Assume you have a page reference string for a process with E frames (initially all empty). The page reference string has length L with D distinct page numbers occurring in it. For any page-replacement algorithm, assuming pure demand paging, what would be the minimum number of page faults that could occur. a L/F b D c None of the others d L/D
Answers
The correct answer is (d) L/D, which implies that the minimum number of page faults is obtained by dividing the length of the page reference string, L, by the number of distinct pages, D. This gives an estimate of the minimum number of page faults that could occur for the given process with E frames.
The minimum number of page faults that could occur for any page-replacement algorithm, assuming pure demand paging, can be calculated using the Belady's Anomaly principle. According to this principle, it is possible to have more page faults with more number of frames allocated to a process.
Therefore, the minimum number of page faults that could occur for a process with E frames can be calculated by evaluating all possible page-reference strings of length L and counting the number of unique pages, D, in each string. The page reference string with the highest number of unique pages will result in the minimum number of page faults for the given process with E frames.
Hence, the correct answer is (d) L/D, which implies that the minimum number of page faults is obtained by dividing the length of the page reference string, L, by the number of distinct pages, D. This gives an estimate of the minimum number of page faults that could occur for the given process with E frames.
Learn more about replacement algorithm here:
https://brainly.com/question/31595854
#SPJ11
Related Questions
Describe each of the principal factors risk factors in
information systems projects (20 marks)
Answers
The principal risk factors in information systems projects encompass various aspects such as project complexity, technology challenges, organizational factors, and external influences.
These factors contribute to the potential risks and uncertainties associated with the successful implementation of information systems projects.
Project Complexity: Information systems projects can be inherently complex due to factors such as scope, scale, and the integration of multiple components. The complexity may arise from intricate business processes, diverse stakeholder requirements, or the need for extensive data management. Complex projects pose risks in terms of project management, resource allocation, and potential delays or cost overruns.
Technology Challenges: Information systems projects often involve implementing new technologies, software systems, or infrastructure. Technological risks include compatibility issues, scalability limitations, security vulnerabilities, and the need for specialized expertise. These challenges may impact the project timeline, functionality, and long-term viability of the system.
Organizational Factors: The success of an information systems project depends on organizational factors such as leadership, communication, and stakeholder engagement. Risks in this domain include lack of management support, insufficient user involvement, resistance to change, inadequate training, and poor project governance. Failure to address these factors can lead to user dissatisfaction, low adoption rates, and project failure.
External Influences: External factors, such as changes in regulatory requirements, market dynamics, or economic conditions, can introduce risks to information systems projects. These factors may necessitate modifications to project scope, increased compliance efforts, or adjustments to business strategies. Failure to anticipate and adapt to external influences can disrupt project timelines and impact the project's overall success.
Understanding and managing these principal risk factors is crucial for effective project planning, risk mitigation, and successful implementation of information systems projects. Proper risk assessment, contingency planning, stakeholder involvement, and ongoing monitoring are essential to minimize the impact of these risks and ensure project success.
Learn more about information systems here:
https://brainly.com/question/13081794
#SPJ11
which of the following intrusion detection and prevention systems uses fake resources to entice intruders by displaying a vulnerability, configuration flaw, or valuable data?
Answers
The intrusion detection and prevention systems use fake resources to entice intruders by displaying a vulnerability, configuration flaw, or valuable data is the honeypot
honeypot is a dedicated computer network that serves as just a decoy to draw cyberattacks. It acts as a phishing site for cybercriminals that takes advantage of the infiltration efforts to learn more about cyber criminals and how they operate or to divert them from those other targets.
Threats and attacks are drawn to honeypots because they are purposefully designed with security flaws. For example, a honeypot may have weak passwords or ports that react to port scans. To lure attackers into the honeypot environment instead of the more secure real network, susceptible ports may well be left open.
It is a resource for information that can assist you in understanding current hazards to the company and identifying the development of future ones. Security initiatives may be selected and concentrated with the help of the information obtained from the honeypot.
Your question is incomplete, most probably the full question was:
Which of the following intrusion detection and prevention systems use fake resources to entice intruders by displaying a vulnerability, configuration flaw, or valuable data?
- Botnet
- Honeypot
- Trojan horse
- Zombie
Learn more about honeypot here: https://brainly.com/question/17004996
#SPJ4
What is tools panel in adobe flash cs3?
Answers
Answer:
menu panel in flash that need to manipulate item on stage
Which of these are part of the five primary elements that make up a post-mortem report?
a. A summary
b. Backup procedures
c. A timeline
d. Resolution and recovery steps
e. A root cause description
f. Recommended future action items
Answers
Option a, c and d are correct. A summary, a timeline, resolution and recovery steps are part of the five primary elements that make up a post- mortem report.
A disaster recovery plan (DRP) is a written, organized strategy that outlines how a company can quickly restart operations following an unanticipated occurrence. A business continuity plan must include a disaster recovery plan.
It is used in relation to organizational components that are dependent on an effective information technology (IT) infrastructure. A disaster recovery plan seeks to assist an organization in resolving data loss and recovering system functioning so that it can function even if it functions at a low level following an incident.
The disaster preparedness strategy comprises of actions to lessen the consequences of a disaster so that the company can carry on with operations or swiftly restart mission-critical tasks. An study of business processes and continuity requirements is typically part of a DRP.
To know more about recovery click on the link:
https://brainly.com/question/1528638
#SPJ4
What is Inheritence in computer science? Explain in your won words with examples.
Answers
Answer:
Inheritance is when one class or script, inherits the properties and methods of another class. They can be re-used which makes it useful. This is why there are parent classes and child classes. Child classes inherit the properties of the parent class. An example is when a "car", "truck" are subclasses of a class called vehicle. Allowing you to make more vehicle using the same parent class.
Hope this makes sense!
what is excel in ibca
Answers
Answer:
Excel is mostly used for data storage. It also more or less has its own programming language within it for automation of data transfer and storage. It's used in a grid layout or what you'd see as a sheet.
I have taken IBCA (Intro to Business Computer Applications) but I'm surprised that you're taking excel in IBCA, perhaps just the basics I'm assuming. Completing IBCA should get you Microsoft certifications in Word and BCA will get you certifications in Powerpoint and Excel. If you pass of course.
YOOO CAN ANYONE SOLVE THIS IN JAVA??
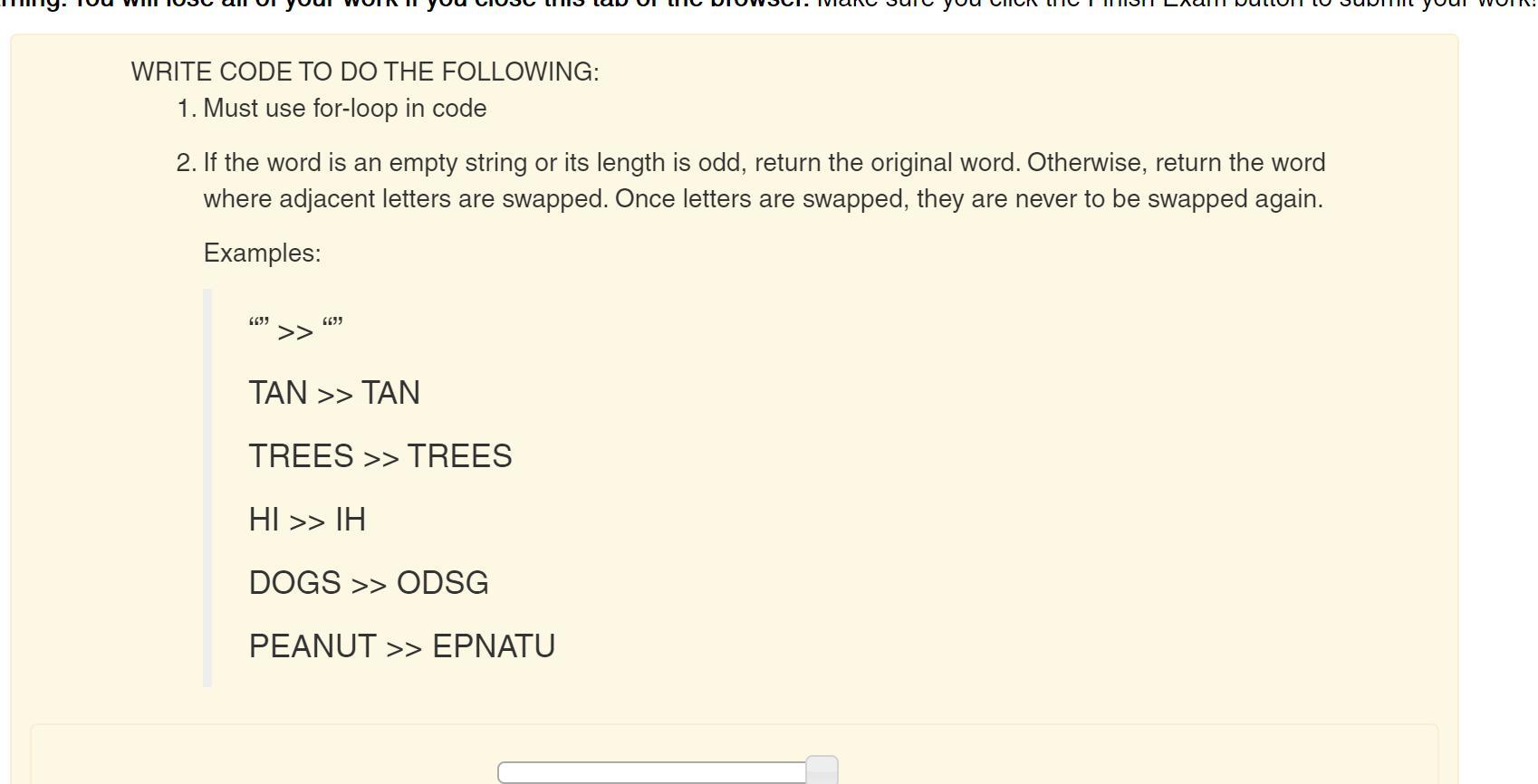
Answers
public class JavaApplication80 {
public static String swapLetters(String word){
char prevC = '_';
String newWord = "";
int count = 0;
if (word.length() % 2 == 1 || word.isBlank()){
return word;
}
else{
for (int i = 0; i<word.length(); i++){
char c = word.charAt(i);
if(count % 2 == 1){
newWord += (c +""+ prevC);
}
prevC = c;
count+=1;
}
}
return newWord;
}
public static void main(String[] args) {
System.out.println(swapLetters("peanut"));
}
}
This works for me. Best of luck.
Answer:
I do not know
Explanation:
What are the four types of technical drawing?
Answers
Answer:
3D drawings (isometric perspective)
exploded-view 3D drawings
complete working drawings
detail drawings (2D orthogonal projections)
diagrams
Programmers will write _________ as a framework from which to write formal code.

Answers
Answer:
pseudocode
Explanation:
Convert the following into binary system
and vice versa.
106
Answers
Write a program to input a number and check whether it is divisible by 5 or not
Answers
Answer:#include<stdio.h>
void main()
{
int a;
clrscr();
printf ("Enter the no.");
scanf("%d",&a);
if(a%5==0)
{
printf("No.is Divisible by 5");
}
else
{
printf("No is not Divisible by 5");
}
getch();
}
How many units are considered a full time student at a community college in California?
Answers
Answer:
12
Explanation:
According to Saddleback college located in California;
12 units are considered full-time student status.
You may take as little as 0.5 units or as many as 19.0 units during a single semester. To take more than 19 units you are required to obtain special permission from the Counseling Department.
give some examples where military needs have influenced technological development
Answers
Answer:
Satellite Systems,
Autonomous Vehicles
In your own words: 1. Briefly explain how to create a new folder in Drive and move files to a new folder. 2. Explain why folders are helpful to keep your Drive organized.
Answers
To create a new folder in Drive, you can follow these steps:
Click on the "New" button in the top left corner of the Drive interface.Select "Folder" from the dropdown menu.Name the folder and hit "Create."How to move files on DriveTo move files to the new folder, select the files you want to move by checking the boxes next to them.Click on the "Move to" button in the top menu bar and select the new folder from the list of options.Folders are helpful in keeping your Drive organized because they allow you to group related files together in a logical manner.
This makes it easier to find and access the files you need quickly, without having to search through all your files one by one.
Folders also make it simpler to share multiple files with others at once, as you can share an entire folder rather than selecting individual files.
Read more about folders here:
https://brainly.com/question/20262915
#SPJ1
Why are financial records important? How does keeping organized financial records contribute to successful money manageme?
Answers
Answer:
Financial records are very important for any organization. There are many reasons to keep records such as knowing financial situation, meeting tax obligations
Explanation:
Firstly is knowing the financial situation of the company which help to further contribute with organization.
Secondly organization meet the ta obligations assign by the government.
This is the question

Answers
Answer:
I dont know it sorry
Explanation:
i would help u
write the order of tasks that each person completes in order to make mashed potatoes in the shortest time. in order to format your answer, write the sequence of tasks each person does, with commas between tasks of one person, and semicolons between task lists of different people. for example, if you submit 0,1,2,4;3,5, person 0 will do tasks 0, 1, 2, and 4 (in that order), and person 1 will do tasks 3 and 5 (in that order). this will take 33 minutes total. you may add spaces, and order the task lists in any order. for example, the autograder will consider the above answer as equivalent to the submission 3,5;0,1,2,4 and the submission 0, 1, 2 ,4 ;3 ,5
Answers
To make mashed potatoes in the shortest time, the tasks can be divided among multiple people. Here is one possible distribution of tasks:
Person 1: Peel and chop potatoes, Boil water, Drain potatoes, Mash potatoesPerson 2: Set the table, Prepare butter and milk, Season mashed potatoe Person 3: Make gravy, Serve mashed potatoes and gravyThe sequence of tasks for each person can be represented as follows:Person 1: Peel and chop potatoes, Boil water, Drain potatoes, Mash potatoesPerson 2: Set the table, Prepare butter and milk, Season mashed potatoesPerson 3: Make gravy, Serve mashed potatoes and gravyNote: The order of the task lists can be rearranged, and spaces can be added for clarity. The autograder will consider answers with equivalent task sequences as correct.
To know more about tasks click the link below:
brainly.com/question/32317663
#SPJ11
how many primary partitions are supported on a gpt partitioned disk
Answers
A GPT partitioned disk can support up to 128 primary partitions.
A GPT (GUID Partition Table) is a partitioning scheme used on modern computer systems. It allows for a larger number of partitions and supports disks larger than 2 terabytes. In GPT, a disk can support up to 128 primary partitions.
However, it's important to note that most operating systems have limitations on the number of partitions they can recognize and use. For example, Windows supports up to 128 partitions, but only allows up to 4 primary partitions by default.
To create more than 4 primary partitions on a GPT disk in Windows, you would need to convert one of the primary partitions into an extended partition, which can then contain multiple logical partitions.
Learn more:About GPT partitioned disk here:
https://brainly.com/question/28236782
#SPJ11
A GPT partitioned disk can support up to 128 partitions. A primary partition is a partition that is utilized as a unique storage unit to operate an OS.
It can be utilized as a bootable partition and contains only one file system. A single hard drive partitioned with a GUID Partition Table (GPT) can support up to 128 partitions. The 128 partitions are split into three types:
Primary partitionExtended partitionLogical partitionA primary partition is one of the four partition types that can be established on a computer's hard drive. It is utilized to store the OS, device drivers, system utilities, and other programs required for the computer to boot up.
You can learn more about partitioned disks at: brainly.com/question/32172495
#SPJ11
7. According to the Value Proposition of Dataiku, Dataiku enables teams to centralize AI initiatives from data to impact so that they can accomplish these. (Choose three. )
Code applications that perform extraordinary tasks
Upskill business analysts with visual tools that empower them to work with data
Provide a single place for developing, testing, and putting projects into production
Unify business, data, and IT teams to work together on AI projects
Answers
Dataiku is a powerful platform that provides businesses with the ability to centralize AI initiatives from data to impact. This enables teams to work together and achieve their goals in a collaborative manner
.
The value proposition of Dataiku is based on three key areas, which include unifying business, data, and IT teams to work together on AI projects.The first area where Dataiku enables teams to work together is in unifying business teams. The platform provides a range of tools and features that allow business teams to work together and collaborate effectively. For example, the platform provides a centralized workspace where teams can access all the necessary data and tools needed to accomplish their objectives. This allows business teams to work together more efficiently and effectively, resulting in better outcomes.The second area where Dataiku enables teams to work together is in unifying data teams. The platform provides a range of features and tools that enable data teams to work together and collaborate effectively. For example, the platform provides a centralized data repository that enables data teams to access and share data more easily. This makes it easier for data teams to work together on projects and to achieve their objectives.Finally, the third area where Dataiku enables teams to work together is in unifying IT teams. The platform provides a range of features and tools that enable IT teams to work together and collaborate effectively. For example, the platform provides a centralized workspace where IT teams can access all the necessary data and tools needed to accomplish their objectives. This enables IT teams to work together more efficiently and effectively, resulting in better outcomes.
For such more questions on value proposition
https://brainly.com/question/14524046
#SPJ11
You have to insert the author's name at the bottom of all the pages of an article
prepared in the word processor. Which of the following tools is the most suitable
for this?
a) Footer
b) Merge Cells
c) Insert Rows
d) Header
Answers
Answer:
Footer
Explanation:
Which of the following types of printers are known as character/line printers?
a)Laser b)Inkjet c)Thermal d)Impact
Answers
The type of printer that is known as a character/line printer is impact printer. Option D is correct.
Impact printers are known as character/line printers because they work by striking a print head against an ink ribbon, creating a character or line impression on the paper. This technology is different from other types of printers, such as laser or inkjet printers, which use a different process to create an image on the paper.
Impact printers are commonly used for printing forms, receipts, invoices, and other documents that require multiple copies or carbon copies. They can print in a variety of fonts and sizes, and are generally durable and reliable.
Therefore, option D is correct.
Learn more about printer https://brainly.com/question/12648081
#SPJ11
They removed my other post but I didn't learn my lesson :)
Unblocked web proxy services:
Latest(dot)cf
If that doesn't work then go to
securly(dot)fail
the dot=. So uhm yea. Wont let me put links but its ok :) hope this helps you.
(Games directory is currently down, working on the rammerhead proxy)
Answers
Answer:
thank you so much I'm so bored in class
Explanation:
When code is compiled it?
Answers
Answer:
To transform a program written in a high-level programming language from source code into object code. The first step is to pass the source code through a compiler, which translates the high-level language instructionsinto object code.
Answer: Compiled code is a set of files that must be linked together and with one master list of steps in order for it to run as a program.
Explanation: This is opposed to a interpreted code like web scripts, host server scripts and BASIC that are run one line at a time.
Hope this helps! :)
To qualify as a professional Android developer, you need to get _____
certification.
Answers
Answer:
proficiency
Explanation:
Commercials, movie trailers, or the backs of books are used to try to persuade us by using a special kind of personal experience saying that a given product is good or bad. This type of evidence is called?
Answers
Commercials, movie trailers, and the backs of books are examples of persuasive texts. These texts are intended to persuade the reader or viewer to take a certain action or buy a specific product.
They do this by using a variety of persuasive techniques, including using personal experiences that imply the product is good or bad.This type of evidence is called anecdotal evidence. It is based on personal experiences or individual cases and may not be reliable. Anecdotal evidence may be biased or unrepresentative of the whole population, making it difficult to draw generalizations or make predictions about how others will react to the product.
Therefore, it is important to consider the source of the information and the context in which it is presented when evaluating the reliability of anecdotal evidence. Overall, while personal experiences can be powerful tools for persuasion, they should be used with caution and complemented with more rigorous forms of evidence to support their claims.
To know more about product visit:
https://brainly.com/question/31815585
#SPJ11
hi pls help me how to connect my imac to our wifi cause it’s not showing the wifi option (use pic for reference)

Answers
Select the correct answer.
Linda is making handouts for her upcoming presentation. She wants the handouts to be comprehensible to people who do not attend her
presentation. Which practice should Linda follow to achieve this goal?
OA.
OB.
OC.
OD.
provide a summary of the presentation
make the handouts more image-oriented
speak in detail about each topic
provide onlya printout of the slideshow
Can someone please help me with this class b4 I lose my mind
Amos: xoxo_11n
Answers
Answer:
OA
Explanation:
I took this quiz
What do you like least about coding in python?
Answers
tle electrical instulation maintance
1.what is inventory 2. what is job order 3. what is barrow form 4. what is purchase request
Answers
Inventory refers to the process of keeping track of all materials and equipment used in electrical insulation maintenance. A job order is a document that contains all the information necessary to complete a specific maintenance task.
Definition of the aforementioned questions1) Inventory refers to the process of keeping track of all materials and equipment used in electrical insulation maintenance. This includes maintaining a list of all the items in stock, monitoring their usage, and ensuring that there are enough supplies to meet the demands of the job.
2) A job order is a document that contains all the information necessary to complete a specific maintenance task. This includes details about the task, such as the materials and tools required, the location of the work, and any safety considerations.
3) A barrow form is a document used to request materials or equipment from the inventory. It contains details about the requested item, including the quantity, the purpose of the request, and the name of the person or team making the request. The form is usually signed by an authorized person and submitted to the inventory manager or other appropriate personnel.
4) A purchase request is a document used to initiate the process of purchasing new materials or equipment for the electrical insulation maintenance program. It contains details about the item to be purchased, including the quantity, the cost, and the vendor or supplier. The purchase request is typically reviewed and approved by a supervisor or manager before the purchase is made.
learn more about electrical insulation maintenance at https://brainly.com/question/28631676
#SPJ1
You invited your product owner to the upcoming iteration retrospective. She thanked you for the invitation and told you that she would look forward to the session and would like to adopt good ideas. Which ESVP role closely relates to this attitude?
Answers
The ESVP role that closely relates to the attitude of the product owner in this scenario is "S" - Supporter. In the ESVP model, which stands for Expert, Supporter, Visionary, and Pragmatist,
the Supporter role is characterized by a positive attitude towards change and a willingness to adopt new ideas or approaches. Supporter individuals are typically open-minded, cooperative, and willing to collaborate with others to achieve team goals.
In this scenario, the product owner's response of thanking for the invitation, expressing a positive attitude towards the upcoming iteration retrospective, and mentioning a willingness to adopt good ideas aligns with the characteristics of a Supporter role in the ESVP model. The product owner's openness and willingness to embrace new ideas and collaborate with the team during the retrospective reflect a supportive and cooperative mindset towards the agile team's improvement efforts.
Learn more about product owner here:
https://brainly.com/question/16412628
#SPJ11