Discuss Coding and error control techniques in wireless network
technology
Answers
Coding and error control techniques play a crucial role in wireless network technology to mitigate the effects of channel impairments and improve data reliability.
In wireless network technology, coding and error control techniques are employed to address the challenges of unreliable wireless channels and mitigate the impact of errors during data transmission. These techniques aim to improve data reliability and ensure accurate delivery of information.
Error detection techniques, such as cyclic redundancy check (CRC), enable the receiver to identify whether errors have occurred during transmission. By appending a checksum to the transmitted data, the receiver can compare it with the received data and detect any discrepancies.
Error correction techniques, like forward error correction (FEC), allow the receiver to correct errors without retransmission. FEC adds redundancy to the transmitted data, which enables the receiver to reconstruct the original message even if some errors have occurred.
Data encoding techniques, such as modulation schemes, convert digital data into analog signals suitable for wireless transmission. These schemes include amplitude shift keying (ASK), frequency shift keying (FSK), and phase shift keying (PSK), among others. Each scheme has its own advantages and trade-offs in terms of data rate, robustness against noise, and bandwidth efficiency.
By implementing coding and error control techniques, wireless networks can mitigate the effects of channel impairments, including noise, interference, and fading. These techniques enhance data integrity, improve transmission reliability, and ultimately contribute to the overall performance and efficiency of wireless communication systems.
Learn more about Coding and error control techniques: brainly.com/question/33209081
#SPJ11
Related Questions
A table that automatically analyzes and summarizes your data is called a/an
Answers
Which increases the rate of soil formation?
Answers
Answer: Increased temperature increases the rate of chemical reactions, which also increases soil formation. In warmer regions, plants and bacteria grow faster, which helps to weather material and produce soils. In tropical regions, where temperature and precipitation are consistently high, thick soils form.
Explanation: Hope this works
They are created from rocks (the parent material) by weathering and erosive forces of nature. Parent material is broken down by a variety of factors, including water, wind, gravity, temperature change, chemical reactions, living things, and pressure variations.
What are the factor involving in the formation of soil?Parent materials' rate of weathering and, consequently, soil characteristics like mineral composition and organic matter concentration are influenced by temperature and precipitation.
Faster plant and bacterial growth in warmer climates aids in the weathering of materials and the formation of soils. Thick soils develop in tropical areas where the temperature and precipitation are both constantly high.
Therefore, The rate of chemical reactions is accelerated by rising temperature, which also accelerates soil formation.
Learn more about soil formation here:
https://brainly.com/question/19554237
#SPJ2
With respect to iot security, what term is used to describe the digital and physical vulnerabilities of the iot hardware and software environment?
a. Traffic Congestion
b. Device Manipulation
c. Attack Surface
d. Environmental Monitoring
Answers
Answer: Answer Surface
Explanation:
Some one help pls will mark brainless !!!!!
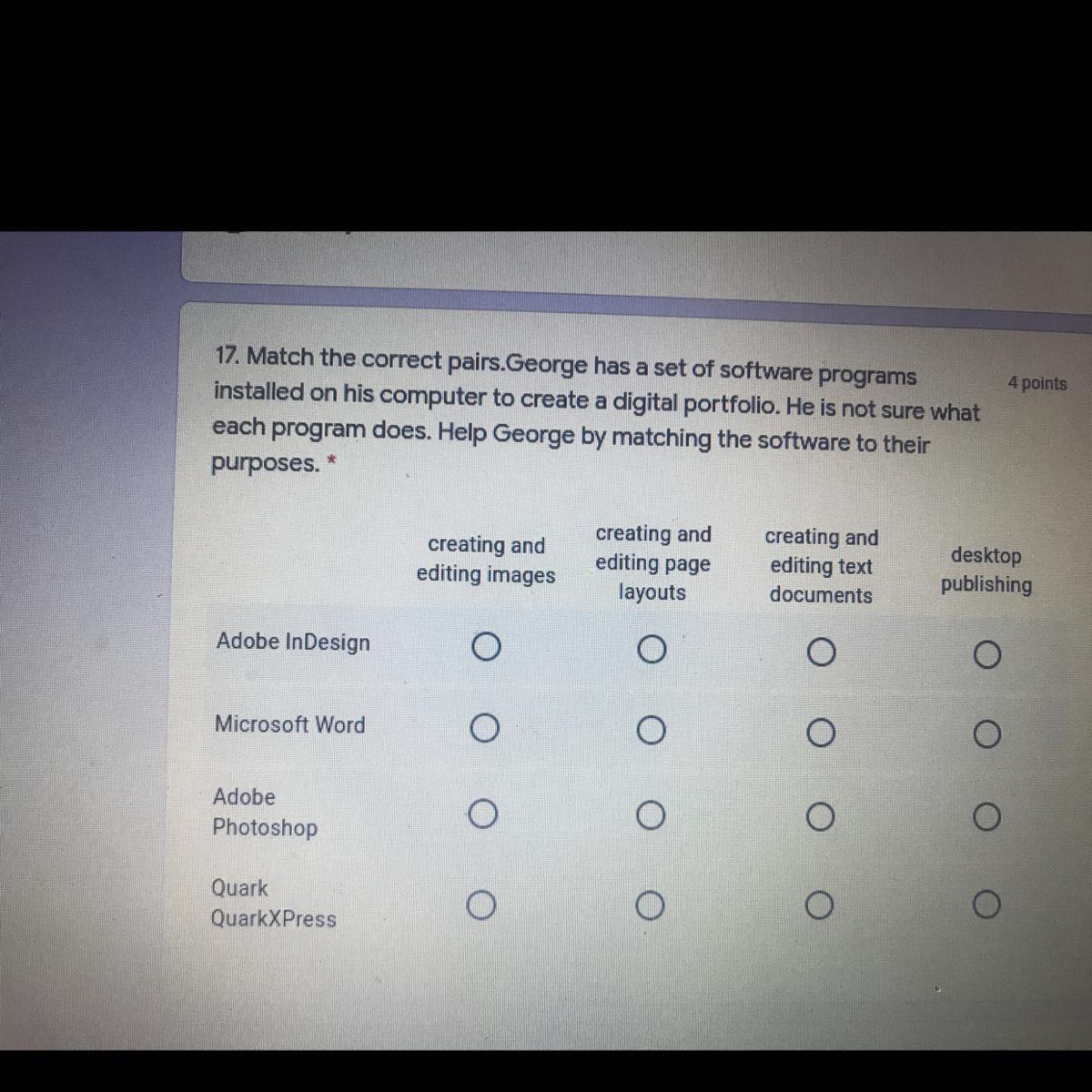
Answers
microsoft word- creating and editing word documents
adobe indesign- layouts
qaurk- publishing
what is output by the following?
print("/\\")
print("\\/")
Answers
Answer:
/\\
\\/
Explanation:
It literally says it. :skull:
What are some useful applications of video games?
Answers
Answer:
Steam, Origin, Uplay and epic games
Explanation:
Who do you like more?
Lolbit
-or-
Mangle

Answers
Answer: lolbit
Explanation: she is my glitchy idol along with the shadows and Mr. Afton's cult.

Answer:
Mangle
Explanation: just because.
What is a WYSIWG program
Answers
Answer: WYSIWYG (pronounced wiz-ee-wig) is a type of editing software that allows users to see and edit content in a form that appears as it would when displayed on an interface, webpage, slide presentation or printed document.
Explanation:
What is intoroperability in information systems, and why is it an important component of systerns development, espocialily in the long-term care field? Why is a database an important component of a healithcare setting's information system?
Answers
Interoperability in information systems refers to the capacity of different systems and applications to communicate and exchange data efficiently. It is a critical component of systems development, particularly in the long-term care field, where data exchange between various healthcare providers, practitioners, and patients is crucial for optimal patient outcomes
.Interoperability allows for seamless sharing of information across systems and promotes better care coordination and patient engagement. This, in turn, leads to enhanced clinical decision-making and improved patient outcomes. It also improves data accuracy, eliminates data duplication, and promotes efficient workflows. Besides, interoperability in information systems ensures that patient data is securely shared across healthcare providers, ensuring that patients receive timely and accurate care
.Database systems are an important component of healthcare settings' information systems for several reasons. They store, organize, and manage vast amounts of patient information, such as medical records, patient history, diagnostic test results, medication records, and appointment schedules. This information is critical in making informed clinical decisions and providing high-quality care to patients. Database systems ensure that patient data is readily available, accurately stored, and easily accessible to authorized users, thus enhancing the quality of patient care
.Furthermore, databases ensure data security and privacy by providing measures such as access controls, data encryption, and secure data storage. They also support real-time reporting, analysis, and data visualization, allowing healthcare providers to track patient outcomes, identify trends, and make data-driven decisions that improve care quality and reduce costs.In conclusion, interoperability in information systems and databases are essential components of healthcare settings' information systems. They promote seamless data exchange, efficient workflows, better care coordination, improved patient outcomes, and enhanced data security and privacy.
To know more about communicate visit:
brainly.com/question/33604736
#SPJ11
Business and Property Spreadsheet Project
The spreadsheet calculations should be set up in a systematic manner. Your set-up should contain a list of the given values, and as many calculated values as possible. Make your spreadsheet as 'active' as possible by using cell references (so that if one value is changed, subsequent calculations will automatically update). Use absolute cell references in special situations. Bob and Angelique Mackenzie bought a property valued at $84,000 for $15,000 down with the balance amortized over 20 years. The terms of the mortgage require equal payments at the end of each month. Interest on the mortgage is 3.4% compounded semi-annually and the mortgage is renewable after five years.
a. What is the size of the monthly payment?
b. Prepare an amortization schedule for the first five-year term. Make sure your payments are rounded to the nearest cent.
c. What is the cost of financing the debt during the first five-year term?
d. If the mortgage is renewed for a further five years at 4.2% compounded semi-annually, what will be the size of each monthly payment?
Answers
Monthly payment = $69,000 * (0.002824 / (1 - (1 + 0.002824)^(-240))) = $386.56
a. The size of the monthly payment can be calculated using the formula for the present value of an annuity. In this case, the present value of the mortgage is $84,000 - $15,000 = $69,000 (the amount left to be paid after the down payment). The interest rate is 3.4% compounded semi-annually, so the monthly interest rate is (1 + 0.034/2)^(2/12) - 1 = 0.002824. The number of monthly payments is 20 years * 12 months/year = 240. Plugging these values into the formula, the size of the monthly payment is:
Monthly payment = $69,000 * (0.002824 / (1 - (1 + 0.002824)^(-240))) = $386.56 (rounded to the nearest cent).
b. To prepare an amortization schedule for the first five-year term, we need to calculate the interest and principal portions of each monthly payment. The interest portion can be calculated by multiplying the outstanding balance at the beginning of the month by the monthly interest rate. The principal portion can be calculated by subtracting the interest portion from the monthly payment.
c. The cost of financing the debt during the first five-year term can be calculated by summing up the interest portions of all the monthly payments during this period.
d. If the mortgage is renewed for a further five years at an interest rate of 4.2% compounded semi-annually, the size of each monthly payment can be calculated using the same formula as in part a, but with the new interest rate.
To know more about mortgage refer for:
https://brainly.com/question/1318711
#SPj11
By using the msleep dataset in R. Determine which mammals are outliers in terms of sleep_total. Outliers, for the sake of this question, are defined as values that are more than 1.5 standard deviations from the mean. Display the name and sleep_total of the mammals which are outliers
Answers
The m sleep data set in R is used to get the mammals that are outliers in terms of sleep_total. Outliers are values that are more than 1.5 standard deviations from the mean.
```{r}library(dplyr)#Reading data in Rmsleep<- read.csv("https://people.sc.fsu.edu/~jburkardt/data/csv/msleep.csv")#Finding Mean and Standard deviation of Sleep_total of all animalsmean_sleep <- mean(msleep$sleep_total)sd_sleep <- sd(msleep$sleep_total)#Calculating lower and upper limit of Sleep_total of all animalslower_limit_sleep <- mean_sleep - 1.5*sd_sleepupper_limit_sleep <- mean_sleep + 1.5*sd_sleep#Finding outliers in sleep_total of all animalsoutliers_sleep
<- msleep %>% filter(sleep_total < lower_limit_sleep | sleep_total > upper_limit_sleep)#Displaying the name and sleep_total of mammals which are outliers in sleep_totaloutliers_sleep %>% select(name, sleep_total)```The above code gives you the name and sleep_total of the mammals which are outliers in terms of sleep_total.
To know more about data visit:
https://brainly.com/question/21927058
#SPJ11
What is the output, if the input is 3 2 4 5? all variables are ints. cin >> num; for (i = 0; i < num; i) { cin >> curr; cout << curr; }
Answers
The given code snippet is incomplete because the termination condition of the for loop is missing. However, I can provide you with an explanation of what the code does with the given input.
The code starts by taking an integer input from the user and storing it in the variable "num". This input is used to determine the number of iterations for the for loop. Next, the code enters the for loop, which iterates from i = 0 until i is less than "num". However, since there is no increment or decrement statement in the loop, it will create an infinite loop. Inside the loop, the code takes integer inputs from the user and stores them in the variable "curr". Then, it outputs the value of "curr" using the "cout" statement. Since the loop is infinite, the code will continuously prompt the user for input and display it on the screen until it is manually terminated. The given code snippet takes an integer input from the user and stores it in the variable "num". This value determines the number of iterations for the for loop. The for loop starts with the initialization of the variable "i" to 0. Then, it checks if "i" is less than "num". Since "i" is initially 0, the condition will be true and the loop will execute. However, the loop lacks an increment or decrement statement, which would usually be used to modify the loop control variable. Inside the loop, the code takes integer inputs from the user and stores them in the variable "curr". Then, it outputs the value of "curr" using the "cout" statement. Without the increment or decrement statement, the loop will create an infinite loop. The program will continuously prompt the user for input and display it on the screen until it is manually terminated.
In conclusion, the given code snippet will create an infinite loop that prompts the user for integer inputs and displays them on the screen. The loop lacks an increment or decrement statement, leading to an infinite iteration.
To learn more about termination condition visit:
brainly.com/question/31933523
#SPJ11
The SQL ________ statement allows you to combine two different tables.
A. SELECT
B. GROUP BY
C. JOIN
D. COMBINE
E. ORDER BY
Answers
The JOIN statement in SQL allows you to combine two different tables based on a common column or key. The correct option is C. JOIN.
This is a powerful feature in SQL that allows you to work with data from multiple tables as if it were in a single table. It is particularly useful for analyzing large datasets and performing complex queries that require data from multiple sources. The other answer options, such as SELECT, GROUP BY, and ORDER BY, are also important SQL statements, but they do not specifically allow for the combination of tables. The correct option is C. JOIN.
Learn more about SQL visit:
https://brainly.com/question/31663284
#SPJ11
in c++, the member access operator arrow is >>.
Answers
In C++, the member access operator arrow is actually represented by "->" and not ">>". The "->" operator is used to access the members (variables or functions) of an object through a pointer to that object. It's typically used with pointers to instances of classes or structs in C++.
I'm sorry, but that statement is incorrect. In C++, the member access operator arrow is represented by the symbol "->". It is used to access the members of an object that is pointed to by a pointer. For example, if we have a pointer "p" pointing to an object of class "myClass", and "myClass" has a member function called "myFunction", we can access that function using the arrow operator like this: "p->myFunction()".
The >> operator, known as the stream extraction operator, is used for input operations on streams such as std::cin (standard input stream) or file streams. It is used to extract values from the stream and store them in variables.
Learn more about Access Operator here-
https://brainly.com/question/30176609
#SPJ11
What is a string in Python language?
A) An ordered set of characters
B) An ordered set of values
C) A sequence of Booleans
D) A sequence of numbers
Answers
Answer:
A
Explanation:
a string consists of letters and numbers
like "myUsername123" can be a string
now their order is important.
but they are not booleans, and they are not necessarily only numbers, and "values" is too vague
so its A
What would happen for the given operation sequence for the shadow page table and nested page table? Explain your answer.Please make copy paste availableFor systems to be able to support multiple virtual machines, two levels of memory virtualization would be needed. Each of the virtual machines would control the mapping of the virtual address to the physical address. The hypervisor would then map the physical address of each of the virtual machines to the machine address. To help speed up the process of these mappings, shadow paging is used to help duplicate each of the virtual machine’s page tables in the hypervisor. It would intercept the virtual address to the physical address mapping changes to keep both copies consistent. To help remove some of the complexity of the shadow page tables, a hardware approach called a nested page table supports the two classes of page tables and can navigate through these tables within hardware directly.Consider the following sequence of operations:1) Create Process2) TLB Miss3) Page Fault4) Context SwitchThis is all the information have available to provide.Please make copy paste available
Answers
For the given operation sequence, both the shadow page table and nested page table would be utilized to facilitate memory virtualization.
When a process is created, its virtual address is mapped to a physical address using the page tables of the virtual machine. If there is a TLB miss, the shadow page table in the hypervisor would be consulted to provide the mapping. If a page fault occurs, the hypervisor would use the shadow page table to create a new mapping for the virtual address. Finally, during a context switch, the hypervisor would switch to the appropriate page tables for the new process.
The use of shadow paging helps to speed up the mapping process by duplicating each virtual machine's page table in the hypervisor and keeping them consistent. However, this can add complexity to the system. To simplify this, a nested page table is used, which supports both classes of page tables and allows for direct navigation through these tables within hardware.
Overall, the operation sequence would involve the utilization of both shadow page table and nested page table to facilitate memory virtualization and provide efficient mapping of virtual addresses to physical addresses for each process.
To learn more about the operation sequence:
https://brainly.com/question/20468691
#SPJ11
What navigation/mission planning information is sent back to the remote pilot from the AV?
Answers
Answer:
Explanation:The type of navigation/mission planning information that is sent back to the remote pilot from the autonomous vehicle (AV) will depend on the specific system and the type of mission being undertaken. However, in general, the following information may be sent back to the remote pilot:
Status updates: The AV may send status updates to the remote pilot, indicating that the vehicle is operating as intended or that there are issues that need attention.
Real-time video: The AV may transmit live video feed from its onboard cameras to the remote pilot, allowing the pilot to monitor the vehicle's surroundings and progress.
Flight path and altitude: The AV may transmit information about its current flight path and altitude to the remote pilot, allowing the pilot to track the vehicle's progress and ensure it remains on course.
Battery and power status: The AV may transmit information about its battery and power status, allowing the remote pilot to ensure the vehicle has sufficient power to complete its mission.
Environmental data: The AV may transmit environmental data, such as temperature, humidity, wind speed and direction, and air pressure, to the remote pilot, allowing the pilot to monitor conditions that may affect the vehicle's performance.
Error messages: The AV may transmit error messages or alerts to the remote pilot, indicating that something has gone wrong with the vehicle's operation or that an issue requires attention.
Overall, the information that is sent back to the remote pilot will depend on the level of autonomy of the AV, the specific mission being undertaken, and the capabilities of the communication system used to transmit data between the vehicle and the remote pilot.
What is the purpose of the 300 Log?
Answers
Answer:
The OSHA Form 300 is a form for employers to record all reportable injuries and illnesses that occur in the workplace, where and when they occur, the nature of the case, the name and job title of the employee injured or made sick, and the number of days away from work or on restricted or light duty, if any.
Explanation: brainliest plzzzz!
differenticate between half and full deplex modes of transmission in three points
Answers
Answer:
In simplex mode, the signal is sent in one direction. In half duplex mode, the signal is sent in both directions, but one at a time. In full duplex mode, the signal is sent in both directions at the same time.In simplex mode, only one device can transmit the signal. In half duplex mode, both devices can transmit the signal, but one at a time. In full duplex mode, both devices can transmit the signal at the same time.Full duplex performs better than half duplex, and half duplex in turn performs better than simplex.Hope it helps!
Which of the following is hardware or software that monitors and controls network traffic to prevent security breaches?
O trojan horse
O firewall
O anti-malware
O keylogger
Need answer now!!!!!
Answers
Answer:
Firewall
Explanation:
A trojan horse and keylogger are types of malware. While an anti-malware software may come with a firewall built in, the firewall is still the thing monitoring network traffic.
hi please help ASAP it's about html!

Answers
Create a HTML code for writing a web page for your school time-table.
Answer :-<html>
<head>
<title> Time Table </title>
</head>
<hrcolor = "red">
<hrcolor = "blue">
<body>
<table><tr = "7"><md = "7"><Period 1_></table>
</body>
</html>
\( \\ \)
Answered by - ItzMaster
How are the internet and the web related?
A.
They are not related.
B.
They are the same thing.
C.
The internet runs on the web.
D.
The web runs on the internet.
Answers
Answer:
hi
Explanation:
i think it is it is C
hope it helps
have a nice day
Click to review the online content. Then answer the question(s) below, using complete sentences. Scroll down to view additional questions.
Online Content: Site 1
Explain how to determine if an online source is credible. (site 1)
Answers
Determining if an online source is credible is an important skill for research and academic purposes. There are many factors that can help you evaluate the reliability and trustworthiness of a website or an article.
What are some common criteria to check source credibility?
Origin: Check to see if the website was created by a reputable organisation or author. The URL or copyright information can be used to identify the author. Trustworthy websites usually end in .org, .edu, .gov, or any recognizable web address.Currency: Check if the information is up-to-date and current. You can look at the date of publication or update on the website or article. Outdated information may not reflect the latest developments or research on a topic.Relevance: Check if the source is relevant to your research topic and purpose. You can look at the title, abstract, introduction, and conclusion of an article to see if it matches your research question and scope.Authority: Check if the author and publication are a trusted authority on the subject you are researching. You can look at their credentials, affiliations, publications, citations, and reputation in their field.Accuracy: Check if the information is factual, verifiable, and supported by evidence. You can look at the sources that the author cited and see if they are easy to find, clear, and unbiased. You can also cross-check with other sources to confirm the accuracy of the information.Purpose: Check if the source has a clear purpose and audience. You can look at the tone, language, style, and bias of the source to see if it is objective, informative, persuasive, or entertaining. You should avoid sources that have hidden agendas, conflicts of interest, or misleading claims.These are some general guidelines that you can follow when evaluating online sources for credibility. However, you should also use your own critical thinking skills and judgment when deciding whether a source is suitable for your research.
To learn more about website, visit: https://brainly.com/question/28431103
#SPJ1
clicking either the date & time button or the ____ button opens the header & footer dialog box.
Answers
clicking either the date & time button or the slide button opens the header & footer dialog box.
What is a dialog box?
An informational and response-prompting graphical control element called a dialog box presents information to the user. Depending on whether they prevent communication with the software that opened the dialog, dialog boxes are categorized as "modal" or "modeless."
A dialog box is a transient window that a program creates to collect user input. Dialog boxes are frequently used in applications to ask users for more details about menu items.
To learn more about a dialog box, use the link given
https://brainly.com/question/23119185
#SPJ1
Whenever Ella gets an assignment in one of her classes, she immediately writes it down in her planner. At home, Ella keeps a notepad and calendar on her desk so she can stay organized with all her coursework. This information suggests that Ella is likely to score high on the five-factor personality trait of
Answers
The five-factor personality trait that Ella is likely to score high on is conscientiousness. Conscientious individuals are typically organized,
detail-oriented, and diligent. Ella's behavior of immediately writing down assignments in her planner and keeping a notepad and calendar on her desk indicates her conscientiousness. These actions demonstrate her proactive approach to staying organized and managing her coursework effectively, which are characteristics associated with conscientious individuals.
Conscientiousness is one of the Big Five personality traits and reflects an individual's tendency to be responsible, dependable, and goal-oriented. It encompasses behaviors such as being organized, planning ahead, and paying attention to details. Ella's habit of promptly recording assignments in her planner and maintaining a notepad and calendar aligns with these conscientious traits. By staying organized and managing her coursework diligently, Ella is likely to demonstrate a high level of conscientiousness, which can contribute to her academic success and overall achievement.
Learn more about Conscientious here:
https://brainly.com/question/30772564
#SPJ11
coding is the process of organizing, arranging, and classifying coding units.a. true
b. false
Answers
The statement "coding is the process of organizing, arranging, and classifying coding units" is false.
Coding refers to the act of writing instructions or commands in a programming language to create software or perform specific tasks. It involves translating human-readable instructions into a language that computers can understand. While organization, arrangement, and classification of coding units can be a part of the coding process, it is not the sole definition of coding. Coding primarily involves writing logical and sequential instructions, implementing algorithms, and manipulating data to achieve desired outcomes. The process of organizing, arranging, and classifying coding units is more closely related to software engineering practices, such as code organization, modular design, and code documentation, which aid in maintaining and managing complex software systems.
Learn more about Coding here: brainly.com/question/17204194
#SPJ11
Sort the options for formatting a table under the tab where they are located.

Answers
Answer:
yes those are the correct order
Explanation: post protected
How do i cancel my subscription please help it doesnt say cancel anywhere todays the last day of my free trial help
Answers
Answer:
The answer is "turn off auto-renewal"
Explanation:
In the given question it is not defined, which type of subscription it is taking about. so, we assume, it is talking about software subscription and the cancellation of the software can be defined as follows:
The application base subscription provides a monthly or yearly service license scheme, which allows customers to purchase the cost per user. In general, users were also obligated to claim for there initial fee soon, which also enables it to use the software and by disabling the auto-renewal option we can cancel our subscription.what is the arrangement of various flash elements, such as the tools panel, control panel, property inspector and stage
Answers
Answer:
could have used a browser but ok
Explanation:
The arrangement of various flash elements such as the tools panel control panel property inspector and windows is called the Workspace. Explanation: The workspace in a computer system makes us easy to navigate to different features and control options.
Implement the frame replacement algorithm for virtual memory
For this task, you need to perform the simulation of page replacement algorithms. Create a Java program which allows the user to specify:
the total of frames currently exist in memory (F),
the total of page requests (N) to be processed,
the list or sequence of N page requests involved,
For example, if N is 10, user must input a list of 10 values (ranging between 0 to TP-1) as the request sequence.
Optionally you may also get additional input,
the total of pages (TP)
This input is optional for your program/work. It only be used to verify that each of the page number given in the request list is valid or invalid. Valid page number should be within the range 0, .. , TP-1. Page number outside the range is invalid.
Then use the input data to calculate the number of page faults produced by each of the following page replacement algorithms:
First-in-first-out (FIFO) – the candidate that is the first one that entered a frame
Least-recently-used (LRU) –the candidate that is the least referred / demanded
Optimal – the candidate is based on future reference where the page will be the least immediately referred / demanded.
Answers
To implement the frame replacement algorithm for virtual memory, you can create a Java program that allows the user to specify the total number of frames in memory (F), the total number of page requests (N), and the sequence of page requests.
Optionally, you can also ask for the total number of pages (TP) to validate the page numbers in the request list. Using this input data, you can calculate the number of page faults for each of the three page replacement algorithms: First-in-first-out (FIFO), Least-recently-used (LRU), and Optimal.
To implement the frame replacement algorithm, you can start by taking input from the user for the total number of frames (F), the total number of page requests (N), and the sequence of page requests. Optionally, you can also ask for the total number of pages (TP) to validate the page numbers in the request list.
Next, you can implement the FIFO algorithm by maintaining a queue to track the order in which the pages are loaded into the frames. Whenever a page fault occurs, i.e., a requested page is not present in any frame, you can remove the page at the front of the queue and load the new page at the rear.
For the LRU algorithm, you can use a data structure, such as a linked list or a priority queue, to keep track of the most recently used pages. Whenever a page fault occurs, you can remove the least recently used page from the data structure and load the new page.
For the Optimal algorithm, you need to predict the future references of the pages. This can be done by analyzing the remaining page requests in the sequence. Whenever a page fault occurs, you can replace the page that will be referenced farthest in the future.
After processing all the page requests, you can calculate and display the number of page faults for each algorithm. The page fault occurs when a requested page is not present in any of the frames and needs to be loaded from the disk into memory.
By implementing these steps, you can simulate the frame replacement algorithm for virtual memory using the FIFO, LRU, and Optimal page replacement algorithms in your Java program.
To learn more about virtual memory click here:
brainly.com/question/30756270
#SPJ11