create a custom autofill list from the values in range a11 a14 ?
Answers
1.Select one or more cells you want to use as a basis for filling additional cells. For a series like 1, 2, 3, 4, 5..., type a11 and a12 in the first two cells. .
2.Drag the fill handle .
3.If needed, click Auto Fill Options. and choose the option you want.
You can save time inputting data manually into a worksheet with Excel's fantastic feature called AutoFill. The weeks and months are already kept in Excel, so it's not quite that magical, but the interesting part is that you can add your own unique lists. You should use custom lists if you frequently type out information like the names of employees, office locations, trading partners' nations, etc.Our list can now be added.
Press the Import list from cells area's choose range button.
Choose a few values from your list to highlight in the list.
Activate the Import button.
Hit the OK button.
You will be returned to the Options box.
learn more about Excel cells here:
https://brainly.com/question/1380185
#SPJ1
Related Questions
The ________ of the web makes it possible to deliver messages with text, audio, and video simultaneously to large numbers of people.
Answers
The richness of the web makes it possible to deliver messages with text, audio, and video simultaneously to large numbers of people.
Web richness refers to the immediacy and volume of data that can be delivered. A high web richness means that a large volume of data can be sent very quickly at the same time to a multitude of recipients. the data may be in any form text, audio or video.
A high richness equates to higher efficiency. The richness of the medium also changes its effectiveness. This means that the more information a message holds and the more people it can reach, the more effective it is. This allows for a simultaneous back and forth exchange which improves user experience.
According to multiple studies, in most cases consumer satisfaction is based upon both the richness of the web and the richness of the information.
You can learn more about richness of web at
https://brainly.com/question/13057128
#SPJ4
1. What is an AUP? (1 point)
O the abbreviation for the school administrator in an online education environment
a document outlining what is acceptable behavior when using the Internet for schoolwork
a policy outlining the proper formatting to use in Microsoft Office documents for online education
O a short course students can take to understand the school's policies better
Answers
The term AUP is option B: a document outlining what is acceptable behavior when using the Internet for school work.
What is an AUP?An Acceptable Use Policy (AUP) is a set of rules and guidelines that outline the appropriate and responsible use of a school's computer equipment, networks, and other digital resources. It is designed to protect the school's technology infrastructure, as well as the privacy and security of students, teachers, and other users.
An AUP may include guidelines for a variety of activities, such as:
Accessing and using the school's computer networks and equipmentUsing the Internet for schoolwork, research, and communicationProtecting personal privacy and security onlineUsing social media and other online communication toolsDownloading and installing software and appsTherefore, based on the context of the above, i can say that an AUP may also specify the consequences for violating the terms of use, which can include disciplinary action, revocation of access to digital resources, and other penalties.
Learn more about Acceptable Use Policy from
https://brainly.com/question/24951641
#SPJ1
Which of the following component is required to insert text in multimedia
programme?
i. Animation
ii. Text
iii. Graphics
Answers
Answer:
Text is used to insert text in multimedia program.
Hence,
Option ii. Text is the correct answer.
Explanation:
Let us define the terms first.
1. Animation:
Animation is kind of images that move. Animations are used to show some kind or process or working that is happening in multimedia program
2. Text:
Text is the explanation which is given in explicitly using fonts and typefaces.
3. Graphics:
Graphics are the images, logos that are used in multimedia.
So from the definitions above,
Text is used to insert text in multimedia program.
Hence,
Option ii. Text is the correct answer.
The following rules will trigger a singleton variable warning. how do you fix the problem?
Answers
The problem can be resolved by changing X to _, but the following rules will result in a singleton variable warning.
What is the trigger?A trigger is a device that activates the use of a speargun, crossbow, airgun, or other type of ranged weapon. The term can also refer to a switch that starts the action of non-shooting gadgets such traps, power tools, and rapid releases.The release of significantly more energy results from applying only a tiny quantity of energy to the trigger. Most triggers have a short, flattened lever (called the trigger blade) that is pushed by the index finger, however certain firearms, like the Springfield Armory M6 Scout and the M2 Browning machine gun, have triggers that are controlled by the thumb.To learn more about trigger, refer to:
https://brainly.com/question/2045902
#SPJ4
Select the correct answer.
Nina obtains an image in which birds are flying across the sky. Some parts of the image are blurry. In which stage of image processing will Nina fix the blurry parts?
A.
image acquisition
B.
preprocessing
C.
extracting features
D.
segmentation
Answers
Answer: Image Acquisition
Explanation:
Name three types of response messages that are used in the workplace.
Answers
Answer:
Verbalbody languagephone callswritten communicationExplanation:
Can someone please explain this issue to me..?
I signed into brainly today to start asking and answering questions, but it's not loading new questions. It's loading question from 2 weeks ago all the way back to questions from 2018.. I tried logging out and back in but that still didn't work. And when I reload it's the exact same questions. Can someone help me please??
Answers
Answer:
try going to your settings and clear the data of the app,that might help but it if it doesn't, try deleting it and then download it again
Write a program that prompts the user to input two POSITIVE numbers — a dividend (numerator) and a divisor (denominator). Your program should then divide the numerator by the denominator, and display the quotient followed by the remainder.
Hint: If you use division (/) to calculate the quotient, you will need to use int() to remove the decimals. You can also use integer division (// ), which was introduced in Question 10 of Lesson Practice 2.3.
Once you've calculated the quotient, you will need to use modular division (%) to calculate the remainder. Remember to clearly define the data types for all inputs in your code. You may need to use float( ) , int( ), and str( ) in your solution.
float( ): Anything inputted by a user should be transformed into a float — after all, we are accepting ALL positive numbers, integers and those with decimals.
int( ): When you divide the numerator and the divisor using /, make sure that the result is an integer.
str( ): After using modular division, you can transform the quotient and remainder back into strings to display the result in the print() command.
Answers
Answer:
yes
Explanation:
para saan po yung points dito?
Answers
Answer:
Hindi kudin Alam eh hahahha
Answer:
Hey, there this is the answer
Users need to use points to post a question. The more points they use, the more quickly their question will be answered. Users gain a basic number of points each time they log into the platform.
Click to review the online content. Then answer the question(s) below. using complete sentences. Scroll down to view additional
questions.
Memory Matters
Explain the difference between occasional forgetfulness and Alzheimer's disease.
Answers
Answer:
The answer is below
Explanation:
Alzheimer's disease is a progressive neurologic disorder which causes the brain to shrink (atrophy) and brain cells to die leading to memory loss and confusion.
Occasional forgetfulness are usually age related that is it occurs in older people while Alzheimer's disease is a memory loss which is progressive (that means that it gets worse over time.
Occasional forgetfulness is forgetting the position of some things while Alzheimer's disease involves Forgetting important information.
Answer:
Alzheimer's disease is a progressive neurologic disorder which causes the brain to shrink (atrophy) and brain cells to die leading to memory loss and confusion.Occasional forgetfulness are usually age related that is it occurs in older people while Alzheimer's disease is a memory loss which is progressive (that means that it gets worse over time.Occasional forgetfulness is forgetting the position of some things while Alzheimer's disease involves Forgetting important information.
Explanation:
got 100% on edg
WILL GIVE BRAINLIEST PLEASE HELP ASAP! ONLY 2 QUESTIONS FOR GUITAR!!!
Question 1:
When you listen to a guitar duet and the guitarists seem to be playing the right notes at the wrong time, which of following would best explain the problem?
One of the guitars is too loud.
One or more of the guitars is out of tune.
The guitars are being held incorrectly.
One or more of the guitarists is not keeping a steady beat.
Question 2:
When you listen to a guitar duet and have trouble hearing the melody, which of the following would best explain the problem?
The guitarists are playing with a balanced sound.
One of the guitarists is playing too loud.
The guitars are being held incorrectly.
The guitarists are not keeping a steady beat.
Answers
Answer: 1.When you listen to a guitar duet and the guitarists seem to be playing the right notes at the wrong time
2.The guitarists are not keeping a steady beat.
tell me if im wrong
There are a wide variety of nonsampling errors that can occur during data collection including the first type, ________.
Answers
Answer:
There are a wide variety of nonsampling errors that can occur during data collection including the first type, Fieldworker error
Explanation:
hopes this help (:
How can you tell if a website is credible?
a. Anything on the web is automatically credible
b. You must review aspects of the site such as the author’s credibility
c. If it has a top-level domain of .com, it is credible
d. All of the above
Answers
Answer:
b
Explanation:
you must review everything, creditability , certificates, domains, etc
What is the drawback of the linear model?
A.
communication is only in one direction
B.
too much noise is created
C.
no feedback is sent on receiving the message
D.
long travel between the sender and the receiver
Answers
Answer:
long travel between the sender and the receiver
Explanation:
The drawback of linear model is long travel between the sender and the receiver. The correct option is D.
What is linear model?Depending on the context, the phrase "linear model" is used differently in statistics.
The word is frequently used interchangeably with a linear regression model since it occurs most frequently in relation to regression models.
The phrase has a different connotation when employed in time series analysis, though.
Something that is linear is related to a line. A line is built using all of the linear equations. A non-linear equation is one that cannot be represented by a straight line. It has a variable slope value and resembles a graphed curve.
The linear model's disadvantage is the distance between the transmitter and the receiver.
Thus, the correct option is D.
For more details regarding linear model, visit:
https://brainly.com/question/29757372
#SPJ2
What are the components required to establish multimedia?
Answers
Answer:
The various components of multimedia are TEXT, AUDIO, GRAPHICS, VIDEO AND ANIMATION.All these components work together to represent information in an effective and easy manner. 1)Text: Text is the most common medium of representing the information
hope it helps
brainliest please
Think of a topic that is of interest to you. Your assignment is
to construct a questionnaire to gather data about your chosen
topic. Your questionnaire must include 10 questions, at a minimum.
You sho
Answers
The questionnaire on sustainable energy practices aims to gather valuable data about individuals' awareness, adoption, motivations, and barriers related to sustainable energy practices.
Topic: Sustainable Energy Practices
Questionnaire:
1. What is your level of awareness regarding sustainable energy practices?
a) Very aware
b) Somewhat aware
c) Not aware
2. Have you implemented any sustainable energy practices in your daily life or business?
a) Yes
b) No
3. If yes, which sustainable energy practices have you implemented? (Select all that apply)
a) Solar panels for electricity generation
b) Energy-efficient appliances
c) LED lighting
d) Wind turbines for electricity generation
e) Geothermal heating/cooling systems
f) Other (please specify) ___________
4. What motivates you to adopt sustainable energy practices? (Select all that apply)
a) Environmental benefits
b) Cost savings
c) Energy independence
d) Government incentives
e) Social responsibility
f) Other (please specify) ___________
5. What are the main barriers preventing you from implementing sustainable energy practices? (Select all that apply)
a) High upfront costs
b) Lack of information or knowledge
c) Uncertainty about the effectiveness of sustainable energy practices
d) Limited availability of resources or technologies
e) Lack of government support or incentives
f) Other (please specify) ___________
6. Are you willing to pay a premium for products or services that are sourced from sustainable energy practices?
a) Yes
b) No
7. How important is it for governments to invest in and promote sustainable energy practices?
a) Very important
b) Somewhat important
c) Not important
8. Are you aware of any government policies or initiatives in your country that support sustainable energy practices?
a) Yes
b) No
9. How satisfied are you with the current availability of sustainable energy options in your area?
a) Very satisfied
b) Somewhat satisfied
c) Not satisfied
10. Would you be interested in learning more about sustainable energy practices and how to implement them?
a) Yes
b) No
The questionnaire consists of ten questions that cover different aspects of sustainable energy practices. The questions are designed to gather information about respondents' awareness, implementation, motivation, barriers, willingness to pay, government involvement, satisfaction, and interest in learning more about sustainable energy practices.
The data collected through this questionnaire can be analyzed to understand the level of awareness, adoption, and perception of sustainable energy practices among the respondents. It can also provide insights into the factors that motivate or hinder the implementation of sustainable energy practices and the role of government policies in promoting sustainable energy.
The questionnaire on sustainable energy practices aims to gather valuable data about individuals' awareness, adoption, motivations, and barriers related to sustainable energy practices. The responses will contribute to understanding the current state of sustainable energy practices and identifying areas for improvement and awareness campaigns. This data can also inform policymakers and organizations about the level of support and interest in sustainable energy, helping shape future initiatives and policies in this field.
To know more about questionnaire follow the link:
https://brainly.com/question/30490175
#SPJ11
what was microsoft's first successful software product called
Answers
Microsoft Disk Operating System
Microsoft's first successful software product was indeed "Microsoft Windows." It was first released on November 20, 1985, and has since become one of the most widely used operating systems globally, maintaining its success over the years.
Microsoft's first successful software product is indeed "Microsoft Windows." Introduced on November 20, 1985, Windows is an operating system that has played a significant role in personal computing. It provides a graphical user interface (GUI) and enables users to run applications, manage files, and access the internet. Over the years, Windows has undergone numerous iterations, with each version introducing new features and enhancements. It has become one of the most widely used operating systems globally, maintaining its success and evolving to meet the changing needs of users. With a substantial market share, Windows continues to be a cornerstone product for Microsoft.
learn more about maintaining here;
https://brainly.com/question/28132832?
#SPJ11
because of an unexplained slowdown on your network, you decide to install monitoring software on several key network hosts to locate the problem. you will then collect and analyze the data from a central network host. which protocol will the software use to detect the problem?
Answers
The protocol that the software will use to find the issue is SNMP (Simple Network Management Protocol).
An Internet Standard protocol called Simple Network Management Protocol (SNMP) is used to gather, organize, and modify data about managed devices over IP networks in order to alter device behavior. Cable modems, routers, switches, servers, workstations, printers, and other devices frequently support SNMP.
Network management makes extensive use of SNMP for network monitoring. In a management information base (MIB), which describes the status and configuration of the managed systems, SNMP provides management data in the form of variables. Afterward, controlling apps can remotely query (and, in some cases, alter) these variables.
Three significant SNMP versions have been created and put into use. The first iteration of the protocol is called SNMPv1. Performance improvements can be found in SNMPv2c and SNMPv3, more recent versions.
To know more about SNMP click here:
https://brainly.com/question/14524481
#SPJ4
HELP HELP. I NEED 2 CODES SOLVED


Answers
The code is written in an incorrect syntax and has a few errors. It seems to be a mixture of two different procedures that are not well-defined.
How to explain the codeHowever, based on the structure and assumptions, I can infer that the output of this code will display the value of ans, which is the sum of the result of F(11,20) and G(-4,3).
The result of F(11,20) will be either 20.5 or 20, depending on the value of the variable p in the if-else statement. The result of G(-4,3) will be 3 because the loop inside the G procedure iterates three times, incrementing the value of val by 1 each time, and then returns val, which is 3. Therefore, the output of the code will be 23.
Learn more about code on
https://brainly.com/question/26134656
#SPJ1
type of keyboard that uses a touch screen as the input device.
Answers
Shakdnsosndksnsoansozjskskssksnsosnsksn
What happened to the ten commandments tablets.
Answers
Answer:
they got destroyed
Explanation:
whenwhen Moses came back from the mountain was angry when he saw the people worshipping Idols who threw down the tablets and broke them
What Does The Computer Monitor Contain?
Answers
Answer:
a visual display, some circuitry, a casing, and a power supply.
Explanation:
Screen, Layered Glass, Stands, Power Connector, Interface Board, Amplifier Circuit, and Reflectors and Light Sources.
This function checks if a character is a vowel. If it is, it returns true. Otherwise, it returns false. Where should return false; be written in the code? function checkVowel(character){ var vowels = ["a", "e", "i", "o", "u"]; for(var i=0; i
Answers
Answer:
at the end, i.e., after the for loop.
Explanation:
see code.
I also added a cooler alternative implementation.


The main function's return of 0 indicates a successful program execution. Return 1 in the main function denotes an error and indicates that the program did not run correctly. Returning zero indicates that a user-defined function has returned false. Returning 1 indicates that a user-defined function has returned true.
What return false be written in the code?One of the two values is what t may return. If the parameter or value supplied is True, it returns True. If the supplied parameter or value is False, it returns False.
Because it is a string, “0” is equivalent to false in JavaScript. However, when it is tested for equality, JavaScript's automatic type conversion changes “0” to its numeric value, which is 0; as we know, 0 denotes a false value. As a result, “0” is false.
Therefore, at the end, i.e., after the for loop. I also included a more attractive alternate implementation.
Learn more about code here:
https://brainly.com/question/20345390
#SPJ5
What is the analysis stage in System development life cycle?
Answers
Answer:
Explanation:
end user business requirements are analyzed and project goals converted into the defined system functions that the organization intends to develop. The three primary activities involved in the analysis phase are as follows: Gathering business requirement. Creating process diagrams.
An office building has two floors. A computer program is used to control an elevator that travels between the two floors. Physical sensors are used to set the following Boolean variables.
The elevator moves when the door is closed and the elevator is called to the floor that it is not currently on.
Which of the following Boolean expressions can be used in a selection statement to cause the elevator to move?
answer choices
(onFloor1 AND callTo2) AND (onFloor2 AND callTo1)
(onFloor1 AND callTo2) OR (onFloor2 AND callTo1)
(onFloor1 OR callTo2) AND (onFloor2 OR callTo1)
(onFloor1 OR callTo2) OR (onFloor2 OR callTo1)
Answers
The following Boolean expressions, "onFloor1 AND callTo2" or "onFloor2 AND callTo1," can be used in a selection statement to move the elevator.
The commands to move the lift may be simply determined based on the other commands designed to be provided and received by the lift, which indicate what operation it is engaged in.
When the elevator is on the first floor and has to be taken to the second floor, the order "onFloor1 AND callTo2" can be used. The order "onFloor2 AND callTo1" would serve as the reverse of the previously given instruction and cause the lift to operate in the exact opposite manner.
To know more about elevator visit:-
https://brainly.com/question/2168570
#SPJ4
graphical user interface (gui) is a special device for communicating with a user. T/F
Answers
False. A graphical user interface (GUI) is not a device but rather a software interface that allows users to interact with electronic devices or software applications.
It provides visual elements such as icons, menus, windows, and buttons to facilitate user interactions. While a GUI can be accessed through various devices such as computers, smartphones, or tablets, it is not a device itself. The GUI serves as a means of communication between the user and the device or software, enabling users to perform actions, input data, and receive feedback in a user-friendly and intuitive manner.
Learn more about graphical user interface here:
https://brainly.com/question/14758410
#SPJ11
Which explanation best explains the importance of using encryption?
Answers
Encryption is important because it protects sensitive information from unauthorized access. Encryption makes it difficult for hackers to steal personal and financial data, which can be used for identity theft, fraud, and other cyber crimes.
Step by step Explanation:
1. Encryption is a method of converting information into a code that only authorized individuals can read. The code is created using an encryption algorithm, which is a complex mathematical formula.
2. The importance of using encryption lies in its ability to protect sensitive information from unauthorized access. This includes personal and financial data, such as credit card numbers, social security numbers, and passwords.
3. Hackers and cyber criminals are always looking for ways to steal this type of information. If they are successful, they can use it for identity theft, fraud, and other crimes. Encryption makes it more difficult for them to do so.
4. Encryption is particularly important when data is transmitted over the internet. This includes online banking, e-commerce transactions, and email communication. Without encryption, this information can be intercepted and read by anyone with access to the internet.
5. Encryption also helps to protect information stored on electronic devices, such as laptops and smartphones. If these devices are lost or stolen, encryption can prevent unauthorized access to the data they contain.
6. In summary, encryption is important because it protects sensitive information from unauthorized access. It is a vital tool in the fight against cybercrime and is essential for ensuring the security and privacy of personal and financial data.
Know more about the encryption click here:
https://brainly.com/question/29572224
#SPJ11
what is computer system
Answers
Answer:
A computer system is a basic, complete and functional hardware and software setup with everything needed to implement computing performance.
Explanation:
Hope this was helpful,Have an amazing, spooky Halloween!!
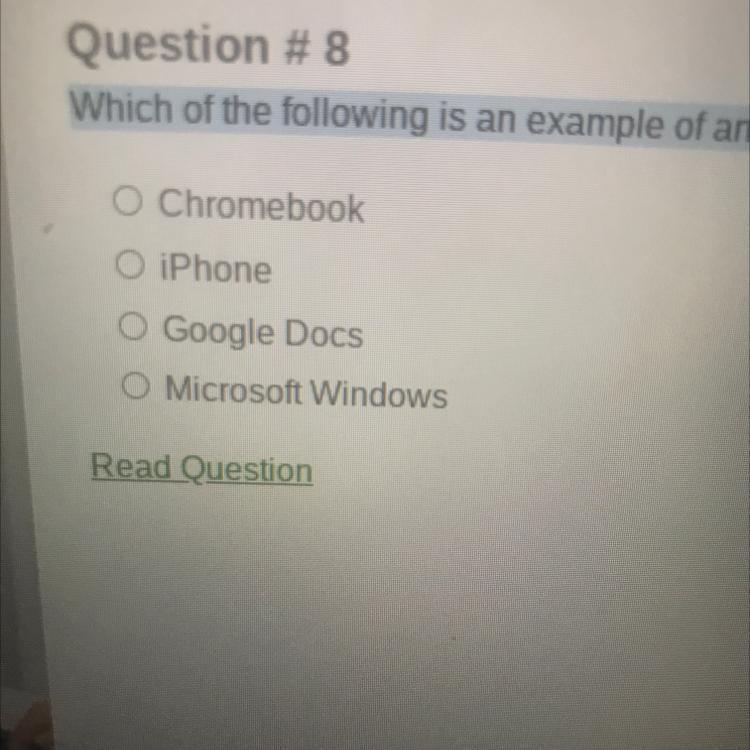
Which of the following is an example of an application ?
Answers
How does air gap networking seek to keep a system secure? by taking extra steps to ensure the DMZ server is fully patched to deal with the latest exploits by physically isolating it from all unsecured networks, such as the internet or a LAN by focusing on the security of the system through detection devices and incident reports
Answers
Air gap networking seeks to keep a system secure by physically isolating it from all unsecured networks, such as the internet or a LAN Thus, the correct option for this question is B.
What do you mean by the Air gap in networking?The air gap in network security may be defined as a type of measure that is utilized in order to ensure a computer network is physically isolated in order to prevent it from establishing an external connection, specifically to the Internet.
According to the context of this question, this process is used in order to ensure the security of the computer and computer network by physically isolating it from unsecured networks such as the internet or a LAN.
Therefore, the correct option for this question is B.
To learn more about Air gap networking, refer to the link:
https://brainly.com/question/14752856
#SPJ1