a user boots and installs a legacy windows operating system on a computer. the user notices that after installation, the system requires many drivers and updates to bring it to a healthy and up-to-date state. the user finds that it is not possible to add updates to which installation media type?
Answers
Installing a legacy Windows OS may require updates and drivers. Adding updates to Windows XP SP2 integrated installation discs may be limited.
What is the windows operating system?Discs for convenient Windows XP installation with integrated updates. But, if user used SP2 disc, adding updates directly could be difficult. SP2 installation discs have a specific set of integrated updates, making it difficult to add more updates later.
Users must download updates separately or use Windows Update. Limitation is only for Windows XP SP2 disc. Other media can be updated using tools or slipstreaming.
Learn more about windows operating system from
https://brainly.com/question/31026788
#SPJ1
Related Questions
Which of the following statements is valid?SELECT InvoiceNumber, VendorNameFROM Invoices JOIN Vendors ON Invoices.VendorID = Vendors.VendorIDWHERE InvoiceTotal = MAX(InvoiceTotal)SELECT InvoiceNumber, VendorNameFROM Invoices JOIN Vendors ON Invoices.VendorID = Vendors.VendorIDWHERE InvoiceTotal = (SELECT MAX(InvoiceTotal))SELECT InvoiceNumber, VendorNameFROM Invoices JOIN Vendors ON Invoices.VendorID = Vendors.VendorIDWHERE InvoiceTotal IN (SELECT MAX(InvoiceTotal) FROM Invoices)All of the above
Answers
Correct Answer:
c.
SELECT InvoiceNumber, VendorName
FROM Invoices JOIN Vendors ON Invoices.VendorID = Vendors.VendorID
WHERE InvoiceTotal IN (SELECT MAX(InvoiceTotal) FROM Invoices)
Explanation:
All options only differ on the WHERE clause:
a: WHERE InvoiceTotal = MAX(InvoiceTotal)
Fails because aggregate functions (like MAX, COUNT, etc) have to be used on the SELECT clause.
b: WHERE InvoiceTotal = (SELECT MAX(InvoiceTotal))
Fails because the SELECT clause is incomplete.
c: WHERE InvoiceTotal IN (SELECT MAX(InvoiceTotal) FROM Invoices)
This one is correct, and returns the InvoiceNumber and VendorName register with the largest value on the InvoiceTotal field.
16.
Macbeth can see a dagger. And if
Macbeth is holding a dagger he could see it. So Macbeth is holding
a dagger.
Select one:
a.
VALID: Modus Ponens.
b.
VALID: modus Tollens.
c.
INVALID:
Answers
The argument presented is invalid.The argument is based on a logical fallacy known as affirming the consequent, which does not lead to a valid conclusion.
The argument structure is as follows:
1. If Macbeth is holding a dagger, he could see it. (Conditional statement)
2. Macbeth can see a dagger. (Antecedent)
3. Therefore, Macbeth is holding a dagger. (Consequent)
The argument assumes that if Macbeth can see a dagger, then he must be holding it. However, there could be other possibilities for Macbeth seeing the dagger. For instance, the dagger could be within his line of sight without him physically holding it.
Therefore, the conclusion that Macbeth is holding a dagger cannot be logically inferred based on the given premises.
The correct application of modus ponens (valid deductive reasoning) would be as follows:
1. If Macbeth is holding a dagger, he could see it. (Conditional statement)
2. Macbeth is holding a dagger. (Antecedent)
3. Therefore, Macbeth can see it. (Consequent)
In this case, the conclusion would be that Macbeth can see the dagger, which follows logically from the premises. However, this is not the structure of the argument given. Therefore, the argument presented is invalid.
Learn more about argument here:
https://brainly.com/question/17039569
#SPJ11
Review the HTML code below.
My Web Page
Hello Friend!
Make it a great day!
Smile
Laugh
Celebrate
Which of the text below would display in the page title, based upon the HTML code above?
Smile
My Web Page
Make it a great day!
Hello Friend!
Answers
My Web Page would display in the page title, based upon the HTML code above.
What is the HTML code?For pages intended to be viewed in a web browser, the HyperText Markup Language, or HTML, is the accepted markup language. Cascading Style Sheets and JavaScript are technologies and scripting languages that can help.A web page's structure and content are organised using HTML (HyperText Markup Language) coding. The organisation of the material, for instance, might take the form of a series of paragraphs, a list of bulleted points, or the use of graphics and data tables.In HTML, four tags are necessary. HTML stands for "title," "head," and "body." These tags go at the start and end of an HTML document.Learn more about HTML refer to :
https://brainly.com/question/4056554
#SPJ1
Discuss the types of data that business might collect and how the business could use that data to drive decision-making in a specific area of the business
Answers
Answer:
Answered below
Explanation:
A business such as an online store like Amazon can collect user data like name, address, mouse clicks on products, how long users stay on page viewing a particular product, marital status, education and many more.
These data are used by these businesses to drive decision-making that enhances the sale of their goods. For instance, adverts and search alternatives about a particular good can be shown to people who have looked at them before. A newly married or pregnant woman would be shown baby products etc.
The spreadsheet below shows how much money each store raised for charity during the months of January, February, and March. A1: Blank. B1: Store 1. C1: Store 2. D1: Store 3. A2: January. B2: 170 dollars. C2: 100 dollars. D2: 150 dollars. A 3: February. B3: 235 dollars. B4: 80 dollars. D3: 240 dollars. A4: March. B4: 300 dollars. C4: 75 dollars. D4: 450 dollars. Using this information, answer the following questions. To obtain the total amount raised by Store 1, which range of cells would you use?
PLEASE HURRY I HAVE TO FINISH BY 12:00

Answers
Answer:
B2:B4
Explanation:
Answer:B2:B4 ,sum ,using the sum and average functions on the range of cells
Explanation:
trust i took the test
can i get my account back if i disabled it on wattpad?
Answers
Answer:
i do not think so
Explanation:
which of the following can be used to enforce strong credential policies for an organization? a. acceptable use policy b. windows active directory c. windows defender d. windows firewall
Answers
The policy which can be used to enforce strong credential policies for an organization is a. acceptable use policy
An acceptable use policy (AUP) can be defined as a policy or document stipulating constraints and practices that a person must agree to for access to a corporate network, the internet, or any other resources. It is a set of rules applied by the creator, owner, or administrator of a computer network service or website.
This policy is generally an integral part of the framework of information security policies; it is often common practice to ask new users or members of an organization to sign an acceptable use policy before they are given access to its information systems. Therefore it must be concise and clear and at the same time should cover the most important points about what users or members are, and are not allowed to do with the IT systems of a company or organization.
To learn more about the acceptable use policy; click here:
https://brainly.com/question/2625500
#SPJ4
Discuss five ways multimedia could be used to fight crime
Answers
Multimedia can be utilized in various ways to fight crime effectively. Five key applications include video surveillance, forensic analysis, crime reenactments, public awareness campaigns, and training simulations.
Video Surveillance: Multimedia technology enables the deployment of extensive video surveillance systems, aiding in crime prevention, detection, and investigation. High-quality cameras and real-time monitoring systems help capture evidence, identify suspects, and deter criminal activities.Forensic Analysis: Multimedia tools are vital for forensic analysis, allowing experts to examine and enhance audio, video, and image evidence. Digital forensics techniques help in authenticating evidence, identifying individuals or objects, and reconstructing crime scenes.Crime Reenactments: Multimedia can be employed to recreate crime scenes and generate virtual crime reenactments. This assists investigators in understanding the sequence of events, identifying potential witnesses, and gathering additional evidence.Public Awareness Campaigns: Multimedia platforms, including social media, websites, and television, facilitate the dissemination of crime-related information to the public. Such campaigns raise awareness, encourage reporting, and foster community involvement in crime prevention.Training Simulations: Multimedia-based training simulations provide law enforcement personnel with realistic scenarios to practice decision-making, response tactics, and de-escalation techniques. Virtual reality and interactive multimedia tools help improve situational awareness, critical thinking, and operational skills.By leveraging multimedia technologies in these ways, crime-fighting efforts can be enhanced, leading to improved prevention, detection, and prosecution of criminal activities.
Learn more about Multimedia here: https://brainly.com/question/32647494
#SPJ11
Helppppp meeeeee eee
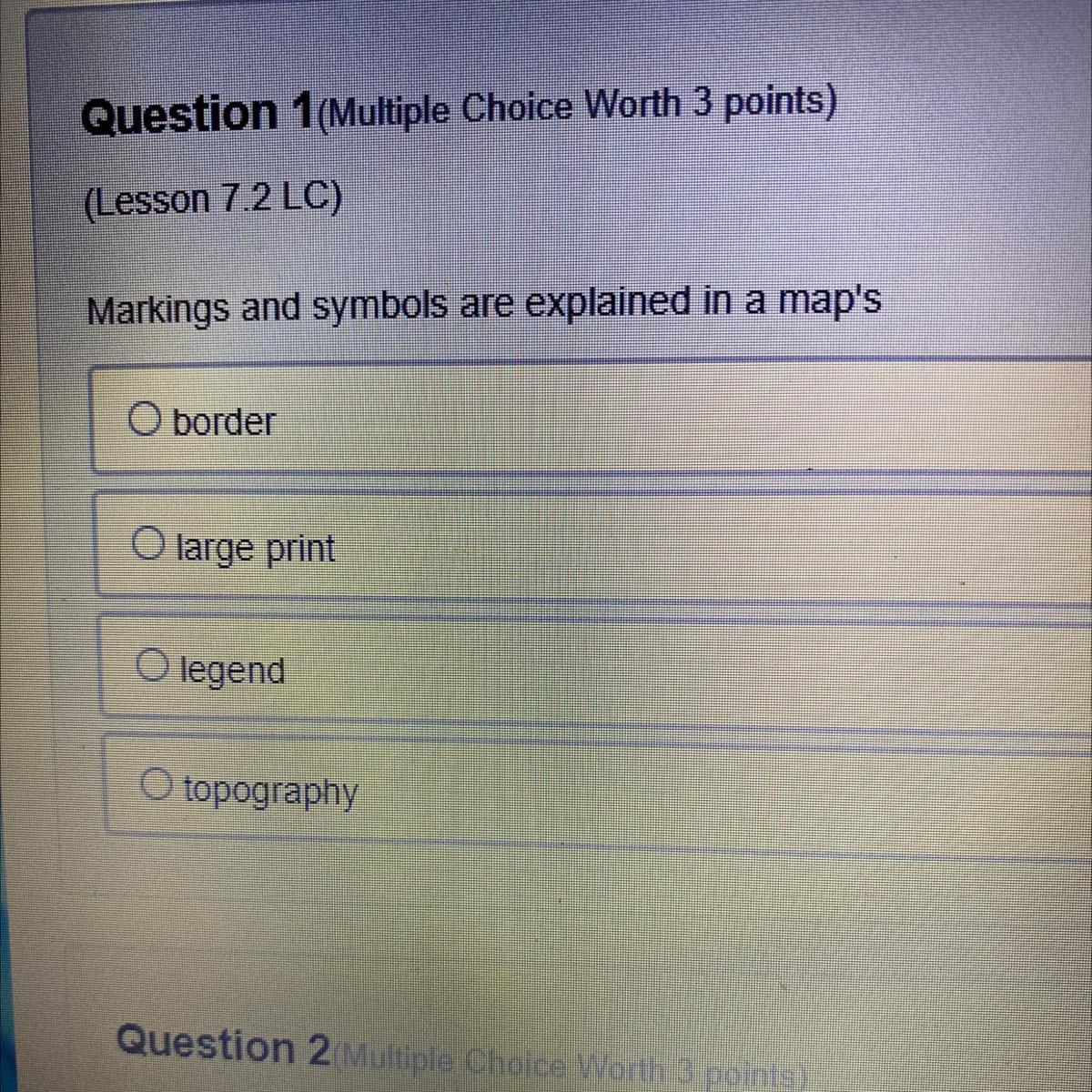
Answers
Answer:
Option C is correct
Explanation:
A map legend or key is a visual explanation of the symbols used on the map. It typically includes a sample of each symbol (point, line, or area), and a short description of what the symbol means.
100 points
The following line of code is in a program.
state = "California"
Which line of code will have the following output?
ifor
O print (state [3:6])
O print (state [3:7])
O print (state [4:7])
O print (state [4:8])
Answers
The line of code that will have the output above is Option B - print (state [3:7])
What is a line of code?Source lines of code, often known as lines of code, is a software metric that counts the number of lines in the text of a computer program's source code to determine the size of the program.
Source lines of code (SLOC), sometimes known as lines of code (LOC), is a software metric that counts the number of lines in the text of a computer program's source code to determine its size.
Learn more about line of code at:
https://brainly.com/question/20212221
#SPJ1
mysqli_connect(): (hy000/1045): access denied for user
Answers
The error message "mysqli_connect(): (hy000/1045): access denied for user" indicates that the user attempting to connect to the database has been denied access. This could be caused by a variety of factors, including incorrect login credentials, incorrect database name, or incorrect database server information.
To fix this error, check that you have the correct login credentials, database name, and server information in your PHP code. Ensure that the user you are trying to connect as has the correct permissions to access the database. Also, make sure that the database server is running and accepting connections.
In summary, the "mysqli_connect(): (hy000/1045): access denied for user" error message can be caused by a number of different issues, including incorrect login credentials, database name, or server information.
To know more about server visit:
https://brainly.com/question/29888289
#SPJ11
is an electronic device that converts computer-readable information into a form that can be transmitted and received over a communications system.
Answers
A modem (short for modulator-demodulator) is an electronic device that converts computer-readable information into a form that can be transmitted and received over a communications system.
Modems can be utilized to link computers to the internet through a phone line or cable or to connect two computers directly through a serial cable. Modems were widely used in the past to link computers to the internet, but they have been mostly replaced by high-speed broadband connections.Modems are still used to communicate data over dial-up telephone networks at speeds of up to 56 kilobits per second (Kbps).DSL modems, cable modems, and wireless modems are the three most common types of modems today.
DSL modems are used to connect to the internet through a telephone line, while cable modems are used to connect to the internet through a cable network. Finally, wireless modems, such as cellular modems, allow wireless internet access over mobile networks.Modems have played a crucial role in the growth and development of the internet and computer networks by allowing computers to communicate over long distances and at high speeds. They are critical pieces of technology that enable internet connections and keep us connected to the rest of the world.
To know more about modem visit
https://brainly.com/question/14208685
#SPJ11
HURRY GIVING BRAINLIEST AND ALL MY POINTS and I only have 40
Write an algorithm using pseudocode that someone else can follow. Choose one of the following options:
1. Decide on the message you would like to display to the screen. Some ideas include:
1. Your favorite book title or TV show and why you like it
2. A few sentences sharing information about you
3. Your favorite sport and team or athlete
4. Use two variables to store your message.
Answers
Answer:
Write an algorithm using pseudocode that someone else can follow. Choose one of the following options:
1. Decide on the message you would like to display to the screen. Some ideas include:
1. Your favorite book title or TV show and why you like it
2. A few sentences sharing information about you
3. Your favorite sport and team or athlete
4. Use two variables to store your message
Explanation:
Answer:
A few sentences about you .
Explanation:
HELP HELP HELP HELP
I spilled acetone nail polish remover on my Chromebook and it left white stains and I tried to scrap most of it off but it won't go away and I REALLY need to fix or cover this up :( Please help me!!!
Answers
cloud kicks intends to protect data with backups by using the data export service. which two considerations should the administrator remember when scheduling the export? choose 2 answers
Answers
Cloud kicks intends to protect data with backups by using data export service in which Data backups are limited to weekly or monthly intervals.
Metadata backups must be run via a separate process.Option A and B are correct.
What are the features of cloud backup?A cloud backup service involves backing up and storing a company's applications and data on a remote server. In the event of a system failure, outage, or natural disaster, businesses choose to backup their data to the cloud.
What does "data backup" entail?The process of creating a backup copy of your digital data and other business information in the event that it is lost, deleted, or damaged is known as data backup. The reinforcement duplicate is then used to recuperate or reestablish your information for business congruity and catastrophe recuperation.
Incomplete question :
Cloud Kicks intends to protect data with backups by using the data export service. Which two considerations should the administrator remember when scheduling the export? Choose 2 answers.
A. Data backups are limited to weekly or monthly intervals.
B. Metadata backups must be run via a separate process.
C. Metadata backups are limited to sandbox refresh intervals.
D. Data export service should be run from a sandbox.
Learn more about cloud kicks :
brainly.com/question/29240780
#SPJ1
Which transmission media is faster? Fibre Optic or Radio-waves? I want full explanation!
Answers
Answer:
Due to the direct line of sight,the data rate of radio links is higher than that of fiber optic connections. A radio link has a lower latency (less delay).In contrast ,fiber optic connections may achieve higher bandwidths
PLEASE HELP!!~~~~
What is the total number of time zones that can be configured to show by default in a calendar in Outlook 2016?
1
2
3
4
Answers
Answer:
2
Explanation:
The total number of time zones that can be configured to show by default in a calendar in Outlook 2016 is 2. The correct option is b.
What are time zones?A time zone is a region that adheres to a common standard of time for social, commercial, and legal activities. All events on the calendar are updated when you open Outlook.
Outlook uses the time zone that is set as the default when you create a new event in the calendar. When establishing an event, you have the option of choosing a different time zone.
The Calendar in the most recent iterations of Outlook for Microsoft 365 can show three different time zones. You can view two time zones in other versions of Outlook, such as Outlook 2019 Volume License, Outlook 2016, Outlook 2013, and Outlook 2010.
Therefore, the correct option is b. 2.
To learn more about Outlook 2016, refer to the link:
https://brainly.com/question/28579226
#SPJ6
Question 2 A data analyst uses the Color tool in Tableau to apply a color scheme to a data visualization. In order to make the visualization accessible for people with color vision deficiencies, what should they do next
Answers
In order to make the visualization accessible for people with color vision deficiencies, he should make sure the color scheme has contrast.
What is a color scheme?A color scheme can be defined as a combination or arrangement of different colors, which are used during the design and development of a software, project, etc.
In this scenario, the data analyst should make sure the color scheme has contrast so as to make the visualization accessible for people with color vision deficiencies.
Read more on data analyst here: https://brainly.com/question/27748920
#SPJ1
how to use function in python
Answers
Answer:
Use the keyword def to declare the function and follow this up with the function name.
Add parameters to the function: they should be within the parentheses of the function. ...
Add statements that the functions should execute.
can
you solve this problem?
Elegant Exphants is a sooosty pet gitt shop seling exctic pet related tems onine the shop has no physical location. Results for last year are shown neat (Click the reon to vew the resats] Hatoment for
Answers
I apologize, but it seems that the question you provided does not make sense and does not require solving a problem. It appears to contain some unrelated information about a pet shop and results from last year. Without a clear problem or question, it is difficult to provide a meaningful answer.
If you have a specific question or problem that you need help with, please provide the details and I will be happy to assist you. It would be helpful if you could provide clear and concise information about the problem or question you need assistance with, along with any relevant details or context.
This will allow me to provide you with a more accurate and helpful answer.
Please let me know how I can assist you further.
To know more about apologize visit:
https://brainly.com/question/32499461
#SPJ11
what type of waves are used on a tv remote control?
Answers
Answer:
(IR) Light
Explanation:
The signal of the remote control, control the pules of the infrared light. But human eye cant see, but can see through a digital camera.
Please please help ASAP it’s timed

Answers
Answer:
First Part = def add(numA, numB) : Return numA + numB
Second Part = answer = add(8,2)
Third Part = print (asnwer)
Hope my answer helps :)
30 pts!
Explain how Moore's law presumes everyone will have access to the Internet.
Answers
Answer:
Moore's law predicts that this trend will continue into the foreseeable future.
Explanation:
Moore's Law refers to Moore's perception that the number of transistors on a microchip doubles every two years, though the cost of computers is halved.
Write a function that given an array a of n integers returns the largest integer k such that both values k and -k.
Answers
To find the largest integer k such that both k and -k exists in an array of integers, we can use a simple algorithm that iterates through the array and keeps track of the largest positive and negative numbers encountered so far. The largest value that satisfies the condition will be the maximum of the absolute values of these two numbers.
Here is a sample function in Python that implements this algorithm:
def largest_k(a):
max_pos = 0
max_neg = 0
for i in a:
if i > 0 and i > max_pos:
max_pos = i
elif i < 0 and abs(i) > abs(max_neg):
max_neg = i
return max(abs(max_pos), abs(max_neg))
This function takes an array of integers as input and initializes two variables max_pos and max_neg to zero. It then iterates through the array, checking each integer and updating max_pos and max_neg if necessary. If an integer is positive and greater than max_pos, it replaces max_pos. If an integer is negative and has a greater absolute value than max_neg, it replaces max_neg. Finally, the function returns the maximum of the absolute values of max_pos and max_neg, which is the largest integer k such that both k and -k exist in the array.
To learn more about Python programming, visit:
https://brainly.com/question/26497128
#SPJ11
Can you see who tries to access a password-protected file, but does not put in the password?
Answers
Yes/no
Explanation:
Depending on the person.
Yes, if your cousins,parents,etc have opened it.
No, if people like hackers have done it.
What is the connection between self-concept and communication?
Answers
The study of interpersonal communication focuses on communication between two persons in close relationships (NCA, nod). Each of us must first establish personal communication.
What is self-concept?The idea that a person has about themselves, including their characteristics and notions of who they are as a person. In his book on the subject from 1979, Rosenberg provided a similar definition of self-concept as "the entirety of an individual's thoughts and feelings bearing reference to himself as an object."Self-concept is how we view our actions, skills, and distinctive qualities. 1 Examples of beliefs that make up a person's general self-concept include "I am a nice friend" and "I am a compassionate person." We separate the four key conceptual building blocks that make up the diverse self-presentational selves. These include the ideal self, the actual or behavioral self, the public self, and the self-concept.To learn more about self-concept refer to:
https://brainly.com/question/13468917
#SPJ4
Project: Math Tutor Program with Error Handling
image of a man sitting on a branch he is about to cut off
Sawing off the branch you are sitting on can only end badly (Imagery supplied by photoschmidt/iStock via Getty)
Unlike the man in the picture, you already know how to plan for and handle errors before they happen. You know how to create and use lists. You know how to use loops. You are going to put these abilities to work in this project. You are going to write a program to help young children with their arithmetic skills.
Objectives
Plan and create a program to practice math facts with error handling.
Your Goal
Your users are young children learning their arithmetic facts. The program will give them a choice of practicing adding or multiplying.
You will use two lists of numbers.
numA = [4, 1, 6, 10, 2, 3, 7, 9, 11, 12, 5, 8]
numB = [2, 12, 10, 11, 1, 3, 7, 9, 4, 8, 5, 6]
If the user chooses adding, you will ask them to add the first number from each list. Tell them if they are right or wrong. If they are wrong, tell them the correct answer.
Then ask them to add the second number in each list and so on.
If the user chooses multiplying, then do similar steps but with multiplying.
Whichever operation the user chooses, they will answer 12 questions.
Write your program and test it on a sibling, friend, or fellow student.
Errors
Think about the types of errors a user can make. Add at least one kind of error handling to your program.
What to Submit
Save your program with a .txt extension. You cannot upload a .py file.
Before you turn your project in, read the rubric.
I need this to be original work
Answers
Answer:
finished = False
numA = [4, 1, 6, 10, 2, 3, 7, 9, 11, 12, 5, 8]
numB = [2, 12, 10, 11, 1, 3, 7, 9, 4, 8, 5, 6]
while True:
pick = input("Would you like to practice addition (+) or multiplication (*)?")
if pick == "+":
for o, k in zip(numA, numB):
ans = input(f"What is {o} + {k}?")
if ans == str(o + k):
print('Correct!\n')
else:
print(f"Incorrect! The correct answer was {o + k}\n")
finished = True
elif pick == "*":
for o, k in zip(numA, numB):
ans = input(f"What is {o} * {k}?")
if ans == str(o * k):
print('Correct!\n')
else:
print(f"Incorrect! The correct answer was {o * k}\n")
finished = True
else:
print('Incorrect Input!')
if finished:
print('Thanks for playing!')
break
Explanation:
aduhhhh
Ashley wrote this paragraph:
Gabe is a hardworking art student. He painted his family history on the fence in front of his home. First, he painted his great-grandfather, who had invented a new kind of long-lasting glue. Then, Gabe added his grandfather, dad, mother, and sisters to the mural. The purple and pink flowers that his mother liked are in the background.
Which would be the best concluding sentence?
A. However, Gabe also earns money loading groceries at the supermarket.
B. Finally, Gabe painted the tree that his dad had planted when they moved into the house.
C. In addition, Gabe does well in school.
D. On the other hand, Gabe forgot to include a painting of his favorite dog.
Answers
Answer:
B
Explanation:
The best concluding sentence is finally, Gabe painted the tree that his dad had planted when they moved into the house.
What does concluding sentences do?The role of concluding sentences do is known to entails the act of summarizing the given clues or points and also ending of any passage.
Note that The best concluding sentence is finally, Gabe painted the tree that his dad had planted when they moved into the house as it is one that can give the best summary of what the passage is about.
Learn more about concluding sentence from
https://brainly.com/question/5427622
#SPJ2
You have booted your windows workstation into safe mode and enabled boot logging. To which log file is the boot logging information now being written?.
Answers
Answer:
Ntbtlog.txt
Explanation:
Found in a book
Have a nice day! :)
Help!! bob searching for a website using the two words theory and practice he finds only one website that has both words most of the other results have only one of the two words some results don't have either of the two words which logic gate principal will help
Answers
Answer:
please just can u explain that
Explanation: