due to the compact nature of laptop devices, all laptop gpus come in the form of cpu-integrated graphics. group of answer choices true false
Answers
False because all laptop graphics processors (GPUs) are built into the CPU because of how small laptop computers are.
What is the name of the part of a laptop that serves as a pointing device?A touch pad is a tool for pointing on a computer display screen (managing input location). It serves as a substitute for the mouse. Touch pads, which were first used with laptop computers, are now being developed for use with desktop PCs as well.
Which of the following best sums up the display technology found in most contemporary laptops?Today's laptops use LCD technology for their displays in the great majority of cases. Liquid crystal displays are called LCDs.
To know more about cpu-integrated graphics visit :-
https://brainly.com/question/26950627
#SPJ4
Related Questions
How to mark someone the Brainliest
Answers
Answer:
Explanation: Once u get more than 1 answer of a question. A message is shown above each answer that is "Mark as brainiest". Click on the option to mark it the best answer.
Answer:
above
Explanation:
Question 1 of 19
What element is not a selection in the Interface preferences?
O UI Character Presets
OUI Font Size
OUI Language
OUI Scaling
Answers
Answer:
UI Character Presets
Explanation:
User Interface is an option or go-to menu in a desktop application. For example, Photoshop. It allows a user to tweak the outlook to his or her own preference rather than the default settings.
To do this, a user is often tasked to do the following:
1. Click on the "Edit" menu
2. Navigate and click on "Preferences"
3. Select the "Interface" link
The options available to change includes:
a. UI Scaling
b. UI Font Size
c. UI Language.
Hence, in this case, the element that is not a selection in the Interface preferences is "UI Character preset"
1] write the o/p of union ,minus , intersect operation on following schema.
Student_set ( Sid ,Sname , Inst_code )
Teacher_set ( Tid , Tname , Inst_code )
\( \\ \\ \)
Thanks:)
Answers
Answer:
Union : select Sid, Sname, Inst_code from Student_set
Union
select Tid, Tname, Inst_code from Teacher_set;
Minus : select Sid, Sname, Inst_code from Student_set
Minus
select Tid, Tname, Inst_code from Teacher_set;
Intersect : select Sid, Sname, Inst_code from Student_set
Intersect
select Tid, Tname, Inst_code from Teacher_set;
Huda wants to start a business. she is doing a lot of paperwork to make her business an llc. why is she most likely determined to structure her business as an llc?
a.
she wants people to be able to buy and sell stock in her business.
b.
she wants to have unlimited liability in her investment.
c.
she wants to be free from any personal liability in her business.
d.
she wants to declare herself the sole owner of this business.
Answers
She most likely determined to structure her business as an llc is she wants to be free from any personal liability in her business.
Huda is most likely determined to structure her business as an LLC because she wants to be free from personal liability in her business. An LLC, or Limited Liability Company, is a type of business structure that provides limited liability protection to the owners, also known as members. This means that the members of an LLC are not personally responsible for the company's debts or liabilities, and their personal assets are generally protected. This can provide a level of security and peace of mind for the business owners, and is likely the reason Huda is choosing this type of business structure.
LLC, or limited liability company, is a business structure that combines the pass-through taxation of a partnership or sole proprietorship with the limited liability protection of a corporation. By choosing to structure her business as an LLC, Huda is seeking to protect herself from personal liability in the business. This means that if the business faces any legal or financial issues, her personal assets will not be at risk. This can give Huda peace of mind and allow her to focus on growing her business, rather than worrying about the potential for personal financial loss.
Learn more about Limited Liability Company(LLC) here:
https://brainly.com/question/18567855
#SPJ4
Can message confidentiality and message integrity protection be applied to the same message? Why or why not?
Answers
Answer:
Yes
Explanation:
Yes, message confidentiality and message integrity protection can be applied to the same message.
Message confidentiality is the protection of information from unauthorized access or disclosure by ensuring that only authorized parties can access and understand the information. This is typically achieved through the use of encryption algorithms that transform the plaintext message into an unintelligible form that can only be deciphered by someone with the appropriate decryption key.
Message integrity protection, on the other hand, is the assurance that the message has not been altered or tampered with during transmission. This is achieved through the use of cryptographic mechanisms, such as message authentication codes (MACs) or digital signatures, that allows the recipient to verify that the message has not been modified or corrupted in transit.
It is possible to apply both message confidentiality and message integrity protection to the same message. In fact, this is a common practice in many communication systems that require both confidentiality and integrity protection. For example, in secure messaging applications, the message is typically encrypted to ensure confidentiality, and a digital signature is added to ensure integrity protection. This provides a secure and trustworthy communication channel for the exchange of sensitive information.
Yes, message confidentiality and message integrity protection can be applied to the same message. Confidentiality protects the secrecy of the message, while integrity ensures that the message has not been tampered with.
Yes, the same communication may be subject to both message confidentiality and message integrity protection. Message integrity protection ensures that the message has not been tampered with during transmission, while message confidentiality ensures that the communication's content is not divulged to uninvited parties. Using encryption and decryption techniques, which can guarantee that only authorized parties can read the message's content and that the message hasn't been altered during transmission, one can achieve both of these security qualities. Message secrecy and message integrity can also be protected using digital signatures and message authentication codes (MACs). As a result, it is possible to protect the confidentiality and integrity of communication by applying both security mechanisms to it.
learn more about message integrity protection here:
https://brainly.com/question/29780054
#SPJ11
Use parallel and highway in a sentence
Answers
Answer:
The road ran parallel to the highway, with the Uncompahgre River separating the unpaved road from the main thoroughfare to the east.
Answer:
QUESTION:
Use parallel and highway in a sentence
ANSWER:
We were on the highway parallel to the train tracks.
Explanation:
Hope that this helps you out! :)
If any questions, please leave them below and I will try my best and help you.
Have a great rest of your day/night!
Please thank me on my profile if this answer has helped you!
melissa is installing a device that the system does not automatically recognize. she discovers that the configuration disk for the adapter has been misplaced or thrown away. what should she do?
Answers
Melissa to install the device must do: Check the manufacturer's website for the device or adapter in question.
Most manufacturers have a support page on their website that offers drivers, software, and firmware updates for their products. You can typically find drivers by searching for the model number of the device or adapter, or by browsing through the company's product support page.Look for third-party driver downloads. There are several websites on the internet that offer a vast database of drivers for various devices. These websites are typically free and don't require a login to access the files.
However, it's important to download drivers from trusted websites only as downloading drivers from the wrong sources may lead to malware being downloaded onto your computer.Download the driver on another computer. If the computer you're trying to install the device on doesn't have an internet connection, you can download the driver onto another computer with an internet connection and transfer it to the computer that needs it. This can be done by saving the driver to a USB flash drive or burning it onto a CD or DVD.
Learn more about firmware updates: https://brainly.com/question/3522075
#SPJ11
Given the following code, find the compile error.
public class Test{
public static void main(String[] args){
m(new GraduateStudent());
m(new Student());
m(new Person());
m(new Object());
}
public static void m(Person x){
System.out.println(x.toString());
}
}
class GraduateStudent extends Student {
public String toString(){ return "GraduateStudent";}
}
class Student extends Person{
public String toString(){ return "Student";}
}
class Person extends Object{
public String toString(){ return "Person";}
}
a. m(new Object()) causes an error
b. m(new Person()) causes an error
c. m(new Student()) causes an error
d. m(new GraduateStudent()) causes an error
Answers
Answer:
a. Object cannot be converted to Person
Explanation:
This program demonstrates polymorphism.
e.g., a Student IS a Person therefore you can call m() with a Student as well as a Person object.
The same goes for GraduateStudent.
However, and Object is not a Person, so the last call fails. This can be deducted by the type checking that happens at compile time.
what is 2D thinking and 3D thinking? i literally don't understand
Answers
Answer:
Two dimensional thinking implies concepts that are flat or only partially representative of the whole. Three dimensional thinking implies the first part of 2d thinking conjoined with intersecting dimensions rendering a deeper field of meaning.
Explanation:
Type the correct answer in the box. Spell all words correctly.
Natasha came across a website that had a building image, where each window in the building was clickable. She clicked on one of the windows,
Upon clicking the link information was sent to another computer. This computer processed the information and returned the appropriate page
about a window. Which attribute is used in this case to identify the type of image map?
The
attribute is used in this case to identify the type of image map.
Answers
Answer:
Redirection
Explanation:
This is something called redirection, you can sometimes get paid for it, or just some sort of reward, sometimes even a virus scanner.
Answer:
The ismap attribute is used in this case to identify the type of image map.
Explanation:
Using ismap indicates to your browser that the link is processed by another computer (server). Once the server processes the information about the link, it returns the appropriate page.
an obstacle or barrier that may prevent you from accomplishing your goal is called
Answers
Answer:
a roadblock
Explanation:
PLEASE HELP ME HELP ME NO IM NOT OKAY AND ITS NOT EASY FOR ME.....Vladimir is reworking an old slideshow. He needs to delete some of the text, combine or summarize other parts, and create a few new slides as well. He wants to only look at the text. Is there any easy way to do that?
A.
Yes, he can use the Outline view to see all the text in one place.
B.
Yes, he can use the Slide Master to view all the text in one place.
C.
No, he'll have to use the Slide pane to navigate the slides one by one.
D.
No, he'll have to copy all the text out into a word processor.
Answers
Answer:
Outline view
Explanation:
This is a formatted window that shows all text, headers, and titles in a popup on the left side of the screen. Slide master shows all the slides but includes slide details such as inserted images and smart art.
What might happen to the wire if the uneven load is never balanced
Answers
If an uneven load on a wire is never balanced, it can lead to a variety of potential problems and risks. One of the most common consequences of uneven loading is the buildup of stress and tension in the wire, which can cause it to become overstretched and potentially snap or break.
When a wire is subjected to uneven loading, such as when a heavier weight is placed on one side of the wire than the other, the tension in the wire becomes unbalanced. This can cause the wire to become stretched beyond its normal limits, which can lead to deformation, fatigue, and ultimately failure. If the wire is not balanced, it may also be more susceptible to external factors such as wind, vibration, and temperature changes, which can exacerbate the stress and strain on the wire.
In addition to the risk of wire failure, uneven loading can also lead to other safety hazards. For example, if the wire is used to support a structure or equipment, an imbalance in the load can cause the structure to become unstable or the equipment to malfunction. This can result in property damage, injuries, and even loss of life.
To prevent these types of issues, it is important to ensure that loads are evenly distributed on wires and other support structures. This can be achieved through the use of proper rigging techniques, such as the use of equalizer bars or spreader bars, and by carefully monitoring loads to ensure that they are balanced at all times. By taking these precautions, the risk of wire failure and other safety hazards can be minimized.
To learn more about Wire loading, visit:
https://brainly.com/question/25922783
#SPJ11
how to use software for simulation experiments and probability calculations, and how to interpret the results and observe patterns in the data.
Answers
using simulation and probability software can help to streamline the process of running experiments and calculations, and can make it easier to interpret the results. By following these tips, you can ensure that you are getting the most out of your software and making informed decisions based on the data.
Simulations and probability calculations can be performed using software that is designed for this purpose. The following are some tips on how to use such software and interpret the results:
1. Content loading: To use simulation and probability software, you will need to load the appropriate content into the program. This content may include data on variables, constraints, and other factors that will be used in the simulation or calculation. The content can be loaded into the software either manually or automatically.
2. Software usage: Once the content is loaded, the software can be used to perform the simulation or probability calculation. This may involve setting certain parameters, defining variables, and specifying other details of the experiment or calculation.
3. Interpretation of results: Once the simulation or calculation is complete, the results must be interpreted in order to make sense of the data. This may involve analyzing the data to identify patterns, trends, or other relevant factors. The results can then be used to draw conclusions about the experiment or calculation, and to inform future decision-making.
4. Observing patterns in data: Patterns in the data can be observed by looking at the graphs, charts, and other visualizations that are generated by the software. These visualizations can help to highlight trends, correlations, and other important factors that may not be immediately apparent from the raw data.
To know more about software Visit:
https://brainly.com/question/32393976
#SPJ11
which output will be displayed by the following program?
print(Grade List)
print(100)
print(93)
print(82)
print(Total)
print(100+93+82)
Answers
Answer:SyntaxError: unexpected data type
Explanation:I just took the test and i tried the code in python
:) good luck on the test!!
The output for the given program will be SyntaxError: invalid syntax.
What is invalid syntax?Invalid syntax simply implies that the code one wrote cannot be interpreted as valid Python instructions. "Syntax" called to the rules and structures of a language, both spoken a s well as written.
Python creates syntax errors when it transforms source code to byte code. They usually implies that something is wrong with the program's syntax.
For illustration: The message is redundant when the colon at the end of a def statement is removed. SyntaxError: insufficient syntax.
Here are some examples of Python syntax errors: x, y = myfunction Otherwise, return x + y: print("Hello!") if mark is greater than 50 print("You succeeded!") If you arrive, print("Hi!") print("Bye!") else If flag is set, print("Flag is set!")
Thus, as per the given program, it is not showing proper format of the language so it will be showing SyntaxError.
For more details regarding programming, visit:
https://brainly.com/question/11023419
#SPJ5
PHOTOGRAPHY: In 200 words or more explain the difference between deep and shallow depth field and when would you use either technique when taking a photograph?
Answers
The differences are:
A shallow depth of field is said to be a small area in view and its background is always blurred but a A deep depth of field is known to be one that captures a bigger area in view and its image are said to be sharp and clear.What is the difference between deep and shallow focus?The Images gotten in shallow focus is one that needs little or shallow depths of field, and its lenses also needs long focal lengths, and big apertures. But Deep focus images needs small focal lengths and long depths of field.
In the case above i recommend deep depth field and therefore, The differences are:
A shallow depth of field is said to be a small area in view and its background is always blurred but a A deep depth of field is known to be one that captures a bigger area in view and its image are said to be sharp and clear.Learn more about photograph from
https://brainly.com/question/13600227
#SPJ1
assume that a network has a subnet mask of 255.255.128.0. what is the maximum number of actual hosts that the subnet can handle
Answers
Answer:
32766 Explanation: Formula for the number for a maximum number
Explanation:
What are uses of Spreadsheet
Answers
Answer: The three most common general uses for spreadsheet software are to create budgets, produce graphs and charts, and for storing and sorting data. Within business spreadsheet software is used to forecast future performance, calculate tax, completing basic payroll, producing charts and calculating revenues.
Explanation:
Answer: You can use it to storing and sorting data and to produce graphs , it also has other uses.
Robert is given a string that ends with a character or a number. he
has to check the length of the given string and append it to the end
in such a way that if the original string ends with a number then the
new string with the appended value must have the length of the
string as the last two characters. if the string ends with a character
then append the total length as the last character.
also, the number to be appended must be a single positive digit.
write a code to implement the given scenario.
input format
input consist of a string
output format
Answers
Robert should first identify the input and output formats, analyze the given string, perform the necessary operations based on the last Character, and then output the result using the determined format.
It seems like Robert is given a string that ends with either a character or a number, and he needs to process it using input and output formats.
Step 1: Identify the input format.
The input format could be a string provided by the user or a file containing the string. Robert should first understand how he will receive the string to process it accordingly.
Step 2: Analyze the string.
Robert needs to identify the last character of the string to determine whether it's a number or a character.
Step 3: Process the string based on the last character.
If the string ends with a number, Robert may perform a specific operation, such as doubling the number. If it ends with a character, he may perform a different operation, like converting the character to uppercase.
Step 4: Determine the output format.
Robert should know how the processed string should be displayed, whether it's printed on the screen, saved in a file, or returned as a variable in a program.
Step 5: Output the processed string.
Based on the output format, Robert will present the processed string accordingly. For example, if the output format is to print on the screen, he will use the appropriate command or function to display the result.
In summary, Robert should first identify the input and output formats, analyze the given string, perform the necessary operations based on the last character, and then output the result using the determined format.
To Learn More About Character
https://brainly.com/question/29319760
#SPJ11
Rohan is creating a presentation with at least 50 slides. He wants the slides to use a consistent layout and formatting. Which of the following parts of the presentation should he design first?
Answers
The parts of the presentation that he should design first is Slide master
Slide master is a slide that enables you to do the following:
•Modify your presentation to suit your taste
•It enables you to make a partial or minor change on the slide layout of your presentation
•Slide master help you to create a perfect and special presentation.
•With Slide master you can easily modify your slide text color.
Inconclusion The parts of the presentation that he should design first is Slide master.
Learn more about Slide master here:
https://brainly.com/question/12600334
what API does the OS provide to user programs?
Answers
The API that the OS provides to user programs is called the "Operating System API" or "System API." This API serves as an interface between the user programs and the operating system, allowing the programs to access various resources and functionalities offered by the OS.
The Operating System API typically includes functions for file management, memory management, process management, and inter-process communication, among others. By using this API, user programs can interact with the OS more efficiently and effectively.
The OS provides various APIs (Application Programming Interfaces) to user programs, which are designed to enable developers to interact with the system's resources and perform various tasks. Some examples of APIs that an OS may provide to user programs include file system APIs, networking APIs, GUI (Graphical User Interface) APIs, device driver APIs, and system call APIs.
These APIs allow user programs to access and manipulate various system resources, such as files, network connections, user input/output, and hardware devices, among others. Overall, the APIs provided by the OS are essential for enabling user programs to function properly and interact with the underlying system effectively.
To know more about API: https://brainly.com/question/6635750
#SPJ11
What is constructive criticism?
Advice and possible solutions intended to help or improve something
Information given to others as a way to make them feel unintelligent
Reports about decreasing profits
Statements and no possible solutions aimed at showing problem areas
Answers
Answer:
Constructive cristsism is a helpful way of giving feedback that provides specific, actionable suggestions. Or, its a nice way of criticizing someone and telling them what to do better
Answer:
Advice and possible solutions intended to help or improve something
Explanation:
I took the test and Got it Correct!
Which of the following numeric values is considered a floating point?
A. 16
B. -16
C. 1.6
D. 160
Answers
Explanation:
B.-16
Because the things is that idk
What six things can you do with GIS?
Answers
Answer:
You can:
- Change detection
- Transport route planning
- Flood risk mapping
- Site selection
- Weed and pest management
- Koala habitat mapping
Hope this helps! :)
What will print to the console after running this code segment?
A. 15.
B. 16.
C. 18.
D. 21.
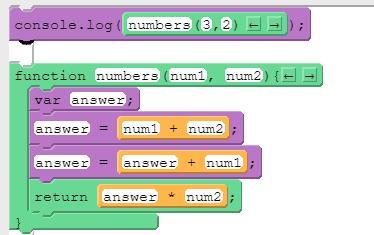
Answers
Answer:
16
Explanation:
answer =3+2
answer =5+3
return 8 × 2
16 will print to the console after running this code segment. Therefore, option B is correct.
What do you mean by code segment ?A code segment, also known as a text segment or simply text, is a section of an object file or the program's virtual address space that contains executable instructions.
A character array segment that represents a text fragment. Even though the array is directly accessible, it should be treated as immutable. This allows for quick access to text fragments without the overhead of copying around characters.
In memory, the code segment functions normally as read-only memory and has a fixed size; thus, without the need for loading, it can generally be found in read-only memory (ROM) on embedded systems.
answer = 3+2, answer = 5+3
return 8 × 2
= 16
Thus, option B is correct.
To learn more about the code segment, follow the link;
https://brainly.com/question/20063766
#SPJ2
How do you interpret and analyze photographs? What method comes most
naturally to you when interpreting and analyzing photographic works? Identify and
discuss the methods and strategies that you use to interpret and analyze
photographs.
Answers
Answer:
You interpret and analyze photographs by observing detail.
Explanation:
a linux security administrator wants to use a built in tool to implement an os security mechanism that enforces access rules based on privileges for interactions between processes, files, and users.
a. true
b. false
Answers
A Linux security administrator should use Mandatory Control Access.
Define Linux.
Linux is an open-source Unix-like operating system built on the Linux kernel, which Linus Torvalds initially made available on September 17, 1991. Linux distributions are the most common form in which Linux is packaged.
For desktops, servers, mainframes, mobile devices, and embedded devices, Linux is an open-source, community-developed operating system (OS) with Unix-like features. Being one of the most broadly supported operating systems, it is compatible with practically all popular computer architectures, such as x86, ARM, and SPARC.
To learn more about Linux, use the link given
https://brainly.com/question/25480553
#SPJ4
er reports that he is having problems with his monitor. He explains that his laptop's liquid crystal display (LCD) is no longer spreading the light over the entire screen. Which component of the LCD is most likely causing this problem?
Answers
Answer:
diffuser
Explanation:
Based on the scenario being described, the most likely cause of the problem is a bad diffuser. This is a component found in nearly every type of LCD backlit displays and are used to produce an even array of lighting across the entire display. If this component fails then it will cause bright spots and dim spots throughout the display, similar to what the client is reporting in this scenario since the light is not being evenly distributed.
Of the following versions of Windows, which support an IPv4/IPv6 dual-stack configuration? (Choose all that apply. )
a. Windows XP
b. Windows Server 2003
c. Windows Server 2008
d. Windows Vista SP1
Answers
Because of the decline in the number of IPv4 addresses and the need to accommodate the growing number of users and internet-connected devices, the shift to IPv6 has become increasingly necessary.
IPv6 has the ability to accommodate a significantly greater number of internet addresses than IPv4, which has only 4.3 billion IP addresses; this number of IP addresses will soon be depleted. The following versions of Windows support an IPv4/IPv6 dual-stack configuration, Windows Server 2008, and Windows Vista SP1 are the only versions that support an IPv4/IPv6 dual-stack configuration.
IPv6 support is not available in Windows XP or Windows Server 2003 (although Windows Server 2003 can provide IPv6 routing).Windows Vista and Windows Server 2008 can both communicate natively over IPv6 networks with other IPv6-enabled systems.
To know more about IPv4 visit:
https://brainly.com/question/32374322
#SPJ11
Anyone have Y.O.U.T.U.B.E or S.O.U.N.D.C.L.O.U.D. I need help putting my music and videos out there
Answers
Answer:
I do have Y.O.U.T.U.B.E.
Explanation:
1. Go on Y.O.U.T.U.B.E app.
2. Create account or log in to an existing account.
3. In the welcome screen, click the button of a camera on the top right corner next to your photo icon.
4. Click "Upload Video"
5. Then upload your video.
6. Add a description and details
7. Done! Just upload to on Y.O.U.T.U.B.E.
I hope this helps! Thank you:)