again, only 2 people may answer this c:
Answers
Answer:
Sup
Explanation:
Related Questions
A switch operates in the OSI reference model __________ layer and uses the __________ address to forward packets.
Answers
Answer:
A switch operates in the OSI reference model data link layer and uses the MAC address to forward packets
Explanation:
A network switch used in wired physical network connection, has several ports and acts as the bridge in the network of computing devices with a port naming system based on MAC addresses to forward data receives at the OSI model data link layer. By incorporating the capability of routing, switches can forward data at the network layer, known as layer 3.
what are the answers for theses question?




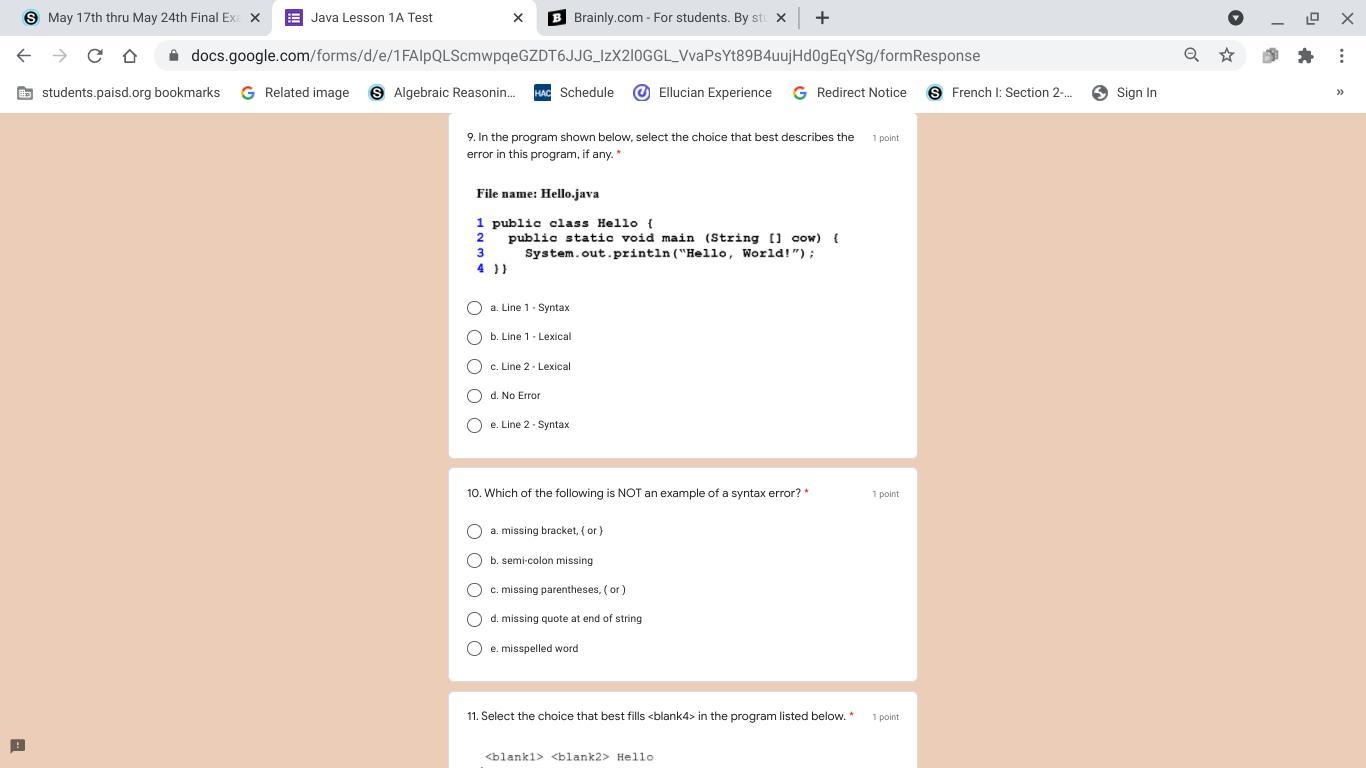
Answers
Answer: me no comprende coding
Explanation:
sorry
who wants to play genshin?
Answers
Answer:
Sure! What server are you on tho?
Explanation:
what ribbon command on the home tab can you use to change a cell fill color
Answers
The ribbon command.
The ribbon command can be found in Microsoft word and the other files types seen on the home button, it can be sued to change the color. It organizes the features of the program and enables the viewer to work efficiently. The tab is dedicated to all the main functions.
Thus the answer is explained in steps.
The first step is for changing colors is the option of select those cells that color you want to change. Second, the command of ctrl+Shift+F. Excel displays the Format Cells dialog box. The third step is you use the Fill tab is selected. In the last step use the color palette and select your color, then click OK.Find out more information about the ribbons command.
brainly.com/question/26113348.
Your question was incomplete.
Darian is preparing for a presentation about the poor condition of the locker rooms at school. Match each of the key components of a presentation to a detail of Darian's presentation. audience to persuade the school board to improve locker-room condition purpose Darian's school board locker-room condition topic a electronic slideshow method can anyone
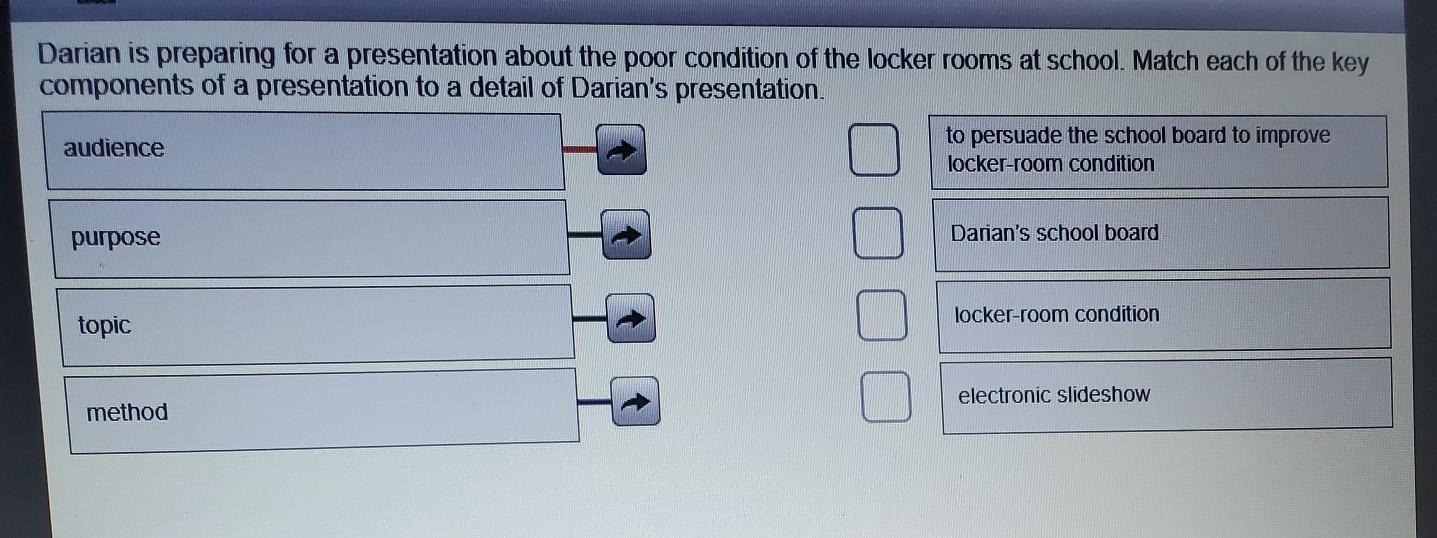
Answers
Answer:
Purpose - To paurswade the board to change the conditions of the locker room
Topic - Locker room condition
Method - Electronic Slideshow
Audience - School Board
Please help me I don't understand. It's Python.
If anyone can help with either of these questions I would appreciate a lot!
Thank you :)

Answers
1.d
2. a
i am not sure but i think its correct
The first step of the Data Encryption Standard (DES) involves breaking the plaintext into blocks of ______.
Answers
Answer:
64 bits
Explanation:
DES uses block encryption
when you are creating formulas using cell locations, the default cell reference is:
Answers
When creating formulas using cell locations in spreadsheet software, the default cell reference is relative.
Relative cell references in a formula refer to cells relative to the position of the formula, meaning that the references will change automatically when the formula is copied or moved to a new location. For example, if a formula in cell A1 references cell B1, when the formula is copied to cell A2, the reference to B1 will automatically update to B2. This can be useful for quickly copying and applying a formula to multiple cells, but can also cause unintended errors if the reference is not adjusted correctly.
Learn more about spreadsheet here;
https://brainly.com/question/11452070
#SPJ11
which of the following policy settings are not supported by local group policy on windows 10?
Answers
The policy setting "Software installation" is not supported by Local Group Policy on Windows 10. The other three policy settings, namely "Software Restriction Policy," "Folder redirection," and "Start Menu and Taskbar," are supported by Local Group Policy on Windows 10. So option 3. is the correct answer.
Local Group Policy allows administrators to configure and enforce various settings on individual Windows computers or user accounts. It provides a way to manage and control the behavior and configuration of the operating system and applications.
While Local Group Policy supports a wide range of policy settings, including those related to software restriction, folder redirection, and start menu/taskbar customization, it does not have native support for managing software installation.
For software installation management, organizations typically use other tools like Microsoft System Center Configuration Manager (SCCM) or Group Policy Software Installation (GPSI) deployed through Active Directory Group Policy.
So the correct answer is option 3. Software installation.
The question should be:
Which of the following policy settings are not supported by Local Group Policy on Windows 10?
Software Restriction PolicyFolder redirectionSoftware installationStart Menu and TaskbarTo learn more about policy settings: https://brainly.com/question/14364696
#SPJ11
you want to configure your computer so that a password is required before the operating system will load. what should you do? Configure an administrator password in the BIOS/UEFI.Require complex passwords in the local security policy.Configure a user password in the BIOS/UEFI.Configure chassis instruction detection.
Answers
Create a user password in the UEFI or BIOS.
What distinguishes a user password from an administrator password in the quizlet on BIOS UEFI configuration?What distinguishes an administrator password from a user password in the BIOS/UEFI configuration? While the admin password is needed to access the BIOS, the user password is needed to boot Windows.
Why are the system requirements important to take into account when installing an operating system on your computer?The programme you are trying to install won't run and might not even install if your computer doesn't fulfil the minimum system requirements. The programme will run on your computer even if it doesn't meet the recommended requirements, but it might not perform as well.
To know more about password visit:-
https://brainly.com/question/30482767
#SPJ1
Ethan entered a long column of numbers into a spreadsheet and noticed that he accidentally entered the data into the column D when it should have been in column E . What is the fastest way for Ethan to make this correction
Answers
Answer:
Ethan should cut the data entered mistakenly in D column and paste it in column E. There are also other ways that he could do it. He should undo the operation of entering the data in the wrong column but it will require a step for entering data in the correct column E.
Explanation:
Got an A the same answer as above but just editedThe incorrectly entered data in column D in the spreadsheet should be copied by Ethan and pasted in column E. He might also accomplish it in other ways. He has to reverse the action of entering the data in the incorrect column.
What is the spreadsheet?A spreadsheet is a computer programme for organising, calculating, and storing data in tabular form. Spreadsheets were created as digital counterparts to traditional paper accounting spreadsheets.
The mistake of entering the data in the wrong column must be undone. A spreadsheet is a piece of software that can store, display, and edit data that has been organised into rows and columns.
Therefore, The data entered into a table's cells is what the programme uses to run.
Learn more about the spreadsheet, refer to:
https://brainly.com/question/8284022
#SPJ5
How are yall today pfft
Answers
Answer:
Good
Explanation:
HEYYYY
im good
anyways ik this was like 2 months ago
What is generally included in an llc's operating agreement? (check all that apply. )
Answers
An LLC operating agreement typically contains a variety of provisions that govern the LLC's internal operations. This agreement is a document that outlines how the limited liability company (LLC) will be run.
In essence, it is an LLC's internal governance document and the most crucial piece of the company's legal structure. This document generally includes the following:
1. Owners' names, roles, and responsibilities.
2. Profit distribution and equity splits.
3. Duration of the company.
4. Tax operating of the company.
In conclusion, an LLC's operating agreement outlines the internal governance of the company and contains important information about the company's operations. It is a crucial legal document that should be drafted and reviewed by an experienced attorney.
To know more about operating visit:
https://brainly.com/question/11596110
#SPJ11
Write a Java program which declares and populates an array with some values (at least 5 values). Then it should call a method passing it the array. The method should modify the array values using a loop. Lastly, after the program calls the method, it should display the modified array contents to the console.
Answers
Answer:
CODE IN JAVA :
import java.util.*;
public class Main
{
public static void modifyArray(int[] arr, int n){
for(int i = 0; i < n; i++){
arr[i] = -1; // each value is modified to -1
}
}
public static void main(String[] args) {
int n;
System.out.print("Enter size of array(atleast 5): ");
Scanner sc = new Scanner(System.in);
n = sc.nextInt();
int array[] = new int[n]; // array with size n declared
// populating the array
System.out.print("Enter array elements: ");
for(int i = 0; i < n; i++){
array[i] = sc.nextInt();
}
// modifying array via a function
modifyArray(array, n);
// printing array values after modifiction
System.out.print("Array after modification: ");
for(int i = 0; i < n; i++){
System.out.print(array[i] + " "); // space separated
}
}
}
Explanation:
What does the touring test determine?
Answers
Answer:
The Turing Test is a method of inquiry in artificial intelligence (AI) for determining whether a computer is capable of thinking like a human being.
Explanation:
an obstacle or barrier that may prevent you from accomplishing your goal is called
Answers
Answer:
a roadblock
Explanation:
What is the token generated when you create a snort rule that will detect outbound traffic using tcp to port 443 and 447?
Answers
The token generated if you create a snort rule that will detect outbound traffic using TCP to port 443 and 447 is:
Alert TCP any any -> any 443 (message: "Test HTTP request alert"; sid:1000001;)What is a Snort detection rule?The Rules is known to be a kind of a different methodology that is known to be often used in the act of performing detection, and it is one that bring about the merit of 0-day detection to one's table.
Note that when compared to other forms of signatures, this rules are known to be based on knowing the actual vulnerability.
Hence, The token generated if you create a snort rule that will detect outbound traffic using TCP to port 443 and 447 is:
Alert TCP any any -> any 443 (message: "Test HTTP request alert"; sid:1000001;)Learn more about TCP from
https://brainly.com/question/17387945
#SPJ1
Most hard drives are divided into sectors of 512 bytes each. Our disk has a size of 16 GB. Fill in the blank to calculate how many sectors the disk has. Note: Your result should be in the format of just a number, not a sentence.
disk_size = 16*1024*1024*1024
sector_size = 512
sector_amount =
print(sector_amount)
Answers
What type of cryptanalytic attack where an adversary has the least amount of information to work with?
Answers
The ciphertext-only attack is the only type of cryptanalytic attack where an adversary has the least amount of information to work with.
Cryptanalysis is the study of cryptographic algorithms and the deciphering of secret codes. A Cryptanalyst is someone who practices Cryptanalysis.
It is necessary to attack a cryptographic system to determine its weak points. Cryptanalytic attacks are what they're called. The attacks are based on the algorithm's nature as well as knowledge of the standard features of the plaintext.
Only some ciphertext is known in this attack, and the attacker attempts to locate the corresponding plaintext and encryption key. It is the most difficult to implement, but it is also the most likely attack because only ciphertext is needed.
To learn more about ciphertext-only attacks: brainly.com/question/13068614
#SPJ4
Define the term editing
Answers
Answer:
editing is a word file mean making changes in the text contain is a file. or a word file is one of the most basic ms office word operation.
Name three organic materials that technology turns into products.
Answers
Answer:
Useful forms of energy that can be produced include
heat
steam
electricity
renewable natural gas
and fuels.
How does the payload free worm method differ from the payload method?
Answers
A worm is a type of computer virus that is self-replicating and can spread throughout a network or the internet. It is a self-contained program that can replicate and spread without the need for a host file. Payload is a program or code that is hidden within the worm and executed on an infected computer.
These payloads can cause damage to the infected system, steal data, or launch additional attacks on other systems or networks. The payload-free worm is a worm that replicates and spreads like a traditional worm but does not contain any payload or malicious code.
It does not cause any damage to the infected system or network. This type of worm is often used for research purposes to study the spread of worms without causing harm to any system. The payload method is a worm that has a hidden code that is designed to cause damage to the infected system or network.
The payload can be programmed to perform various functions, including deleting files, stealing data, launching attacks on other systems, or installing additional malware. This type of worm is often used by cybercriminals to launch attacks on specific targets or to spread malware for financial gain.
For more such questions Payload,Click on
https://brainly.com/question/30144748
#SPJ8
When a person can present their own ideas without barreling over the other person and their ideas, they are exhibiting
Answers
Answer:
Assertiveness.
Explanation:
Assertiveness can be defined as a social skill and communication style in which an individual expresses his or her feelings, ideas, desires, opinions, needs or even their rights without being disrespectful to the other party.
Basically, an individual who communicates effectively without being aggressive and disrespectful is said to possess an assertive communication skills.
This ultimately implies that, this kind of individual can effectively combine his behavioral, cognitive and emotional traits while communicating with others.
Hence, when a person can present their own ideas without barreling over the other person and their ideas, they are exhibiting assertiveness.
A person with a kinesthetic learning style learns best by
a. reading and writing.
b. moving around and interacting with objects.
c. working with numbers and patterns.
d. independent study.
Answers
Explain motherboard in detail
Answers
Answer:
A motherboard is the main printed circuit board in general-purpose computers and other expandable systems. It holds and allows communication between many of the crucial electronic components of a system, such as the central processing unit and memory, and provides connectors for other peripherals. Unlike a backplane, a motherboard usually contains significant sub-systems, such as the central processor, the chipset's input/output and memory controllers, interface connectors, and other components integrated for general use. It also makes arithmetical operations
Explanation:
Have a nice day ;]
Answer:
motherboard is the main printed circuit board (PCB) in a computer. The motherboard is a computer’s central communications backbone connectivity point, through which all components and external peripherals connect. The large PCB of a motherboard may include 6-14 layers of fiberglass, copper connecting traces and copper planes for power and signal isolation.
The motherboard contains the connectors for attaching additional boards, such as the CPU, BIOS, memory, mass storage interfaces, serial and parallel ports, expansion slots and all the controllers that are required to control standard peripheral devices such as the display screen, keyboard, and hard drive.
20 points
Suppose the following array is declared: int[ ] grades = {88, 92, 95, 83}; and the following integer is declared: int index = 1 + 6 % 3; What is the value of grades[index]?
Answers
Answer:
92
Explanation:
int index = 1 + 6 % 3;
Modulo is calculated before adding, so as first you need to calc 6 % 3, result is 0.
int index = 1 + 0 = 1;
Indexes in arrays starts from 0, ends in length - 1. So first element in the array has 0 as index, second element has 1 as idnex, etc. Your index = 1, so value of the second element in the grades will be your result. Finally, the answer is 92.
pls help have absolutely no clue how to delete this

Answers
Answer:
is that a picture or a file if it's a file then touch the pad with two fingers
if a picture then i don't know
Explanation:
Answer:
not sure if this will mess anything up but try to run cmd as admin and del that folder
Explanation:
what jtids/mids protocol dictates that platforms take turns transmitting and receiving data according to time?
Answers
Link 16 JTIDS/MIDS protocol dictates that platforms take turns transmitting and receiving data according to time. Link 16 is a standard military tactical data exchange network that allows military platforms to share data on a common network.
What is Link 16?
Link 16 is a time-division multiplexing (TDM) network that allows many users to share the same radio frequency band. The TDM method permits each user to transmit its data within its own time slot. This guarantees that the radios' messages do not collide with one another. The Link 16 terminals do this using the Time Division Multiple Access (TDMA) method.
This method ensures that platforms transmit their data at precise, prearranged intervals. Link 16 is also a secure radio that prevents eavesdropping by encrypting the information.
To know more about time-division multiplexing (TDM) visit:
https://brainly.com/question/31666197
#SPJ11
3.Troubleshooting Methodology: Given a scenario, you should be able to know how to troubleshoot.
Answers
Troubleshooting methodology is a systematic approach to identify, analyze, and resolve problems or issues that arise in various scenarios. While the specific troubleshooting steps may vary depending on the situation, there are some common principles and techniques that can be applied.
If a scenario is given, here are some general steps to follow when troubleshooting:
Define the problem:
Clearly identify the problem so that you know what to look for and how to fix it. Check whether the issue is related to hardware, software, or a mixture of both. Check if there is any error message appearing and try to decode the message. Identify the root cause of the problem.Understand the system or network:
Identify the system or network components that could be affected by the problem. Check whether the system or network is operational. If it is operational, perform a status check to identify any obvious problems.Identify the possible causes:
Identify the potential causes of the issue. Consider what changes may have been made to the system recently, as this can often help in identifying the problem.Implement a solution:
Depending on the issue, this might involve reconfiguring software settings, replacing a hardware component, or reinstalling a program.Verify the solution:
Verify the solution by testing the system or network. Check if the solution has solved the issue completely or partially. If the issue is partially resolved, repeat the above process. If the issue is resolved completely, then the solution is good to go!Document the issue and the solution:
Write down the issue and the solution for future reference. If the problem was complex, document the process followed to solve the problem. This documentation will be useful for future reference and might help other people who might encounter a similar problem.To learn more about troubleshooting: https://brainly.com/question/28508198
#SPJ11
the primary reason for data normalization is to: group of answer choices optimize access or processing speed for quicker reports better communicate requirements to the users optimize storage requirements by reducing data redundancy test the efficiency and effectiveness of database designers
Answers
When a relational database's attributes and tables are organized to reduce data redundancy, this process is known as database normalization.
Why does normalization exist in the first place?Reducing or getting rid of redundant data storage is referred to as normalization. Avoiding issues resulting from updating redundant data is normalization's main goal. The 3NF-3rd Normal Form, for instance, uses a design approach to normalization that could lead to a lot of tables.
What could normalizing a database be used for?The purpose of normalizing a database is to reduce redundancy (duplicate data) and make sure that only related data is kept in each table. Additionally, it stops any problems brought on by updates, insertions, and deletions in the database.
To know more about database visit :-
https://brainly.com/question/6447559
#SPJ4