Can someone help me to write a python code to save list form python to CSV file please?
Answers
f = open("MyFileName.csv", "w")
lst = ["Hello", "Hi", "Bye"]
f.write(str(lst))
f.close()
I didn't necessarily know what you meant by list form. This program works for me in pycharm. I had to install the CSV plugin though. If you encounter any errors, I'll try my best to help you.
Related Questions
The term for an operator that may not evaluate one of its subexpressions is
Answers
Answer:
short-circuit
Explanation:
If you wanted to multiply two numbers, you would use the _____ key.
-
*
=
/
Answers
Incremental software development could be very effectively used for customers who do not
have a clear idea about the systems needed for their operations. Discuss.
Answers
Business software systems usually complex, software intensive, and frequently being changes when business goals or processes are changed. So incremental development is better. Real-time systems usually involve many hardware components which are not easy to change and cannot be incremental…
When we use the Incremental Model? When the requirements are superior. A project has a lengthy development schedule. When Software team are not very well skilled or trained...
Rather than delaying feedback until final delivery when time and resources have already been spent, incremental development ensures that teams can use feedback to make changes early and often…
Incremental model is a process in the software development cycle where we divide the requirement into multiple modules. This module goes through the phases of the model and release is added up until the purpose and the completion of the development model is achieved…
Incremental development is a method of building software products in which a system is built piece-by-piece. The final requirement specification is clear from the beginning, and everyone knows the end result clearly. The system is broken down into small sub-systems which are designed, built and tested independently…
Which of the following is the best example of a purpose of e-mail?
rapidly create and track project schedules of employees in different locations
easily provide printed documents to multiple people in one location
quickly share information with multiple recipients in several locations
O privately communicate with select participants at a single, common location
Answers
Answer:
The best example of a purpose of email among the options provided is: quickly share information with multiple recipients in several locations.
While each option serves a specific purpose, the ability to quickly share information with multiple recipients in different locations is one of the primary and most commonly used functions of email. Email allows for efficient communication, ensuring that information can be disseminated to multiple individuals simultaneously, regardless of their physical location. It eliminates the need for physical copies or face-to-face interactions, making it an effective tool for communication across distances.
Explanation:
Hi guys, I am in need of help. I have an HTML assignment due today at 11:59 PM and I have to work with video and animation. I am having trouble with working on keyframes because when I run my program, my video remains the same size. I do not know what I am doing wrong. I have attached a picture of my code. Please help me ASAP.
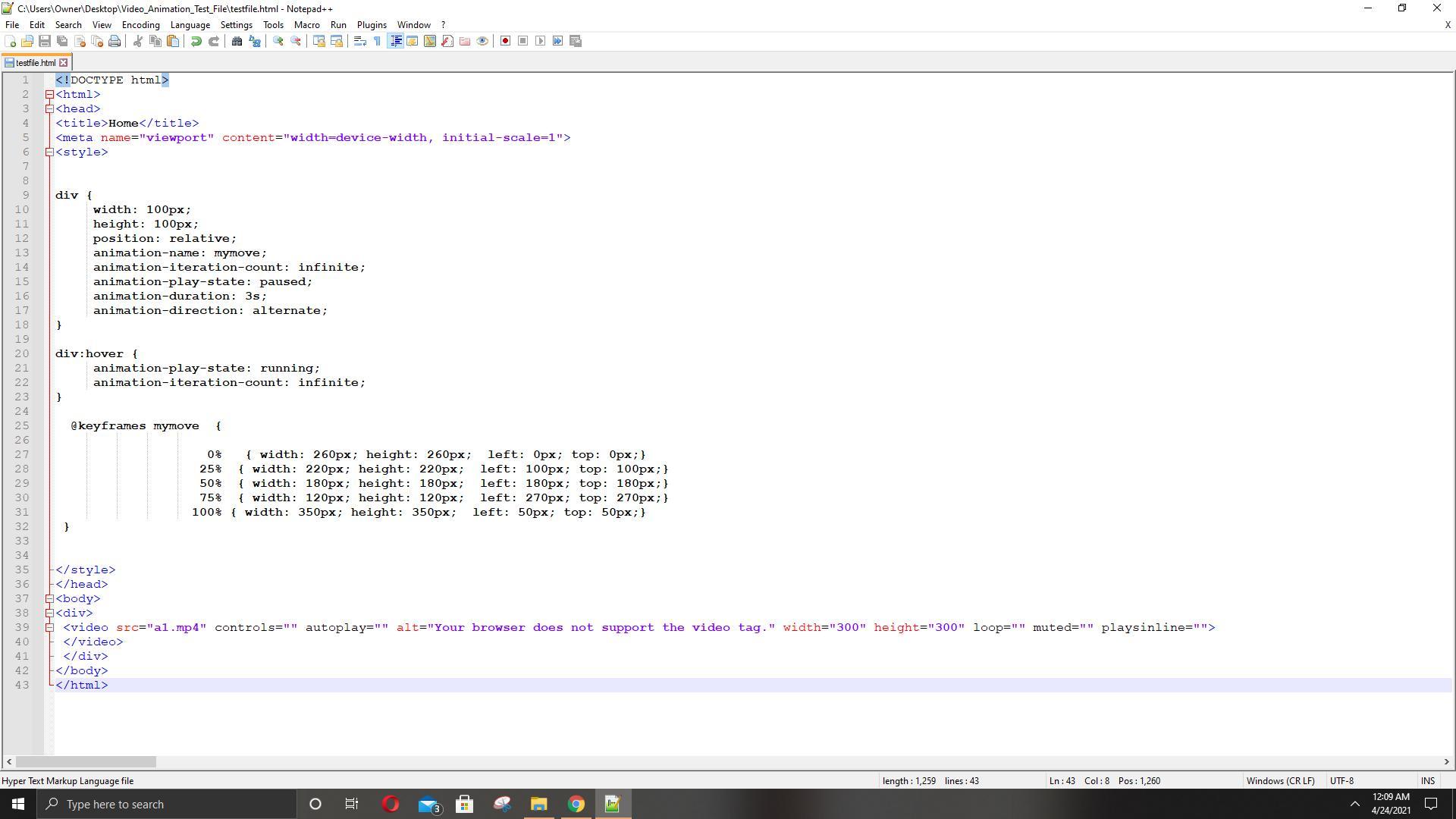
Answers
Answer:
Nothing much is wrong
Explanation:
Nothing much is wrong with it but then again I'm a full on computer geek, I assume you need to go back and re-read it and edit whatever you feel is wrong or incorrect it's like a gut feeling and you will have doubts on certain parts of what you are doing
is Cycle and share electric vehicles is agree or dis agree?why?
Answers
Utilizing more energy-efficient vehicles, such as hybrid and electric models, promotes the American economy and contributes to the fleet's diversification.
What are major safety in electric vehicles?Like any latest tech, EVs have been the subject of some scepticism, trepidation, and uncertainty. sometimes, even rumours. Certainly, some individuals are worried about the safety using electric automobiles. Even though there have been some reasons for worry, it's crucial to see the truth through the smoke. While EVs may have a special set of issues, many of them have been resolved because to the significant R&D and industry knowledge hired by OEMs, who daily work to advance EV technology. EV batteries are safeguarded in a tamper- and crash-proof construction. EVs include a technology that immediately disengages the battery during collisions to increase safety.
To know more about major safety in electric vehicles visit:
https://brainly.com/question/28222772
#SPJ1
Your professor is advising a new crowd-funding app for women's self-help groups (SHGs) in Latin America on their database architecture. This is the business requirement she has worked on: All campaigns belong to a SHG. An SHG must exist before a campaign is created, and when an SHG is deleted from the database, all its campaigns are deleted. SHGs always belong to a country, and a country must be added to the app before SHGs are added to it. Which of the following is true of the entities defined in the database? Select all that apply.
Question 6 options:
An SHG entity depends on a Campaign entity
A Campaign entity is a depend on the SHG entity
A Country is not dependent on the Campaign entity
An SHG entity is dependent on a Country entity
A Campaign is an Independent entity
Answers
Based on the given information, the following statements are true:
An SHG entity depends on a Country entity.A Campaign entity is dependent on the SHG entity.What is a country entity?In the context of database design, a country entity refers to a logical representation of a country within a database system.
It typically stores information related to countries, such as their names, codes, demographics, or any other relevant data.
The country entity serves as a reference point for other entities in the database, such as self-help groups (SHGs) or campaigns, allowing for proper organization and association of data within the system.
Learn more about Entity at:
https://brainly.com/question/29491576
#SPJ1
What is part of the computer?
Hardware
Software
CPU
All of these
Answers
Answer:
All of these are the parts of computer
Answer:
yes your answer is correct all those are the parts of the computer
hope it is helpful to you
What formatting changes do spreadsheet applications permit in the rows and columns of a spreadsheet?
Row and Column Formatting Options
Formatting rows and columns is similar to cell formatting. In an OpenOffice Calc spreadsheet, you can format data entered into rows and columns with the help of the Rows and Columns options. You can insert rows and columns into, or delete rows and columns from, a spreadsheet. Use the Insert or Delete rows and columns option on the Insert tab. Alternatively, select the row or column where you want new rows or columns to appear, right-click, and select Insert Only Row or Only Column options.
You can hide or show rows and columns in a spreadsheet. Use the Hide or Show option on the Format tab. For example, to hide a row, first select the row, then choose the Insert tab, then select the Row option, and then select Hide. Alternatively, you can select the row or columns, right-click, and select the Hide or Show option.
You can adjust the height of rows and width of columns. Select Row and then select the Height option on the Format tab. Similarly, select Column, then select the Width option on the Format tab. Alternatively, you can hold the mouse on the row and column divider, and drag the double arrow to the position. You can also use the AutoFit option on the Table tab to resize rows and columns.
Answers
Formatting rows and columns in a spreadsheet is similar to cell formatting. In OpenOffice Calc, users can insert or delete rows and columns, hide or show them, and adjust the height and width of the rows and columns.
What is spreadsheet?A spreadsheet is an electronic document that stores data in a tabular format and is used to perform calculations and analysis. It is a type of software program designed to assist with data entry, calculations, and other analysis tasks. Spreadsheets often contain formulas and functions that allow users to quickly and accurately calculate values based on the data they enter. Spreadsheets also provide users with the ability to present data in an organized and visually appealing way. Spreadsheets are an essential tool for businesses, schools, and other organizations to help them make decisions, track progress, and manage resources.
Users can access these options from the Insert, Format, and Table tabs. Alternatively, they can select the row or column they want to format, right-click, and select the relevant option. Additionally, users can hold the mouse on the row or column divider and drag the double arrow to the desired position. The AutoFit option on the Table tab can also be used to resize rows and columns.
To learn more about spreadsheet
https://brainly.com/question/30039670
#SPJ1
Lossy compression means that when you compress the file, you're going to lose some of the detail.
True
False
Question 2
InDesign is the industry standard for editing photos.
True
False
Question 3
Serif fonts are great for print media, while sans serif fonts are best for digital media.
True
False
Question 4
You should avoid using elements of photography such as repetition or symmetry in your photography.
True
False
Answers
Lossy compression means that when you compress the file, you're going to lose some of the detail is a true statement.
2. InDesign is the industry standard for editing photos is a true statement.
3. Serif fonts are great for print media, while sans serif fonts are best for digital media is a true statement.
4. You should avoid using elements of photography such as repetition or symmetry in your photography is a false statement.
What lossy compression means?The term lossy compression is known to be done to a data in a file and it is one where the data of the file is removed and is not saved to its original form after it has undergone decompression.
Note that data here tends to be permanently deleted, which is the reason this method is said to be known as an irreversible compression method.
Therefore, Lossy compression means that when you compress the file, you're going to lose some of the detail is a true statement.
Learn more about File compression from
https://brainly.com/question/9158961
#SPJ1
Enter a formula in cell C8 that divides the product of cells C5 through C7 by cell C4.
Answers
Answer: =(C5*C6*C7)/C4
Use the drop-down menus to complete statements about how to use the database documenter
options for 2: Home crate external data database tools
options for 3: reports analyze relationships documentation
options for 5: end finish ok run

Answers
To use the database documenter, follow these steps -
2: Select "Database Tools" from the dropdown menu.3: Choose "Analyze" from the dropdown menu.5: Click on "OK" to run the documenter and generate the desired reports and documentation.How is this so?This is the suggested sequence of steps to use the database documenter based on the given options.
By selecting "Database Tools" (2), choosing "Analyze" (3), and clicking on "OK" (5), you can initiate the documenter and generate the desired reports and documentation. Following these steps will help you utilize the database documenter effectively and efficiently.
Learn more about database documenter at:
https://brainly.com/question/31450253
#SPJ1
WHAT TYPES OF ACTIVITIES ARE PERFORMED BY HEALTH CARE SOFTWARES
Answers
Answer:
lectronic Health Record (EHR) Software. ...
Medical database software. ...
Medical research software. ...
Medical diagnosis software. ...
Medical imaging software. ...
E-prescribing software. ...
Telemedicine software. ...
Appointment scheduling (booking) software.
Discuss the relationship of culture and trends?
Answers
please note, my working hours may be different than yours. please don't feel obligated to respond outside of your normal business hours unless necessary.
Answers
A statement "please note, my working hours may be different than yours. please don't feel obligated to respond outside of your normal business hours unless necessary." this means that more benefit to change to flexible work.
What is flexible work?Individual behavior describes the behaviors, responses, reactions, and ways in which a person behaves when they are in a certain situation. It consists of a variety of reactions to both internal and external stimuli. Individual habits and actions are frequently linked, either because of time restraints, resource accessibility, social connections, or biological inclinations. For instance, drinkers are more likely to smoke than non-drinkers, and physically unfit people are also less likely to make an effort to prepare meals at home.
Learn more about flexible work: https://brainly.com/question/29316477
#SPJ4
a. If the value in the Elected column is equal to the text "Yes", the formula should display Elected as the text.
b. Otherwise, the formula should determine if the value in the Finance Certified column is equal to the text "Yes" and return the text Yes if true And No if false.
Answers
=IF(Election="Yes","Election",IF(Finance Certified="Yes","Yes","No")) You can accomplish this by nesting one IF function inside of another IF function. The outer IF function determines whether "Yes" or "No" is the value in the Elected column.
How do you utilize Excel's IF function with a yes or no decision?In this instance, cell D2's formula reads: IF
Return Yes if C2 = 1; else, return No.
As you can see, you may evaluate text and values using the IF function. Error evaluation is another application for it.
What does Excel's between function do?You can determine whether a number, date, or other piece of data, such text, falls between two specified values in a dataset using the BETWEEN function or formula. A formula is employed to determine whether.
To know more about function visit:-
https://brainly.com/question/28939774
#SPJ1
What would be an ideal scenario for using edge computing solutions?
Answers
An ideal scenario for using edge computing solutions will be a school computer lab with workstations connected to a local network. The correct option is C.
What is edge computing?The most typical places to find edge computing are in the transportation, industrial, energy, and even retail sectors.
The performant and scalable implementation model used by Akamai ensures that data and computation are not constrained by latency problems, which can negatively affect digital experiences.
Thanks to EdgeWorkers and EdgeKV, development teams can now focus on creating cutting-edge services and manage Akamai as code as a part of their digital infrastructure.
Thus, the correct option is C.
For more details regarding edge computing, visit:
https://brainly.com/question/28256857
#SPJ1
Create a program that will ask the user to specify a file in the current directory. The program will count and report the number of lines, words and characters. There are several approaches that can be used. Hint: You may want to consider read(), readlines(), readline(), split() method, and/or a for statement such as 'for line in thisfile' might be helpful. The approach is up to you. It is correct if it works!
Answers
Answer:
Explanation:
The following code is written in Python. It is a function that takes in the file directory as an argument, reads the file. Then it counts the lines and words in the file and saves that count in separate variables. Then it loops through the entire file counting the characters, without counting whitespace and newlines breaks. Finally, it prints all of that information out.
def countText(file):
f = open(file, 'r')
text = f.read()
lines = len(text.split('\n'))
words = len(text.split(' '))
characters = 0
for char in text:
if (char != ' ') and (char != '\n'):
characters += 1
print("File Count:")
print("Lines: " + str(lines))
print("Words: " + str(words))
print("Characters: " + str(characters))

what is the role of product management in agile safe
Answers
Product management plays a crucial role in Agile SAFe (Scaled Agile Framework) by defining desirable, viable, feasible, and sustainable solutions that meet customer needs and supporting development across the product life cycle.
In an Agile SAFe environment, product management acts as the bridge between the customer and the development teams. They are responsible for understanding customer needs, gathering feedback, and translating those needs into actionable requirements.
By collaborating with stakeholders, product management ensures that the product vision aligns with customer expectations.
To define desirable solutions, product management conducts market research, user interviews, and analyzes customer feedback. They identify market trends, user pain points, and prioritize features accordingly.
They work closely with customers to gather insights and validate product ideas through iterative feedback loops.
Viable solutions are determined by evaluating market demand, competitive landscape, and business objectives. Product management considers factors like revenue potential, market share, and return on investment to ensure the product is financially sustainable.
Feasible solutions require close collaboration with development teams. Product management works with engineering, design, and other teams to assess technical feasibility, define scope, and establish delivery timelines.
They engage in Agile ceremonies such as sprint planning, backlog refinement, and daily stand-ups to facilitate efficient development.
Sustainable solutions are designed with long-term success in mind. Product management focuses on creating scalable, adaptable products that can evolve with changing customer needs and market dynamics. They continuously monitor and analyze product performance, customer feedback, and market trends to make informed decisions and drive iterative improvements.
In summary, product management in Agile SAFe is responsible for understanding customer needs, defining desirable and viable solutions, ensuring technical feasibility, and supporting development teams throughout the product life cycle to deliver sustainable products that meet customer expectations.
For more such questions Product,click on
https://brainly.com/question/28776010
#SPJ8
In most cases, the word "software" is interchangeable with the word
Answers
Answer:
In most cases, the word "software" is interchangeable with the word "program"
Explanation:
The terms software and program are used interchangeably as they often refer to the same thing in daily usage.
In a balanced budget, the amount is the amount
Answers
In a balanced budget, the Income amount is same as the expense amount.
What is a balanced budget?A balanced budget is one in which the revenues match the expenditures. As a result, neither a fiscal deficit nor a fiscal surplus exist. In general, it is a budget that does not have a budget deficit but may have a budget surplus.
Planning a balanced budget assists governments in avoiding excessive spending and focuses cash on regions and services that are most in need.
Hence the above statement is correct.
Learn more about Budget:
https://brainly.com/question/15683430
#SPJ1
Discuss at least 1 Miscrosoft Windows security features that could protect data.
Answers
Answer:
Virus & threat protection.
Explanation:
Monitor threats to your device, run scans, and get updates to help detect the latest threats.
Answer:
User account control.
Explanation:
prevents malware damage. Helps organizations deploy a better-managed desktop.
Hi!
i want to ask how to create this matrix A=[-4 2 1;2 -4 1;1 2 -4] using only eye ones and zeros .Thanks in advance!!
Answers
The matrix A=[-4 2 1;2 -4 1;1 2 -4] can be created by using the following code in Matlab/Octave:
A = -4*eye(3) + 2*(eye(3,3) - eye(3)) + (eye(3,3) - 2*eye(3))
Here, eye(3) creates an identity matrix of size 3x3 with ones on the diagonal and zeros elsewhere.
eye(3,3) - eye(3) creates a matrix of size 3x3 with ones on the off-diagonal and zeros on the diagonal.
eye(3,3) - 2*eye(3) creates a matrix of size 3x3 with -1 on the off-diagonal and zeros on the diagonal.
The code above uses the properties of the identity matrix and the properties of matrix addition and scalar multiplication to create the desired matrix A.
You can also create the matrix A by using following code:
A = [-4 2 1; 2 -4 1; 1 2 -4]
It is not necessary to create the matrix A using only ones and zeroes but this is one of the way to create this matrix.
Plzz help will mark brainliest

Answers
Answer:
11. 3 dimensions
12. ( i believe its number 3)
13. 2 option
14. Natural Light
15. Development
Explanation:
can someone please give me the correct answer to this? 8.7.5 Calendar Codehs.
Answers
The calendar Codes is given as follows;
import calendar
# Prompt user for month and year
month = int(input("Enter month (1-12): "))
year = int(input("Enter year: "))
# Display calendar for the given month and year
print(calendar.month(year, month) )
How does this work ?The month ) function from the calendar module takes two arguments: the year and month to display the calendar for.
It returns a formatted string representing the calendar for that month, which is then printed to the console.
A formatted string literal, often known as an f-string, is a string literal that begins with 'f' or 'F' in programming.
Learn more about Codes at:
https://brainly.com/question/3042960
#SPJ1
PLEASE HELP
Find five secure websites. For each site, include the following:
the name of the site
a link to the site
a screenshot of the security icon for each specific site
a description of how you knew the site was secure
Use your own words and complete sentences when explaining how you knew the site was secure.
Answers
The name of the secure websites are given as follows:
Each of the above websites had the security icon on the top left corner of the address bar just before the above domain names.
What is Website Security?The protection of personal and corporate public-facing websites from cyberattacks is referred to as website security.
It also refers to any program or activity done to avoid website exploitation in any way or to ensure that website data is not accessible to cybercriminals.
Businesses that do not have a proactive security policy risk virus spread, as well as attacks on other websites, networks, and IT infrastructures.
Web-based threats, also known as online threats, are a type of cybersecurity risk that can create an unwanted occurrence or action over the internet. End-user weaknesses, web service programmers, or web services themselves enable online threats.
Learn more about website security:
https://brainly.com/question/28269688
#SPJ1

Please Complete in Java a. Create a class named Book that has 5 fields variables: a stock number, author, title, price, and number of pages for a book. For each field variable create methods to get and set methods. b. Design an application that declares two Book objects. For each object set 2 field variables and print 2 field values. c. Design an application that declares an array of 10 Books. Prompt the user to set all field variables for each Book object in the array, and then print all the values.
Answers
Answer:
Explanation:
The following code is written in Java. I created both versions of the program that was described in the question. The outputs can be seen in the attached images below. Both versions are attached as txt files below as well.


Which of the following is NOT a video playback option in Microsoft PowerPoint?
Answers
The option that is NOT a video playback option in Microsoft PowerPoint is Record Narration
What is the Microsoft PowerPointIn Microsoft PowerPoint, "program playback alternatives" concern the various controls and scenes that are accessible for performing and maneuvering a television file that has been introduced into a flow.
This feature is independent to video playback but moderately to accumulating visual and audio entertainment transmitted via radio waves to the performance. When you record a reading, you can occasion it to play instinctively accompanying each veer or admit the consumer to control playback.
Learn more about Microsoft PowerPoint from
https://brainly.com/question/23714390
#SPJ1
Recently, Walmart offered a wireless data contract based on bandwidth used, with a minimum monthly charge of $42 for up to 5 gigabytes (GB) of use. Additional GB can be purchased at the following rates: $12 for an additional 1 GB, $28 for an additional 3 GB, and $44 for a capacity of 10 GB. What is the cost for a user who is expecting to use 9 GB
Answers
Answer:
For 9GB of data the user would pay $82 monthly!
Explanation:
To start off, our end goal is 9GB. We have the equation 9 = ? We can add up to our solutions with 1GB, 3GB, and 10GB. We can immediately rule out 10GB, since 9GB ≠ 10GB. To cost the least amount of money we can add up 3GB and 1GB = 4GB + 5GB = 9GB!
So, our equation is 3GB + 1GB + 5GB = 9GB, now lets figure out the cost!
$28 + $12 + $42 = $82
For 9GB of data the user would pay $82 monthly!
Hope this Helps! :)
Have any questions? Ask below in the comments and I will try my best to answer.
-SGO
John tells you that a certain algorithm runs in time (3 + 200), and Bill tells you that the same algorithm runs in time Ω(3). Can both John and Bill be correct? Why?
Answers
According to the question, the statements made by both John and Bill are correct. This is because both express the value of algorithms with respect to their requirement and identification.
What is an Algorithm?An algorithm may be characterized as a type of procedure that is widely used for solving a problem or performing a computation. They act as an exact list of instructions that conduct specified actions step by step in either hardware- or software-based routines.
As per John, the worst-case run time requires the setting of the algorithm to (3+200), but on contrary, as per Bill, the running time of the same algorithm requires Ω(3). The concept of both people is correct but they are understanding the algorithm with respect to their facts and requirements.
Therefore, the statements made by both John and Bill are correct. This is because both express the value of algorithms with respect to their requirement and identification.
To learn more about Algorithm, refer to the link:
https://brainly.com/question/24953880
#SPJ9