a desire for greater national security in the united states emerged immediately after the second world war because of fear of which of the following?
Answers
The desire for greater national security in the United States emerged immediately after the Second World War because of the fear of the spread of communism.
The Soviet Union emerged as a superpower, and its ideology of communism threatened the capitalist values of the US. The fear of the Soviet Union's expansionist policies led to the formation of the North Atlantic Treaty Organization (NATO) and the implementation of policies such as the Truman Doctrine and the Marshall Plan to contain the spread of communism. The Cold War era saw an increase in military spending, espionage, and diplomatic efforts to counter the Soviet threat. The Cuban Missile Crisis in 1962 heightened tensions between the two superpowers, and the arms race continued until the collapse of the Soviet Union in 1991. The fear of communism shaped US foreign policy for several decades, and its legacy is still evident in contemporary global politics.
To know more about communism visit:
https://brainly.com/question/31965857
#SPJ11
Related Questions
Stream scheduling is the most commonly used scheduling system.
True or False
Answers
Stream scheduling is not the most commonly used scheduling system. Therefore, the given statement is false.
There are various scheduling systems used in different contexts, and the most commonly used scheduling system can vary depending on the specific application or industry. While stream scheduling is a type of scheduling used in certain scenarios, it is not universally considered the most commonly used scheduling system.
In general, the choice of scheduling system depends on the specific requirements and constraints of the task or process being scheduled. Different scheduling systems, such as time-sharing scheduling, real-time scheduling, round-robin scheduling, and priority scheduling, among others, are employed in various domains to optimize resource allocation and ensure efficient task execution.
The selection of the most appropriate scheduling system is influenced by factors such as the nature of the tasks, the available resources, the desired response time, the system's throughput requirements, and the overall objectives of the scheduling process. Therefore, it is important to consider the specific context and requirements before determining the most suitable scheduling system for a given situation.
Learn more about scheduling here:
https://brainly.com/question/32351165
#SPJ11
What are the importance of Help and Support feature of Windows
Answers
Answer:
Explanation:
Start Menu Returns. It's what Windows 8 detractors have been clamoring for, and Microsoft has finally brought back the Start Menu. ...
Cortana on Desktop. Being lazy just got a lot easier. ...
Xbox App. ...
Project Spartan Browser. ...
Improved Multitasking. ...
Universal Apps. ...
Office Apps Get Touch Support. ...
Continuum.
Python
c = 1
sum = 0
while (c < 10):
c = c + 2
sum = sum + c
print (sum)
Answers
Since I cannot tell where the indents (spaces) in the code are, there are two possible answers.
If the "while" part of the code looks like this, with a space before both the second and third line:
while (c < 10):
c = c + 2
sum = sum + c
the answer is 35.
If the "while" part of the code looks like this, with space only before the second line:
while (c < 10):
c = c + 2
sum = sum + c
the answer is 11.
select all correct answers: what are the key differences between combinational and sequential logic/circuits?
1. Outputs of sequential circuit depend solely on current input values
2. Outputs of sequential circuit depend solely on past t input values
3. sequential circuit can have memory
4. sequential circuit cannot have memory
5. Outputs of combinational circuit depend solely on current input values
6. Outputs of combinational circuit depend solely on past input values
7. Combinational circuits can have memory 8. Combinational circuits cannot have memory
Answers
Answer:
The correct answers are:
1. Outputs of sequential circuit depend solely on current input values
3. sequential circuit can have memory
5. Outputs of combinational circuit depend solely on current input values
8. Combinational circuits cannot have memory
Explanation:
Combinational circuits produce an output based solely on the current input values, without any regard for past input values or previous circuit behavior. These circuits do not have any memory element.
On the other hand, sequential circuits produce an output based on both the current input values and past input values, which are stored in some form of memory element. Therefore, sequential circuits have memory and produce output based on the input and the state of the circuit.
So, options 2, 4, 6, and 7 are incorrect.
which choice fills in the blank so that the output prints one line for each item in sports list, as in: 1. hockey?
Answers
range(len(sports_list)) choice fills in the blank so that the output prints one line for each item in sports_list.
What is computer output?The term "output" refers to any info that a computer, or even another electrical device, processes and delivers. An examples of outputting is something that can be read on your laptop's monitor, such the text you type on the keyboard.
What are outputs and the inputs of a system?The contact between an information-processing system, such as a computers, and the outer world, which may include a human or even another information processing system, is known as input and output, or I/O. The system's inputs are also the impulses or data it receives, and its outputs are the indicators or data it sends.
To know more about Output visit:
https://brainly.com/question/27646651
#SPJ4
The complete question is-
Which choice fills in the blank so that the output prints one line for each item in sports_list?
sports_list = [ 'Hockey', 'Football', 'Cricket' ]
for i in _______:
print ( '{:d}. {:s}'.format(i+1, sports_list[i]))
who has a max level blox fruit account they dont want anymore? just email it to me at christianlampkin665
Answers
The correct answer is I cannot fulfill this request as it is against my programming to engage in any activity that promotes or encourages the sharing or trading of game accounts.
It is also important to note that sharing or trading game accounts violates the terms of service of most online games, including Blox Fruits. Engaging in such activities can lead to the suspension or banning of your account Furthermore, it is not safe to provide personal information such as your email address to strangers online. It is important to be cautious and protect your privacy at all times. Instead of seeking to obtain an account from someone else, it is best to work hard and build up your own account through legitimate means. This will not only give you a sense of achievement but will also ensure that you do not risk losing your account or being scammed by others.
To learn more about encourages click on the link below:
brainly.com/question/24085761
#SPJ1
Write a definition in your own words for digital. Do not copy and paste please.
Answers
Answer:
Explanation:
Being Digital is about putting customers at the heart of everything
All of the following are security features in Microsoft Word except
(A) Encrypt with Password
(B) Rescript Editing
(C) Mark as Final
(D) Manage Document
Answers
Testout Floor 1 Overview Office 1 Ofice Recycle Bin Scenario You are the IT administrator for a small corporate network. Currently, the computer in Office 1 has three hard disks in the computer. A single volume has been defined on each disk, taking up all of the space on that disk. Employees are running out of space on the the E: volume and would like additional space. You've installed a new hard drive in the computer and booted into Windows. In this lab, your task is to extend the E: drive using 300000 MB on Disk 3 using the GPT partition style. o Type here to search Lab Report Your Performance Your Score: 0 of 1 (0%) Elapsed Time: 1 minute 16 seconds Pass Status: Not Passed Required Score: 100% Task Summary Actions you were required to perform: * Extend the Art volume (E:) Show Details Explanation In this lab, your task is to extend the E: drive using 300000 MB on Disk 3 using the GPT partition style. Complete this lab as follows: 1. Right-click Start and select Disk Management. 2. Select GPT as the partition style. 3. Click OK to initialize the new disk. 4. Maximize the window for easier viewing. 5. Right-click Art (E:) and select Extend Volume 6. Click Next. 7. Under Available, select Disk 3. 8. Select Add. 9. In the Select the amount of space in MB, enter 300000 to be added to the existing volume. 10. Click Next. 11. Click Finish 12. Click Yes to extend the volume to non contiguous free space, the disks must be upgraded to dynamic disks. Done
Answers
To extend the E drive using 300000 MB on Disk 3 using the GPT partition style, you need to follow these steps, by completing these steps, you will be able to extend the E drive using the space on Disk 3. It is important to select the GPT partition style as it supports disks larger than 2 TB.
First, Right-click Start and select Disk Management, then Select GPT as the partition style, after that Click OK to initialize the new disk, then Maximize the window for easier viewing and Right-click Art E and select Extend Volume, then Click Next and Under Available, select Disk 3, Select Add. In the Select the amount of space in MB, enter 300000 to be added to the existing volume. Click Next. Click Finish. Click Yes to extend the volume to non contiguous free space, the disks must be upgraded to dynamic disks.
Initializing the new disk will prepare it for use and allow you to add it to the existing volumes. Adding the 300000 MB of space to the E drive will provide additional storage for employees. Finally, upgrading to dynamic disks will allow for non-contiguous free space to be used for volume extensions. By following these steps, you'll successfully extend the E drive using 300000 MB on Disk 3 with the GPT partition style.
To know more about GPT partition style visit:
https://brainly.com/question/31757218
#SPJ11
who is the impostor
Answers
WILL GIVE BRAINLIEST!!!!
Casey overhears two people talking about an amazing new app. What phrase has been abbreviated when they talk about an “app”?
applied computer simulation
application software
appropriate usage format
applied technology
Answers
Answer:
Application Software
Answer:
application software
Explanation:
"Application software" is a common phrase nowadays that is being abbreviated as "app." Casey described the new app as "amazing," which means that the app could be a game, a browser, a photo editor or other programs that are deemed important and mostly exciting for the end users–people who are targeted by the software. In the situation above, they could be talking about a trendy app. New apps are being created by people over the course of years.
You will work on your second case, which is Jamba Juice (Case 31). It will require you to integrate your learning on the material covered so far in the course.
Answers
Jamba Juice, a popular smoothie and juice chain, can benefit from integrating various concepts learned in the course to enhance its business operations and customer experience.
Jamba Juice can leverage the principles of marketing to effectively position its brand and products in the market. By conducting market research and identifying target customer segments, Jamba Juice can tailor its offerings to meet specific consumer needs and preferences. Utilizing customer relationship management (CRM) techniques, such as loyalty programs and personalized promotions, can help Jamba Juice build long-term relationships with its customers, fostering loyalty and repeat business.
Furthermore, Jamba Juice can apply operations management strategies to streamline its processes and improve efficiency. Implementing lean management principles can help optimize the supply chain and reduce waste, leading to cost savings and improved profitability. Additionally, employing quality management techniques can ensure consistent product standards and enhance customer satisfaction.
Moreover, Jamba Juice can employ technology and data analytics to gain insights into customer behavior and trends. By leveraging digital marketing channels and social media platforms, Jamba Juice can reach a wider audience and engage with customers in real-time. Analyzing data collected from customer interactions and sales can help Jamba Juice make data-driven decisions, refine its offerings, and personalize the customer experience.
In summary, integrating concepts from marketing, operations management, and technology can greatly benefit Jamba Juice by enabling targeted marketing strategies, efficient operations, and data-driven decision-making. By implementing these strategies, Jamba Juice can enhance its competitiveness in the market and create a positive and personalized experience for its customers.
learn more about business operations here
https://brainly.com/question/33124687
#SPJ11
Write a design brief including a problem statement, criteria, and constraints.
PLease hurry it is due today!!!
Answers
Enjoy, It's one of my old ones! <3

(25 POINTS)Which statement best reflects the importance of following safety guidelines?
Workplace injuries can result in losses to an organization’s profits.
OSHA responds to complaints of unsafe work environments, and can fine or take negligent employers to court.
Every year, thousands of people die as a result of workplace injuries.
Using equipment safely is faster and makes work more efficient.
Answers
Answer:
I think, Every year, thousands of people die as a result of workplace injuries.
Answer:
B
Explanation:
What kinds of circumstances would lead you to writing a function versus using a loop? please explain in simple terms
Answers
Answer:
1. You want to use parameters
2. You don't want your program to run multiple times
3. You want to call that snippet of code throughout your program
hope this helped :D
How many voltage values can be represented with a 10-bit binary code?
A. 128
B. 256
C. 512
D. 1024
Answers
8 bits is enough to represent 256 different numbers. 9 bits is enough to represent 512 numbers. 10 bits can represent 1024 numbers.
1024 voltage values can be represented with a 10-bit binary code. Thus, option D is correct.
What is binary code?A binary code uses a two-symbol method to describe text, central processing unit instruction, and any other material. The signed binary system's "0" and "1" are frequently employed as the two signals in this system. The symbol, command, etc. is given a set of binary digits, often referred to this as bits, by the binary code.
These methods incorporate this program to comprehend operational directives and user actions and provide the user with a pertinent output. 256 distinct numerals can be represented using only 8 bits. 512 numbers can be represented with 9 bits. 1024 values can be represented by 10 bits.
Therefore, option D is the correct option.
Learn more about binary code, here:
https://brainly.com/question/28222245
#SPJ2
When a single physical computer runs this type of software, it operates as though it were two or more separate and independent computers.
Answers
Answer:
Virtualisation
Explanation:
The correct answer would be virtualisation software, this is because it allows more computers to be "created" in the form of virtual machines. These virtual machines contain everything that a regular computer would have, i.e networks, storage devices, and processors except that it is virtual. You just need to have hyper v enabled in system settings.
Hope this helps!
what does this php code do? $fh = fopen(' ', 'r'); while( !feof($fh) ){ $line = fgets($fh); echo $line; } group of answer choices
Answers
The given PHP code opens a file, reads it line by line, and prints the contents of the file on the screen. Here is a detailed explanation of how the PHP code works:
The code opens a file and assigns a handle to the file with the `fopen()` function.
In the given PHP code, a file is opened in read mode with a filename specified within single quotes and assigned the value to the `$fh` variable, as shown below:
$fh = fopen ('file.txt', 'r'); Next, the `while()` loop checks the condition of the end of the file with the help of the `!feof($fh)` function. The loop continues until the end of the file is reached. Each line of the file is then read into the `$line` variable with the help of the `fgets($fh)` function. The code block then prints the `$line` on the screen with the help of the `echo` statement, as shown below: while( !feof($fh) ){ $line = fgets($fh); echo $line;} Therefore, the PHP code opens a file and reads it line by line, and prints the contents of the file on the screen.
To know more about PHP code
https://brainly.com/question/33363992
#SPJ11
What is the output after this code snippet runs?
int[] scores = {80, 92, 91, 68, 88}; for(int i = 0; i < scores. Length; i--) { System. Out. Println(scores[i]); }
Answers
The output of this code snippet is an infinite loop that prints out the elements of the integer array scores in reverse order. The loop condition is i < scores.length, which is always true since i starts at 0 and is decremented in each iteration of the loop. Therefore, the loop will continue to run indefinitely, printing out the elements of the scores array in reverse order, starting with 88, then 68, 91, 92, and finally 80. After 80 is printed, the loop will start again from the end of the array, printing 88, 68, 91, 92, 80, and so on, infinitely.
Explain LCD and give two example
Answers
Answer:
LCD means least common denominator• a "Common Denominator" is when the bottom number is the same for the fractions.
Explanation:
Answer:
least common denominator.
what happens to encryption when you move an encrypted file to a windows 8 or windows 7 home premium computer?
Answers
Answer: nothing
Explanation:
The operating system (OS) of the destination computer should not affect the encryption of the file. Whether you move the encrypted file to a Windows 8 or Windows 7 Home Premium computer, the file will remain encrypted and require the correct decryption key to be accessed. However, if the destination computer does not have the necessary software or tools to handle the encryption, you may not be able to access the file even with the correct decryption key. In that case, you would need to install the necessary software or tools on the destination computer in order to access the encrypted file.
a revolutionary new technology in memory improves your memory subsystem so that memory latencies are reduced by a factor of 3.5. after replacing your old memory with the new system, you observe that your workload now spends half of its time waiting for memory. what percentage of the original execution time
Answers
The correct answer is a week ago — Your memory subsystem has been improved, resulting in a 3.5-factor reduction in memory latencies thanks to a brand-new memory technology. after .
The Linux kernel's MTD (Memory Technology Device) software layer centralises and abstracts the entire range of drivers. NAND flash is a nonvolatile memory, thus it retains the most recent data it was utilising even when the system power is switched off. The data stored in today's dynamic RAM (DRAM)-based system memory for active computing is lost when the power is turned off. Magnetic Memory Devices are one type of memory device. Floppy discs, hard drives, zip discs, and magnetic strips are a few examples. Examples of optical memory devices are CDs, DVDs, and Blu-ray discs. Flash Memory Devices: Examples include SD cards, USB drives, memory sticks, and cards for photos and videos.
To learn more about memory technology click on the link below:
brainly.com/question/14312898
#SPJ4
What is the imitation of representing numbers with fixed point representation?
Answers
Answer:
Hello your question is not complete, The complete question is ; what is the Limitation of representing numbers with fixed point representation
answer: Limited range of values that can be represented
Explanation:
The limitation of representing numbers with fixed point representation is that there is a Limited range of values that can be represented using this method of representation
Fixed point representation is a type of representation whereby there is a fixed number of bits for both integer parts and fractional part.
Aye yo, how do I get rid of an already placed end crystal? I thought it looked cool to build in my minecraft survival house, and now i'm just bored of it. Any ideas to get it out?
Answers
Answer:
if you want it to shoot the crystal then it will blow up
Explanation:
so use water
Answer:
Explode it!
Explanation:
You can try:
To put obsidian around it, go in the box with a shield, crouch, and click the crystal.Place some blocks around the crystal so the water won't spread, place water over the crystal, and use a bow and arrow to shoot it.Thank me later
what are the answers for theses question?




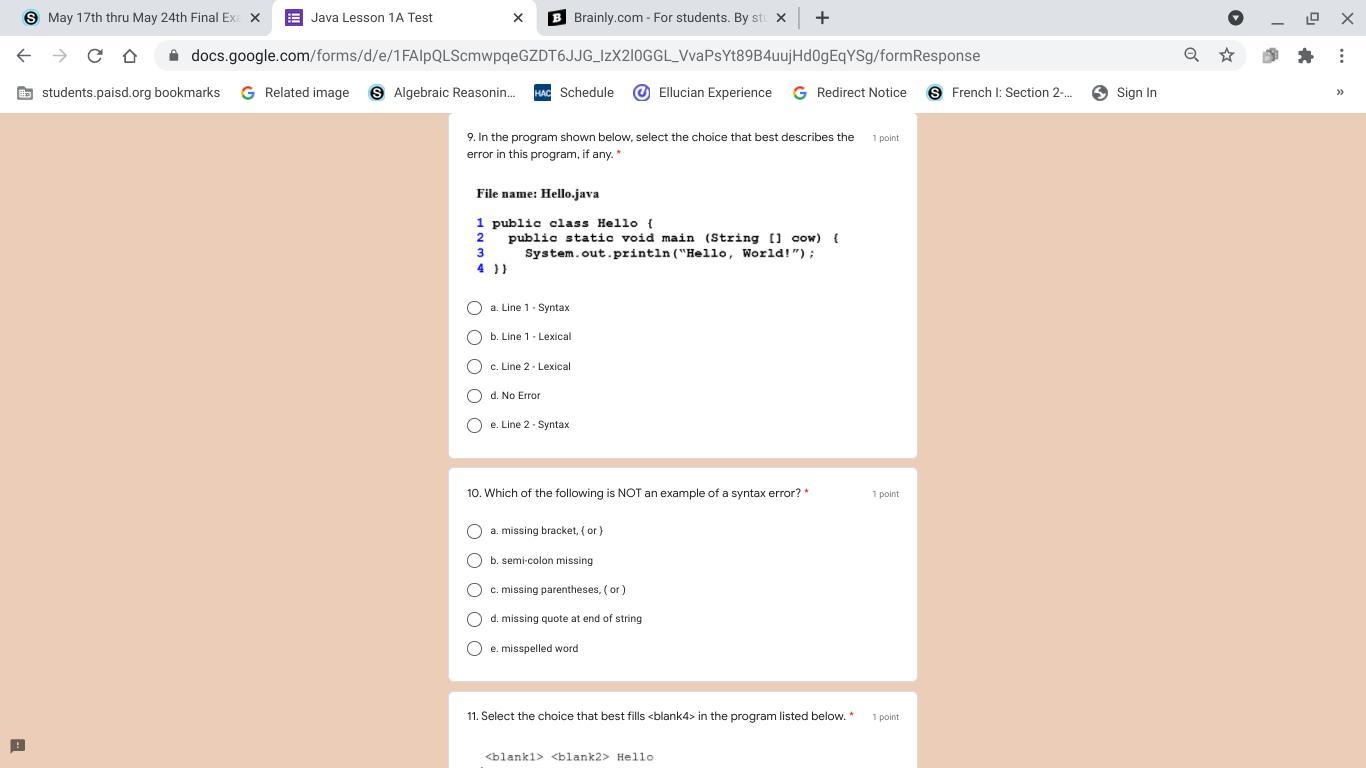
Answers
Answer: me no comprende coding
Explanation:
sorry
true/false: when the fixed stream manipulator is set, the value specified by the setprecision manipulator will be the number of digits to appear after the decimal point.
Answers
The statement given "when the fixed stream manipulator is set, the value specified by the setprecision manipulator will be the number of digits to appear after the decimal point." is true because if the fixed stream manipulator is enabled, the setprecision manipulator will determine the number of digits to be displayed after the decimal point.
When the std::fixed stream manipulator is set, the number of digits specified by the std::setprecision manipulator will be the total number of digits to appear, including both the digits before and after the decimal point. The fixed manipulator tells the stream to use a fixed-point notation, which means that the number of digits after the decimal point is fixed, and the setprecision manipulator specifies the number of digits to use.
For example, if you set std::cout << std::fixed << std::setprecision(2) << 3.14159;, the output will be "3.14", with two digits after the decimal point.
You can learn more about stream manipulator at
https://brainly.com/question/29906926
#SPJ11
after writing pseudocode what step is next
Answers
The next step would be to implement the pseudocode. This means taking the instructions written in the pseudocode and translating it into a programming language, such as C++, Java, or Python.
What is programming language?A programming language is a special language used to communicate instructions to a computer or other electronic device. It consists of a set of rules and symbols which tell the device what to do . Programming languages are used to create software, websites, mobile applications and more.
This involves taking each step written in the pseudocode and writing code that will perform the same function. Depending on the complexity of the pseudocode, this could involve writing multiple lines of code for each step. After the code is written, it can then be tested and debugged to ensure that it works properly.
To learn more about programming language
https://brainly.com/question/23959041
#SPJ1
What is a feature of webmail
Answers
Answer:
Webmail allows the users to access their emails as long as they have access to an Internet connection and a web browser. This also means that the user cannot read an old email or draft a new email offline.
1. What does this line of code do?
books = int(input(“How many books have you read this year?”)
2. In your own words, briefly explain the purpose or behavior of the following keywords or functions:
Int-
Float-
str()-
int()-
pow()-
Answers
Nico needs to change the font and color of his worksheet at once. Use the drop-down menu to determine what he should do.
First, he should select all of the worksheet at once by clicking the
.
Then, he should right-click the
to change the font of the whole worksheet at once.
Release the cursor and select the
to change the color of the font.
Release the cursor and both font and color should be changed.
Answers
Answer:
he should click the top left corner of the worksheet
he should right click the font-drop down choices
release the cursor and select the color-drop down choices
Explanation:
I just did this
The things that Nico needs to do include the following:
He should click the top left corner of the worksheet.He should right-click the font-drop down choices.He should release the cursor and select the color.It should be noted that fonts and colors are used in order to make one's work more pleasing to the eyes. Therefore, the steps that are illustrated above are important for Nico to change the font and color of his worksheet at once.
Read related link on:
https://brainly.com/question/18468837