a network administrator is deploying qos with the ability to provide a special queue for voice traffic so that voice traffic is forwarded before network traffic in other queues. which queuing method would be the best choice?
Answers
The queuing method that would be the best choice is LLQ. The correct option is C.
What is network administrator?The day-to-day operation of these networks is the responsibility of network and computer systems administrators.
They organize, install, and support an organization's computer systems, which include LANs, WANs, network segments, intranets, and other data communication systems.
A queuing system is a facility that consists of one or more servers designed to perform specific tasks or process specific jobs, as well as a queue of jobs awaiting processing.
Jobs enter the queuing system, wait for an available server, are processed by this server, and then exit. The most appropriate queuing method would be LLQ.
Thus, the correct option is C.
For more details regarding network administrator, visit:
https://brainly.com/question/14093054
#SPJ1
Your question seems incomplete, the missing option is:
A. FIFO
B. WFQ
C. LLQ
D. CBWFQ
The queuing method that would be the best choice is LLQ. The correct option is C.
What is network administrator?The day by day operation of these networks has the responsibility or the ability of the network and computer systems administrators.
They organize, install, and support an organization's computer systems, which include LANs, WANs, network segments, intranets, and other data communication systems.
A queuing system has been known as a facility that has been consists of one or more servers designed to perform specific tasks or process specific jobs, as well as a queue of jobs awaiting processing.
Thus, the correct option is C.
Learn more details regarding network administrator, visit:
brainly.com/question/14093054
#SPJ1
Related Questions
A measuring cylinder is used to measure the volume of an irregular
solid object.
Answers
Answer:
Yes it is used for measuring the volume of irregular solid objects for example a peice of stone, rubber etc.
Explanation:
What is the best budget electric skateboard under 500$ by your fact or opinion?
I'm giving brainliest to any answer + lots of points!!
Answers
Answer:
I have the Meepo Mini 2s and it is and amazing electric skateboard. The top speed for this skateboard is 28 mph.
It would also help me out a lot if you could solve my question too.
Foreign Intelligence Entities seldom use elicitation to extract information from people who have access to classified or sensitive information. Foreign Intelligence Entities (FEI) seldom use the Internet or other communications including social networking services as a collection method.
Answers
The question statement is true i.e., foreign intelligence entities (FEI) seldom use the internet or other communications including social networking services as a collection method and also seldom use elicitation to extract information from people who have access to classified or sensitive information.
Elicitation is the technique of obtaining information by extracting it from a human source, often without them being aware that they are providing it. It can be conducted through casual conversation or more formal interrogation. FEI's use of elicitationFEI's seldom use elicitation to extract information from people who have access to classified or sensitive information. Elicitation is an expensive and time-consuming process that requires a significant investment of resources and personnel to complete effectively. FEI's are more likely to use other methods, such as cyberattacks or human intelligence (HUMINT) collection, to gather classified or sensitive information.FEI's use of the internet or social networking servicesFEI's seldom use the internet or other communications including social networking services as a collection method. This is due to the high risk of detection and the low yield of information gained from these methods. Instead, FEI's often use more traditional collection methods such as human intelligence (HUMINT), signals intelligence (SIGINT), and open-source intelligence (OSINT) to gather information.Thus, we can conclude that the given statement is true as FEI's seldom use the internet or other communications including social networking services as a collection method and also seldom use elicitation to extract information from people who have access to classified or sensitive information.
To know more about foreign intelligence visit:
https://brainly.com/question/32500376
#SPJ11
Foreign Intelligence Entities (FEIs) do use elicitation and online platforms for collecting classified or sensitive information. Elicitation appears as harmless conversations while Internet-based methods facilitate quick, expansive, and covert data accumulation.
Explanation:Foreign Intelligence Entities (FEIs) are agencies or organizations that gather intelligence either by recruiting agents or through various forms of espionage. Despite how it might seem on the surface, FEIs often utilize elicitation tactics to gain valuable classified or sensitive information. Elicitation can involve seemingly innocent conversations or interviews that are designed to draw out answers from individuals who may unknowingly hold information of interest.
Furthermore, despite the strides in technology, it's not uncommon for FEIs to use the Internet, social platforms, and other communication methods as means for collection. These platforms provide expansive research, networking opportunities, and avenues of manipulation for FEIs seeking swift and discreet information gathering.
Learn more about Espionage Methods here:https://brainly.com/question/34203237
Artificial intelligence could be useful or harmful for humans true or false
Answers
Answer:
Artificial intelligence (AI) can be both useful and harmful for humans, depending on how it is developed and used. AI has the potential to solve complex problems, improve efficiency, and enhance human capabilities in various fields such as healthcare, education, and transportation. However, AI can also pose risks and challenges, such as job displacement, biased decision-making, and security threats. Therefore, the statement
"Artificial intelligence could be useful or harmful for humans" is true.The TechWorld goes on a fast pace, what do you think would be the solution to the growing amount of data being collected by the software applications to have a fully sustainable usage for customers like us?
Answers
The solution to the growing amount of data in software applications to have fully sustainable usage for customers is;
Development of a sustainable model for the future now requires data storage that is engineered to be lower power requirements, lower cooling requirements, and lower waste production.Sustainable data storage and usageThe objective of Sustainable Data Storage Initiative is to spread awareness of the solutions that can reduce the environmental impact of high waste producing data centers.
The environmental impact of data infrastructure is growing as data workloads increase. Hence, building a sustainable model for the future now requires data storage that is engineered to be lower power requirements, lower cooling requirements, and lower waste production.
Read more on Sustainable data storage and usage;
https://brainly.com/question/24882256
Write a program in java to input N numbers from the user in a Single Dimensional Array .Now, display only those numbers that are palindrome
Answers
Using the knowledge of computational language in JAVA it is possible to write a code that input N numbers from the user in a Single Dimensional Array .
Writting the code:class GFG {
// Function to reverse a number n
static int reverse(int n)
{
int d = 0, s = 0;
while (n > 0) {
d = n % 10;
s = s * 10 + d;
n = n / 10;
}
return s;
}
// Function to check if a number n is
// palindrome
static boolean isPalin(int n)
{
// If n is equal to the reverse of n
// it is a palindrome
return n == reverse(n);
}
// Function to calculate sum of all array
// elements which are palindrome
static int sumOfArray(int[] arr, int n)
{
int s = 0;
for (int i = 0; i < n; i++) {
if ((arr[i] > 10) && isPalin(arr[i])) {
// summation of all palindrome numbers
// present in array
s += arr[i];
}
}
return s;
}
// Driver Code
public static void main(String[] args)
{
int n = 6;
int[] arr = { 12, 313, 11, 44, 9, 1 };
System.out.println(sumOfArray(arr, n));
}
}
See more about JAVA at brainly.com/question/12975450
#SPJ1

(Java) What, in your opinion, is wrong with this nested for loop?
for(int x = 0; x < 10; x++){
for(int x = 10; x > 0; x--){
System.out.println(x);
}
}
Answers
The issue with this nested for loop in Java is the declarationof the second loop variable.
Why is this so?Both loops use the same variable name"x" for iteration. This creates a conflict because the inner loop re-declares the "x" variable, leading to a compilation error.
Each loop should have a unique variable name to avoid naming conflicts and ensure proper loop execution.
The corrected code will be --
for (int x =0; x < 10; x++) {
for (int y = 10;y > 0; y--) {
System.out.println(y);
}
}
Learn more about Java at:
https://brainly.com/question/25458754
#SPJ1
In Chapter 20 you read all about different types of private networks -- VLANs, NAT, PAT, and network segmentation. Additionally, the chapter covered virtual networks. Network virtualization has changed computing for the better. It saves money, allows for more scalability in networks, provides a more rich training environment since students or new hires are able to go out and "play" with the virtual machines and really get some hands-on experience! Some of you may not have really heard too much about virtual networks or how to use a virtual computer. For this discussion board, I want you to share with the class what experience (if any) you have with VMs. Initial Response Guidelines:
In roughly 100-150 words, describe to the class your experience with virtual networks or virtual computers. Virtual reality does not really count, but if it's all you have to discuss it will work. I want you to describe not only your experiences but also your thoughts on using virtual machines to save money, learn new techniques and any other aspects of VMs you want to share.
Answers
I have extensive experience with virtual networks and virtual machines (VMs). I have worked with various virtualization platforms like VMware, VirtualBox, and Hyper-V, both for personal use and in professional settings.
Virtual networks have been an integral part of my work and learning environment. They offer several advantages, including cost savings and increased scalability. By running multiple virtual machines on a single physical server, resources can be utilized more efficiently, reducing hardware costs. Moreover, VMs can be easily cloned, allowing for quick deployment and replication of complex network setups.
Using virtual machines has also enhanced my learning experience. I have been able to experiment with different operating systems, software configurations, and networking scenarios without the need for additional physical hardware. This hands-on approach has enabled me to gain practical skills, troubleshoot issues, and explore new techniques in a safe and isolated environment.
Overall, virtual machines have been invaluable tools for me. They have provided cost-effective solutions, facilitated learning opportunities, and allowed for the exploration of diverse network setups. The ability to create and manage virtual networks has not only saved money but also enriched my understanding of networking concepts and technologies.
To know more about virtual machines ,visit:
https://brainly.com/question/31674424
#SPJ11
backlinks that are considered pure endorsements that will improve a webpage's ranking on any search engine is a(n) link.
Answers
Backlinks that are considered pure endorsements that will improve a webpage's ranking on any search engine is an editorial links. The correct option is a.
What is backlinks?An anchor text link from one website to another is referred to as a backlink. Any article you come across with a link to another source or website is an example of a backlink.
Examples of website backlinks can be found all over the internet, particularly on well-known blog sites that link to pertinent content. A webpage is a page that is online, created with codes in a computer.
Therefore, the correct option is a. editorial.
To learn more about backlinks, refer to the link:
https://brainly.com/question/28390891
#SPJ1
The question is incomplete. Your most probably complete question is given below:
a. editorial
b. manual
c. neighborhood
d. manufactured
Give an example of a function from the set of integers to the set of positive integers that is:_____________
a. one-to-one, but not onto.
b. onto, but not one-to-one.
c. one-to-one and onto.
d. neither one-to-one nor onto
Answers
The following are some examples of a function from the set of integers to the set of positive integers that are:(a) one-to-one, but not onto: For instance, f: Z→ N such that f(x) = x², where Z represents the set of integers, and N denotes the set of positive integers.
This function maps each element of Z to its square, thus it is one-to-one, but it is not onto since there is no negative number that is the image of this function.(b) onto, but not one-to-one: For instance, f: Z → N such that f(x) = │x│, where Z represents the set of integers, and N denotes the set of positive integers. This function maps each element of Z to its absolute value. Thus it is onto, but it is not one-to-one since the absolute values of two different integers can be equal.(c) one-to-one and onto:
For instance, f: Z → N such that f(x) = x+1, where Z represents the set of integers, and N denotes the set of positive integers. This function maps each element of Z to the number immediately following it. Thus it is one-to-one and onto.(d) neither one-to-one nor onto: For instance, f: Z → N such that f(x) = 2x, where Z represents the set of integers, and N denotes the set of positive integers. This function maps each even integer to its half. Thus it is not one-to-one, since two different integers are mapped to the same image, and it is not onto since there is no odd number in the image of this function.
To know more about integers visit:-
https://brainly.com/question/31793000
#SPJ11
. while designing changes to a data center because of a new ioe implementation, a network administrator has the job of diagramming the new physical topology of the area. what should be included in the physical topology diagram?
Answers
One way to avoid the spread of worms over the entire corporate network is to implement network segmentation.
Network segmentation involves dividing a large network into smaller, more manageable subnetworks or segments. Each segment can then be isolated from other segments using firewalls and other security measures.
By limiting the communication between segments, the spread of worms and other malware can be contained, preventing them from infecting the entire network. This also makes it easier to monitor network activity and detect any security breaches.
Network segmentation can be implemented through various methods such as VLANs, subnets, and physical isolation. It is an effective strategy for large corporations to secure their computer networks and protect against cyber threats.
For more questions like Network click the link below:
https://brainly.com/question/15332165
#SPJ11
explain what a relational database to an elderly person is.
Answers
The term relational database been defined to an elderly person is that it is used to established relationships that is to organize data into one or more tables (or "relations") of columns and rows, relational databases make it simple to view and comprehend how various data structures relate to one another.
Why do we use relational databases?The consistency of the data is guaranteed via a relational database model for all users. As a result of everyone seeing the same information, understanding is improved throughout an organization.
For instance, it could be sensible to designate a separate box inside your toy box (database) to hold all of your dolls' heads and another box to hold their arms. Because it keeps track of which dolls' limbs and heads correspond to which dolls, that form of database is known as a relational database.
Learn more about relational database from
https://brainly.com/question/28119648
#SPJ1
What do network executives blame for the superficiality in media reporting?
Answers
Network executives often express concern about the superficiality in media reporting, which refers to the lack of depth and quality in news stories, leading to a limited understanding of important issues.
There are several factors that network executives typically blame for superficiality in media reporting:
Sensationalism: News organizations sometimes prioritize attention-grabbing headlines and stories over more in-depth and informative pieces, as they attract higher ratings and ad revenue.Deadline pressures: Reporters face constant pressure to deliver news quickly, which may lead to less thorough research and a focus on shorter, less informative pieces.Limited resources: Many news outlets have reduced their budgets, leading to fewer investigative journalists and a reliance on easy-to-produce stories.Audience preferences: Some network executives believe that audiences prefer shorter, more easily digestible news stories, and therefore cater their content to meet these preferences.Social media: The rapid spread of information through social media platforms can result in a shallow understanding of complex issues, as users may only read headlines or short summaries.In conclusion, network executives attribute the superficiality in media reporting to factors such as sensationalism, deadline pressures, limited resources, audience preferences, and the influence of social media. This can result in a lack of in-depth and informative news coverage, which may limit the public's understanding of important issues.
To learn more about Network, visit:
https://brainly.com/question/30456221
#SPJ11
charanya decides it is time for an upgrade. she buys a new computer, a used 17-inch lcd monitor at a thrift shop, as well as a vga splitter for screen duplication purposes and compatibility with the original vga monitor. when she plugs in the monitors, the image on the lcd monitor is blurry. what are possible explanations for, and/or how could she rectify, this condition? select two.
Answers
Charanya has purchased a new computer, a used 17-inch LCD monitor, and a VGA splitter. However, when she plugs in the monitors, the image on the LCD monitor is blurry. There could be several possible explanations for this condition, including issues with the monitor, cable, or computer settings. Two possible explanations and/or solutions are as follows:
1. Adjust the display settings: One possible explanation for the blurry image on the LCD monitor is that the display settings are not properly configured. Charanya should check the display settings on her computer and ensure that they are set to the correct resolution for the monitor. She can also adjust the brightness and contrast settings to improve the image quality.
2. Check the VGA cable: Another possible explanation for the blurry image is that there is an issue with the VGA cable. Charanya should check the cable connections and ensure that they are properly connected and not damaged. She can also try using a different VGA cable to see if that resolves the issue.
3.In conclusion, there are several possible explanations for a blurry image on an LCD monitor, including issues with the display settings or VGA cable. Charanya can try adjusting the display settings and checking the cable connections to rectify the condition.
for more such question on terminology
https://brainly.com/question/28587255
#SPJ11
Over the weekend, i was thinking about the process for analyzing the technology needs for this new department. the service department will need a system to support its unique needs of scheduling technicians, obtaining parts for repair, and setting up follow up appointments once parts are in-stock. i want to make sure that none of the analysis and design tasks fall through the cracks. i need you to identify all of the tasks that you will need to complete. i find it is helpful to create a work breakdown structure to identify the tasks. don't forget to include the system and industry analysis, system design, implementation plans, and security tasks in your wbs. what would be an example of a wbs?
Answers
The primary problem to be attained is the estimating of the sources. Its it good that one assign sources to all of the activity as in step with the things that can be done of that pastime and those to be finished efficiently as well as successfully.
What is WBS?The term Work Breakdown Structure (WBS) is known to be a form of an hierarchical statement of the tasks that is needed to complete a project.
Note that the WBS tends to “breaks down” the structure of a project into what we call the manageable deliverables.
The Work breakdown structure (WBS) in project management is also known as a method for finishing a complex, multi-step project and as such, The primary problem to be attained is the estimating of the sources. Its it good that one assign sources to all of the activity as in step with the things that can be done of that pastime and those to be finished efficiently as well as successfully.
Learn more about Work Breakdown Structure from
https://brainly.com/question/3757134
#SPJ1
2.5 code practice
edhesive
import random
a = random.randint(1, 11)
b = random.randint(1, 11)
print ("What is:
+ str(a) + " X " + str(b) + "?")
þins
int(input("Your answer: "))
if (a * b
ans):
print ("Correct!")
else:
print ("Incorrect!")
it says
int(input(“Your answer: “))
is incorrect and is highlighted red.
Answers
Answer:
50000
Explanation:
Elena finished typing her report on dogs into a Word document. What command should she choose to proof her document for errors
Answers
Elena should choose the "Spelling & Grammar" command in Microsoft Word to proof her document for errors.
To proofread her document for errors, Elena should select the "Spelling & Grammar" command in Microsoft Word. This feature automatically checks the text for spelling and grammar mistakes. By selecting this option, Word will scan the entire document, underlining any potential errors and offering suggested corrections.
The "Spelling & Grammar" command in Word is a powerful tool that helps users identify and correct mistakes in their documents. When Elena initiates the command, Word will review the text and highlight any misspelled words or grammar errors using red or green underlines. She can then right-click on the underlined words or phrases to see a list of suggested corrections.
By carefully reviewing these suggestions, Elena can make the necessary corrections to ensure her report is free from errors and maintains a professional quality. Additionally, the command also provides grammar suggestions, such as identifying incorrect verb tenses or subject-verb agreement errors, which further enhances the overall accuracy and clarity of the document.
Learn more about Microsoft Word here:
https://brainly.com/question/30160880
#SPJ11
what can eallb spell in computer terms
Answers
Write a program that:
Takes the list lotsOfNumbers and uses a loop to find the sum of all of the odd numbers in the list (hint: use Mod).
Displays the sum.
Situation B
Write a procedure that takes a positive integer as a parameter. If the number given to the procedure is no more than 30, the procedure should return the absolute difference between that number and 30. If the number is greater than 30, the procedure should return the number doubled.
Answers
#include <iostream>
#include <vector>
#include <string>
int main(int argc, char* argv[]) {
//Fill it by own.
std::vector<int> lotsOfNumbers = {0,1,2,3,4,5,6,7,8,9};
//Loop to find odd numbers.
for(int i=0;i<lotsOfNumbers.size(); i++) {
if(lotsOfNumbers[i]%2!=0) std::cout << lotsOfNumbers[i] << std::endl;
else continue;
}
return 0;
}
Situation B:#include <iostream>
#define check(x) ((x>30) ? 2*x : 30-x)
int main(int argc, char* argv[]) {
std::cout << check(15) << std::endl;
std::cout << check(-2) << std::endl;
std::cout << check(30) << std::endl;
std::cout << check(78) << std::endl;
return 0;
}


A taxi cab costs $1.25 for the first mile and $0.25 for each additional mile. Write an
equation for the total cost of a taxi ride, where x is the number of miles that you can ride for
$8.00.
Answers
Answer:
0.25x+1.25=8
Explanation:
Hope this helps
A user pays for retail purchase by placing a smart phone next to the merchant's reader.Which of the following mobile connections is used?A. MicroUSBB. BluetoothC. LightningD. NFC
Answers
OLAP (online analytical processing) software is the software to perform various high-speed analytics of large amounts of data from a data center, data mart, or other integrated, centralized data store.
What is the use of Online Analytical Processing (OLAP)?OLAP provides pre-calculated data for various data mining tools, business modeling tools, performance analysis tools, and reporting tools.
OLAP can help with Planning and Budgeting andFinancial Modeling. Online Analytical Processing (OLAP) is included in many Business Intelligence (BI) software applications. It is used for a range of analytical calculations and other activities.
Therefore, OLAP (online analytical processing) software is the software to perform various high-speed analytics of large amounts of data from a data center, data mart, or other integrated, centralized data store.
Learn more about Online Analytical Processing (OLAP):
brainly.com/question/13286981
#SPJ1
which would allow humas to access groundwater
Answers
Answer:
Snorkel,
Explanation:
So I couldn't remember that thing in gta that lets you breathe underwater but snorkels let you breathe under the water so what's the big deal I hope I helped enough. =P
Which PlayStation was the first to allow connection between it and computer network
Answers
If you're talking about connecting to the internet internet, it would be the PS2. You could buy an adapter for an ethernet cable to allow for online play.
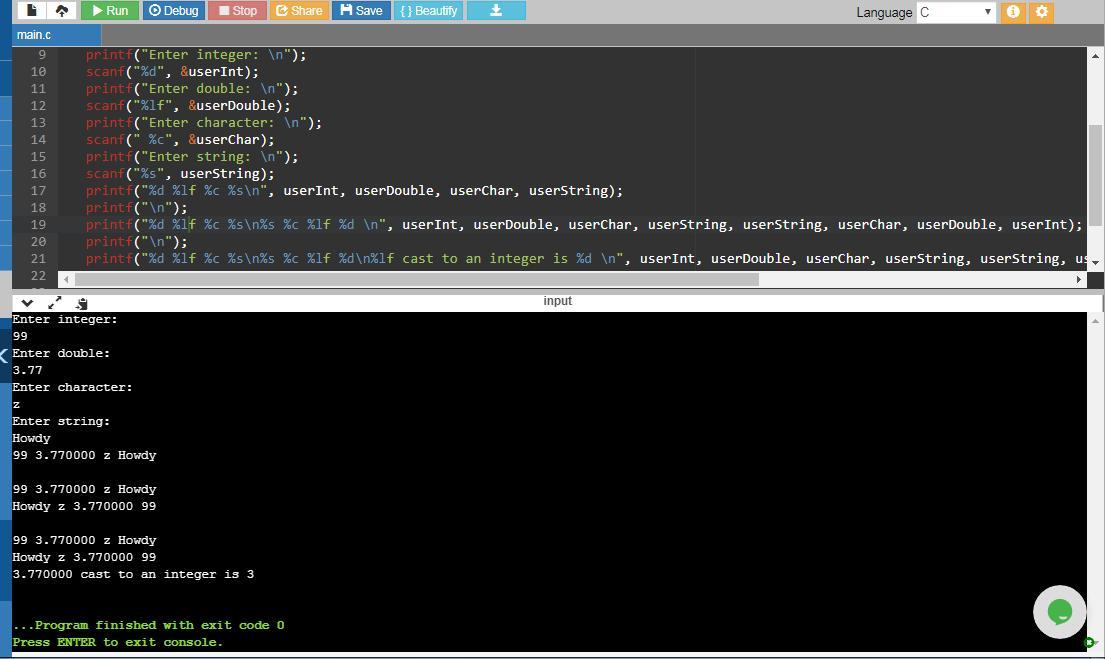
2.36 LAB: Warm up: Variables, input, and casting (1) Prompt the user to input an integer, a double, a character, and a string, storing each into separate variables. Then, output those four values on a single line separated by a space. Enter integer: 99 Enter double: 3.77 Enter character: z Enter string: Howdy 99 3.770000 z Howdy (2) Extend to also output in reverse. (1 pt) Enter integer: 99 Enter double: 3.77 Enter character: z Enter string: Howdy 99 3.770000 z Howdy Howdy z 3.770000 99 (3) Extend to cast the double to an integer, and output that integer. (2 pts) Enter integer: 99 Enter double: 3.77 Enter character: z Enter string: Howdy 99 3.770000 z Howdy Howdy z 3.770000 99 3.770000 cast to an integer is 3
Answers
Answer:
The entire program is:
#include <iostream>
using namespace std;
int main() {
int userInt;
double userDouble;
char userChar;
string userString;
cout<<"Enter integer:"<<endl;
cin>>userInt;
cout<<"Enter double:"<<endl;
cin>>userDouble;
cout<<"Enter character:"<<endl;
cin>>userChar;
cout<<"Enter string:"<<endl;
cin>>userString;
cout<<userInt<<" "<<userDouble<<" "<<userChar<<" "<<userString<<endl;
cout<<endl;
cout<<userInt<<" "<<userDouble<<" "<<userChar<<" "<<userString<<endl<<userString<<" "<<userChar<<" "<<userDouble<<" "<<userInt<<endl;
cout<<endl;
cout<<userInt<<" "<<userDouble<<" "<<userChar<<" "<<userString<<endl<<userString<<" "<<userChar<<" "<<userDouble<<" "<<userInt<<endl<<userDouble<<" cast to an integer is "<<(int)userDouble;
return 0; }
The program in C language:
#include <stdio.h>
int main() {
int userInt;
double userDouble;
char userChar;
char userString[50];
printf("Enter integer: \n");
scanf("%d", &userInt);
printf("Enter double: \n");
scanf("%lf", &userDouble);
printf("Enter character: \n");
scanf(" %c", &userChar);
printf("Enter string: \n");
scanf("%s", userString);
printf("%d %lf %c %s\n", userInt, userDouble, userChar, userString);
printf("\n");
printf("%d %lf %c %s\n%s %c %lf %d \n", userInt, userDouble, userChar, userString, userString, userChar, userDouble, userInt);
printf("\n");
printf("%d %lf %c %s\n%s %c %lf %d\n%lf cast to an integer is %d \n", userInt, userDouble, userChar, userString, userString, userChar, userDouble, userInt, userDouble, (int)userDouble); }
Explanation:
Lets do the program step by step:
1) Prompt the user to input an integer, a double, a character, and a string, storing each into separate variables. Then, output those four values on a single line separated by a space:
Solution:
The program is:
#include <iostream> //to use input output functions
using namespace std; //to identify objects cin cout
int main() { //start of main method
//declare an integer, a double, a character and a string variable
int userInt; //int type variable to store integer
double userDouble; //double type variable to store double precision floating point number
char userChar; //char type variable to store character
string userString; //string type variable to store a string
cout<<"Enter integer:"<<endl; //prompts user to enter an integer
cin>>userInt; //reads the input integer and store it to userInt variable
cout<<"Enter double:"<<endl; //prompts user to enter a double type value
cin>>userDouble; //reads the input double value and store it to userDouble variable
cout<<"Enter character:"<<endl; //prompts user to enter a character
cin>>userChar; //reads the input character and store it to userChar variable
cout<<"Enter string:"<<endl; //prompts user to enter a string
cin>>userString; //reads the input string and store it to userString variable
cout<<userInt<<" "<<userDouble<<" "<<userChar<<" "<<userString<<endl; //output the values on a single line separated by space
So the output of the entire program is:
Enter integer: 99 Enter double: 3.77 Enter character: z Enter string: Howdy 99 3.77 z Howdy
(2) Extend to also output in reverse.
Now the above code remains the same but add this output (cout) statement at the end:
cout<<userString<<" "<<userChar<<" "<<userDouble<<" "<<userInt;
Now the output with the same values given as input is:
Enter integer: 99 Enter double: 3.77 Enter character: z Enter string: Howdy
99 3.77 z Howdy Howdy z 3.77 99
(3) Extend to cast the double to an integer, and output that integer.
The rest of the code remains the same but add the following output (cout) statement in the end:
cout<<userDouble<<" cast to an integer is "<<(int)userDouble;
Now the output with the same values given as input is:
Enter integer: 99 Enter double: 3.77 Enter character: z Enter string: Howdy 99 3.77 z Howdy Howdy z 3.77 99 3.77 cast to an integer is 3

Answer:
howdy
Explanation:
which cable type suffers from electromagnetic interference (emi)?
Answers
The cable type that suffers from Electromagnetic Interference (EMI) is Unshielded Twisted Pair (UTP) cable.
What is EMI?
Electromagnetic Interference is the process by which electromagnetic waves (EM) generated by one device interfere with the operation of another device, causing unwanted and potentially harmful results.
What is a UTP cable?
A type of cable used in telecommunications, Ethernet networks, and video transmission that is composed of four pairs of wires, each of which is twisted together. The twisting lowers the crosstalk between the wires, which is electromagnetic interference that happens between the wires. The twist also lowers the amount of external interference the cable receives.
Cable Shielding: Shielding helps to protect the cable from EMI. When electrical devices and cables are located near one another, there is a risk of interference. Shielding a cable helps to reduce the electromagnetic field around the conductor, which can lead to a drop in interference levels. Twisted pair cables are the least expensive and most commonly utilized type of cable. This type of cable suffers from EMI and is not shielded. When the cable is exposed to EMI, the twisting between the pairs provides some degree of noise reduction, but it may not be sufficient to filter out all noise or interference.
Learn more about Electromagnetic Interference:
https://brainly.com/question/14661230
#SPJ11
which technology goes beyond virtual machines and extends to virtual storage networks and virtualized networking? group of answer choices wac vpn containers hci
Answers
The technology that goes beyond virtual machines and extends to virtual storage networks and virtualized networking is HCI (Hyper-Converged Infrastructure).The correct answer is option D.
HCI is a software-defined infrastructure that combines computing, storage, and networking resources into a single, integrated system. It eliminates the need for separate hardware components by virtualizing these resources and making them available through a unified management interface.
HCI extends virtualization beyond virtual machines by incorporating virtual storage networks and virtualized networking. With HCI, storage resources are abstracted and pooled together, allowing for flexible allocation and management of storage capacity across the infrastructure. This virtual storage network enables efficient data storage and retrieval, and it can be easily scaled up or down based on the organization's needs.
Moreover, HCI incorporates virtualized networking, which virtualizes the network infrastructure and enables software-defined networking capabilities.
This allows administrators to dynamically configure and manage network resources, such as switches, routers, and firewalls, through a centralized management interface.
By leveraging HCI, organizations can achieve greater agility, scalability, and cost-efficiency in their IT infrastructure. It provides a foundation for building highly virtualized and software-defined data centers, empowering businesses to adapt to evolving technology requirements and optimize resource utilization.
For more such questions networking,click on
https://brainly.com/question/28342757
#SPJ8
The probable question may be:
which technology goes beyond virtual machines and extends to virtual storage networks and virtualized networking? group of answer choices
A. wac
B. vpn
C. containers
D. hci
Assume double[] scores = {1, 2, 3, 4, 5}, what value does java.util.arrays.binarysearch(scores, 3.5) return?
Answers
Double[ ] scores = {1, 2, 3, 4, 5}.
value does java.util.arrays.binarysearch(scores, 3.5) return is -4.
What do you mean by sets?A set is a collection of components or numbers or objects, represented within the curly brackets { }. For instance: {1,2,3,4} is a set of numbers.
What is meant by sets in?
set, in mathematics and logic, any collection of objects (elements), which may be mathematical (e.g., numbers and functions) or not.
A set is generally represented as a list of all its members enclosed in braces. The intuitive idea of a set is presumably even older than that of number.
To learn more about set, refer
https://brainly.com/question/24700823
#SPJ4
discuss different generation of computer with the technologies used in each generation
Answers
Answer: Each generation is defined by a significant technological development that changes fundamentally how computers operate – leading to more compact, less expensive, but more powerful, efficient and robust machines. These early computers used vacuum tubes as circuitry and magnetic drums for memory.
Explanation:
A circle has a circumference of 113. 4113. 04113, point, 04 units. What is the diameter of the circle?
Answers
The diameter of the circle is approximately 36 units. The circumference of a circle is the distance around its perimeter. In this case, the given circumference is 113.04113 units.
To find the diameter, we can use the formula: Diameter = Circumference / π. Since the value of π is approximately 3.14159, we divide the given circumference by π. This gives us a diameter of approximately 36 units. The diameter is a straight line passing through the center of the circle, and it is equal to twice the radius. Knowing the diameter is useful for various calculations and measurements related to the circle, such as finding the area or determining the size of objects that can fit within it.
learn more about circle here:
https://brainly.com/question/30409681
#SPJ11
what is the difference between list and array with examples
Answers
List is utilized to gather things that as a rule comprise of components of different data types. An array is additionally a imperative component that collects a few things of the same information sort. List cannot oversee number-crunching operations. array can oversee math operations.
What is the difference between list and array?In programming, a list and an cluster are two information structures used to store and control collections of values. The most contrast between them is the way they store and get to the information.
So, A list is an requested collection of things, and each thing can be of a distinctive information sort. Array: An cluster is additionally an requested collection of items, but all things must be of the same information sort.
Learn more about array from
https://brainly.com/question/24275089
#SPJ1