Data File needed for this Case Problem: NP_EX_8-4.xlsx
Hardin Medical Clinic Catherine Smythe is a personal manager for Hardin Medical Clinic in Toledo, Ohio. Part of Catherine's job is to manage the weekly nursing schedule. The clinic employs 20 nurses—16 full-time and 4 part-time. The clinic needs 12 nurses on weekdays and 10 on weekends. Catherine is working on the schedule for an upcoming week and is trying to accommodate all the vacation and sick-leave requests, while maintaining the required level of on-duty nurses. Catherine asks you to develop a schedule that meets the needs of the clinic and the requests of the nurses. Complete the following:
1. Open the NP_EX_8-4.xlsx workbook located in the Excel8 > Case2 folder included with your Data Files. Save the workbook as NP_EX_8_Clinic in the location specified by your instructor.
2. In the Documentation sheet, enter your name and the date.
3. In the Schedule worksheet, in the range D5:J24, enter 0 in all the cells. In this sheet, 0s and 1s indicate whether an employee is schedule for a shift that day (0 indicates an employee is not scheduled and 1 indicates an employee is scheduled).
4. In the range K5:K24, enter formulas to sum the total number of shifts worked by each employee from Monday through Sunday.
5. In the range L5:L24, calculate the total number of hours worked by each employee during the week by multiplying the number of shifts worked by 8 (each shift is eight hours long).
6. In the range D26:J26, enter the required shifts per day. The clinic requires 12 nurses on the weekdays, and 10 nurses on Saturday and Sunday.
7. In the range D27:J27, enter formulas to sum the total number of shifts scheduled for nurses on each day.
8. In the range D28:J28, enter formulas to calculate the difference between the number of nurses scheduled and the number of nurses required. A negative value indicates that not enough nurses are scheduled to cover that day's shifts.
9. In cell D30, calculate the total shortfall for the week by summing the daily shortfall values in the range D28:J28.
Explore 10. Create a Solver model that sets the value of cell D30 to 0 (indicating that all shifts are covered for every day of the week) by changing the values in the range D5:J24 under the following constraints:
a. Add a binary constraint to force every value in the range D5:J24 to be either a 0 or a 1.
b. Add a constraint to limit the total hours worked by each full-time employee to less than or equal to 40.
c. Add a constraint to limit the total hours worked by each part-time employee to less than or equal to 24.
d. Add a constraint to require that the difference values in the range D28:J28 all equal 0.
e. Add more constraints based on the schedule requests in the range C5:C24 so that nurses are not scheduled to work shifts on days they have requested off. If a nurse has requested a day off, the cell corresponding to that day for that nurse must equal 0.
Explore 11. Run the Solver model using the Evolutionary method. (Solver might take a minute to arrive at a solution.) Confirm that the schedule generated by Solver fulfills all the requirements—all shifts are covered each day, no full-time nurse works more than 40 hours, no part-time nurse works more than 24 hours, and no nurse works on a requested day off.
12. Save the workbook, and then close it.
Answers
To create a nursing schedule that meets the requirements of Hardin Medical Clinic and the requests of the nurses, follow these steps:
1. Open the NP_EX_8-4.xlsx workbook and save it as NP_EX_8_Clinic.
2. Enter your name and date in the Documentation sheet.
3. In the Schedule worksheet, enter 0 in the range D5:J24 to indicate employees' initial schedule.
4. Calculate the total shifts worked for each employee using formulas in the range K5:K24.
5. Calculate the total hours worked for each employee in the range L5:L24.
6. Enter the required shifts per day in the range D26:J26 (12 nurses on weekdays and 10 on weekends).
7. Sum the total shifts scheduled for nurses on each day using formulas in the range D27:J27.
8. Calculate the difference between the number of nurses scheduled and required using formulas in the range D28:J28.
9. Calculate the total shortfall for the week in cell D30 by summing the daily shortfall values in the range D28:J28.
10. Create a Solver model with the following constraints:
a. Add a binary constraint for the range D5:J24.
b. Limit full-time employees to 40 hours or less.
c. Limit part-time employees to 24 hours or less.
d. Require the difference values in the range D28:J28 to equal 0.
e. Add constraints based on schedule requests in the range C5:C24.
11. Run the Solver model using the Evolutionary method. Confirm that the generated schedule fulfills all requirements.
12. Save and close the workbook.
To know more about Evolutionary method, click here:
https://brainly.com/question/31023478
#SPJ11
Related Questions
Given a 10-bit Binary Code determine the user or human input if bits in the 1st and 4th positions are on. 8. A user types the "Tilde - using QWERTY keyboard. Determine the machine language equivalent for the user input.
Answers
The machine language equivalent for the user input is 126.
1. The 10-bit binary code for the user input is 0100000111.
2. The 1st and 4th positions in the binary code are both on.
3. The machine language equivalent for the user input is 01111100.
1. The 10-bit binary code representation of the user input "Tilde" is 0100000111.
2. In binary, the positions are numbered from right to left, starting from 1. So, the 1st and 4th positions correspond to the bits in the binary code.
3. Both the 1st and 4th bits are on (1), indicating that the "Tilde" key was pressed.
4. The machine language equivalent for the user input "Tilde" is represented by the binary code 01111100. Machine language instructions vary depending on the specific system architecture and instruction set being used.
Learn more about binary code here:
https://brainly.com/question/29792509
#SPJ11
Create a function called biggestNum that returns the largest number in an array of integers. The function is passed only one parameter, an array. In main, ask the user the input eight integers. Each integer should be added to an array called nums. Then, call the function and output the largest number in the array.

Answers
This is for Python
def biggestNum():
array = []
for i in range(8):
number = int(input('Enter number: '))
array.append(number)
return max(array)
print(biggestNum())
you have a variable n with a non-negative value and need to write a loop that will keep print n blank lines what loop construct should you use
Answers
Answer:
write down same applications of AI in agriculture,health,education, and business
What is a WYSIWG program
Answers
Answer: WYSIWYG (pronounced wiz-ee-wig) is a type of editing software that allows users to see and edit content in a form that appears as it would when displayed on an interface, webpage, slide presentation or printed document.
Explanation:
Which of the software below is best suited for storing records of books in a library?
A.Control program
B. Measuring program
C. Word processor 3
D. Search engine
E.Database
Answers
Answer:
E.Database
Explanation:
You pull on a torque Wrench of 0.5 m long with 30 N.
What is the torque at the end of the torque wrench?
Nm
check
Answers
Answer:
The torque is 15 N·m
Explanation:
The given parameters are;
The length of the torque wrench = 0.5 m
The force applied on the torque wrench = 30 N
The torque at the end of the torque wrench is equal to the applied force multiplied by the perpendicular distance from the point of application of the force to the end of the torque wrench
Therefore;
Torque = The force applied on the torque wrench handle × The length of the torque wrench
Torque = 30 N × 0.5 m = 15 N·m
Torque = 15 N·m.
Question 16 2.5 pts When is it OK to use the less-precise "fast_normalize()" call instead of the full-precision "normalize()" call? Always Never When using it for scientific computing O When using it for computer graphics
Answers
It is not appropriate to use the less-precise "fast_ normalize()" call instead of the full-precision "normalize()" call in any scenario. The purpose of the "normalize()" function is to ensure accurate and precise normalization of data, which is essential in various fields such as scientific computing and computer graphics.
The "normalize()" function typically calculates the precise normalization of a given set of data, which involves dividing each data point by the magnitude or sum of all data points. This process ensures that the resulting normalized values maintain their original proportions and accurately represent the data.
On the other hand, the "fast_normalize()" function suggests a less-precise or approximate normalization approach. While it may provide faster computation, it sacrifices accuracy and reliability, which are crucial in many applications.
In scientific computing, accurate results are of utmost importance. Researchers and scientists rely on precise calculations to obtain reliable outcomes and draw meaningful conclusions. Using a less-precise normalization method can introduce errors and inaccuracies in the data, leading to flawed analyses and potentially misleading results.
Similarly, in computer graphics, maintaining precision is vital for generating realistic and visually appealing graphics. Any compromise on accuracy can result in distorted images or incorrect rendering, compromising the quality of the graphics.
Therefore, it is never acceptable to use the less-precise "fast_ normalize()" call instead of the full-precision "normalize()" call. It is essential to prioritize accuracy and reliability in scientific computing, computer graphics, and any other field where precise normalization is required.
for more questions on computer
https://brainly.com/question/24540334
#SPJ8
var1 = 1
var2 = 2
var3 = "3"
print(var1 + var2 + var3)
Answers
Explanation:
omg it's Python, I don't like it
I would say the answer is 33 or 6
a list of approved digital certificates it's called a
Answers
A list of approved digital certificates is called a Certificate Authority (CA) list. This is a critical component of the public key infrastructure (PKI) system that ensures secure communication over the internet. The CA list includes the names of trusted certificate authorities that have been verified and authorized to issue digital certificates. These certificates are used to authenticate the identity of websites, individuals, and organizations in online transactions. The CA list is constantly updated to ensure that only trustworthy CAs are included, and that certificates issued by these CAs are valid and reliable. In conclusion, the CA list plays a vital role in maintaining the security and integrity of online communication.
This list contains the trusted root certificates issued by various Certificate Authorities. The CA Trust List ensures secure and trusted connections between users and websites, as it verifies the authenticity of a website's digital certificate. In conclusion, maintaining an up-to-date CA Trust List is crucial for ensuring online security and establishing trust between users and websites.
To know more about Certificate Authority visit:
https://brainly.com/question/31306785
#SPJ11
outline the steps involved in changing the colour of a theme
Answers
Answer:
Right click on the desktop and click on personalize option and then click on window color. After that window color and appearance window appears. select a color scheme you want. Go to Appearance and personalization, click on theme and select any theme from the list and click on ok.
which step comes first when solving a problem?
A.organizing the data
B.forming a hypothesis
C.collecting data
D.ask a question
Answers
Answer:
D
Explanation:
The steps are as follows:
D, B, C, A.
Hope that helps
Answer:
D
Explanation:
first you need to understand the problem before you can solve it.
Please help urgently i will give 61 points

Answers
Web browsers can be used to access the internet.
What is a short history of web browsers?When we talk of the web browsers we are talking about the kind of applications that we can use to access pages on the web. Today there are so many of such applications that we can be able to use search for pages on the web.
The initial attempts at web browsers were the hyperlinked applications that were produced by Tim Berners-Lee during the mid and late 1980s and 1990.
Today, we have a lot of the web browsers in use like the Chrome, Safari, Internet Explorer (IE), Firefox, and Opera.
Learn more about web browsers:https://brainly.com/question/9776568
#SPJ1
Which term describes a protocol to manage a network, able to configure a network, monitor activity, and control devices?
Post Office Protocol version 3 (POP 3)
Simple Mail Transfer Protocol (SMTP)
Internet Message Access Protocol (IMAP)
Simple Network Management Protocol (SNMP)
Answers
Answer:
Simple Network Management Protocol (SNMP)
Explanation:
Answer:
SNMP
Explanation:
vote brainliest please.
A collection of data stored on a nonvolatile device in a computer system is ____________.
Answers
A collection of data stored on a nonvolatile device in a computer system is known as "persistent data."
Persistent data refers to information that remains stored even when the computer system is powered off or restarted. It is typically stored on nonvolatile storage devices such as hard disk drives, solid-state drives, or other external storage media. Unlike volatile data, which is stored in temporary memory and is lost when the system is turned off, persistent data is retained for long-term storage and future retrieval.
Persistent data plays a crucial role in computer systems as it allows for the preservation of important information, such as user files, databases, operating system configurations, and application data. It provides the ability to store and retrieve data over an extended period, enabling users to access their files and applications consistently.
Learn more about storage devices here:
https://brainly.com/question/31936113
#SPJ11
anna created a 3-d clustered column pivotchart and wants to apply a gradient fill color to the back wall of the chart. which buttons will she choose after selecting the chart element and clicking the format tab?
Answers
Anna will choose "Format Selection," "Fill & Line," and "Gradient Fill" buttons on the Format tab.
How can Anna apply a gradient fill color to the back wall of her 3-D clustered column pivot chart?When Anna wants to apply a gradient fill color to the back wall of her 3-D clustered column pivot chart, she needs to follow a few steps. Firstly, after selecting the chart element, she should click on the "Format" tab. Then, she needs to locate and click the "Format Selection" button, which will open a side panel with various formatting options.
In this side panel, she should look for the "Fill & Line" button and click on it. Finally, within the "Fill & Line" options, she should choose the "Gradient Fill" option to access a range of gradient fill colors. By selecting her desired gradient fill color, Anna can enhance the visual appeal of the back wall of her chart.
Learn more about pivot chart
brainly.com/question/30205071
#SPJ11
scroll down to the flexconnect portion of the page. click to enable flexconnect local switching and flexconnect local auth. packet tracers
Answers
FlexConnect is a feature that allows local switching of data packets at remote sites. It provides flexibility and scalability for wireless LANs (WLANs) by allowing remote sites to connect directly to the main network while reducing traffic on the main network.
The FlexConnect feature is enabled by default on many Cisco access points. To enable it, follow these steps:Step 1: Scroll down to the FlexConnect portion of the page.Step 2: Click to enable FlexConnect local switching and FlexConnect local authentication.
Step 3: Click on the Packet Tracer button to simulate the configuration of the access point with FlexConnect enabled.Step 4: Use the Packet Tracer tool to test your configuration and ensure that it works as expected. The tool will generate traffic between the access point and the main network to confirm that the configuration is correct. It will also verify that the FlexConnect feature is working properly. The FlexConnect feature is a powerful tool that can be used to improve the performance and reliability of WLANs.
To know more about data visit:
https://brainly.com/question/29117029
#SPJ11
i) Convert 8GB to bits. Give the expression.
Answers
Answer:
64 billion
Explanation:
1gb = 1 billion bytes
so 8gb = 8 billion bytes
then
1 byte= 8 bits
so 8 billion bytes = 8 × 8 billion bits, 64 billion bits
we started to develop our singlylinkedlist collection class. the most recent version would be the one we came up with in module 9 demo 3. use this code to implement a stack ( linkedstack.java ) that will use our own collection class singlylinkedlist.java to store elements. see the uml of our singlylinkedlist collection class and the interface it implements. the singlylinkedlist is the collection class that stores and organizes objects.
Answers
To implement a stack, we can also use a linked list rather than an array. Memory is allocated dynamically using linked lists.
However, the time complexity for all three operations—push, pop, and peek—is the same in both scenarios. The nodes in a linked list implementation of a stack are kept apart from one another in memory.
Javac compilation LinkedStack.java
Java LinkedStack execution with input.txt
StdIn.java and StdOut.java are dependencies.
a linked list is used to implement a generic stack. The type of each stack element is Item.
To be or not to - be - that is the question in more tobe.txt
To be not that or be, %java LinkedStack (2 left on stack)
Learn more about operation here-
https://brainly.com/question/28335468
#SPJ4
According to the video, what are common tasks performed by Tour Guides? Check all that apply.
leading trips
maintaining equipment
shepherding tourists and luggage
socializing
purchasing tickets for flights
selling equipment
setting up meals
teaching first aid
Answers
Common tasks of the tour guide.
As per the question, the video shows us the tour guide n the ways he handles the tasks. The tour guide can be seen using making techniques such as providing tips, giving information, socializing with people, and setting up meals and other arrangements.
Thus the answer is leading trips, maintaining equipment, shepherding the tourists and luggage, and socializing, setting up meals.
Thus the duty of the tour guide its provide the latest information and provide the cratered services to the clients. The services like hotel, travel and maintains of the equipment's is essential for them. Thus the option 1, 2, 3,4 and 7 are correct.Learn more about the according to the video.
brainly.com/question/19175630.
Answer: 1 2 3 4 7
Explanation:
what the other guy said
meaning and explanation of fortran
Answers
Answer:
is a general-purpose, compiled imperative programming language that is especially suited to numeric computation and scientific computing.
Explanation:
Fortran, as derived from Formula Translating System, is a general-purpose, imperative programming language. It is used for numeric and scientific computing. Fortran was originally developed by IBM in the 1950s for scientific and engineering applications.
Describe how to check which pages users are authorized to access
in a cloud service
Answers
The standard procedure for verifying the authorized pages that cloud service users can access involves the following steps below
What is the cloud serviceBefore allowing access to any cloud service pages, it is important to verify the authentication of users. There are different ways to accomplish this, which include utilizing diverse means of authentication like delivering a username and password, implementing multi-factor authentication (MFA), or connecting with third-party identity providers.
Implementing RBAC in your cloud service will allow you to define roles and their associated permissions.
Learn more about cloud service from
https://brainly.com/question/19057393
#SPJ4
7.2 code practice edhesive. I need help!!
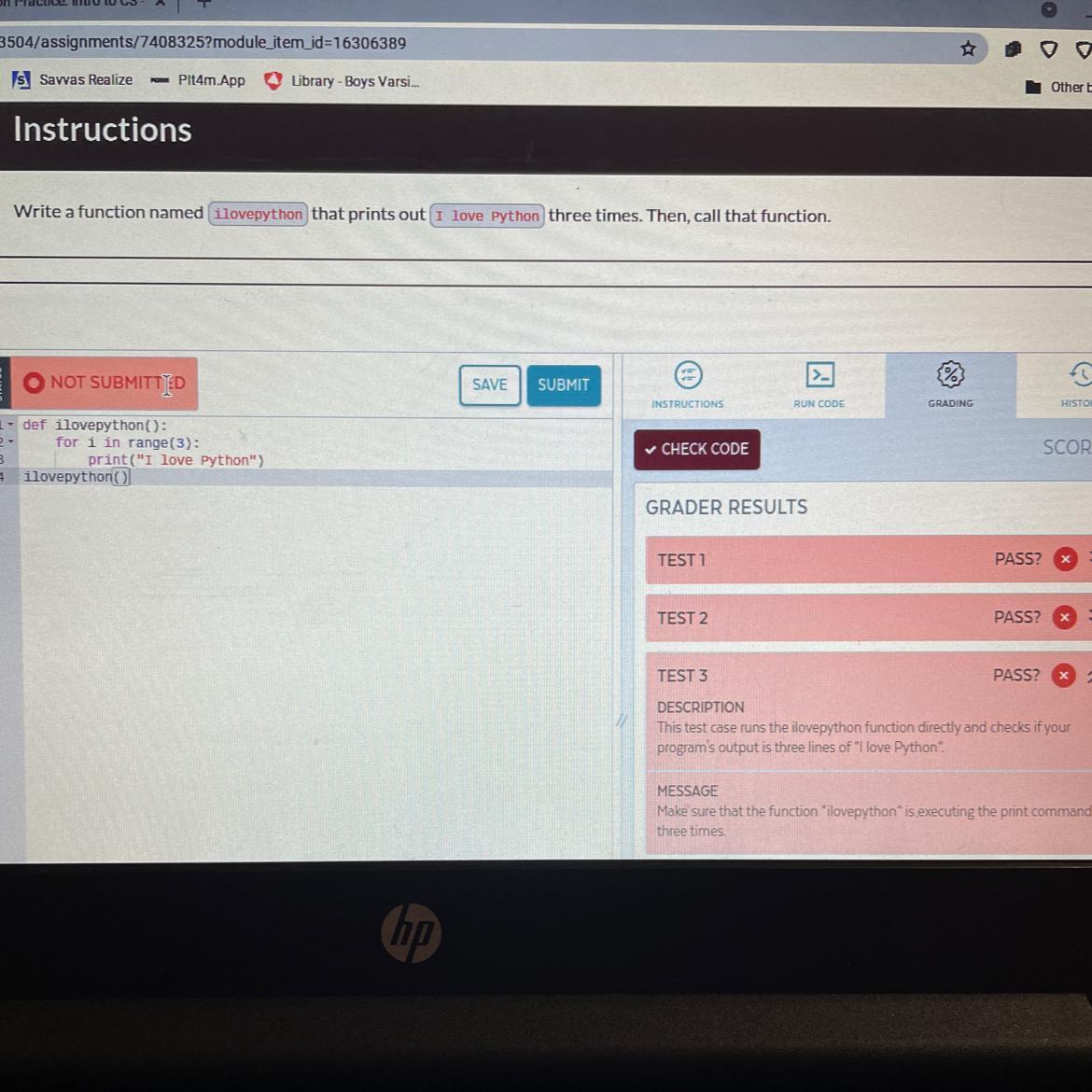
Answers
Answer:
It already looks right so I don't know why it's not working but try it this way?
Explanation:
def ilovepython():
for i in range(1, 4):
print("I love Python")
ilovepython()
Which of the following would be considered a central idea for a mind map?
moons
solar system
planets
stars
Answers
Answer:
solar syetem
Explanation:
Answer:
B
Explanation:
write a QBASIC that ask length,breadth and height of room and calculate its area and volume.create a user-defined function to calculate area and sub programe to calculate volume
Answers
Answer:
REM Program to calculate the area and volume of a room
DIM length, breadth, height, area, volume AS SINGLE
INPUT "Enter the length of the room: ", length
INPUT "Enter the breadth of the room: ", breadth
INPUT "Enter the height of the room: ", height
REM Call user-defined function to calculate area
area = calculateArea(length, breadth)
REM Call sub-program to calculate volume
CALL calculateVolume(length, breadth, height, volume)
PRINT "The area of the room is "; area; " square units."
PRINT "The volume of the room is "; volume; " cubic units."
END
REM User-defined function to calculate area
FUNCTION calculateArea(l, b)
calculateArea = l * b
END FUNCTION
REM Sub-program to calculate volume
SUB calculateVolume(l, b, h, v)
v = l * b * h
END SUB
Explanation:
The program first asks the user to enter the length, breadth, and height of the room. It then calls a user-defined function calculateArea to calculate the area of the room, which is stored in the area variable. The program then calls a sub-program calculateVolume to calculate the volume of the room, which is stored in the volume variable. Finally, the program prints the values of area and volume.
Note that the user-defined function calculateArea takes two parameters l and b which represent the length and breadth of the room respectively, and returns the product of l and b, which is the area of the room. The sub-program calculateVolume takes three parameters l, b, and h which represent the length, breadth, and height of the room respectively, and calculates the product of l, b, and h, which is the volume of the room. The volume is stored in the variable v, which is passed as a parameter to the sub-program.
what is output? dict1 = {1: 'hi', 2: 'bye'} dict2 = {2: 'yes'} dict1.update(dict2) dict3 = {3: 'no'} dict1.update(dict3) print(dict1)
Answers
The output of the code will be :
{1: 'hi', 2: 'yes', 3: 'no'}
In the given Python code, the output will be a dictionary that includes the key-value pairs of all three dictionaries. The code can be explained step-by-step:
Firstly, two dictionaries, dict1 and dict2, are defined. The keys of dict1 are 1 and 2, and their values are 'hi' and 'bye' respectively. The key of dict2 is 2, and its value is 'yes'.
{1: 'hi', 2: 'bye'}{2: 'yes'}
Then, the dict2 dictionary is merged with dict1 using the update() method. The key-value pairs of dict2 are added to dict1. Since both dicts have the same key 2, the value in dict1 is overwritten with the value from dict2. Hence, the updated dictionary is:
{1: 'hi', 2: 'yes'}{2: 'yes'}
Then, a third dictionary, dict3, is defined with the key 3 and value 'no'.
{3: 'no'}
Finally, dict3 is merged with dict1 using the update() method. The key-value pairs of dict3 are added to dict1. Since dict1 does not have the key 3, the key-value pair from dict3 is simply added to dict1. The final dictionary after the update is:
{1: 'hi', 2: 'yes', 3: 'no'}
Therefore, the output of the code will be:
{1: 'hi', 2: 'yes', 3: 'no'}
To learn more about Python code visit : https://brainly.com/question/26497128
#SPJ11
the portion of the application that allows you to control and to interact with the program. true or false?
Answers
Statement "The portion of the application that allows you to control and to interact with the program" is false because the true is user interface.
The portion of an operating system, software, or device that enables a user to enter and receive information is referred to as the user interface (UI). Text is shown on a text-based user interface (see the image to the left), and instructions are often entered using a keyboard on a command line. Graphical User Interface is the right response. A human may communicate with a computer using symbols, icons, visual metaphors, and pointing devices thanks to an operating system.
Learn more about operating system: https://brainly.com/question/22811693
#SPJ4
Which method will return an empty string when it has attempted to read beyond the end of a file? a. read b. getline c. input d. readline d . readline
Answers
It is to be noted that the method will return an empty string when it has attempted to read beyond the end of a file is: "readline" (Option D).
What is an empty string?An empty string is a zero-length string instance, but a null string has no value at all. The character "" represents an empty string. It consists of a zero-character sequence. Null represents a null string.
The empty string is a specific instance in which the sequence has length zero and so contains no symbols. There is only one empty string since two strings are only distinct if their lengths or symbol sequences differ.
Learn more about files:
https://brainly.com/question/14338673
#SPJ1
You are able to add Sheets to your workbook by pressing the + button by the sheet tabs.
O True
O False
Answers
Answer:
True
Explanation:
review the saleitem relation below where itemnumber plus ordernumber is the primary key. what type of primary key does this relation have?
Answers
The relationship "saleitem" has a compound primary key, which is a type of primary key that consists of two or more columns. In this case, the composite primary key consists of an "itemnumber" field and an "ordernumber" column. A composite primary key ensures that each combination of values in the "itemnumber" and "ordernumber" fields is unique in the relationship. This helps enforce data integrity and prevent duplicates or inconsistencies in the database.
A database is an organized collection of data that is stored and accessed electronically. It is designed to support efficient and organized data storage, retrieval, modification and deletion. Databases are used to store and manage large amounts of information for various applications, such as websites, software applications, and business operations. They typically use a structured query language (SQL) to interact with the data, allowing users to easily search, sort, filter, and manipulate data. There are several types of databases, including relational databases, NoSQL databases, graph databases, and more, each with its own unique features and uses.
You can learn more about databases here brainly.com/question/6447559
#SPJ4
for Jenny's personal computer?
id videos. Which operating
system would be appropriate Jenny's needs to buy a computer to create word documents, make presentations, listen to music, and watch movies and videos.
OA. UNIX
O B. Linux
O C. Microsoft Windows
O D. MS-DOS
Answers
Answer: C
Explanation: Microsoft Windows would be the most viable option here because UNIX and Linux are used for server-side applications, and MS-DOS is an old operating system which is not supported anymore. There is also the Microsoft 365 suite on Microsoft Windows, which can allow Jenny to make presentations using powerpoint, and edit videos.