At a local Linux User Group (LUG) meeting, some people who are unfamiliar with Linux ask you to explain what the GPL is and how it relates to OSS. These people also don’t understand how OSS generates profit and are under the impression that the quality of OSS is poor compared to commercial software. They suggest that the potential for OSS in the future might be limited. How do you reply? Include examples to demonstrate your points. To which Web sites can you direct them for further information?
Answers
The GPL, or what is known as the GNU General Public License, is seen as a form of a type of software license that is known to be commonly used in terms of distributing as well as sharing open source software.
What is the GPL about?The GPL is known also to be made by the Free Software Foundation (FSF) and it is said to be one that is known to be widely used as well as known form for licenses for OSS.
OSS is seen aa a software that has its source code to be available to all of the public.
Hence, to address the misconceptions in regards to OSS, one has to look at the Quality of OSS.
Learn more about Web sites from
https://brainly.com/question/28431103
#SPJ4
Related Questions
USE PYTHON TURTLE GRAPHICS


Answers
Code:
In .txt file
Explanation:
I made the code a bit more flexible than instructed, for example, you don't need two different functions for the two chessboards. And you can easily edit the chessboard's size, numbers and coordinates.
Please ask me if there is anything you don't understand, or if the code isn't working correctly.


need help on question 5! no links pls

Answers
Answer: less than 50%, it’s about 49%
Explanation:
Answer:
59.5
so I would say the 3 third option
pls, help it's urgent... 44 points plsssssssssssssssss
Write an algorithm and Flowchart for reversing a Number eg. N=9486.
Answers
The steps to reverse a number is given below:
The AlgorithmStep 1 Start
step 2 Read a number n
Step 3 a=n/1000
step 4 calculate b=(n%1000)/100
step 5 calculate c= (n%100)/10
step 6 calculate d = n%10
step 7 calculate reverse = a+(b*10)+(c*100)+(d*1000)
step 8 display reverse
step 9 stop
Read more about algorithms here:
https://brainly.com/question/24953880
#SPJ1
Why won't my brainly account level up?
Answers
Well, you need to have 5 brainiest answers plus 500 points. So, in order to level up in brainly you need 500 plus 5 brainiest.
What is brainly?Brainly is a Polish company with headquarters in New York City. It is a social learning platform where millions of students and teachers work together to solve academic problems. The mission of Brainly is to encourage students to share and explore knowledge in a collaborative environment.
It can also be used to ask and answer homework questions by students, parents, and teachers. The platform includes n elements such as points and ranks. It encourages users to participate in the online community by answering questions posted by other users. Brainly reported 350 million monthly users as of November 2020, making it the most popular education app in the world.
Learn more about level up
https://brainly.com/question/7853380
#SPJ1
Answer:
This is because to level up, you need a certain number of points and brainliest answers! To get this you can always keep answering questions to get your points up and whenever you complete an answer which is superior than any other, the user may choose to give you brainliest!
Hope this helps, have a lovely day! :)
a message ____________________ is a fingerprint of the author’s message that is compared with the recipient’s locally calculated hash of the same message.
Answers
A message fingerprint is a unique digital signature that identifies the author's message and is compared to the recipient's locally calculated hash of the same message. This method of verification helps to ensure the authenticity and integrity of the message being sent.
Message fingerprinting is a widespread approach in modern communication networks for preventing unwanted access to data and ensuring that messages have not been tampered with during transit. A hashing technique is used to turn the content of a communication into a unique digital signature before it is transmitted. This signature, or fingerprint, is then delivered to the receiver along with the message.
When the message is received, the recipient's system computes the hash of the message and compares it to the sender's hash to guarantee that they match. If they don't match, it means the communication was tampered with or distorted in route. The communication will be refused in such instances, and the sender will be alerted.
Message fingerprinting is a crucial security measure that is used in various communication technologies such as email, instant messaging, and file-sharing systems. By using message fingerprints, organizations can ensure that their sensitive data remains secure and that their messages are delivered without any tampering or unauthorized access.
To learn more about the digital signature, visit:
https://brainly.com/question/14862771
#SPJ11
A name given to a spot in memory is called:
Answers
Answer:
Variable
Explanation:
I'll answer this question in computing terms.
The answer to this question is a variable. Variable can be seen as memory location or spots.
They can be compared to the containers (in real world). Variables are used to store values same way containers are used to store contents.
In computing, a variable must have a
NameTypeSizeetc...Part 1 Assume that the ready queue has just received for processes: P1, P2, P3, P4, in that order. All at time 0. The CPU execution times for these processes are as follows: Process Execution Time P1 9 P2 24 P3 8 13 P4 Draw the Gantt chart and calculate the metric listed in parentheses for each of the following scheduling algorithms: 1. First Come, First Served (Total Wait Time) 2. Shortest Job First (Total Wait Time) 3. Round Robin, with a time quantum of 6 ms (Total Wait and Response Times) Part II Now assume that P1 arrives in the ready queue at time 0, P2 arrives at time 6, P3 arrives at time 15, and P4 arrives at time 21. The CPU execution times for the processes are the same as in Part I: Process Execution Time P1 9 P2 24 P3 8 13 P4 Draw the Gantt chart and calculate the total wait time for each of the following scheduling algorithms: 1. Shortest Job First 2. Shortest Remaining Time Next (remember, this is a preemptive algorithm) 3. Preemptive priority with the following priorities: Process Priority P1 1 P2 4 3 P3 P4 2 For this system, assume that the highest priority has the lowest number (i.e., 1 is the most important) 4. Non-Preemptive priority with the same priorities as above. Be sure to note priority inversion when/if it occurs. Priority inversion is when a process with a lower priority executes over a process with a higher priority.
Answers
In Part I, we will analyze three scheduling algorithms: First Come, First Served (FCFS), Shortest Job First (SJF), and Round Robin (RR) with a time quantum of 6 ms. We will draw Gantt charts and calculate the total wait time for each algorithm. In Part II, we will consider the same scheduling algorithms but with different arrival times for the processes. We will draw Gantt charts and calculate the total wait time, considering the Shortest Job First (SJF), Shortest Remaining Time Next (SRTN), Preemptive Priority, and Non-Preemptive Priority algorithms.
Part I:
For FCFS, we will arrange the processes in the order they arrived (P1, P2, P3, P4). We will calculate the total wait time by summing up the waiting time for each process.
For SJF, we will prioritize the processes based on their execution times (P3, P1, P4, P2). We will calculate the total wait time by summing up the waiting time for each process.
For RR with a time quantum of 6 ms, we will allocate the CPU to each process for 6 ms until their execution completes. We will draw the Gantt chart accordingly and calculate the total wait and response times.
Part II:
Considering the new arrival times, we will follow the same approach as in Part I for each scheduling algorithm.
For SJF, we will prioritize the processes based on their execution times. However, since the processes arrive at different times, we will calculate the wait time accordingly.
For SRTN, we will preemptively allocate the CPU to the process with the shortest remaining time. We will draw the Gantt chart and calculate the total wait time.
For Preemptive Priority, we will assign priorities to the processes and allocate the CPU based on the highest priority. We will calculate the total wait time, considering priority inversion if it occurs.
For Non-Preemptive Priority, we will assign priorities to the processes but allow each process to complete its execution before switching to another process. We will calculate the total wait time, considering any potential priority inversion.
By analyzing each scheduling algorithm, drawing Gantt charts, and calculating the total wait time, we can evaluate their efficiency and performance in different scenarios.
Learn more about Non-Preemptive here:
https://brainly.com/question/32612990
#SPJ11
why is the quality of the photo, music, etc better when more samples are taken?
Answers
When more samples are taken, the signal is represented more accurately and with less distortion, resulting in a better quality photo, music, or other digital signal.
What is distortion ?Distortion is the alteration or misrepresentation of the original shape, appearance, or sound of something. It is a distortion of the truth, in which facts are exaggerated or misstated to support an argument or opinion. It can also refer to the alteration of a signal, such as audio or video, by external means such as a microphone, amplifier, or speaker. In audio, distortion can be used to create interesting effects, or it can be a result of an overdriven signal, caused by too much gain.
The quality of a photo, music, or other digital signal is determined by the number of samples taken. The more samples taken, the more accurately the signal can be represented. This is known as sampling rate or sampling frequency. The higher the sampling rate, the better the quality of the signal.
To learn more about distortion
https://brainly.com/question/28603019
#SPJ4
Which sharing method should you recommend if a user wants to configure share and NTFS permissions for another user that wants to access a folder on their computer in a single simple process?
a. Grant access to
b. Public folder sharing
c. Create A Shared Folder Wizard
d. Advanced sharing
Answers
When a user wishes to configure sharing and NTFS permissions for another user who wants to access a folder on their computer in a single, easy process, the best sharing method to recommend is the "Create A Shared Folder Wizard."
The correct answer to the given question is option 3.
The "Create A Shared Folder Wizard" simplifies the procedure of configuring a folder to be shared on a network by automating most of the process.
To share a folder on the computer with others, you must first select the folder and then run the "Create A Shared Folder Wizard" from within the folder's properties. The wizard provides prompts for sharing the folder and granting permission to other users, making it simple to configure share and NTFS permissions for the user who wishes to access the folder.
You can also specify the level of access granted to other users, such as read-only or full access, using the wizard.Furthermore, the wizard streamlines the process of sharing files with others on the network by providing a single tool that handles both sharing and permissions, saving time and effort.
Overall, when a user wishes to share a folder with another user on their computer, the "Create A Shared Folder Wizard" is a highly recommended sharing method that simplifies the process and allows for easy configuration of share and NTFS permissions.
For more such questions on NTFS permissions, click on:
https://brainly.com/question/14178838
#SPJ8
question 1: perform the following operations for the following b -tree insert 11 insert 1000 delete 19 delete 1000 insert 13
Answers
The given operations on the B-tree are:
- Insert 11
- Insert 1000
- Delete 19
- Delete 1000
- Insert 13
The B-tree is a self-balancing tree data structure commonly used in computer science. It maintains data in sorted order and allows efficient insertion, deletion, and retrieval operations. Let's go through the given operations step by step.
1. Insert 11: Initially, we start with an empty B-tree. Inserting 11 as the first element creates a root node with 11 as its key.
2. Insert 1000: Since 1000 is larger than the current key in the root node, we need to traverse to the right subtree. However, if the right child is full, we split it into two nodes and promote the middle key to the parent. In this case, we split the root node, promote 11 to a parent node, and create a new right child node with 1000 as its key.
3. Delete 19: To delete a key, we traverse the B-tree to find the corresponding node. In this case, 19 is not present in the tree, so the delete operation has no effect.
4. Delete 1000: Similar to the previous step, we traverse the B-tree to find 1000. Since it is a leaf node, we can directly remove it from the tree.
5. Insert 13: After the previous operations, the tree now contains two nodes: one with key 11 and the other with key 1000. Inserting 13 requires splitting the right child node of the root, promoting 13 to the parent, and creating a new right child node with 1000 as its key.
Learn more about B-tree
brainly.com/question/32667862
#SPJ11
presenting results to the user is called
Answers
Answer:
You're answer is,
Output devices
Explanation:
An output device is any piece of computer hardware equipment which converts information into a human-perceptible form or, historically, into a physical machine-readable form for use with other non-computerized equipment. It can be text, graphics, tactile, audio, or video. Examples include monitors, printers, speakers, headphones, projectors, GPS devices, optical mark readers, and braille readers.
Hope this helps
`
`
`
Tori
Steeler corporation is planning to sell 100,000 units for 2.00 per unit and will break even at this level of sales fixed expenses will be 75,000 what are the company's variable expenses per unit
Answers
Answer:
1.25 per unit
Explanation:
Number of units to sell = 100,000
Price per unit = 2
Fixed expense = 75000
At break even point :
Revenue = total expenses
Total expenses = fixed cost + variable cost
Let variable cost = x
Revenue = units to sell * price per unit
Revenue = 100,000 * 2 = 200,000
Hence,
Fixed cost + variable cost = Revenue
75000 + x = 200,000
x = 200, 000 - 75000
x = 125,000
Variable cost = 125,000
The variable expense per unit is thus :
Variable expense / number of units
125,000 / 100,000 = 1.25 per unit
Binary digits can represent the state of an electrical charge. How
many different states of an electrical charge can binary digits
represent?
Answers
What are 3 examples of Chassis Wiring?
Answers
Answer:
.
Explanation:
I need help for 8.10 Code Practice: Question 2. Thanks! =D

Answers
vocab = ['Libraries', 'Bandwidth', 'Hierarchy', 'Software', 'Firewall', 'Cybersecurity', 'Phishing', 'Logic', 'Productivity']
# Print the list before sorting
print(vocab)
# Sort the list
for i in range(len(vocab)):
for j in range(i+1, len(vocab)):
if len(vocab[i]) > len(vocab[j]):
vocab[i], vocab[j] = vocab[j], vocab[i]
# Print the list after sorting
print(vocab)
Compare the OSI Application Layer with the TCP/IP Application Layer. Which statement is true? Both application layers are relevant mainly to programmers, not to network technicians. The OSI application layer involves more things than does the TCP/IP application layer. They are the same layer, only they are viewed through different conventions. The TCP/IP application layer is for the user; it is not important to programmers or network technicians.
Answers
Answer:
They are the same layer, only they are viewed through different conventions.
Explanation:
OSI model stands for Open Systems Interconnection. The seven layers of OSI model architecture starts from the Hardware Layers (Layers in Hardware Systems) to Software Layers (Layers in Software Systems) and includes the following;
1. Physical Layer
2. Data link Layer
3. Network Layer
4. Transport Layer
5. Session Layer
6. Presentation Layer
7. Application Layer
Each layer has its unique functionality which is responsible for the proper functioning of the communication services.
On the other hand, the Transmission Control Protocol and Internet Protocol (TCP/IP) Application Layer comprises of four (4) main layers and these includes;
I. Application layer.
II. Transport layer.
III. Internet layer.
IV. Network layer.
This ultimately implies that, the Open Systems Interconnection (OSI) Application Layer and the Transmission Control Protocol and Internet Protocol (TCP/IP) Application Layer are the same layer, only they are made up of different number of layers and as such are viewed through different conventions.
Answer:
c
Explanation:
Please help with coding from a beginner's computer sci. class (Language=Java)
Assignment details=
1. Write code for one round.
a. Get the user’s selection using a Scanner reading from the keyboard.
Let's play RPSLR!
1. Rock
2. Paper
3. Scissors
4. Lizard
5. Spock
What is your selection? 4
b. Get the computer’s selection by generating a random number.
c. Compare the user’s selection to the computer’s selection.
d. For each comparison, print the outcome of the round.
You chose Lizard.
The Computer chose Spock.
Lizard poisons Spock.
The User has won.
2. Modify your code by adding a loop.
a. Add a loop to your code to repeat each round.
b. Ask if the player wants to play again. If the player doesn’t want to play again, break out
of the loop.
Do you want to play again? (Y or N) Y
3. Add summary statistics.
a. Add variables to count rounds, wins, losses, and draws and increment them
appropriately.
b. After the loop, print the summary information.
______SUMMARY_______
Rounds: 13
Wins: 5 38.5%
Loses: 7 53.8%
Draws: 1 7.7%
Answers
Answer: Here is some sample code that demonstrates how to complete the assignment using Java:
import java.util.Random;
import java.util.Scanner;
public class RPSLR {
public static void main(String[] args) {
// Initialize scanner for reading user input
Scanner scanner = new Scanner(System.in);
// Initialize random number generator for computer's selection
Random random = new Random();
// Initialize counters for rounds, wins, losses, and draws
int rounds = 0;
int wins = 0;
int losses = 0;
int draws = 0;
// Main game loop
while (true) {
// Get user's selection
System.out.println("Let's play RPSLR!");
System.out.println("1. Rock");
System.out.println("2. Paper");
System.out.println("3. Scissors");
System.out.println("4. Lizard");
System.out.println("5. Spock");
System.out.print("What is your selection? ");
int userSelection = scanner.nextInt();
// Get computer's selection
int computerSelection = random.nextInt(5) + 1;
// Compare selections and determine outcome
String outcome;
if (userSelection == computerSelection) {
outcome = "draw";
draws++;
} else if ((userSelection == 1 && computerSelection == 3) ||
(userSelection == 1 && computerSelection == 4) ||
(userSelection == 2 && computerSelection == 1) ||
(userSelection == 2 && computerSelection == 5) ||
(userSelection == 3 && computerSelection == 2) ||
(userSelection == 3 && computerSelection == 4) ||
(userSelection == 4 && computerSelection == 2) ||
(userSelection == 4 && computerSelection == 5) ||
(userSelection == 5 && computerSelection == 1) ||
(userSelection == 5 && computerSelection == 3)) {
outcome = "win";
wins++;
} else {
outcome = "lose";
losses++;
}
// Print outcome of round
String userSelectionString;
String computerSelectionString;
if (userSelection == 1) {
userSelectionString = "Rock";
} else if (userSelection == 2) {
userSelectionString = "Paper";
} else if (userSelection == 3) {
userSelectionString = "Scissors";
} else if (userSelection == 4) {
userSelectionString = "Lizard";
} else {
userSelectionString = "Spock";
}
if (computerSelection == 1) {
computerSelectionString = "Rock";
} else if (computerSelection == 2) {
computerSelectionString = "Paper";
} else if (computerSelection == 3) {
computerSelectionString = "Scissors";
} else if (computerSelection == 4) {
computerSelectionString = "Lizard";
} else {
computerSelectionString = "Spock";
}
Page orientation is determined in Microsoft Word from the __________ tab
Answers
Answer:
Page orientation is determined in Microsoft Word from the Page Layout tab.
Explanation:
The Page Layout Tab holds all the options that allow you to arrange your document pages just the way you want them. You can set margins, apply themes, control of page orientation and size, add sections and line breaks, display line numbers, and set paragraph indentation and lines.
What it takes to be a Graphic Designer and your interest
Do you plan to pursue or get certified?
150 words
Answers
Answer:
There are a few key steps to starting a career in graphic design: learn the principles of design, enroll in a graphic design course, practice graphic design tools, work on projects, and build your portfolio. … You will also need to master common graphic design tools, such as Photoshop, Illustrator and InDesign.
This portion of the question is up to you not me "Do you plan to pursue or get certified?"
Vijay enters into a contract to sell his laptop to Winnie. Winnie takes possession of the laptop as a minor and continues to use it well after reaching the age of majority. Winnie has a. expressly ratified the contract. b. impliedly ratified the contract. c. disaffirmed the contract. d. none of the choices.
Answers
Winnie, by continuing to use the laptop well after reaching the age of majority, has impliedly ratified the contract.
In this scenario, Winnie took possession of the laptop as a minor and continued to use it after reaching the age of majority. The question asks whether Winnie has expressly ratified the contract, impliedly ratified the contract, disaffirmed the contract, or none of the choices.
Express ratification occurs when a person explicitly states their intention to be bound by the terms of the contract. Implied ratification, on the other hand, occurs when a person's actions indicate their acceptance and affirmation of the contract. Disaffirmance refers to the act of rejecting or voiding the contract.
In Winnie's case, since she continued to use the laptop well after reaching the age of majority, it can be inferred that she has either expressly or impliedly ratified the contract. By using the laptop, she is demonstrating her acceptance and affirmation of the contract. Therefore, the correct answer is b. impliedly ratified the contract.
Learn more:About contract here:
https://brainly.com/question/2669219
#SPJ11
The correct answer is c. disaffirmed the contract.
When Winnie, as a minor, initially took possession of the laptop, she entered into a contract with Vijay. However, as a minor, she has the legal right to disaffirm or void the contract. Disaffirming a contract means that the minor chooses not to be bound by its terms and seeks to undo the legal obligations that arise from the contract.
In this scenario, Winnie continues to use the laptop well after reaching the age of majority. By doing so, she is implying her intention to disaffirm the contract. Implied ratification occurs when a person, upon reaching the age of majority, continues to perform under a contract made while they were a minor. In this case, Winnie's actions indicate that she does not wish to ratify or affirm the contract.
Express ratification, on the other hand, would occur if Winnie explicitly stated or signed a document indicating her intention to be bound by the contract after reaching the age of majority. However, there is no mention of such express ratification in the given scenario.
Therefore, the most appropriate option is c. disaffirmed the contract, as Winnie, upon reaching the age of majority, continues to use the laptop without explicitly ratifying the contract.
Learn more about
#SPJ11
it is the responsibility of a routing algorithm to determine the cost of an output link. group of answer choices true false
Answers
FALSE. The price of an output connection is something that a routing algorithm decides.
Algorithm: What is it?
An algorithm for sorting is one that arranges the items in a list, according to computer science. The two orders that are most frequently employed are lexicographical and numerical order, both in ascending or descending order. For other algorithms (including search and merger algorithms) which require input data to be in part of a sample, efficient sorting is crucial to maximizing their efficiency. Data canonicalization and the creation of output that is readable by humans both benefit greatly from sorting.
To know more about algorithm
https://brainly.com/question/24953880
#SPJ4
Please help!!
The following are two different images that are encoded using the same algorithm. The images are each in a 5 by 5 grid of pixels where each pixel is black, white, red, green or blue.
The image on the left gets encoded and compressed down to 21 digits while the image on the right gets compressed down to 25 digits. Although the same algorithm was used to encode and compress these images, why are the end results a different length?
The algorithm was probably used improperly in the image on the right, causing it to be a longer length than it should have been.
Because this is a lossy compression, sometimes information is lost during the compression.
The amount of size reduction from compression depends on the amount of redundancy in the original data.
The image on the right uses more colored squares and therefore requires more digits to represent the pixels.

Answers
Answer: The amount of size reduction from compression depends on the amount of redundancy in the original data.
The reason why the end results have a different length is because: C. The amount of size reduction from compression depends on the amount of redundancy in the original data.
What is a lossy compression?A lossy compression is also referred to as irreversible compression and it can be defined as a type of data encoding (data compression algorithm) in which the data in a file such as an image, is removed by using inexact approximations, in order to reduce the amount of size of a file after decompression.
Since the same algorithm was used to encode and compress these images, the reason why the resulting images have a different length is simply because the amount of size reduction from compression depends on the amount of redundancy in the original image file (data).
Read more on lossy compression here: https://brainly.com/question/17542014
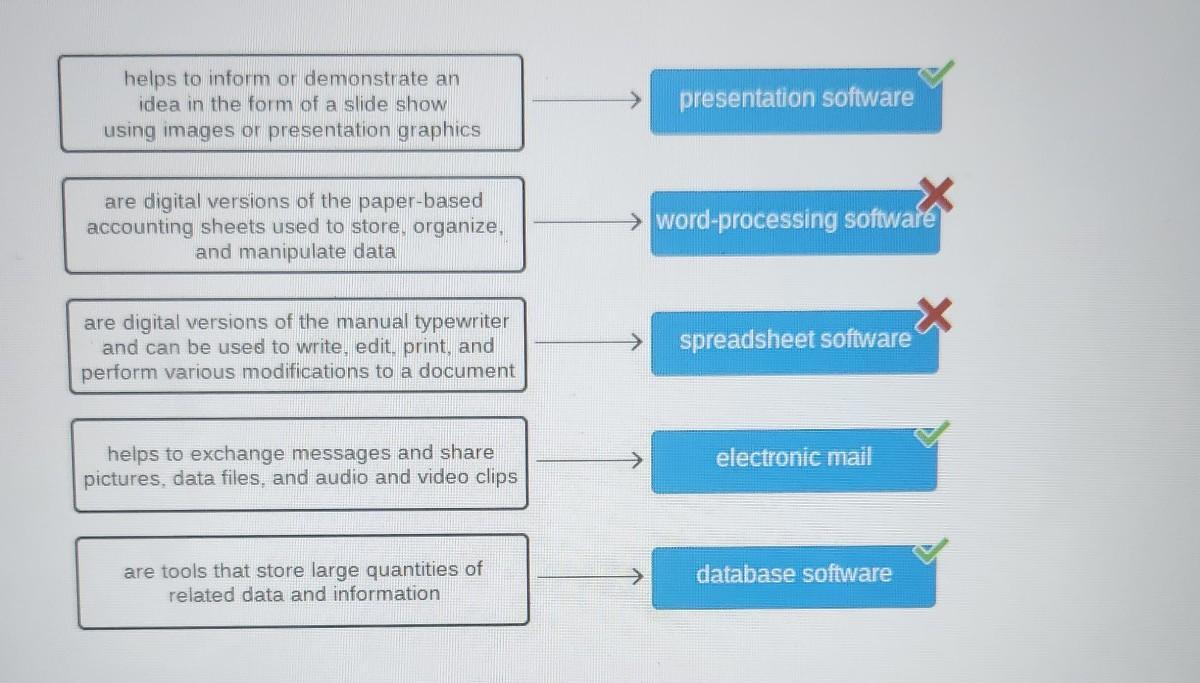
please help
match the features with the software
Word Processor, Spreadsheet, Database
- addiction of images, drawings, tables and graphics to text
- centralized data management
- data security
- digital version accounting sheets
- supports multiple users for adding data simultaneously
- visual representation of data
- digital version of a typewriter
Answers
Answer:
word processor- addition of images, drawing tables, and graphics to texts and digital version of a typewriter. spreadsheet- digital version of accounting sheets and visual representation of data. database- centralized data management, data security, and supports multiple users for adding data simultaneously
Just switch the two I got wrong and you'll get the correct answers. :)
Describe information technology (IT) someone helllpppp
Answers
Answer:
Describe information technology (IT) someone helllpppp
Explanation: :´(
Answer: information technology is the use of computers to store, retrieve, transmit, and manipulate data or information. IT is typically used within the context of business operations as opposed to personal or entertainment technologies. IT is considered to be a subset of information and communications technology.
Explanation:the term information technology in its modern sense first appeared in a 1958 article published in the Harvard Business Review; authors Harold J. Leavitt and Thomas L. Whisler commented that "the new technology does not yet have a single established name. We shall call it information technology (IT)." Their definition consists of three categories: techniques for processing, the application of statistical and mathematical methods to decision-making, and the simulation of higher-order thinking through computer programs.
Ned is trying to decide how he wants to connect the nodes on the network he created. What are the two options that he has?
Select one:
a through physical nearness or a central server
b. through hard cabling or wireless radio waves
c. through ethernet cables or Bluetooth
d. through software programs or osmosis
Answers
Since Ned is trying to decide how he wants to connect the nodes on the network he created, the two options that he has are option b and C:
b. Through hard cabling or wireless radio waves.
c. Through ethernet cables or Bluetooth.
What kind of cable does a computer system typically use to connect to a network?A twisted pair Ethernet cable called an Ethernet crossover is used to directly connect computing devices that would typically be connected through a network switch, Ethernet hub, or router, such as by connecting two personal computers together using their network adapters.
Note that a group of two or more interconnected nodes makes up a node network. Once a connection has been established between two or more nodes, all searches return lists of configured users and resources from both nearby and distant nodes. Every computer in the node network keeps track of this fundamental data.
Therefore, Through a link or communication channel, nodes are connected. A computer network may use cable, fiber, or both of these.
Learn more about ethernet from
https://brainly.com/question/28156384
#SPJ1
explain the importance of using onedrive in windows 10, and how knowledge of it will have an impact on today's workplace
Answers
Answer:
The importance of using Onedrive it helps save stuff if you have no more room on your computer it helps with schooling and works for jobs you have Microsoft Teams, Onedrive, Outlook, Office 365. It gives all sorts of things that you can use for anything contacts on Outlook and Teams.
This question is for programming in swift playground in learn to code 2 world creation the question is : how do you a lock that controls a platform to make it go up . I will give brainliest if your answer works please respond quickly
Answers
The most effective ways to lock that controls a platform to make it go up is by using a Good power words grab attention. If we used it and provoke a response, the audience reading will increase by placing them in crucial parts of your message.
In computer and technology, Swift Playgrounds generally can be defined as an educational tool and development environment for the Swift programming language developed by Apple Inc., Swift Playgrounds technology initially announced at the WWDC 2016 conference. There are several powerful words that can be used to attract someone, such as Evaluate, Formulate, Describe, Support, Trace, Analyze, Infer, Explain, Summarize, Compare, Contrast, and also Predict.
Here you can learn more about swift playground https://brainly.com/question/30270752
#SPJ1
If Jake wants to find out if the size of a fruit has any effect on the total sales for the week of that particular fruit, what chart should he use?
Answers
Answer:
XY scatter
Explanation:
XY (Scatter) maps plot two sequence of data as one set of XY coordinates. XY charts demonstrate the relationship between two sets of data. Each indicator is a piece of data. Each data set should have two types of information: its XY coordinate. XY charts are capable of having more than one set.
Takes a 3-letter String parameter. Returns true if the second and
third characters are “ix”
Python and using function
Answers
Answer:
def ix(s):
return s[1:3]=="ix"
Explanation:
Which three events occur when a DNS request is processed?
A. A local DNS server sends the IP address back to the requesting
device for access.
B. A local DNS server checks to see if it knows the IP address for the
site requested.
C. A subdomain DNS server defines how data will be transferred
over the internet.
D. Top-level domain DNS servers look up the site and return the IP
address.
Answers
The three events occur when a DNS request is processed is that
A local DNS server sends the IP address back to the requesting device for access. A local DNS server checks to see if it knows the IP address for the site requested.Top-level domain DNS servers look up the site and return the IP address.What are the types of DNS queries?There are known to be 3 types of DNS queries which are:
Recursive iterativenon-recursive.Therefore, The three events occur when a DNS request is processed is that
A local DNS server sends the IP address back to the requesting device for access. A local DNS server checks to see if it knows the IP address for the site requested.Top-level domain DNS servers look up the site and return the IP address.Learn more about DNS from
https://brainly.com/question/12465146
#SPJ1