Arviz purchases a copy of Word Sample 7.0 software, the newest version of the word processing program he normally uses. Ravitz wants to share a copy of the software with his friends Kim and Carrie, but the program was designed to only be copied once. Ravitz is a decent programmer, so after spending a little time with the program, Ravitz learns how to bypass the code that only allows the program to be copied once. Arvitz then makes copies of the program and gives these copies to Kim and Carrie. By copying the word processing program and giving the program to his friends, Arvitz has violated:
Answers
Answer:
programmer" (and any subsequent words) was ignored because we limit queries to 32 words.
By copying the word processing software program and giving it to his friends, Arvitz has violated: the Digital Millennium Copyright Act (DMCA).
Globally, there are three (3) main ways to protect an intellectual property (IP) and these include:
TrademarksPatentsCopyright lawA copyright law can be defined as a set of formal rules that are granted by a government to protect an intellectual property (IP) by granting the owner an exclusive right to use it, while preventing any unauthorized access, use or duplication (copying) by others.
The Digital Millennium Copyright Act (DMCA) is a universal copyright law which protects and regulates the sharing and downloading rights of digital media such as music, books, software programs, etc.
In conclusion, Arvitz violated the Digital Millennium Copyright Act (DMCA) by copying the word processing software program and giving it to his friends Kim and Carrie.
Read more on copyright law here: https://brainly.com/question/1078532
Related Questions
As a photographer, what will be the driving force behind everything that you produce?
Answers
Explanation:
What is Photography?
Photography is basically an art of generating the pictures by the reaction of the light and radiant energy on the specific surface.
It is also a science of creating a long-lasting image by capturing the light, which can be done in either of the ways, such as chemically or electronically using a light-sensitive substance like photographic film or an image sensor.
It is the power of the vision through which the photographer is able to produce the perfect and beautiful pictures of any object or the human beings.
Therefore, it can be concluded that The photographer's vision serves as the inspiration for all he creates. Hence, option
Answer:
It your vision :)
Explanation:
have a nice day
how do we add questions on sam Blockly?
Answers
Answer:
I do not know that answer
please help me with computing!
the question is:
solve the following algorithm in pseudocode "the algorithm is required to prepare a teacher's payroll. For them, the hours worked and the price per hour are taken into account. place the input data and the output data.
Answers
Answer:
ok i help
Explanation:
Which of the following describes a type of view that is based on a subquery that retrieves or derives data from one or more tables, and may also contain functions or grouped data?A - simple viewB - complex viewC - inline viewD - "TOP-N" analysis
Answers
The type of view described in the question is referred to as an "inline view" (option C).
An inline view is a type of view in a database that is based on a subquery. It retrieves or derives data from one or more tables and may also include functions or grouped data. An inline view is typically used within a larger SQL statement and acts as a temporary table or virtual table. The subquery in the inline view is executed first, generating a result set, which is then used in the main query. The inline view allows for complex calculations, filtering, or data transformations to be performed before being combined with other data in the main query.
This type of view is different from a simple view (option A), which is a named query that is stored in the database and can be used like a table. Complex views (option B) refer to views that involve multiple tables or more intricate SQL logic. "TOP-N" analysis (option D) is a technique used to retrieve a specified number (N) of rows with the highest or lowest values in a query result. Therefore, the correct answer for the described type of view is option C - inline view.
Learn more about query here: https://brainly.com/question/32137119
#SPJ11
¿Quién recibe la orden de ejecución de un programa enviada por el usuario?
Answers
Answer:
El sistema operativo.
Explanation:
En ciencias de la computación, una orden es una instrucción a un sistema operativo de computadora para realizar una tarea específica. Generalmente, una orden se emite a través de una interfaz de línea de órdenes de otro programa. Así, se trata de una instrucción a un programa de computadora para que actúe como intérprete para resolver un problema.
Por ejemplo, podemos pedir a través de una orden que muestre el contenido de una carpeta, buscar un archivo en particular y especificar mediante parámetros adicionales cómo se debe realizar esta acción (por ejemplo, utilizando expresiones regulares para realizar una búsqueda).
Write multiple if statements:
If car_year is before 1967, print "Probably has few safety features. " (without quotes).
If after 1970, print "Probably has seat belts. ".
If after 1990, print "Probably has electronic stability control. ".
If after 2002, print "Probably has tire-pressure monitor. ".
End each phrase with period and newline. Remember that print() automatically adds a newline.
Ex: car_year = 1995 prints:
Probably has seat belts.
Probably has electronic stability control
Answers
Here is an example of using multiple if statements based on the car_year variable:
python
Copy code
if car_year < 1967:
print("Probably has few safety features.")
if car_year > 1970:
print("Probably has seat belts.")
if car_year > 1990:
print("Probably has electronic stability control.")
if car_year > 2002:
print("Probably has tire-pressure monitor.")
Note that the conditions are checked sequentially, so if a car's year meets multiple conditions, all corresponding statements will be executed.
learn more about statements here :
https://brainly.com/question/2285414
#SPJ11
smart tv has _____ intergrated with it
Answers
Answer:
an operating system
Explanation:
Company B is setting up commercial printing services on their network. Which of these are advantages of centrally managed commercial printers? Check all that apply.
Answers
Answer:
Centralized management of printing activities, allowing administrators to manage all print devices using a network.
Explanation:
The advantages of centrally managed commercial printers are:
Printers can be easily created and deployed in virtual sessions such as Citrix or VMwareCentralized management of printing activities, allowing administrators to manage all print devices using a network.Reduces the number of printer related issues thereby increasing productivity.It provides a way of keeping record those who are printing and what have been printerAll print related jobs can be easily managed from a central controlled network.Increased security as a print server allows you to total control over who can print what and where High availability and redundancy due to pooling of printers Easily customize printer profileIs there an equivalent notion of header information that is added to passengers and baggage as they move down the airline protocol stack?
Answers
With reference to airline industry, they use tags that holds information on passenger's name, destination and flight number for identification.
What is the equivalent notion of header information that is added to passengers and baggage as they move down the airline protocol stackIn the context of the airline industry, there is a similar concept to header information called baggage tags, which are attached to each checked bag as it moves through the airline's handling process. These tags contain information such as the passenger's name, flight number, destination, and a unique identifying number for the bag. This information is used to track the bag's location and ensure that it is loaded onto the correct flight and delivered to the correct destination. Similarly, passengers are assigned boarding passes, which contain information such as the passenger's name, flight number, seat assignment, and departure gate. This information is used to manage passenger flow through the airport and onto the correct flight. So, while the exact terminology may differ, the concept of adding identifying information to passengers and baggage as they move through the airline protocol stack is an essential aspect of airline operations.
Learn more on airline industry here;
https://brainly.com/question/28147456
#SPJ1
why does low air pressure usually indicate bad weather?
Answers
Areas with high pressure typically have calm, fair weather. Areas with low pressure have comparatively thin atmospheres.
Why does poor weather typically signal low air pressure?Low pressure causes active weather. The atmosphere becomes unstable when the air rises since it is lighter than the surrounding air masses. When the air pressure increases, water vapor in the air condenses, creating clouds and rain, among other things. Both severe weather and active weather, such as wind and rain, are brought on by low pressure systems.
What type of weather lowers air pressure?Low-pressure areas are typically associated with bad weather, while high-pressure areas are associated with calmer winds and clear skies (such as cloudy, windy, with potential for rain or storms).
To know more about low air pressure visit:-
https://brainly.com/question/2194071
#SPJ4
20) which one of the following statements is not true? a) the internet backbone is owned by the federal government in the united states. b) icann manages the domain name system. c) the iab establishes the overall structure of the internet. d) the internet must conform to laws where it operates. e) w3c determines programming standards for the internet.
Answers
The statement that the internet backbone is owned by the federal government in the United States is not true. In fact, the internet backbone is owned by multiple Tier 1 ISPs around the world. No one owns the whole internet backbone and the internet itself is free for everyone.
The internet backboneThe internet is a global network of computers. Its core is the internet backbone, the largest and fastest network linked together with fiber-optic cables around the world. The traffic of the global internet runs here connecting all locations around the globe. This backbone infrastructure is owned by multiple ISP companies.
Learn more about the internet https://brainly.com/question/2780939
#SPJ4
Write a while loop that prints the first 16 numbers of the pattern: 1, 4, 9, 16, 25
Answers
Answer:
Explanation:
the pattern is increasing squared number. 1^2, 2^2, 3^2, 4^2, 5^2
int i=1;
while (i<=16) {
Print i^2;
i++;
}
could anyone tell me how to solve this? ty

Answers
Based on the information, the output of the program is 54314 because the string S is "1279". The correct option is A.
How to explain the informationThe first line initializes the variables ans and S. ans is a string that will store the output of the program, and S is the string that we will be processing.
The second line starts the outer loop. The outer loop iterates over the characters in S from right to left, in steps of 3. For example, if S is "1279", then the outer loop will iterate over the characters "9", "7", and "1".
In this case, the output of the program is 54314 because the string S is "1279". The first substring is "9", the second substring is "79", and the third substring is "1279". The values of these substrings are 9, 133, and 2207, respectively. When these values are added together, the result is 54314.
Learn more about program on
https://brainly.com/question/26642771
#SPJ1
Which instructor lives on Webster Avenue?
a. Vicki Pegues
b. Neda Tahan
c. Memo Said
d. Luke Lane
Answers
Answer:
The instructor who lives on Webster Avenue is Vicki Pegues
The instructor who lives on Webster Avenue is option A: Vicki Pegues
What is the instructorAn instructor is someone who teaches and guides people in a specific subject or field. In schools, colleges, or universities, an instructor is the person who teaches courses or leads classes. They can be a teacher, professor, or educator. They are very important in helping students learn, teaching them new things, and helping them with their school work.
Instructors can be skilled in different subjects like math, science, languages, humanities, arts, and job-related topics.
Therefore, option A is correct.
Read more about instructor here:
https://brainly.com/question/22596721
#SPJ2
On which tab are the print commands in Excel 2016 accessed?
Home
File (Backstage)
View
Edit
Answers
Answer:
file (backstage)
Explanation:
edginuity 2020
The tab that is the print commands in Excel 2016 accessed is File (Backstage). The correct option is b.
What is Excel?Microsoft produced Microsoft Excel, a spreadsheet, for Windows, macOS, Android, and iOS. It has calculation, graphing tools, pivot tables, and Visual Basic for Applications, a macro programming language. Microsoft created a spreadsheet for it.
It has calculation, graphing tools, pivot tables, and Visual Basic for Applications, a macro programming language. A spreadsheet application that is a part of the Microsoft Office suite of programs. Spreadsheets display value tables arranged in rows and columns that can be mathematically manipulated using both fundamental and sophisticated functions.
Therefore, the correct option is b. File (Backstage).
To learn more about Excel, refer to the link:
https://brainly.com/question/24202382
#SPJ5
Give 3 features and uses of
Desktop
laptop
palmtop computer
Answers
Answer:
A Palmtop or hand-held personal computer is small enough to hold in one hand and operate with the other. Also called a handtop, these ultra-small computers may have specialized keyboards or keypads for data entry applications or have small qwerty keyboards.
• Palmtops are also called PDAs, hand-held computers and pocket computers.
• Palmtop or hand-held personal computer, lightweight, small, battery-powered, general-purpose programmable computer. It typically has a miniaturized full-function, typewriter like keyboard for input and a small, full color, liquid-crystal display for output. In addition to an operating system that is compatible with that of a desktop computer, a palmtop will typically contain a word processor, a spreadsheet program, and a calendar and phone book. A variety of other programs can be loaded and executed, and data can usually be transferred to and from a desktop computer. Although some palmtops are like personal digital assistants in that they accept handwritten or touch screen input, they generally differ in that the palmtop has more memory, a keyboard, and a greater variety of available programs.
Explanation:
Convert the following EBNF grammar rules to BNF. Remove all EBNF symbols. Avoid left recursion. Your answer will be graded on both correctness and simplicity.
A → B {(x|y) B}
B → w[z]
Hint: Both new A-rules and B-rules will have multiple RHSs
Answers
Converted forms of the EBNF grammar rules to BNF are:
A → B CA → BB → w DB → wC → x BC → y BD → εD → zWhat are EBNF symbols?EBNF stands for Extended Backus-Naur Form, which is a metalanguage used to describe the syntax of a programming language or other formal language. EBNF symbols are the notation used in EBNF to describe the syntax of a language.
Some common EBNF symbols include: Terminal symbols, Nonterminal symbols, Concatenation, Alternation, Optional symbols, Repetition symbols.
Find out more on EBNF symbols here: https://brainly.com/question/30805088
#SPJ4
Plotting in MATLAB
Use the code below to generate 4 arrays in Matlab, x1, y1, x2, y2
Generate 10 random numbers
x1 = 1:10;
y1 = round (100*rand (1, numel (x1)));
Generate interpolated data step= 100;
x2 = 0:1/step: max (x1);
y2 = spline (x1,y1,x2);
Design Goal: Plot both data sets in the same figure
(1) Generate a new figure with a grid
(2) Plot y1 vs x1 in BLUE, with LINEWIDTH 3 (x1 is on the x-axis, y1 is on the y-axis) (3) Plot y2 vs x2 in RED, with LINEWIDTH 2 (x2 is on the x-axis, y2 is on the y-axis) (4) Add a legend: Raw Data, Spline Fit Data
Submit: Submit a copy of your code and the plot AND the list of the ten numbers YOUR copy of Matlab produces that you use in the spline function (meaning, also provide as a list of numbers your y1 array)
Answers
The provided MATLAB code generates the required arrays and plot, and it also displays the list of ten random numbers used in the spline function.
Here's the MATLAB code to generate the arrays x1, y1, x2, and y2 as described:
% Generate 10 random numbers
numbers = randi([1, 100], 1, 10);
% Generate x1 and y1
x1 = 1:10;
y1 = round(numbers);
% Generate interpolated data
step = 100;
x2 = 0:1/step:max(x1);
y2 = spline(x1, y1, x2);
% Plotting
figure;
grid on;
hold on;
plot(x1, y1, 'b', 'LineWidth', 3);
plot(x2, y2, 'r', 'LineWidth', 2);
legend('Raw Data', 'Spline Fit Data');
xlabel('x-axis');
ylabel('y-axis');
title('Raw Data and Spline Fit');
% Display the generated numbers used in y1
disp('Numbers used in y1:');
disp(numbers);
Explanation:
The code generates 10 random numbers using the randi function and stores them in the variable numbers.
The arrays x1 and y1 are generated, where x1 contains the values from 1 to 10, and y1 is obtained by rounding the generated random numbers.
The interpolated data is generated by using the spline function with x1, y1, and x2. x2 is created with a step size of 1/step from 0 to the maximum value in x1.
A new figure is created, the grid is turned on, and both data sets are plotted on the same figure. The raw data is plotted in blue with a linewidth of 3, and the spline fit data is plotted in red with a linewidth of 2.
A legend is added to the plot, labeling the two data sets.
x-axis and y-axis labels are added, and a title is given to the plot.
The generated numbers used in y1 are displayed.
To know more about MATLAB code visit :
https://brainly.com/question/31502933
#SPJ11
What is the starting and ending address of the segment located by the segment register value, 1000H?a. 10FFFH, FFFFFHb. 10000H, 10FFFHc. 01000H, 01FFFHd. 10000H, 1FFFFH
Answers
The starting and ending address of the segment located by the segment register value, 1000H is 10000H, 1FFFFH. The correct option is d.
What is resistor?The smallest data storage components that are part of the CPU itself are called registers. These are the memory areas that the processor can access right away.
It could contain a storage address, an instruction, or any sort of data, like a series of bits or a single character.
Memories called registers are found inside the Central Processing Unit (CPU). A register normally has less than 64 bits in capacity, and they are both low in number (there are very rarely more than 64 registers).
The segment's starting and ending addresses are 10000H, 1FFFFH, which may be found by using the segment register value 1000H.
Thus, the correct option is d.
For more details regarding resistor, visit:
https://brainly.com/question/24297401
#SPJ1
The owner of an organic pet food store would like to analyze the sales data to determine if the
business is growing, declining or remaining flat. The owner has the following data:
Sales Revenue Last Year = $350,000
Sales Revenue Current Year = $402,500
What is the sales growth?
0000
13%
10%
15%
17%
Answers
Answer:
Growth sales 15%
Explanation:
Let's make a proportion:
$350,000 - 100%
$402,500 - X%
X = $402,500 * 100% / $350,000 ≈ 115%
Growth sales:
115% - 100% = 15%
10. The technology used to weave patterns into cloth inspired the future creation of computer data storage and retrieval
True or false?!
Answers
Write a method mirror that accepts an ArrayList of Strings as a parameter and produces a mirrored copy of the list as output, with the original values followed by those same values in the opposite order. For example, if an ArrayList variable called list contains the values ["a", "b", "c"], after a call of mirror(list); it should contain ["a", "b", "c", "c", "b", "a"].
Answers
Answer:
Here is the JAVA program:
private static void mirror(ArrayList<String> list) { // method mirror that accepts ArrayList of Strings as a parameter
for (int i = list.size() - 1; i >= 0; i--) {//iterates through the array list
list.add(list.get(i)); } //produces a mirrored copy of the list
System.out.println(list); } ///prints the mirrored copy of list
Explanation:
This is the complete program:
import java.util.ArrayList; //to use dynamic arrays
public class MirroredArraylist{
private static void mirror(ArrayList<String> list) { //method to produce mirrored copy of the list
for (int i = list.size() - 1; i >= 0; i--) { /
list.add(list.get(i)); }
System.out.println(list); }
public static void main(String[] args) {
ArrayList<String> list = new ArrayList<String>();//creates a String type array list
//adds values to the Arraylist i.e list
list.add("a"); .
list.add("b");
list.add("c");
mirror(list); }} //calss mirror method passing list to it
The method works as follows:
For loop variable i is initialized to the list.size() - 1 which means 1 less than the size of the ArrayList i.e list. For example the list contains the following values ["a", "b", "c"]. So
i = list.size() - 1
= 3-1
i = 2
so i is set to the last element/value of list i.e. "c"
Then the for loop checks if the value of i is greater than or equals to 0 which is true because i = 2
So the program control enters the body of the for loop
list.add(list.get(i)); This statement has two methods; add() and get()
add() method is used to add the value/element to the ArrayList, list.
get() method is used to get the element/value in list at i-th index
So the element at i=2 means element at 2nd index is "c"
Hence value "c" is added to the list.
Then the value of i is decremented to 1. So i=1
At next iteration
i is set to the second last element/value of list i.e. "b"
Then the for loop checks if the value of i is greater than or equals to 0 which is true because i = 1
So the program control enters the body of the for loop and gets the value of list i.e "b" and adds it to the list. Next the value of "a" is get and added to the list. So the list becomes:
["c", "b", "a"]
In the main() method
list.add("a"); .
list.add("b");
list.add("c");
The above three statements adds the values to list that are "a", "b" and "c". So the list becomes:
["a", "b", "c"]
Next statement mirror(list); calls the method mirror which returns the mirrored copy of the list. So the output is:
["a", "b", "c", "c", "b", "a"].
The screen shot of the program along with its output is attached.

A _____ key is defined as a key that is used strictly for data retrieval purposes.
Answers
A secondary key is defined as a key that is used strictly for data retrieval purposes.
Secondary data is data obtained from the results of previous studies. Generally, this type of data has information in the form of "referenced, quoted, or reported". This proves if the researcher does not get the data obtained from the main source.
Key Types in Relational Databases
In relational method, there are 6 known keys which will be explained as follows:
Candidate Key, one of a series that has a unique value to distinguish or identify.Primary Key, attribute Is a candidate key that has been selected to uniquely identify each record.Alternate key, Unselected candidate key.Foreign Key, a collection of fields in one relation that is used to "refer" (point) to a row (tuple) in another relation (must correspond to the primary key in the second relation).Secondary key, an attribute or combination used only for data retrieval purposes.Composite key, a key consisting of 2 or more attributes that uniquely identify an entity occurrence.You can learn more about Relational Databases here https://brainly.com/question/13262352
#SPJ4
Help pweeze this is due today :(
I will give u brainliest just pweeze, I need this answer :(
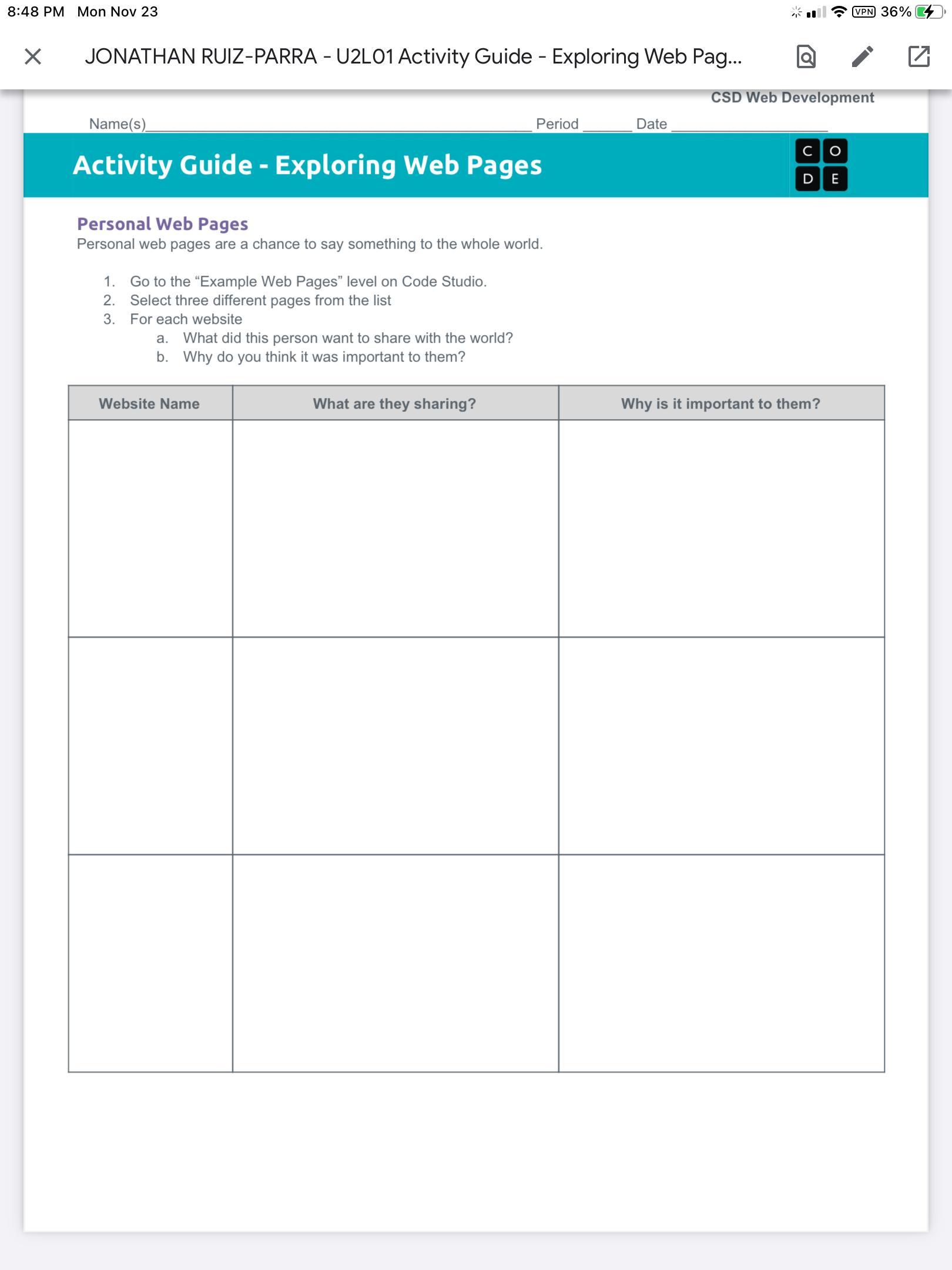
Answers
Answer:
just go in a website and see why important to them
Explanation:
and why the share with more people
Create a template of a change request form. What sections did you include and why?
Answers
According to the information some sections included in the change request form: Request Information, Description of Change, Impact Analysis, Proposed Solution, Benefits of the Change, Cost Estimate, Approval and Authorization, etc---Cttachments, etc...
What secctions do we include and why?Request Information: This section collects essential details such as the project name, change request number, date, requestor's information, and contact details for easy identification and communication.Description of Change: This section provides a clear and detailed description of the requested change, including the reasons behind it and any relevant background information. Impact Analysis: This section assesses and documents the potential impact of the change on various project aspects, suc´+Proposed Solution: Here, the proposed solution to address the requested change is described, along with any alternative options considered.Benefits of the Change: This section highlights the anticipated benefits or advantages that the change will bring to the project. It helps stakeholders evaluate the value and potential positive outcomes associated with the change.Cost Estimate: This section provides an estimate of the costs associated with implementing the change. It includes financial costs, resource requirements, and any additional expenses. Approval and Authorization: In this section, the approval process for the change request is outlined. It specifies the individuals or roles responsible for reviewing and approving the request. It also provides space for authorized signatures and dates to formalize the approval process.Attachments: This section lists any supporting documents or files that are relevant to the change request. It allows stakeholders to attach additional information, such as diagrams, specifications, or previous discussions, to provide a comprehensive understanding of the change.Review and Evaluation: This section provides space for project stakeholders or change control board members to review and evaluate the change request. Change Request Status: This section helps track the status of the change request, including submission date, review dates, approval status, and implementation status.Learn more about template in: https://brainly.com/question/13566912
SPJ4
you are assigned the task of reviewing incoming and outgoing traffic on a windows server that has been reported as sluggish. there are no servers or appliances on the segment that can capture the traffic to the machine, so you will run your own tool. which tool will provide you with live data, showing connections, ports, protocols, and volume of traffic similar to the image below?
Answers
To analyze incoming and outgoing traffic on a Windows server that has been reported as sluggish, you can use the built-in tool called "Resource Monitor." This tool provides live data, showing connections, ports, protocols, and volume of traffic, which will help you identify potential issues with appliances or other connections causing the sluggish performance. You can access Resource Monitor by typing "resmon" in the Windows search bar or by opening Task Manager and clicking on the "Performance" tab, then selecting "Open Resource Monitor."
the tool that can provide you with live data, showing connections, ports, protocols, and volume of traffic is likely a network traffic analyzer or packet sniffer. These tools capture network packets in real-time and provide detailed information about the network traffic.
One commonly used network traffic analyzer for Windows servers is Wireshark. Wireshark allows you to capture and analyze network packets, providing you with insights into the traffic patterns, protocols, ports, and volumes. It offers a graphical user interface (GUI) that displays the captured data in a detailed and customizable manner, allowing you to diagnose and troubleshoot network-related issues.
By using Wireshark or a similar network traffic analyzer, you can monitor the incoming and outgoing traffic on the Windows server, identify any anomalies or potential causes of sluggishness, and take appropriate actions to optimize the server's performance.
Learn more about Windows server click here:
brainly.in/question/54963857
#SPJ11
__________, a level beyond vulnerability testing, is a set of security tests and evaluations that simulate attacks by a malicious external source (hacker).
Answers
According to security evaluation, Penetration testing is a level beyond vulnerability testing, a set of security tests and evaluations that simulate attacks by a malicious external source (hacker).
Penetration testing is often considered or described as ethical hacking. It involves the process of securing a firm or organization's cyber defenses.
The process of penetration testing or security testing includes assessing for exploitable vulnerabilities in networks, web apps, and user security.
Hence, in this case, it is concluded that the correct answer is Penetration testing.
Learn more about penetration testing here: https://brainly.com/question/13137421
Put the following numbers in order from greatest to least: 15 0 -11 45 -37.
A. 45,15,0,-11 -37
B. 45, -37, 15, -11, 0
C. -11, -37, 0, 15, 45
D.45, 15, 0, -37, -11
PLEASE HELP ME I NEED TO DO IT NOW
Answers
Answer:
A
Explanation:
The smallest number is -37 and the largest is 45
even if you perform regular backups, what must be done to ensure that you are protected against data loss? answer restrict restoration privileges to system administrators. configure system maintenance to automatically defragment system hard drives every night. write-protect all backup media. regularly test restoration procedure
Answers
Regularly test restoration procedures to ensure they work effectively and efficiently, as well as restrict restoration privileges to system administrators, write-protect backup media, and configure automatic system maintenance to defragment hard drives every night.
Regularly testing restoration procedures ensures that in case of data loss, the recovery process is efficient and effective. Restricting restoration privileges to system administrators prevents unauthorized access to backed-up data. Write-protecting backup media prevents accidental or intentional alteration of backed-up data. Configuring automatic system maintenance to defragment hard drives every night ensures optimal performance and reduces the risk of data loss due to disk errors. These measures, when combined with regular backups, provide a comprehensive approach to data protection.
learn more about hard drives here:
https://brainly.com/question/10677358
#SPJ11
name two different colors used in the python program file window.name the type of program content that has each color ......
whoever answer this correct i will rate them 5 stars and a like .....
please urgent
Answers
In the Python program window, black is used for code and syntax, while white is used as the background.
How is this so?1. Black - The color black is typically used for the program's code and syntax. It represents the actual Python code and includes keywords, functions, variables, and other programming constructs.
2. White - The color white is commonly used as the background color in the program window. It provides a clean and neutral backdrop for the code and makes it easier to read and understand.
Learn more about python program at:
https://brainly.com/question/26497128
#SPJ1