Cron only allows the user to create one time tasks. group of answer choices
a. true
b. false
Answers
The given statement that is Cron only allows the user to create one time tasks is true.
On Unix-like operating systems, a job scheduler is the command-line tool cron. Cron is a tool used by those who set up and maintain software systems to plan tasks, sometimes referred to as cron jobs, to run on a regular basis at predetermined times, dates, or intervals.
The term Cron, a clock daemon, comes from the Greek word Chronos, which means time. It allows users to programmatically execute instructions, scripts (a collection of commands), or programmes at predetermined intervals.
A persistent process that runs instructions at predetermined times and dates is the cron daemon. This can be used to schedule tasks that are either one-time occurrences or ongoing duties. Use the at or batch command with cron to schedule one-time tasks.
Learn more about cron:
https://brainly.com/question/28283739
#SPJ4
Related Questions
1 of 10 What information do banking institutions use to help detect fraudulent transactions? Historical transaction data 0 Internet search engine statistics Local business' sales forecasts National financial trends Submit Post-Assessment a 2 of 10 What layer of a decision tree tells you how a series of connected factors lead to a final outcome? The bottom layer Any layer with a threshold value over 5% Any layer with a threshold value over 15% The top layer Post-Assessment 3 of 10 Which is a tool can be used to automate the fraud detection process? O regression analysis confusion matrix logistic regression decision tree Submit Post-Assessment of 10 Which of these saves an institution time? Decision trees Fraud detection Confusion matrices Automated processes 9 Post-Assessment 5 of 10 Teaching an algorithm how to make decisions is known as training the model a decision tree identity fraud a confusion matrix Post-Assessment 6 of 10 Which of the following is not an example of fraud? Odata collection Odata visualization data breach c Both A and B 9 0 Post-Assessment 7 of 10 The value that decides whether something falls into one category or another is called a confusion matrix regression analysis logistic regression threshold ht Post-Assessment Bor 10 How is a confusion matrix used? To automate decision-making processes To verify the accuracy of a traud detection model Asa checklist to determine it a purchase is fraudulent As a checklist to determine a purchase is fraudulent g Post-Assessment 9 of 10 When should you use a confusion matrix? When you want to determine the value you should use as a threshold for your model When you want to automate a promess When you want to see if predictions made using logistic regression match actual outcomes When you want to create a decision tree Subm g Post-Assessment 10 of 10 What tool do data scientists use to examine the connections between variables? fraud detection decision trees confusion matrices O regression analysis Subs
Answers
1. A option is correct. historical transaction data
2. Any layer with threshold value above 15 % is the correct option
Answer:3. Decision tree
Answer:4. Automated process
5. Training the modle A option is the correct one
6. Both A and B
7. Threshold DD option is the correct option
8. As a checklist to determine if a purchase is fraduklent
9. C option is the correct option
10. Regression analyssis
What is the Intention of a Confusion Matrix in Machine Learning?
The goal of a confusion matrix in Machine Learning is to assess the competency of a classification model. It is a table used to gauge the correctness of the projections made by the model by contrasting the forecasted values against actual figures.
It demonstrates the amount of accurate positives, true negatives, false positives, and incorrect negatives, which are after then utilized to estimate various metrics like accuracy, recall, and the F1 score.
Learn more about banking on
https://brainly.com/question/25664180
#SPJ1
The deliberate misuse of computers and networks, _____ use malicious code to modify the normal operations of a computer or network.
Answers
Answer:
Virusus
Explanation:
-
Hope that helps
which type of hazzard are those substances which threathen you physical safety ?
Answers
Answer:
98o
Explanation:
How mutex locks solve critical section problem?
Answers
Mutex locks help solve the critical section problem by providing a synchronization mechanism that ensures mutual exclusion, thus preventing multiple threads from accessing shared resources concurrently. Here's a step-by-step explanation:
1. Mutual exclusion (mutex) locks are a type of synchronization primitive used in multithreading environments.
2. A critical section is a part of code that accesses shared resources and must not be executed concurrently by multiple threads to avoid conflicts and data corruption.
3. When a thread wants to enter the critical section, it requests a mutex lock.
4. If the mutex lock is available, the thread acquires the lock and proceeds to execute the critical section code.
5. If the mutex lock is already held by another thread, the requesting thread will block (wait) until the lock is released by the owner.
6. Once the thread holding the mutex lock finishes executing the critical section, it releases the lock, allowing another waiting thread to acquire it.
7. By following this process, only one thread at a time can hold the mutex lock and access the critical section, thus ensuring mutual exclusion and preventing concurrent access to shared resources.
This mechanism helps to solve the critical section problem by providing controlled access to shared resources, ensuring data integrity, and preventing race conditions in multithreaded applications.
Learn more about Mutex Lock from : brainly.com/question/29843048
#SPJ11
HELP
When differentiating data, the WHAT of the data is:
Answers
Answer:
a source and a target.
Explanation:
In computer science and information theory, data differencing or differential compression is producing a technical description of the difference between two sets of data – a source and a target.
which of the following is not a deadlock prevention method? group of answer choices deadlock detection and recovery resource ordering eliminate hold and wait eliminate mutual exclusion
Answers
"Eliminate mutual exclusion" is not a deadlock prevention method.
Deadlock prevention is a technique used in operating systems to avoid situations where two or more processes are blocked waiting for each other to release resources, resulting in a system deadlock. There are several methods for preventing deadlocks, such as deadlock detection and recovery, resource ordering, eliminate hold and wait, and others.
"Eliminate mutual exclusion" is not a deadlock prevention method because mutual exclusion is a fundamental principle in preventing concurrent access to shared resources by multiple processes. Without mutual exclusion, multiple processes can access the same resource simultaneously, leading to inconsistencies or errors. Therefore, eliminating mutual exclusion is not a viable solution for preventing deadlocks.
In contrast, other deadlock prevention methods such as resource ordering, eliminate hold and wait, and deadlock detection and recovery focus on ensuring that resources are allocated in a manner that prevents deadlocks from occurring. These methods aim to prevent deadlocks by either avoiding the conditions that lead to deadlocks or by detecting and recovering from deadlocks in a timely manner.
Learn more about deadlock detection here:
https://brainly.com/question/29839797
#SPJ11
What invention of the ancient world provided power that did not depend on human or animal labor?
Answers
Answer:
water currents? like the water mill
Explanation:
Water mills can be used for such purposes as grinding flour or agricultural produce, cutting up materials such as pulp or timber, or metal shaping. Traditional water mills are made from a wheel or turbine with wooden blades that turn when water runs through.
if you have water flowing through your property, you might consider building a small hydropower system to generate electricity. Microhydropower systems usually generate up to 100 kilowatts of electricity.
brad, a student in his final semester, is planning to start his job search soon. in order to find the right job, brad should start thinking like a networker. his first step in building a network should be to start with
Answers
His classmates should be the first people he contacts while establishing a network.
How do networks work?
Two or more computers connected together to share resources (such printers and CDs), exchange files, or enable electronic communications make up a network. A network's connections to its computers can be made by cables, phone lines, radio signals, satellites, or infrared laser beams. Computers, servers, mainframes, network equipment, peripherals, and other linked devices form a network that enables data sharing. The Net, which links millions around the world, is an illustration of a network
To know more about Network
https://brainly.com/question/13102717
#SPJ4
Jesse purchases a new smartphone and is immediately able to use it to send a photo over the Internet to a friend who lives in a different country. Which of the following is NOT necessary to make this possible?
a. Both devices are using the same shared and open protocols
b. A single direct connection is established between any two devices connected to the Internet
c. The data of the image is routed through a sequence of directly connected devices before arriving at its destination.
d. Both devices are directly connected to at least one part of the Internet
Answers
Answer:b
Explanation:
In other to send files from one device to another, the devices must be connected in one way or the other.
(b) A single direct connection between the devices is not necessary.
Of the given options, option B is not a necessary requirement for Jesse to transfer images to his friend.
The reason is that:
When a single direct connection is used to connect devices, it means that:
The devices are at a close proximity (e.g. devices in the same room)The devices need a cable for their connection to be successful.From the question, we understand that his friend is in another country.
This means that it is practically impossible for their devices to be at a close proximity and by extension they cannot use a cable to connect their devices (i.e. phones).
However, other options are true because:
Their connection must be universal i.e. (a) shared and open protocolThey must be connected through the internet i.e. (c) and (d)Hence, option (b) is not necessary.
Read more about device connections at:
https://brainly.com/question/5059138
Write a program that will input a list of test scores in from the keyboard. When the user enters -1, print the average.
What do you need to be careful about when using -1 to stop a loop?
Enter the Scores:
45
100
-1
The average is: 72.5
Answers
print("Enter the Scores:")
total = []
while True:
num = int(input())
if num == -1:
break
total.append(num)
print("The average is:",(sum(total)/len(total)))
I wrote my code in python 3.8. Also, you have to be careful about adding -1 to the total. You don't want to count -1 in the average.
An employee sets up Apache HTTP Server. He types 127.0.0.1 in the browser to check that the content is there. What is the next step in the setup process?
Answers
Answer:
Set up DNS so the server can be accessed through the Internet
Explanation:
If an employee establishes the HTTP server for Apache. In the browser, he types 127.0.0.1 to verify whether the content is visible or not
So by considering this, the next step in the setup process is to establish the DNS as after that, employees will need to provide the server name to the IP address, i.e. where the server exists on the internet. In addition, to do so, the server name must be in DNS.
Hence, the first option is correct
Your question is lacking the necessary answer options, so I will be adding them here:
A. Set up DNS so the server can be accessed through the Internet.
B. Install CUPS.
C. Assign a static IP address.
D. Nothing. The web server is good to go.
So, given your question, what is the next step in the setup process when setting up an Apache HTTP Server, the best option to answer it would be: A. Set up DNS so the server can be accessed through the Internet.
A server can be defined as a specialized computer system that is designed and configured to provide specific services for its end users (clients) on a request basis. A typical example of a server is a web server.
A web server is a type of computer that run websites and distribute web pages as they are being requested over the Internet by end users (clients).
Basically, when an end user (client) request for a website by adding or typing the uniform resource locator (URL) on the address bar of a web browser; a request is sent to the Internet to view the corresponding web pages (website) associated with that particular address (domain name).
An Apache HTTP Server is a freely-available and open source web server software designed and developed to avail end users the ability to deploy their websites on the world wide web (WWW) or Internet.
In this scenario, an employee sets up an Apache HTTP Server and types 127.0.0.1 in the web browser to check that the content is there. Thus, the next step in the setup process would be to set up a domain name system (DNS) so the server can be accessed by its users through the Internet.
In conclusion, the employee should set up a domain name system (DNS) in order to make the Apache HTTP Server accessible to end users through the Internet.
Find more information here: https://brainly.com/question/19341088
determining the context of a text or media piece helps ypu:
Answers
unix command to check if file exists in a directory
Answers
To check if a file exists in a directory, the Unix command used is "ls."
The ls command is used to list the contents of a directory. This command provides a list of files and directories in a folder on the Unix operating system. There are different ways to check if a file exists in a directory in Unix. One way is to use the ls command to list all the files and directories in a directory. To check if a file exists in the directory, you can use the following command:
ls /directory_path/file_name
This command will check if the file "file_name" exists in the "directory_path" directory. If the file exists, it will be listed in the output of the command. If the file does not exist, there will be no output.
To check if a file exists in the current directory, use the following command: ls file_name
This command will check if the file "file_name" exists in the current directory. If the file exists, it will be listed in the output of the command. If the file does not exist, there will be no output.
Learn more about UNIX Command:
https://brainly.com/question/33326550
#SPJ11
I know how to do this but I'm struggling to make it appear on the screen am I doing it right? If I am please tell me that if not please tell me and explain to me how to do it also help me to understand by explaining it to me what I'm doing wrong so that in the future I will never ever make this mistake again.
Answers
Answer:
maybe you should try to copy the image then paste it, or save it to your files then go into your files and add it
Explanation:
11.9 LAB: Vending machine
Given two integers as user inputs that represent the number of drinks to buy and the number of bottles to restock, create a VendingMachine object that performs the following operations:
Purchases input number of drinks
Restocks input number of bottles
Reports inventory
The VendingMachine is found in VendingMachine.java. A VendingMachine's initial inventory is 20 drinks.
Ex: If the input is:
5 2
the output is:
Inventory: 17 bottles
_______________________________________________________________
LabProgram.java
import java.util.Scanner;
public class LabProgram {
public static void main(String[] args) {
Scanner scnr = new Scanner(System.in);
/* Type your code here. */
}
}
______________________________________
VendingMachine.java
// simulates a simple vending machine with operations to purchase drinks and check inventory.
public class VendingMachine {
// number of bottle in stock
private int bottles;
// initial inventory is 20
public VendingMachine(){
bottles = 20;
}
public void purchase(int amount){
bottles = bottles - amount;
}
public int getInventory(){
return bottles;
}
public void restock(int amount){
bottles = bottles + amount;
}
public void report(){
System.out.println("Inventory: " + bottles + " bottles");
}
}
Answers
You can use the Scanner class to read the user inputs for the number of drinks and the number of bottles to restock. Then, you can create a VendingMachine object, call its purchase() and restock() methods with the user inputs, and finally call its report() method to display the current inventory.
Here's the updated code for LabProgram.java:import java.util.Scanner;
public class LabProgram {
public static void main(String[] args) {
Scanner scnr = new Scanner(System.in);
// Read user inputs
System.out.print("Enter number of drinks to buy: ");
int numDrinks = scnr.nextInt();
System.out.print("Enter number of bottles to restock: ");
int numBottles = scnr.nextInt();
// Create vending machine object
VendingMachine vm = new VendingMachine();
// Purchase drinks and restock bottles
vm.purchase(numDrinks);
vm.restock(numBottles);
// Report current inventory
vm.report();
}
}
When the program is run and the user enters "5 2" as input, the output will be:
Enter number of drinks to buy: 5
Enter number of bottles to restock: 2
Inventory: 17 bottles
Read more about java here:
https://brainly.com/question/26789430
#SPJ1
what is created when a packet is encapsulated with additional headers to allow an encrypted packet to be correctly routed by internet devices? a.efs b.frame c.tunnel d.access point
Answers
In order for an encrypted packet to be properly routed by internet devices, a tunnel is constructed when a packet is encapsulated with extra headers.
What results from adding extra headers to a packet in order to allow an encrypted packet to be correctly routed by Internet devices?What results from adding extra headers to a packet in order to allow an encrypted packet to be correctly routed by Internet devices.
According to the majority of specialists, what kind of malware is so challenging to find and eliminate?Since they can hide their presence inside an infected system, rootkits are difficult to find. To remotely access, control, and steal data from your computer, hackers utilize rootkit malware.
To know more about encrypted packet visit:-
https://brainly.com/question/29562357
#SPJ1
You want to add together the contents of three cells in your spreadsheet: B1,
C3, and D5. Which three formulas could you use?
A. SUM(B1:C3:D5)
B. B1+C3+D5
C. B1*C3*D5
D. SUM(B1+C3+D5)

Answers
Answer:
B. B1+C3+D5
D. SUM(B1+C3+D5)
E. =B1+C3+D5
Explanation:
what is a technology that exists inside another device called
Answers
Answer: embedded technology
Explanation: just took the test
Answer:
AExplanation:
Embedded technology
PLEASE HELP WITH JAVA CODING THIS IS ANOTHER ASSIGNMENT THAT HAS TO BE DONE.
DETAILS WILL BOTH BE PASTED HERE AND ON A PICTURE BECAUSE IT COULDN'T BE CAPTURED ALL IN ONE PICTURE
Instructions:
//Name:
//Period:
import java.util.*;
public class ChangeMakerAPP
{
public static void main(String[] args)
{
Scanner console = new Scanner(System.in);
}
}
A method is, essentially, a named block of code. We run a method by calling it (typing in its name and supplying it the information it needs to run - the method's parameters). Methods are written OUTSIDE OF OTHER METHODS BUT INSIDE THE CLASS, and have the following parts:
public static String sampleMethod(int a)
{
//something
}
public static
access modifier (for now, this will always be public static).
String
the return type. The type of data this method will return (to where it's called) when it's finished running.
sampleMethod
method name. Naming convention is the same as variables.
int a
method's parameter. Placeholder variable for the information passed in to the method.

Answers
The makeChange method is one that tends to adopt two parameters and as such the code that shows it all in terms of use of arrays to monitor all the denominations as well as their counts is given below
What is the algorithm about?The code that is given below is one that will take input from the user based on the priced amount paid as well as the cost of the bill.
The makeChange method is one that tends to calculate as well as print the change breakdown.
Therefore, the given implementation is one that does assumes that the input values are known to be valid and that the amount paid is one that is greater than or what we call equal to the amount of the cost of the bill.
Learn more about algorithm from
https://brainly.com/question/24953880
#SPJ1
See text below
Write a method public static void makeChange(double paid, double cost) that will "makhange". given the amount of the bill (cost) and the amount the customer handed the cashier (pa
Your method should calculate the number of bills and coins that should be returned to the customer. Use the following denominations:
⚫ Bills: $20, $10, $5, $1 //assume we won't be making change with $100s and $50s ⚫ Coins: 25c, 10c, 5c, 1c
A greedy algorithm makes a locally optimal choice without considering the globally optimal solution. For standard US coins, the greedy algorithm will return the ideal amount of change (fewest number of coins).
Think about what would happen if we had coin denominations of 1, 9, 10 (instead of 1, 5, 10) and attempted to make change for 18 cents.
Use a greedy algorithm (subtract the largest denomination possible each time from the amount of change to make, until done). To keep the change-making procedure precise, use type casting (e.g. (int) 2.56) to convert the amount of change to make to an integer. Your method should produce an output like the following, for makeChange(20.0, 13.44):
$20: 0 $10: 0
$5: 1
$1: 1
25c: 2
10c: 0
5c: 1
1c:
1
A better version of this method will utilize arrays.


Question 3 of 10
A business letter is not written:
Answers
Answer:
yes. business letter better use statistic. or audit.
FREE BRAINLIEST!!!
When recording a macro, the cursor will look like a _____ to indicate it is recording. A.microphone
B. Arrow
C. CD
D. cassette tape
Answers
Answer:
B
Explanation:
Answer:
When recording a macro, the cursor will look like a cassette tape to indicate it is recording. This answer has been confirmed as correct and helpful.
Explanation:
the correct answer is D
new technology, like the latest cell phones and hdtv, would probably be costed using the:
Answers
New technologies like the latest cell phones and HDTVs would most likely be costed using market-based pricing strategies.
Market-based pricing determines the price of a product based on market demand and competition. Companies assess factors such as production costs, competition, consumer preferences, and perceived value to set a price that maximizes profitability while remaining competitive in the market. For new technologies, pricing strategies often consider factors like research and development costs, production costs, brand positioning, and the perceived value of the product in the market. Additionally, introductory pricing or promotional pricing strategies may be used initially to stimulate demand and gain market share. Ultimately, market-based pricing allows companies to adjust prices based on market dynamics and customer willingness to pay for the latest technological innovations.
Learn more about technologies :
https://brainly.com/question/9171028
#SPJ11
ANYONE THERE!?!?
TO HELP ME.




Answers
Answer:
Penguin
Explanation:
the sprite is Penguin and it is going to say what you put into the answer spot
What are the steps for rearranging the layout of a form?
Answers
Answer:
I hope i help :)
Explanation:
Right-click the form in the Navigation Pane, and then click Design View. Hold down the SHIFT key and then click the controls that you want to move to the new control layout. Do one of the following: On the Arrange tab, in the Table group, click the layout type that you want for the new layout (Tabular or Stacked
Choose all items that are true about the two example of HTML shown on the right.
Example 1 will display differently than example 2 in a web browser.
They are styled differently, but will look the same in a web browser.
Example 2 is easier to analyze and repair.
The styling in example 2 is required by modern web browsers.
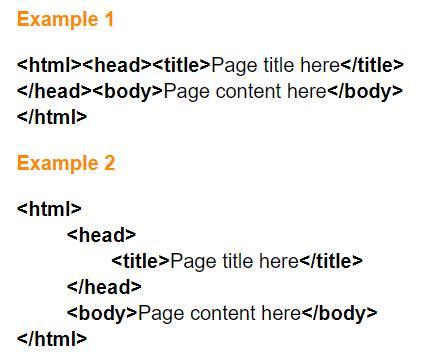
Answers
Answer:
2
Explanation:
Answer:
B and C
Explanation:
Confounding often defeats attempts to show that one variable causes changes in another variable. Confounding means that
Answers
Confounding often defeats attempts to show that one variable causes changes in another variable. Confounding means that extraneous factors or variables are present and can lead to incorrect conclusions being drawn about the relationship between the variables in question. In other words, the observed relationship between the two variables may not be a direct causal relationship, but rather one that is influenced by other variables.
Confounding refers to the presence of variables other than the ones being studied that can influence the outcome of the study. In research, confounding variables are important to identify and control for to ensure that the observed relationship between the independent variable and dependent variable is truly causal. Otherwise, there is a risk of making erroneous conclusions or assumptions about the relationship between the variables in question.In order to avoid confounding variables, researchers must take steps to control for them. One way to do this is to design a study that incorporates a control group, which is a group that is similar to the experimental group in every way except that it is not exposed to the independent variable being studied.
By comparing the results of the experimental group to those of the control group, researchers can determine if any differences observed between the groups are truly due to the independent variable and not to some other confounding variable that was not controlled for. Another way to control for confounding variables is to use statistical techniques to analyze the data. One such technique is regression analysis, which can be used to isolate the effect of the independent variable on the dependent variable while controlling for other variables that may be present. In conclusion, confounding variables are an important consideration in any research study, and researchers must take steps to control for them in order to draw accurate conclusions about the relationship between the variables being studied.
To know more about Confounding visit:-
https://brainly.com/question/14143697
#SPJ11
All the following are the basis of the World Wide Web except:
Web browser programs
Infrastructure
Web servers
HTML
Answers
Answer:
Web browser programs
Explanation:
Web broswer programs arent very important because they arent being used to maintain the servers or contail the contents of all the sites, they are only used by people to easily view the world wide web without using advanced commands in a terminal to view sites. all the other selections are very important when it comes to maintaining the entirety of the internet.
Answer:
web browser'
Explanation:
if the lookback window is seven days and a user sees an ad on day one, sees an ad again on day three, sees and clicks on an ad on day four, and converts on day ten, then which impression gets the conversion credit?
Answers
The conversion credit would be applied to the day four impression when the user clicked on the advertisement.
Ad - what is it?
The word "ad" is an abbreviation for "advertisement," which is a type of communication meant to influence viewers, readers, or listeners to take a particular action with regard to goods, concepts, or services. Advertisements can be found in a variety of media, including papers, magazines, television, radio, billboards, and online. They are often placed by marketers, corporations, and organizations. Reaching an audience is assured with advertisements. By creating an appealing ad, and paying enough to reach your target consumers, adverts can have an immediate influence on business. Among many other indicators, this impact may be seen in increased brand awareness or improved commerce.
To know more about Ad
https://brainly.com/question/3163475
#SPJ4
. Cloudy Corporation has provided the following cost data for last year when 50,000 units were produced and sold: All costs are variable except for $100,000 of manufacturing overhead and $100,000 of selling and administrative expense. If the selling price is $12 per unit, the net operating income from producing and selling 120,000 units would be: 17. Constance Company sells two products, as follows: Fixed expenses total $450,000 annually. The expected sales mix in units is 60% for Product Y and 40% for Product Z. How much is Constance Company's expected break-even sales in dollars?
Answers
Constance Company's expected break-even sales in dollars are $2,160,000.
1. Net operating income from producing and selling 120,000 units would be:Given data: Selling price per unit = $12Variable costs = $8 per unitFixed manufacturing overhead = $100,000Fixed selling and administrative expense = $100,000Total cost per unit = Variable cost per unit + Fixed manufacturing overhead / Units produced= $8 + $100,000 / 50,000= $10 per unitContribution margin per unit = Selling price per unit - Total cost per unit= $12 - $10= $2 per unitContribution margin ratio = Contribution margin per unit / Selling price per unit= $2 / $12= 0.167 or 16.7%Net operating income (NOI) for 50,000 units sold= Selling price per unit × Units sold - Total cost= $12 × 50,000 - ($8 × 50,000 + $100,000 + $100,000)= $600,000 - $600,000= $0 NOI for 120,000 units sold= Selling price per unit × Units sold - Total cost= $12 × 120,000 - ($8 × 120,000 + $100,000 + $100,000)= $1,440,000 - $1,460,000= ($20,000) or a net loss of $20,000.2. Constance Company's expected break-even sales in dollars can be calculated as follows:Constance Company sells two products, Y and Z.Fixed expenses = $450,000 per yearSelling price of Product Y = $120 per unitVariable cost of Product Y = $90 per unitSelling price of Product Z = $180 per unitVariable cost of Product Z = $150 per unitContribution margin of Product Y = Selling price of Product Y - Variable cost of Product Y= $120 - $90= $30Contribution margin of Product Z = Selling price of Product Z - Variable cost of Product Z= $180 - $150= $30Weighted average contribution margin per unit = (Contribution margin of Product Y × Sales mix of Product Y) + (Contribution margin of Product Z × Sales mix of Product Z) = ($30 × 60%) + ($30 × 40%)= $18 + $12= $30Contribution margin ratio = Weighted average contribution margin per unit / Selling price per unit= $30 / [(60% × $120) + (40% × $180)]= $30 / ($72 + $72)= $30 / $144= 0.2083 or 20.83%Breakeven sales in units = Fixed expenses / Contribution margin per unit= $450,000 / $30= 15,000Breakeven sales in dollars = Breakeven sales in units × Selling price per unit= 15,000 × [(60% × $120) + (40% × $180)]= 15,000 × ($72 + $72)= 15,000 × $144= $2,160,000.
Learn more about break-even here :-
https://brainly.com/question/31774927
#SPJ11
Design a webpage on Artificial Intelligence/augmented reality
Answers
Answer: is there even an answeR for this? Anyway plz do my question. If you are looking for web page options thou I would offer a Alexa vs VR
Explanation: