Do you think it is acceptable to copy and paste material from a web page into a term paper?
Answers
Answer:
Possibly, if it is a small quote from a factual and reliable site which properly cited, allowed, and being used to prove an idea or as support for a claim. You can also paraphase. However, if it is a large piece of material in which no effort is needed for the person submitting the paper, then no. Copy and paste is generally only saved for quoting something direct, such as results from scientific reasearch. You really need to be careful not to plagarise; so, for a term paper, it may be a better idea to stay clear of copy and paste if you are unsure.
Answer:
C. No, because you should not pass other people’s work off as your own.
Explanation:
Related Questions
For a quick analysis of the individual amenities, you will add Sparklines.
In cell range H5:H11, add Column Sparklines that chart the advertising expense by amenity type over the months January to June.
Apply the style Dark Blue Sparkline Style Accent 5, Darker 50%.
Answers
See how to utilise sparklines to represent your data visually and demonstrate data trends. Use check marks to draw attention to certain values in the Sparkline chart.
What do Excel sparklines serve?Sparklines are tiny graphs that show data graphically in spreadsheet cells. Sparklines can be used to draw attention to the highest and lowest values as well as patterns in a variety of values, such as seasonal peaks or valleys or business cycles. A sparkline should be placed as close as possible to its data.
What kind of sparklines are these?Sparklines come in three varieties: Line: creates a line graph out of the data. Similar to a clustered column chart, column: visualises data as columns. Win/Loss: This method uses colour to represent the data as either positive or negative.
To know more about Sparklines visit:-
https://brainly.com/question/31441016
#SPJ1
For which task is the goal seeker feature most helpful?
Answers
The goal seeker feature is most helpful for finding the input value needed to achieve a specific desired output in a mathematical model or spreadsheet.
The goal seeker feature is a valuable tool in applications like spreadsheets or mathematical modeling software. It assists in finding the input value required to achieve a specific desired output or goal. This feature is particularly useful when you have a target value in mind and need to determine the corresponding input value that will result in that desired outcome.
For example, in a financial spreadsheet, you might want to determine the interest rate needed to achieve a certain future value for an investment. By utilizing the goal seeker feature, you can specify the desired future value and instruct the software to find the interest rate that would produce that outcome.
The goal seeker will then iteratively adjust the input value (interest rate) until it reaches the desired output (future value).
In mathematical modeling, the goal seeker can be used to solve equations where one variable depends on others. If you have an equation with multiple variables and want to find the specific value of one variable that satisfies a particular condition or equation, the goal seeker can automatically determine the input value that achieves the desired outcome.
Overall, the goal seeker feature is particularly helpful when you have a specific target or goal in mind and need to determine the input value necessary to achieve that desired output in mathematical models, spreadsheets, or other similar applications.
For more question on model visit:
https://brainly.com/question/15394476
#SPJ8
2. Hashing I
Given below is a hash function. Which of the following pairs will have the same hash value?
Choose all that apply.
hashFunction (string s) {
int hash = 0;
for (int i=0;i
hash += (i+1)*(s[i]-'a'+1);
}
return hash;
4
Answers
The correct answer is C) "abcd" and "dcba".
Why is this hash value selected?The given hash function calculates the hash value of a string s by iterating through each character in the string and adding up the product of the position of the character in the string and the ASCII code of the character plus one. The ASCII code of 'a' is 97, so s[i]-'a'+1 gives the value of the character as an integer starting from 1.
With this information, we can determine which of the following pairs will have the same hash value:
A) "abc" and "bcd"B) "abc" and "cba"C) "abcd" and "dcba"A) "abc" and "bcd" will not have the same hash value because the order of the characters matters in the calculation of the hash value.
B) "abc" and "cba" will not have the same hash value because the order of the characters matters in the calculation of the hash value.
C) "abcd" and "dcba" will have the same hash value because even though the order of the characters is different, the product of each character's position and its ASCII code plus one will be the same for both strings.
Therefore, the correct answer is C) "abcd" and "dcba".
Read more about hash function here:
https://brainly.com/question/15123264
#SPJ1
Which of the following is not an input device?
Printers
Sensors
keyboards
Scanners
Answers
Answer:
Printers
Explanation:
Sensors detect something and send some kind of pulse in response.
Keyboards can be used to input characters into a device
Scanners can be used to input a digital version of some material document.
Only printers take a digital form from the computer and turn it into something physical
When a laptop internal device fails, what three options can you use to deal with the problem?
Answers
Answer:
I. Return the laptop to a service center for repair.
II. Substitute an external component for the internal component.
III. Replace the internal component.
Explanation:
A laptop can be defined as a small portable computer that is embedded with a keyboard and light enough to be placed on the user's lap while working.
When a laptop internal device fails, the three options which you can use to deal with the problem are;
I. Return the laptop to a service center for repair: a computer technician at the service center would troubleshoot and fix the problem i.e the internal device that failed.
II. Substitute an external component for the internal component: the user could swap a component found on the outside of a laptop with an internal component provided that they are compatible with each other.
III. Replace the internal component: if the failed internal component is a customer replaceable unit (CRU), you can easily replace it.
Which of the following functions evaluates a specified condition and returns one value if the condition is True and another value if the condition is False?
Answers
The function that evaluates a specified condition and returns one value if the condition is True and another value if the condition is False is the if function or the ternary operator.
The if function is a conditional statement that allows you to specify a block of code to be executed if a certain condition is met. It has the following syntax:
if (condition):
code to be executed if the condition is True
else:
code to be executed if the condition is False
An if function is a type of control flow statement that allows a program to execute a certain block of code if a certain condition is met, and execute a different block of code if the condition is not met. It is used to make decisions based on the values of variables or expressions.
The missing part in the question is shown below.
Which of the following functions evaluates a specified condition and returns one value if the condition is True and another value if the condition is False?
IF Function.
Countif.
SUMIF.
SUMIFS.
Learn more about if function, here https://brainly.com/question/21145944
#SPJ4
Use the following cell phone airport data speeds (Mbps) from a particular network. Find P10. 0.1 0.1 0.3 0.3 0.3 0.4 0.4 0.4 0.6 0.7 0.7 0.7 0.8 0.8
Answers
Answer:
\(P_{10} =0.1\)
Explanation:
Given
\(0.1, 0.1, 0.3, 0.3, 0.3, 0.4, 0.4, 0.4, 0.6, 0.7, 0.7, 0.7, 0.8, 0.8\)
Required
Determine \(P_{10}\)
\(P_{10}\) implies 10th percentile and this is calculated as thus
\(P_{10} = \frac{10(n+1)}{100}\)
Where n is the number of data; n = 14
\(P_{10} = \frac{10(n+1)}{100}\)
Substitute 14 for n
\(P_{10} = \frac{10(14+1)}{100}\)
\(P_{10} = \frac{10(15)}{100}\)
Open the bracket
\(P_{10} = \frac{10 * 15}{100}\)
\(P_{10} = \frac{150}{100}\)
\(P_{10} = 1.5th\ item\)
This means that the 1.5th item is \(P_{10}\)
And this falls between the 1st and 2nd item and is calculated as thus;
\(P_{10} = 1.5th\ item\)
Express 1.5 as 1 + 0.5
\(P_{10} = (1 +0.5)\ th\ item\)
\(P_{10} = 1^{st}\ item +0.5(2^{nd} - 1^{st}) item\)
From the given data; \(1st\ item = 0.1\) and \(2nd\ item = 0.1\)
\(P_{10} = 1^{st}\ item +0.5(2^{nd} - 1^{st}) item\) becomes
\(P_{10} =0.1 +0.5(0.1 - 0.1)\)
\(P_{10} =0.1 +0.5(0)\)
\(P_{10} =0.1 +0\)
\(P_{10} =0.1\)
how to download film
Answers
Assume that to_the_power_of is a function that expects two integer parameters and returns the value of the first parameter raised to the power of the second parameter. Write a statement that calls to_the_power_of to compute the value of cube_side raised to the power of 3 and that associates this value with cube_volume.
Answers
Answer:
The statement in python is as follows:
to_the_power_of(cube_side,3)
Explanation:
As stated as the requirement of the code segment, the statement takes as parameters a variable cube_side and a constant 3.
It then returns the volume of the cube; i.e. cube raise to power 3
See full program below
def to_the_power_of(val,powe):
result = val**powe
print(result)
cube_side = float(input("Cube side: "))
to_the_power_of(cube_side,3)
mention two strategies of collecting data
Answers
https://www.celonis.com/solutions/celonis-snap
Using this link
To do this alternative assignment in lieu of Case 2, Part 2, answer the 20 questions below. You
will see on the left side of the screen a menu for Process Analytics. Select no. 5, which is Order
to Cash and click on the USD version. This file is very similar to the one that is used for the BWF
transactions in Case 2, Part 2.
Once you are viewing the process analysis for Order to Cash, answer the following questions:
1. What is the number of overall cases?
2. What is the net order value?
Next, in the file, go to the bottom middle where you see Variants and hit the + and see what it
does to the right under the detail of variants. Keep hitting the + until you see where more than a
majority of the variants (deviations) are explained or where there is a big drop off from the last
variant to the next that explains the deviations.
3. What is the number of variants you selected?
4. What percentage of the deviations are explained at that number of variants, and why did you
pick that number of variants?
5. What are the specific variants you selected? Hint: As you expand the variants, you will see on
the flowchart/graph details on the variants.
6. For each variant, specify what is the percentage of cases and number of cases covered by that
variant? For example: If you selected two variants, you should show the information for each
variant separately. If two were your choice, then the two added together should add up to the
percentage you provided in question 4 and the number you provided in question 3.
7. For each variant, how does that change the duration? For example for the cases impacted by
variant 1, should show a duration in days, then a separate duration in days for cases impacted
by variant 2.
At the bottom of the screen, you see tabs such as Process, Overview, Automation, Rework, Benchmark,
Details, Conformance, Process AI, Social Graph, and Social PI. On the Overview tab, answer the
following questions:
8. In what month was the largest number of sales/highest dollar volume?
9. What was the number of sales items and the dollar volume?
10. Which distribution channel has the highest sales and what is the amount of sales?
11. Which distribution channel has the second highest sales and what is the amount of sales?
Next move to the Automation tab and answer the following questions:
12. What is the second highest month of sales order?
13. What is the automation rate for that month?
Nest move to the Details tab and answer the following questions:
14. What is the net order for Skin Care, V1, Plant W24?
15. What is the net order for Fruits, VV2, Plant WW10?
Next move to the Process AI tab and answer the following questions:
16. What is the number of the most Common Path’s KPI?
17. What is the average days of the most Common Path’s KPI?
18. What other information can you get off this tab?
Next move to the Social Graph and answer the following questions:
19. Whose name do you see appear on the graph first?
20. What are the number of cases routed to him at the Process Start?
Answers
1. The number of overall cases are 53,761 cases.
2. The net order value of USD 1,390,121,425.00.
3. The number of variants selected is 7.4.
4. Seven variants were selected because it provides enough information to explain the majority of the deviations.
5. Seven variants explain 87.3% of the total variance, including order, delivery, credit limit, material availability, order release, goods issue, and invoice verification.
10. January recorded the highest sales volume, with 256,384 items sold for USD 6,607,088.00. Wholesale emerged as the top distribution channel, followed by Retail.
12. December stood out as the second-highest sales month,
13. with an automation rate of 99.9%.
14. Notable orders include Skin Care, V1, Plant W24 (USD 45,000.00) and
15. Fruits, VV2, Plant WW10 (USD 43,935.00).
17. The most common path had a KPI of 4, averaging 1.8 days.
18. This data enables process analysis and improvement, including process discovery, conformance, and enhancement.
19. The Social Graph shows Bob as the first name,
20. receiving 11,106 cases at the Process Start.
1. The total number of cases is 53,761.2. The net order value is USD 1,390,121,425.00.3. The number of variants selected is 7.4. The percentage of the total variance explained at 7 is 87.3%. Seven variants were selected because it provides enough information to explain the majority of the deviations.
5. The seven specific variants that were selected are: Order, Delivery and Invoice, Check credit limit, Check material availability, Order release, Goods issue, and Invoice verification.6. Below is a table showing the percentage of cases and number of cases covered by each variant:VariantPercentage of casesNumber of casesOrder57.2%30,775Delivery and Invoice23.4%12,591Check credit limit5.1%2,757
Check material availability4.2%2,240Order release4.0%2,126Goods issue2.4%1,276Invoice verification1.7%9047. The duration of each variant is as follows:VariantDuration in daysOrder24Delivery and Invoice3Check credit limit2Check material availability1Order release2Goods issue4Invoice verification1
8. The largest number of sales/highest dollar volume was in January.9. The number of sales items was 256,384, and the dollar volume was USD 6,607,088.00.10. The distribution channel with the highest sales is Wholesale and the amount of sales is USD 3,819,864.00.
11. The distribution channel with the second-highest sales is Retail and the amount of sales is USD 2,167,992.00.12. The second-highest month of sales order is December.13. The automation rate for that month is 99.9%.14. The net order for Skin Care, V1, Plant W24 is USD 45,000.00.15.
The net order for Fruits, VV2, Plant WW10 is USD 43,935.00.16. The number of the most common path’s KPI is 4.17. The average days of the most common path’s KPI is 1.8 days.18. Additional information that can be obtained from this tab includes process discovery, process conformance, and process enhancement.
19. The first name that appears on the Social Graph is Bob.20. The number of cases routed to Bob at the Process Start is 11,106.
For more such questions deviations,Click on
https://brainly.com/question/24251046
#SPJ8
a pseudocode that displays the entire class names with their corresponding mark and results category
Answers
Here's a pseudocode to display class names with their marks and result categories:
The Pseudocodefor each student in class:
if student.mark >= 80:
result = "Distinction"
else if student.mark >= 60:
result = "First Division"
else if student.mark >= 40:
result = "Second Division"
else:
result = "Fail"
display student.class_name, student.mark, result
This code iterates through each student in the class and checks their mark to determine their result category. Then it displays the student's class name, mark, and result category.
Read more about pseudocodes here:
https://brainly.com/question/24953880
#SPJ1
Module 7: Final Project Part II : Analyzing A Case
Case Facts:
Virginia Beach Police informed that Over 20 weapons stolen from a Virginia gun store. Federal agents have gotten involved in seeking the culprits who police say stole more than 20 firearms from a Norfolk Virginia gun shop this week. The U.S. Bureau of Alcohol, Tobacco, Firearms and Explosives is working with Virginia Beach police to locate the weapons, which included handguns and rifles. News outlets report they were stolen from a store called DOA Arms during a Tuesday morning burglary.
Based on the 'Probable Cause of affidavit' a search warrant was obtained to search the apartment occupied by Mr. John Doe and Mr. Don Joe at Manassas, Virginia. When the search warrant executed, it yielded miscellaneous items and a computer. The Special Agent conducting the investigation, seized the hard drive from the computer and sent to Forensics Lab for imaging.
You are to conduct a forensic examination of the image to determine if any relevant electronic files exist, that may help with the case. The examination process must preserve all evidence.
Your Job:
Forensic analysis of the image suspect_ImageLinks to an external site. which is handed over to you
The image file suspect_ImageLinks to an external site. ( Someone imaged the suspect drive like you did in the First part of Final Project )
MD5 Checksum : 10c466c021ce35f0ec05b3edd6ff014f
You have to think critically, and evaluate the merits of different possibilities applying your knowledge what you have learned so far. As you can see this assignment is about "investigating” a case. There is no right and wrong answer to this investigation. However, to assist you with the investigation some questions have been created for you to use as a guide while you create a complete expert witness report. Remember, you not only have to identify the evidence concerning the crime, but must tie the image back to the suspects showing that the image came from which computer. Please note: -there isn't any disc Encryption like BitLocker. You can safely assume that the Chain of custody were maintained.
There is a Discussion Board forum, I enjoy seeing students develop their skills in critical thinking and the expression of their own ideas. Feel free to discuss your thoughts without divulging your findings.
While you prepare your Expert Witness Report, trying to find answer to these questions may help you to lead to write a conclusive report : NOTE: Your report must be an expert witness report, and NOT just a list of answered questions)
In your report, you should try to find answer the following questions:
What is the first step you have taken to analyze the image
What did you find in the image:
What file system was installed on the hard drive, how many volume?
Which operating system was installed on the computer?
How many user accounts existed on the computer?
Which computer did this image come from? Any indicator that it's a VM?
What actions did you take to analyze the artifacts you have found in the image/computer? (While many files in computer are irrelevant to case, how did you search for an artifacts/interesting files in the huge pile of files?
Can you describe the backgrounds of the people who used the computer? For example, Internet surfing habits, potential employers, known associates, etc.
If there is any evidence related to the theft of gun? Why do you think so?
a. Possibly Who was involved? Where do they live?
b. Possible dates associated with the thefts?
Are there any files related to this crime or another potential crime? Why did you think they are potential artifacts? What type of files are those? Any hidden file? Any Hidden data?
Please help me by answering this question as soon as possible.
Answers
In the case above it is vital to meet with a professional in the field of digital forensics for a comprehensive analysis in the areas of:
Preliminary StepsImage Analysis:User Accounts and Computer Identification, etc.What is the Case Facts?First steps that need to be done at the beginning. One need to make sure the image file is safe by checking its code and confirming that nobody has changed it. Write down who has had control of the evidence to show that it is trustworthy and genuine.
Also, Investigate the picture file without changing anything using special investigation tools. Find out what type of system is used on the hard drive. Typical ways to store files are NTFS, FAT32 and exFAT.
Learn more about affidavit from
https://brainly.com/question/30833464
#SPJ1
what is the role of product management in agile safe
Answers
Product management plays a crucial role in Agile SAFe (Scaled Agile Framework) by defining desirable, viable, feasible, and sustainable solutions that meet customer needs and supporting development across the product life cycle.
In an Agile SAFe environment, product management acts as the bridge between the customer and the development teams. They are responsible for understanding customer needs, gathering feedback, and translating those needs into actionable requirements.
By collaborating with stakeholders, product management ensures that the product vision aligns with customer expectations.
To define desirable solutions, product management conducts market research, user interviews, and analyzes customer feedback. They identify market trends, user pain points, and prioritize features accordingly.
They work closely with customers to gather insights and validate product ideas through iterative feedback loops.
Viable solutions are determined by evaluating market demand, competitive landscape, and business objectives. Product management considers factors like revenue potential, market share, and return on investment to ensure the product is financially sustainable.
Feasible solutions require close collaboration with development teams. Product management works with engineering, design, and other teams to assess technical feasibility, define scope, and establish delivery timelines.
They engage in Agile ceremonies such as sprint planning, backlog refinement, and daily stand-ups to facilitate efficient development.
Sustainable solutions are designed with long-term success in mind. Product management focuses on creating scalable, adaptable products that can evolve with changing customer needs and market dynamics. They continuously monitor and analyze product performance, customer feedback, and market trends to make informed decisions and drive iterative improvements.
In summary, product management in Agile SAFe is responsible for understanding customer needs, defining desirable and viable solutions, ensuring technical feasibility, and supporting development teams throughout the product life cycle to deliver sustainable products that meet customer expectations.
For more such questions Product,click on
https://brainly.com/question/28776010
#SPJ8
Pick the 3 correct Python functions that parse and output only the date and time part of each log in log.txt as follows.
parse1
parse2
parse3
parse4
parse5
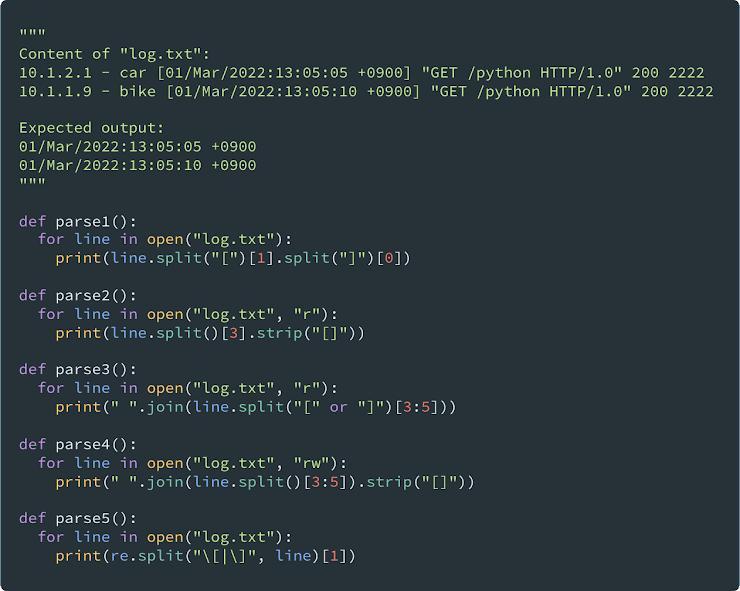
Answers
Answer:
1, 4, 5
Explanation:
parse2:
. In this case it's passing "r" as an argument, which really does absolutely nothing, because whenever you call open("file.txt") it defaults to reading mode, so all you're doing is explicitly passing the "r". So let's look at the first line. Whenever you call str.split() without any arguments, by default it splits it by empty text, and filters any empty text. So str.split() is not the same as str.split(" ") although it has similar behavior. " ".split(" ") will output ['', '', '', '', '', ''], while " ".split() will output []. So in this case the line.split() will split the string '10.1.2.1 - car [01/Mar/2022:13:05:05 +0900] "GET /python HTTP/1.0" 200 2222' into the list ['10.1.2.1', '-', 'car', '[01/Mar/2022:13:05:05', '+0900]', '"GET', '/python', 'HTTP/1.0"', '200', '2222']. As you can see the the data is split into two pieces of text, AND they include the brackets in both strings. So when it gets the 3 index and strips it of the "[]" it will have the incomplete date
parse3:
In this instance the "r" does nothing as mentioned before the "r" is already defaulted whenever you call open("file.txt") so open("file.txt") is the same as open("file.txt", "r"). So in this case we won't be working left to right, we're going inside the brackets first, kind of like in math you don't don't work left to right in equation 3 + 3(2+3). You work in the brackets first (inside brackets you do left to right). So the first piece of code to run is the line.split("[" or "]"). I actually kind of misspoke here. Technically the "[" or "]" runs first because this doesn't do what you may think it does. The or will only return one value. this is not splitting the line by both "[" and "]". The, or will evaluate which is true from left to right, and if it is true, it returns that. Since strings are evaluated on their length to determine if they're true. the "[" will evaluate to true, because any string that is not empty is true, if a string is empty it's false. So the "[" will evaluate to true this the "[" or "]" will evaluate to "[". So after that the code will run line.split("[") which makes the list: ['10.1.2.1 - car ', '01/Mar/2022:13:05:05 +0900] "GET /python HTTP/1.0" 200 2222']. Now the [3:5] will splice the list so that it returns a list with the elements at index 3 (including 3) to 5 (excluding 5). This returns the list: [], because the previous list only has 2 elements. There are no elements at index 3 to 5 (excluding 5). So when you join the list by " ", you'll get an empty string
parse4:
So I'm actually a bit confused here, I thought the "r+" would open the file in read-writing mode, but maybe this is a different version of python I have no idea, so I'm going to assume it is reading/writing mode, which just means you can read and write to the file. Anyways when you split the line by doing line.split(), as mentioned before it will split by empty spaces and filter any empty spaces. This line will return: ['10.1.2.1', '-', 'car', '[01/Mar/2022:13:05:05', '+0900]', '"GET', '/python', 'HTTP/1.0"', '200', '2222']. and then you splice the list from indexes 3 to 5 (excluding 5). This will return the list: ['[01/Mar/2022:13:05:05', '+0900]'] which has the two pieces of information you need for the date. Now it joins them by a space which will output: '[01/Mar/2022:13:05:05 +0900]'. Now when you strip the "[]" you get the string: '01/Mar/2022:13:05:05 +0900' which is the correct output!
parse 5:
So in this example it's using re.split. And the re.split is splitting by "[" or "]" which is what re.split can be used for, to split by multiple strings, which may be confused by string.split("[" or "]") which is not the same thing as explained above what the latter does. Also the reason there is a backslash in front of the [ and ] is to escape it, because normally those two characters would be used to define a set, but by using a \ in front of it, you're essentially telling regex to interpret it literally. So in splitting the string by "[" and "]" you'll get the list: ['10.1.2.1 - car ', '01/Mar/2022:13:05:05 +0900', ' "GET /python HTTP/1.0" 200 2222'] which has 3 elements, since it was split by the [ and the ]. The second element has the date, so all you need to do is index the list using the index 1, which is exactly what the code does
In order to average together values that match two different conditions in different ranges, an excel user should use the ____ function.
Answers
Answer: Excel Average functions
Explanation: it gets the work done.
Answer:
excel average
Explanation:
Please help ASAP!!! :))

Answers
Answer:
You can upgrade the OS by applying SECURITY patches to the server
Explanation:
I can't think of anything else it could be
Three years later, you're still consulting for CNT Books. The network has more than 15 subnets and 10 routers in several buildings and locations. You have been keeping up with the network by configuring the routers statically. However users have had problems with downtime in the past year because of network links going off line, as there's only one route to reach every subnet. The owner wants fault tolerance built into the network to include back up links in case a primary link goes offline. You're concerned that the current router configuration method will still cause some downtime, even if the backup links operate correctly. Why might there be downtime if a primary link goes offline but the backup link is ok? What can you do to reduce the possibility of downtime?
Answers
There may be downtime if a primary link goes offline but the backup link is ok because the router configuration is static, meaning the router will not automatically detect the new backup link and switch to it.
What is the configuration ?Configuration is the way in which components of a system or a network are connected and arranged. It is the specific arrangement of hardware, software, networks and other components that make up a system or a network. It is also the process of setting up or organizing the components of a system so that they can properly interact with one another and perform as expected. Configuration can refer to anything from the configuration of a single computer to the configuration of a large-scale computer network. Configuration also includes the setup of applications, services and databases that are used in the system or network.
To learn more about configuration
https://brainly.com/question/9978288
#SPJ1
the acronym PC stands of
Answers
Answer:
personal computer
Explanation:
It stands for personal computer
Which are common applications of Deep Learning in Artificial Intelligence (AI)?
Answers
Answer:
Deep learning uses huge neural networks with many layers of processing units, taking advantage of advances in computing power and improved training techniques to learn complex patterns in large amounts of data. Common applications include image and speech recognition.
flow chart to read 50 numbers and print summation of even numbers only
Answers
The sum of terms in an arithmetic progression formula is used to get the sum of even numbers formula. Sum of Even Numbers Formula is written as n(n+1), where n is the total number of entries in the series.
What is print summation of even numbers only?Python comes with a built-in method called sum() that adds up the values in the list. Syntax: sum (iterable, start) (iterable, start) Iterable:
Most importantly, iterable should be numbers. Start: This start is added to the total of the iterable's numbers.
Therefore, By definition, when a number is divided by two, there is never a remainder. There will therefore be no residue when it is added to another even integer.
Learn more about summation here:
https://brainly.com/question/29334900
#SPJ1
write a recirsive function named productsof odds that accepts a tuple
Answers
Answer:
def productOfOdds(t):
if len(t) == 1:
if t[0] % 2 == 1:
return t[0]
else:
return 1
else:
if t[0] % 2 == 1:
return t[0] * productOfOdds(t[1:])
else:
return productOfOdds(t[1:])
t = (1, 2, 3, 4, 5, 6, 7, 8, 9)
print("Product of odd elements:", productOfOdds(t)
Which holds all of the essential memory that tells your computer how to be
a computer (on the motherboard)? *
O Primary memory
Secondary memory
Answers
Hope that helps have a nice day purr:)
3
Drag each label to the correct location on the image.
An organization has decided to initiate a business project. The project management team needs to prepare the project proposal and business
justification documents. Help the management team match the purpose and content of the documents.
contains high-level details
of the proposed project
contains a preliminary timeline
of the project
helps to determine the project type,
scope, time, cost, and classification
helps to determine whether the
project needs meets business
needs
contains cost estimates,
project requirements, and risks
helps to determine the stakeholders
relevant to the project
Project proposal
Business justification
Answers
Here's the correct match for the purpose and content of the documents:
The Correct Matching of the documentsProject proposal: contains high-level details of the proposed project, contains a preliminary timeline of the project, helps to determine the project type, scope, time, cost, and classification, helps to determine the stakeholders relevant to the project.
Business justification: helps to determine whether the project needs meet business needs, contains cost estimates, project requirements, and risks.
Please note that the purpose and content of these documents may vary depending on the organization and specific project. However, this is a general guideline for matching the labels to the documents.
Read more about Project proposal here:
https://brainly.com/question/29307495
#SPJ1
True or false: Desktop computers, cell phones, and tablet computers are examples of new-to-the-world products considered disruptive innovations.
Answers
A new product is a product that is new to the company introducing it even though it may have been made in same form by others.
What is new product with example?In this case, it is appropriate to take into account the population of American adults who use cell phones and tablets if the data are referring to the use of mobile devices for local weather forecasts and dining information. As a result, the figures are consistent with the proportion of adults in the United States who own mobile devices, such as smartphones or tablets. A census is a survey of all the observational items for a population. Censuses are enumerations of the entire population or groups at a specified period in time, based on clearly defined characteristics such population size, production, and traffic on particular routes. In some circumstances, the term "sample census" has a distinct connotation.To learn more about new product refer to:
https://brainly.com/question/14736470
#SPJ4
What is a word processing program? Give examples of word processing programs.
Answers
Answer:
A word processor, or word processing program, does exactly what the name implies. It processes words. It also processes paragraphs, pages, and entire papers. Some examples of word processing programs include Microsoft Word, WordPerfect (Windows only), AppleWorks (Mac only), and OpenOffice.org.
The movie polar express was critically acclaimed due to the unbelievably lifelike movements of Tom Hanks character
Answers
Answer:
False
Explanation:
a brief written summary of employment history, education, and other related
information.
essay
bold
resume
font
Answers
Answer:
Heres my answer
Explanation:
Mention your current job title and professional experience. Say how you want to help the employer achieve their goals. Add info on your key achievements to prove you can deliver results when hired. Limit it to 3 or 5 sentences and use numbers whenever possible.
Answer: c. resume
Explanation:
Which of the following is true of how computers represent numbers?
Answers
Answer:
C. Binary can be used to represent more complex, higher level abstractions, including but not limited to numbers, characters, and colors. D. When data is large enough computers switch to using decimal representation instead of binary, because you can represent larger numbers with fewer digits
Explanation:
Answer:
D
Explanation:
which of the following is a proprietary OS for desktop and loptop computers?
conguardelation
Answers
Answer:
windows
Explanation:
windows is the best operating system for desktop and laptop