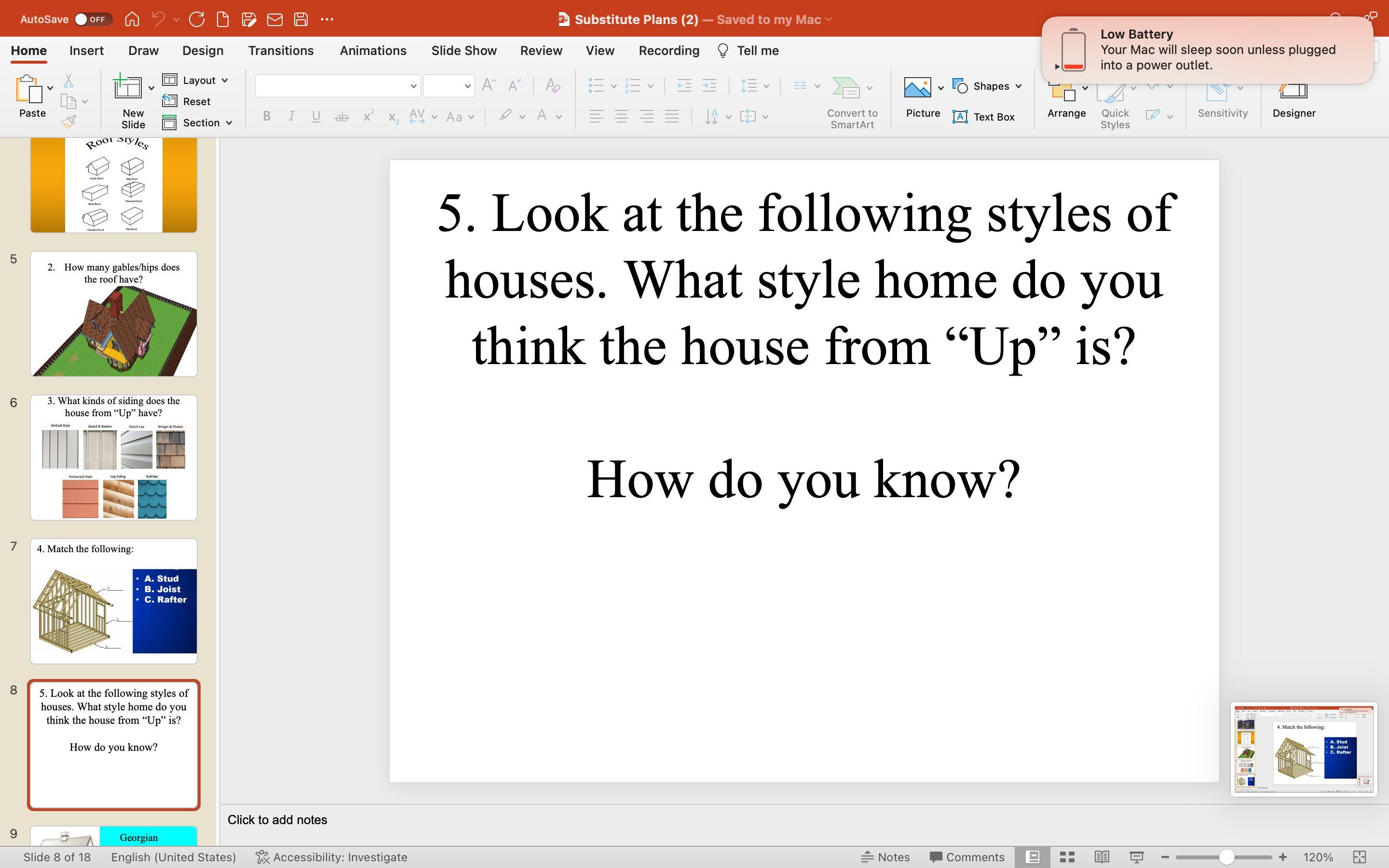
Answers
The house from "Up" has clapboard siding, which is a type of wooden siding that consists of long, narrow boards that overlap each other horizontally.
How to explain information regarding the houseThe house from "Up" appears to be a Victorian-style house with elements of Queen Anne style.
There are several characteristics of the house from "Up" that suggest it is a Victorian-style home. First, the house has a steeply pitched roof with multiple gables and dormer windows, which is a common feature of Victorian architecture.
The house also has a wrap-around porch with decorative railing, another hallmark of Victorian design. Additionally, the use of ornate detailing and vibrant colors, such as the elaborate trim work and bold purple paint, is typical of the Queen Anne style of Victorian architecture.
Learn more about house on:
brainly.com/question/23241042
#SPJ1
Enlist the main Component of each generation of computer
Answers
Answer:
First Generation - 1940 – 1956 - Vacuum Tubes.
Second Generation- 1956 – 1963- Transistors.
Third Generation - 1964 – 1971 - Integrated Circuits.
Fourth Generation- - 1972 – 2010 - Microprocessors.
Fifth Generation - 2010- present - Artificial Intelligence.
A computer is known to be an electronic machine. The main components of the computer generations are:
First Generation: This is known to have existed from 1940 – 1956. It component is that of Vacuum Tubes.Second Generation: this is known to have existed from 1956 – 1963- It man features is that of Transistors.Third Generation: Is known to be created and existed from 1964 – 1971. Its component is made up of Integrated Circuits.Fourth Generation was known to have existed between 1972 – 2010. It components is that of Microprocessors.Fifth Generation is known to be created in 2010 and it is still exiting. It component is that of Artificial Intelligence.There is the Generations of Computer that have been created by man. Due to new technologies, a lot of generation (5) have existed till date.
Learn more about Computers from
https://brainly.com/question/24540334
Deleting messages keeps them in the mailbox and on the server. How can they be removed from the server to reduce the quota?
Answers
Answer:
Left-click each message, and move it to the Trash folder.
Right-click the Deleted Items folder, and click Empty Folder.
Click the Folder tab, and click the Empty Folder in Clean Up group.
Right-click the Deleted Items folder, and click Mark All as Read.
is the application of information technology to the field of biology. group of answer choices bioinformatics bioengineering biocoenosis biofeedback
Answers
The correct answer is A) Bioinformatics.
What is Bioinformatics?Bioinformatics is the application of information technology to the field of biology. It involves the use of computational tools and techniques to analyze and interpret biological data, such as DNA sequences, protein structures, and gene expression patterns.
Bioinformatics is a rapidly growing field that has been driven by the rapid advancement of technology and the growing availability of biological data. It plays a critical role in many areas of biology, including genomics, proteomics, and systems biology.
Bioinformatics tools and techniques are used to study the structure and function of biological systems, to identify patterns and relationships in biological data, and to develop new algorithms and methods for analyzing and interpreting biological data.
Bioinformatics has many applications in biology and medicine, including drug discovery, disease diagnosis, and personalized medicine. It also has applications in agriculture, environmental science, and other fields.
The other options in the list are not related to the application of information technology to biology. Bioengineering is the application of engineering principles to the design and development of biological systems and technologies. Biocoenosis is a term used in ecology to refer to the interaction of organisms within a particular environment. Biofeedback is a technique used to train people to control their physiological responses to stress or other stimuli.
To Know More About Biocoenosis, Check Out
https://brainly.com/question/29563220
#SPJ4
PLEASE ANSWER FAST IM TIMED
A WYSIWYG editor will save time and make the process of Web site design an artistic practice rather than a ------- practice.
Answers
This open source software helps you either create a website through code, or design it with the help of templates and facile customizations.
What is the difference between HTML and WYSIWYG?A WYSIWYG editor shows you a rendered web page as you edit the page. You do not see the actual HTML. When using manual coding, you see the HTML, but you must load the document in a web browser to view the rendered page.
Is WYSIWYG easy to use?An efficient free WYSIWYG Editor comes with an easy-to-use toolbar, keyboard shortcuts, and other features that allow you to easily add or edit content, images, videos, tables, or links. A WYSIWYG editor saves time and makes web content creation quick and easy.
To know more about WYSIWYG visit:
https://brainly.com/question/12340404
#SPJ1
Answer:
Programming
Explanation:
WYSIWYG (sometimes pronounced "wizzy wig") is an acronym that stands for "What You See Is What You Get." It is a phrase that was coined when most word processing, desktop publishing, and typesetting programs were text and code based. HTML, at its code level, is much like the early interfaces on this sort of software. A WYSIWYG editor saves time and makes the process of website design an artistic practice rather than a programming practice.