deborahc1287563 You like Among us too?
Answers
Answer:
i also like Among us
Explanation:
Related Questions
Walt needs to ensure that messages from a colleague in another organization are never incorrectly identified as spam. What should he do?
A.Configure a safe recipient.
B.Configure a blocked sender.
C.Configure a safe sender.
D.Do nothing.
Answers
Answer:
C. Configure a safe sender
Explanation:
It’s dabest thing to do
As per the given scenario, Walt should need to configure a safe sender. The correct option is C.
What is configuration?A system's configuration in communications or computer systems refers to how each of its functional elements is organised in relation to their nature, number, and distinguishing features.
Configuration frequently involves picking the right hardware, software, firmware, and documentation.
A person, group, or organisation that starts the communication is known as the sender. The success of the message stems primarily from this source.
The communication is influenced by the sender's experiences, attitudes, knowledge, competence, perspectives, and culture.
Walt must take care to prevent messages from a colleague in a different organisation from ever being mistakenly classified as spam. He ought to set up a secure sender.
Thus the correct option is C.
For more details regarding configuration, visit:
https://brainly.com/question/13410673
#SPJ2
I need help. So basically the internet on my computer keeps turning off and on at random times. And when I try to reconnect it doesn't work. I restarted my computer and shut it down multiple times. I just need some advice on what I need too do to get it to work.
Answers
Answer:
First of all, check your router (the thing that gives you internet). Maybe that's the problem. It that doesn´t work, try going to settings and going to WIFI. Then disconnect the WIFI and connect it again. Sometimes the WIFI gets connected, but doesn't like ¨grab¨ correctly, so it keeps falling. Hope this helped.
Explanation:
How do you code things to make shapes out of them and add color
Answers
Answer:
go to KhanAcademy and search "Coloring with code" and it should be the first thing at the top
3 different ways that ultrasonic sensors can be used in everyday life.
Answers
Answer:
Ultrasonic Sensors Uses:
Anti-Collision DetectionPeople DetectionContouring or ProfilingPresence DetectionBox Sorting using a Multi-Transducer SystemEasy Control of Trash Collection VehiclesPallet Detection with ForkliftsBottle Counting on Drink Filling MachinesLearn more about Ultrasonic Sensors here
Visit —
https://brainly.in/question/19907919
https://brainly.ph/question/13809853
Hope my answer helps you ✌️
Mark BRAINLIEST
Ultrasonic retro-reflective sensors.
Ultrasonic through-beam sensors.
why is 'Among us' so popular? what is this video game?
Answers
It's a game where there is one (or up to three) impostors among 10 people
The impostor has to sabotage the ship and kill the crewmates.
The crewmates have to find out who the impostor is or finish the given tasks to win.
It is very fun, recommend testing on mobile before installing on PC.
Basically players are all assigned a role as either crew mate or imposter. The crewmates job is to complete tasks while the imposters try and stealthily kill off crewmates.
The crewmates then try and vote out imposters before they kill off the crew
The game is super fun to play with friends and is like a nice mystery
When the prompt function is used in JavaScript, _____ appears.
A.
an error message
B.
a pop-up box
C.
a data warning
D.
a password request
Answers
Answer:
B
Explanation:
instructs the browser to display a dialog with an optional message prompting the user to input some text, and to wait until the user either submits the text or cancels the dialog
GIVING OUT BRAINLIEST AND I AM ALSO WARNING EVERYONE TO NOT ANSWER A BUNCH OF rubbish just to get the points!
EXPLAIN: Describe school community or list 2-3 facts.
Answers
A list of what you could say:
Friendly
Helpful
Understanding
Assertive
Thoughtful
affectionate
Happy
Compassionate
Facts: are the meals good? Is the school safe? It it a good environment?
Digital and analog audio recordings have pros and cons. Do you think the pros of digital recordings outweigh the cons and therefore prefer digital audio recordings? Or, do you think the cons outweigh the pros and therefore you prefer analog audio recordings? Explain. ( USE C.E.R *Claim, Evidence, Reasoning* )
Answers
I think the pros of digital recordings outweigh the cons! I prefer digital audio recordings over analog audio recordings because analog recordings require more financing and preservation. Compared to digital recordings, analog recording equipment is more expensive and the tape deteriorates over time. Which to me personally, doesn't seem to be worth the amount of effort since it's such a process to go through. You can possibly go into debt due to that. Digital recording equipment, on the other hand, is more affordable. It's less time-consuming and although it does have its disadvantages, they're minor. Digital recordings can be stored online. Its data get corrupted? You can get it back! It won't cost you anything.
Select all the correct answers.
Which two of these should a website’s privacy policy created under California Online Privacy Protection Act describe?
third parties that may view the information
name and designation of the author of the policy
effective date and expiration date of the policy
links to third-party policies, if any
approvals necessary to bypass the policy
Answers
approvals necessary to bypass the policy
What is the problem at Monsters, Inc at the beginning of the movie?
A. A supply surplus
B. A lack of demand
C. A supply shortage
E. An employee strike
Answers
Why isn't my brainly post being answered?
Answers
Try deleting then reposting, it may not always pop up in new questions, I will have a look at the question anyway.
Hope this helps!
List at least one thing to check for when you're checking the clarity and professionalism of a document.
Answers
Answer:
Company Style. Verify that the tone and style of the document matches the document type and purpose. ...
Format Review. ...
Grammar and Spelling. ...
Layout Critique. ...
Confirm Accuracy. ...
Answer:
1. Read the cover letter to make sure it's specific, professional, and clear.
2. If you see anything you'd like to change, do that now. Edge 2022
Explanation:
Trust my doppelganger
What connections do you see between variables and the Input-Output-Store-Process model of a computer?
Answers
Match the letter with the feature it represents.
Put responses in the correct input to answer the question.
slide pane
menu bar
drawing toolbar
slide (normal) view
task pane
formatting toolbar
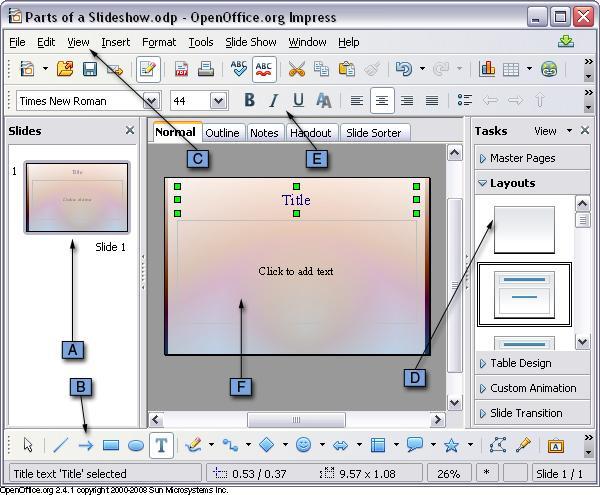
Answers
B is drawing toolbar
C is menu bar
D is task pane
E is formatting toolbar
F is slide normal view
What is output?
Print (12 % 5)
Answer
0
5
2
1
Answers
Question 12 (2 points)
Match the vocabulary word with the correct definition.
Column A
1.
narrative:
narrative
2.
ludonarrative:
ludonarrative
3.
player agency:
player agency
4.
engagement:
engagement
5.
emotion:
emotion
Column B
a.the game designer creates a world and the story within it
b.the choices of the player shape what happens in their own personal experience
c.the way that players get personally involved in a game and influence the outcome
d.a feeling that can be positive, negative, or neutral
e.the level that a player is interacting with the story or game
Answers
Explain how you think robotics plays a part in the subway driver's job.
Answers
Answer: Because the robotics help the train move
Explanation:
Please help! -Screenshot-
I am a little unsure about this answer, please let me know if I am correct or if I need to chang it.

Answers
Answer: you're correct
Explanation:
that's the only one that has privacy and safety in mind;
password-protected sites are important for keeping your account & info safe
your age and appearance is private and personal information
posting photographs of yourself can be unsafe
so B is right
Hope that helps<3
_____ describes the layout of the screen. Block-based, Interface, Editor, Player
Answers
Write 2 paragraphs. 1 comparing Shrek the movie and Shrek the musical and another contrasting them.
Answers
The scene which I’m going to compare between each medium will be the scene in which Shrek interrupts the wedding between Fiona and Lord Farquaad. First we will observe the scene from the movie and then go onto the musical afterward to compare. The movie has Mike Myers as Shrek, Eddie Murphy as Donkey, Cameron Diaz as Fiona, and John Lithgow as Farquaad, directed by Andrew Adamson and Vicky Jenson, and produced by Dreamworks, not Disney.
The scene starts with Shrek and Donkey arriving outside the church, discussing whether or not Fiona and Farquaad have said “I do” yet. Shrek then continues to throw donkey up to look into the window to see whether or not they have, having the camera cut from inside the cathedral, to a camera angle looking down on Shrek, to a side angle showing the window and donkey being thrown into the air. Then after realizing that they had said the line “I do”, Shrek bursts into the cathedral yelling “I object!”, with a view looking back at him from the front, before Fiona and Farquaad are about to kiss, then switching to an angle facing a disgruntled Farquaad and a relieved Fiona. Then the camera follows Shrek as he runs down the aisle, frightening all the attendants, then a quick above shot showing them all standing up, then another close-up. This scene has some power as the music combined with the lines can show the emotion in Shrek (1:16:40).
This part of the scene continues as it switches between the characters talking, then shows a joke where Farquaad makes the audience laugh at Shrek. Fiona looks at the window, showing the sunset, as she begins reciting her curse as she walks to the window and transforms into an ogre, showing Shrek being surprised and sounds of displeasure from Dulok. After that, we have shots from left, to right, then above, as Farquaad has guards seize the two ogres.They fight the guards to try to get to each-other, before Farquaad puts a dagger to Fiona. Shrek then frees his arm and whistles, as we get a show of the dragon flying through the upper window, then a shot looking down upon Farquaad, as he gets eaten by the dragon, with Donkey riding on top of it. The guards back away releasing Shrek and Fiona, as the audience claps and the two ogres tell each-other their feelings, as they kiss and sparkles appear around Fiona, as she floats up and begins glowing, and the camera rotates up her, then around the cathedral, as she then floats back down, landing gently on the ground, as Shrek picks her up it’s revealed that her curse has been lifted and she will now be an ogre forever. The scene ends on Shrek covering up the camera with his hand and the scene transitioning to the swamp where they have a “proper” wedding (1:21:30).
This scene has power with the music and the way the shots move to convey emotion and establish plot. This is a very important scene as it rounds off the movie, coming to the climax of the story, ending on a high note before changing scenes and enacting a musical number followed by credits. Now after going over the scene from the movie, we’re going to go over the play, where they can’t have angles like a movie, so we’re going to see how they try to replicate that scene in play form and see how well they do it. The play stars Brian d'Arcy James as Shrek, Sutton Foster as Princess Fiona, Christopher Sieber as Lord Farquaad, and Chester Gregory II as Donkey.
This scene starts with the curtain opening to the inside of the cathedral and a chorus walking on stage with the priest up on a pedestal and Fiona and Farquaad walking into the scene to stand in front of him. The ceremony then begins with the priest yelling his lines and Fiona looking disgusted. Fiona then asks the priest to skip to the “I do’s” and Farquaad agreeing with her.
In a minimum of 250 words, discuss the technological problems that can occur when consumers emphasize on speed over security.
Answers
1. Vulnerabilities and Breaches: Emphasizing speed often means sacrificing robust security measures. This can lead to vulnerabilities in software, applications, or systems that attackers can exploit. Without adequate security measures, data breaches become more likely, exposing sensitive information such as personal data, financial records, or trade secrets. The aftermath of a breach can be detrimental, including reputational damage, legal consequences, and financial losses.
2. Malware and Phishing Attacks: When speed takes precedence, consumers may overlook potential malware or phishing attacks. By rushing through security checks or bypassing cautionary measures, they inadvertently expose themselves to malicious software or fraudulent schemes. These attacks can compromise personal information, hijack devices, or gain unauthorized access to networks, resulting in financial losses and privacy violations.
3. Inadequate Authentication and Authorization: Speed-centric approaches might lead to weak or simplified authentication and authorization mechanisms. For instance, consumers may choose easy-to-guess passwords or reuse them across multiple platforms, making it easier for attackers to gain unauthorized access. Additionally, authorization processes may be rushed, granting excessive privileges or overlooking necessary access controls, creating opportunities for unauthorized users to exploit system vulnerabilities.
4. Neglected Updates and Patches: Prioritizing speed often means neglecting regular updates and patches for software and systems. By delaying or avoiding updates, consumers miss out on critical security fixes and vulnerability patches. Hackers actively exploit known vulnerabilities, and without timely updates, devices and systems remain exposed to these threats, making them easy targets.
5. Lack of Secure Development Practices: When speed becomes the primary concern, secure development practices might take a backseat. Security testing, code reviews, and quality assurance measures may be rushed or ignored, leading to the inclusion of vulnerabilities in the software or application itself. These vulnerabilities can be exploited by attackers to gain unauthorized access or execute malicious activities.
To mitigate these problems, it is essential to strike a balance between speed and security. Consumers should prioritize security measures such as using strong passwords, enabling multi-factor authentication, regularly updating software, and being cautious of suspicious links or emails. Service providers and developers must also prioritize security in their products and services by implementing secure coding practices, conducting thorough security assessments, and promptly addressing vulnerabilities. Ultimately, a comprehensive approach that values both speed and security is crucial for maintaining a safe and efficient technological ecosystem.
Explanation:
--> used brainly simplify :D
Consumers prioritizing speed over security can lead to several technological problems. This includes vulnerabilities and breaches where attackers can exploit weaknesses in software or systems. Malware and phishing attacks become more likely when security measures are overlooked. Weak or simplified authentication and authorization methods can make it easier for unauthorized users to gain access. Neglecting updates and patches leaves devices and systems vulnerable to known threats. Lastly, rushing through secure development practices may result in the inclusion of vulnerabilities in the software itself. To address these issues, consumers should use strong passwords, update their software regularly, and be cautious of suspicious links or emails. Service providers and developers should prioritize security by conducting thorough security assessments and promptly addressing vulnerabilities. Striking a balance between speed and security is crucial for a safe and efficient technological environment.
How does a resident virus differ from a non-resident virus? !!!25 POINTS!!!!!
A) Resident viruses simply disrupt operations while non-resident viruses will control hosts.
B)Resident viruses will control hosts while non-resident viruses simply disrupt operations.
C)Resident viruses find networks to infect while non-resident viruses load themselves into memory.
D)esident viruses load themselves into memory while non-resident viruses find networks to infect.
Answers
Answer:
The correct answer is **D)** Resident viruses load themselves into memory while non-resident viruses find networks to infect. A resident virus is a type of computer virus that’s deployed and resides within a computer’s random access memory (RAM). A non-resident computer virus, on the other hand, is a type of computer virus that doesn’t reside within a computer’s RAM. Non-resident computer viruses can still be deployed within RAM, but they don’t stay there.
Why is yo utu be down?
(You restrict talking about yo utu be, really)
Answers
On the Audio Tools contextual tab, which tab will control how the audio file appears, if it appears, on the slide itself?
Bookmarks
Playback
Format
Design
Answers
MP3 utilizes playback
Carina's computer is turning off without warning. Which of the following steps should she take to troubleshoot the problem?
A: Try several fixes at once.
B: Uninstall the anti-virus software.
C: Check the cable connections.
D: Remove devices.
Answers
The reason why it’s c is because maybe a cord is loose which is most likely the reason why it turning off all of a sudden (this has also happened to me in real life so trust me on this)
Part 1: Compare the Websites
You are conducting research for a project about elephant sanctuaries. Compare the two websites using the 5 W’s criteria for reliability and validity. For each website, complete the 5 W’s Checklist.
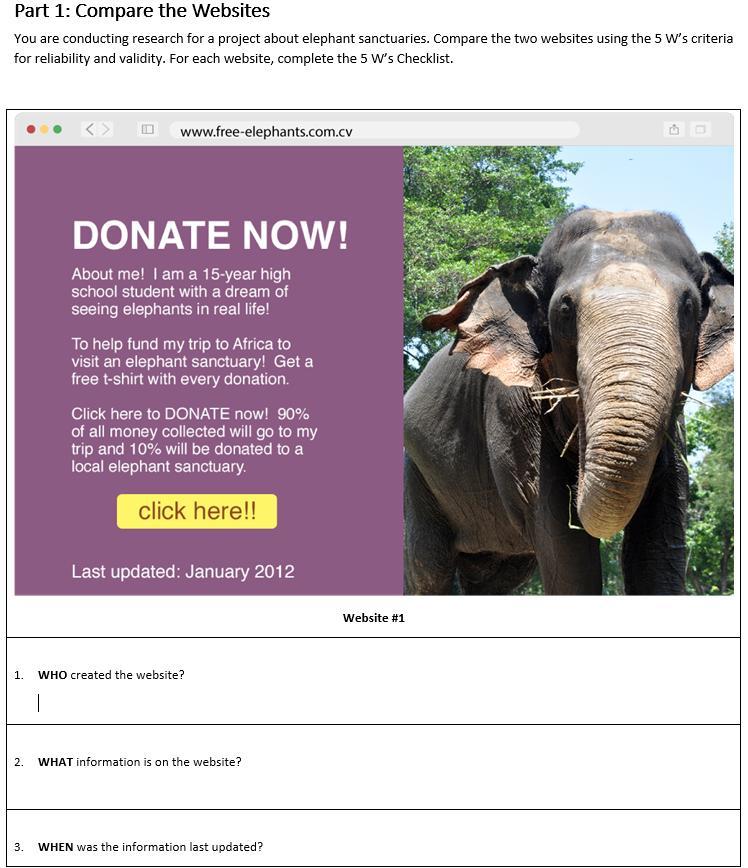




Answers
Answer:
WHO: a 15-year old high school student
WHAT: information about donating to a local elephant sanctuary and a trip
WHEN: January 2012
WHERE: www.free-elephants.com.cv
WHY: To help fund the student's trip to Africa to visit an elephant sanctuary
who: a 15-year-old high school student
what: information about donating to a local elephant sanctuary and a trip
when: January 2012
where: www.free-elephants.com.cv
why: To help fund the student's trip to Africa to visit an elephant sanctuary
Kris is the project manager for a large software company. Which part of project management describes the overall project in detail?
Analysis report
Resources document
Scope
Scope creep
Answers
Which statements correctly compare and contrast the Cut and Copy commands in PowerPoint? Check all that apply.
O Both use galleries to carry out tasks.
O Both are options found in the mini toolbar.
O Both use the Paste command to move text.
O Only the Cut command removes the text from its location.
O Only the Copy command stores information on the clipboard.
Answers
Answer:
If there are only two options, they are:
--- Both are options found in the mini toolbar.
--- Only the Copy command stores information on the clipboard.
If there can be three options, they are:
--- Both are options found in the mini toolbar.
--- Only the Copy command stores information on the clipboard.
--- Only the Cut command removes the text from its location.
PLEASE HELP ITS DUE SOON!!
How do software and hardware work together
A. As a function
B. As a program
C. As a system
D. As a standard
Answers
Answer:
C. As a system.
Explanation:
Software and hardware work together as a system to perform a specific task or a set of tasks. Hardware refers to the physical components of a computer system, such as the processor, memory, hard drive, keyboard, and mouse, while software refers to the instructions, data, and programs that are stored on the hardware and used to perform specific tasks. The hardware provides the platform and resources for the software to run, and the software controls and utilizes the hardware to execute tasks. The two work together in a coordinated manner to achieve the desired outcomes
This is answer
Marsha receive an email saying that she won a free cruise to Alaska. What Marsha didn’t realize is that the email was fake and contained a virus that infected her computer. She sent the email to several of her friends, and now their computers have viruses too. Has Marsha committed a computer crime?
Yes, because she illegally forwarded a private email
No, because she did not knowingly spread or create the virus
No, but she has acted unethically
Yes, because she was the cause of other people’s computers becoming infected
Answers
Answer:
I think the answer is B
Explanation:She sent it to her friends not knowing it would give there computers a virus too.