a complete model of the skeleton that could be useful for all practical applications would b a dissected human a dissected human a 3d computer generated model a 3d computer generated model such a model is impossible such a model is impossible a 2d computer generated model
Answers
A complete model of the skeleton that could be useful for all practical applications would option C. such a model is impossible.
What is model skeleton?A skeleton model is known to be a term that tells about a classic item that can be seen or found in a lot of medical settings.
Note that Doctors often have a human skeleton model that can be accessible to quickly show the bone structure of the human body and this is often made to their patients.
Therefore, based on the above, A complete model of the skeleton that could be useful for all practical applications would option C. such a model is impossible.
Learn more about model from
https://brainly.com/question/28545111
#SPJ1
A complete model of the skeleton that could be useful for all practical applications would be
A. a 3D computer generated model
B. a 2D computer generated model
C. such a model is impossible
D. a dissected human
Related Questions
Shruti has displayed the entire text of her document in uppercase. Name the property she must have used to
achieve the same.
Cyber tools
Answers
Drag each tile to the correct box.
What are the steps involved in accepting all the changes in a document?
Click Edit
Click Accept or Reject.
Click Changes
Click Accept All
Answers
Answer:1
Explanation: Drag each tile to the correct box. What are the steps involved in accepting all the changes in a document? Click Edit Click Accept or Reject. Click Changes Click Accept All
COMPUTER ACTIVITY
help guys thank you so much!!

Answers
A type of flowchart called an Entity Relationship (ER) Diagram shows how "entities" like people, things, or ideas relate to each other in a system.
What exactly is a ER diagram?A type of flowchart called an Entity Relationship (ER) Diagram shows how "entities" like people, things, or ideas relate to each other in a system. In the fields of software engineering, business information systems, education, and research, ER Diagrams are most frequently utilized for the design or debugging of relational databases. They use a defined set of symbols like rectangles, diamonds, ovals, and connecting lines to show how entities, relationships, and their characteristics are interconnected. They follow grammatical structure, using relationships as verbs and entities as nouns.
To learn more about databases visit :
https://brainly.com/question/6447559
#SPJ1
Yahoo Messenger is an example of a/an __________ service on the Internet.
Answers
Answer:
Yahoo Messenger is an example of a service on the Internet.
Pls name me brainliest!!! ;D
This question has two parts : 1. List two conditions required for price discrimination to take place. No need to explain, just list two conditions separtely. 2. How do income effect influence work hours when wage increases? Be specific and write your answer in one line or maximum two lines.
Answers
Keep in mind that rapid prototyping is a process that uses the original design to create a model of a part or a product. 3D printing is the common name for rapid prototyping.
Accounting's Business Entity Assumption is a business entity assumption. It is a term used to allude to proclaiming the detachment of each and every monetary record of the business from any of the monetary records of its proprietors or that of different organizations.
At the end of the day, we accept that the business has its own character which is unique in relation to that of the proprietor or different organizations.
Learn more about Accounting Principle on:
brainly.com/question/17095465
#SPJ4
What does it mean to explore the context of a work?
OA. To take note of the reviewer's reaction to the work
B. To analyze how well the work will be received
C. To research its historical background and original purpose
O
D. To analyze its content and various components
Answers
To explore the context of a work means to "research its historical background and original purpose" (Option C)
What is context in research?Context is described as "the conditions that provide the backdrop for an event, statement, or concept and allow it to be completely comprehended."
Determine the Context and Background Information to find the context of a study endeavor. Find and study articles in subject reference books, dictionaries, and handbooks after you've identified your research topic and some keywords that characterize it. These articles will assist you in understanding the background of your issue (historical, cultural, and disciplinary).
Context gives the intended message significance and clarity. Context clues in a literary work form a link between the writer and the reader, providing a better knowledge of the writer's goal and direction.
Learn more about context:
https://brainly.com/question/10943525
#SPJ1
Linux a user typed in the command pwd and saw the output: /home/jim/sales/pending. how could that user navigate to the /home/jim directory?
Answers
Linux a user typed in the command pwd and saw the output: /home/jim/sales/pending. the way in which that user can navigate to the /home/jim directory? is cd ../..
What is a Directory?This refers to the special type of file that has only the information needed to access files.
Hence, we can see that Linux a user typed in the command pwd and saw the output: /home/jim/sales/pending. the way in which that user can navigate to the /home/jim directory? is cd ../..
This would take him back to the root directory which is home in the Jim directory and he can start viewing the files in their parent-child order.
Read more about directories here:
https://brainly.com/question/28391587
#SPJ1
Suppose that a disk drive has 5,000 cylinders, numbered 0 to 4999. The drive is currently serving a request at cylinder 2150, and the previous request was at cylinder 1805. The queue of pending requests, in FIFO order, is: 2069, 1212, 2296, 2800, 544, 1618, 356, 1523, 4965, 3681 Starting from the current head position, what is the total distance (in cylinders) that the disk arm moves to satisfy all the pending requests for each of the following disk-scheduling algorithms?
a. FCFS
b. SSTF
c. SCAN
d. LOOK
e. C_SCAN
f. C_LOOK
Answers
Answer:
a. FCFS
Explanation:
The AND operator outputs true except where both inputs are false.
True
or
False
Answers
Answer:
true both have to be true for it to have output
predict what the world would be like if no one tried to think critically. explain your predictions
Answers
The world would be in chaos and we would all be dead duh.
True or false: Most Brainly users are saltier than the ocean. If false, explain why.
Answers
Explanation:
btw I'm not salty........
coment on this if your user starts with dida
Answers
Answer:
oh sorry i needed points but i have a friend whos user starts with dida
Explanation:
Sebastian is working on a web page that includes both essential and non-essential information about an event that is happening at his shop. How
Answers
Sebastian can organize the essential and non-essential information about the event on his webpage in the following steps:
1. Identify the essential information: Determine the key details that visitors to the webpage need to know about the event. This may include the date, time, location, and purpose of the event.
2. Highlight the essential information: Make sure that the essential information stands out on the webpage. Use headings, bullet points, or bold text to draw attention to these important details.
3. Provide additional details: Include non-essential information about the event that may be of interest to visitors but is not crucial for understanding the event. This could include background information, special features, or testimonials.
4. Use clear formatting: Arrange the essential and non-essential information in a logical and easy-to-read manner. Consider using sections or tabs to separate the different types of information, making it clear what is essential and what is non-essential.
5. Prioritize the essential information: Place the essential information prominently on the webpage so that it is easily noticeable. This ensures that visitors can quickly find the most important details without having to search through the entire page.
In summary, Sebastian can organize the essential and non-essential information about the event on his webpage by identifying the key details, highlighting them, providing additional non-essential details, using clear formatting, and prioritizing the essential information.
#SPJ11
Learn more about Information
https://brainly.com/question/26260220
Sebastian can organize the web page by distinguishing between essential and non-essential information about the event happening at his shop. Here's how he can do it:
1. Identify essential information: Sebastian should determine the key details that visitors must know about the event, such as the date, time, location, and any important announcements or updates.
2. Prioritize essential information: Once he has identified the essential information, Sebastian should place it prominently on the web page, ensuring that it is easily visible and accessible to visitors. This could include using headings, subheadings, bullet points, or highlighting key details.
3. Separate non-essential information: Sebastian should then identify any additional details or supplementary information that is not essential for visitors to know. This could include things like event background, history, or optional activities.
4. Organize non-essential information: Sebastian can create separate sections or tabs on the web page to present the non-essential information. This way, visitors who are interested in learning more can easily access it, while those who are looking for essential details can find them without being overwhelmed.
5. Use clear and concise language: Regardless of whether it's essential or non-essential information, Sebastian should ensure that all text on the web page is written in a clear, concise, and easy-to-understand manner. This will help visitors quickly grasp the important details and navigate through the web page effectively.
By following these steps, Sebastian can create a well-organized web page that presents both essential and non-essential information about the event happening at his shop.
#SPJ11
Learn more about Web page here:
brainly.com/question/32613341
Which of the following scenarios best shows the relationship between art, commerce, and technology?
A stage director wants to develop a show that is entirely digital, except for the actors. The set will be created using 3D images projected from a state-of-the-art system. Music will be recorded and played over a digital sound system and special effects will be created using brand new software.
An artist wants to create a mural of the Statue of Liberty using individual images of Americans from across the country. She needs a software program that will allow her to take, edit, and store files, as well as software that will create her mural.
A feature-film director needs to increase sales of his movie in order to please his film studio. The artist works with a multimedia artist to rebrand the film and build a bigger following on social media.
A musician has signed a deal with a record label to create an entirely digital album using digitally created instruments and background vocals. The first tracks are not producing a realistic sound. The artist works with a multimedia artist to develop software that will create the appropriate sound and fulfill the musician’s contract.
Answers
Answer:
b
Explanation:
i think
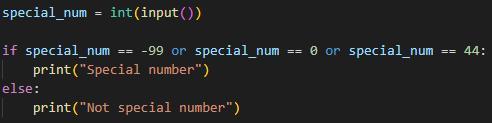
Can you solve this challenging activity?

Answers
Answer:
special_num = int(input())
if special_num == -99 or special_num == 0 or special_num == 44:
print("Special number")
else:
print("Not special number")
Explanation:
What is a user data?
Answers
Answer: Any data the user creates or owns.
Explanation:
the user being the one on the otherside of the computer, usually a human.
but examples of user data are intalled programs, uploads, word documents created by user (computer user)
which members of the following class are private?class employee { string name; double salary; double to hourly(double); void set name(string); string get name(); void set salary(double); double get salary(); double get weekly salary(); double get monthly salary();} of of of the data members, but none of the member of them except for the getter and setter functions
Answers
The data members "name" and "salary" of the class employee are private. The getter and setter functions are the only way to access or modify these private data members from outside the class.
This is an example of encapsulation, where the internal details of the class are hidden and can only be accessed through specific methods. This helps to ensure the integrity of the data and prevent unintended modifications.
Hi, to answer your question about which members of the given employee class are private: In the provided class definition, you did not specify the access specifiers (public, protected, or private) for the members. In C++, if no access specifier is provided, class members are private by default. So, all the data members and member functions in the employee class are private.
Class definition: class employee {string name; double salary; double to_hourly(double); void set_name(string); string get_name(); void set_salary(double) double get_salary(); double get_weekly_salary(); double get_monthly_salary();
} Please note that it is generally good practice to make data members private and provide public getter and setter functions to access and modify them. This helps maintain data integrity and encapsulation in your code.
To know more about data visit:
https://brainly.com/question/30051017
#SPJ11
The list shows the steps in developing a research plan.
Which two steps are out of order?
1. Select the topic.
2. Create a schedule.
3. Set goals.
4. Write down research questions.
5. Identify research method(s).
6. Find and evaluate sources.
O 5 and 6
O4 and 5
O 3 and 4
O 2 and 3
Answers
Answer:
4 and 5 are out of order
Explanation:
Answer:
Do u still need help?
Explanation:
P1: Write a function called FindPrimes that takes 2 scalars, lowerRange and upperRange, and produces a 1D array called outPrimes1. The function finds all the prime numbers within the range defined by lower Range and upperRange. The output outPrimes1 is a 1D array with all the primes within the specified range. Remember that a prime number is a whole number greater than 1 whose only factors are 1 and itself. The input arguments (lowerRange, upperRange) are two (numeric) scalars. The output argument (outPrimes1) is a 1xm (numeric) array. Restrictions: Do not use the primes() function. Hint: use a for loop to go through the entire range and check if the number is prime or not using the isprime() function. For example: For the given inputs: lowerRange = 2; upperRange= 20; On calling FindPrimes: outPrimes1 Find Primes (lower Range, upperRange) produces, outPrimes1 = 1x8 2 3 5 7 11 13 17 19 In outPrimes1 all the prime numbers contained within the range of lowerRange=2 and upperRange=20 are shown. P2 Complete the function FindPrimes to produce a 1D array called outPrimes2. outPrimes2 is a copy of outPrimes1 but contains only the prime numbers that summed together are less than the highest element of outPrimes 1. The input arguments (lowerRange, totalNumbers) are two (numeric) scalars. The output argument (outPrimes2) is a 1 x n (numeric) array. Restrictions: Do not use the primes() function. Hint: use a while loop to go through the outPrimes1 array and and check if the total sum is lower than the highest primer number in outPrimes1. For example: For the given inputs: lower Range = 2; upperRange=20; On calling FindPrimes: outPrimes2= Find Primes (lower Range, upperRange) produces, outPrimes2 = 1x4 2 3 5 7 The output outPrimes2 only contains the prime numbers 2 3 5 7. The sum of all the prime numbers in outPrimes2 is 17, less than 19, which is the highest prime number in outPrimes1. Function > 1 function [outPrimes1, outPrimes2] = FindPrimes (lower Range, upper Range) %Enter your name and section here 2 3 4 endl Code to call your function > 1 lower Range = 2; 2 upperRange=20; 3 [out Primes1, outPrimes2]=FindPrimes (lower Range, upper Range) Save C Reset MATLAB Documentation C Reset
Answers
The function FindPrimes takes two scalar inputs, lowerRange and upperRange, and returns two 1D arrays: outPrimes1 and outPrimes2. The function finds all the prime numbers within the range specified by lowerRange and upperRange.
1. The FindPrimes function first uses a for loop to iterate through the entire range defined by lowerRange and upperRange. Within the loop, each number is checked for primality using the isprime() function. If a number is found to be prime, it is appended to the outPrimes1 array.
2. Once outPrimes1 is populated with all the prime numbers within the range, a while loop is used to iterate through the elements of outPrimes1. The loop checks if the sum of the prime numbers encountered so far is less than the highest prime number in outPrimes1. If the sum is less, the prime number is appended to the outPrimes2 array.
3. Finally, the function returns both outPrimes1 and outPrimes2 as output. outPrimes1 contains all the prime numbers within the specified range, while outPrimes2 contains a subset of prime numbers whose sum is less than the highest prime number in outPrimes1.
4. In the given example, FindPrimes with lowerRange = 2 and upperRange = 20 would produce outPrimes1 = [2, 3, 5, 7, 11, 13, 17, 19] and outPrimes2 = [2, 3, 5, 7]. The sum of the prime numbers in outPrimes2 is 17, which is less than the highest prime number in outPrimes1 (19).
Learn more about for loop here: brainly.com/question/30494342
#SPJ11
please answer fast..

Answers
Answer:
a. False.
b. True.
c. False.
d. False.
Explanation:
a. False: Data stored in RAM are called firmware. It's the data stored in read only memory (ROM) are called firmware.
Radom Access Memory (RAM) can be defined as the main memory of a computer system which allow users to store commands and data temporarily.
Generally, the Radom Access Memory (RAM) is a volatile memory and as such can only retain data temporarily.
All software applications temporarily stores and retrieves data from a Radom Access Memory (RAM) in computer, this is to ensure that informations are quickly accessible, therefore it supports read and write of files.
b. True: a register is a temporary storage device within the central processing unit (CPU) of a computer system. Thus, it is designed to quickly accept, store and transfer data or instructions being used on a computer system.
c. False: the result obtained after data processing is given by input devices. Any result obtained after data processing is given by output devices such as speakers, monitor, projector, etc.. Input devices such as keyboard, mouse, scanner, etc., are used for entering the data into a system.
d. False: E-shopping allows us to make deposits, withdrawal and pay bills with the click of a mouse.
E-shopping can be defined as a marketing strategy that deals with meeting the needs of consumers, by selling products or services to the consumers over the internet.
This ultimately implies that, E-shopping is strictly based on the buying and selling of goods or services electronically, over the internet or through a digital platform. Also, the payment for such goods or services are typically done over the internet such as online payment services.
public int sup_guys(int a, int b) {} //main method int c = 1; int d = 2; sup_guys(c,d) What are the actual parameters in this example? a) b and d b) c and d c) a and c d) a and b
Answers
The actual parameters of sup_guys(int a, int b) are c and d, which are the values passed when calling the function. The answer is b).
The actual parameters are: c and d. In the code given below,
public int sup_guys(int a, int b) {}
//main method int c = 1;
int d = 2; sup_guys(c,d)
the function named sup_guys takes two parameters as input: a and b, but when this function is called in the main method, it is called with two arguments: c and d. Thus, the actual parameters are c and d.Here, c = 1 and d = 2,
so calling sup_guys(c,d) means that we are calling the function with the values of c and d which are actual parameters, instead of a and b. In short, the values passed when calling a function are called actual parameters. Therefore, the answer is option b) c and d.
To know more about actual parameters Visit:
https://brainly.com/question/23799067
#SPJ11
What could be one use for a business report from a manufacturer?
Question 3 options:
share details of the new employee benefits program
share details of a job offer, such as start date and salary
share quarterly earnings with investors
share an apology with a disgruntled customer
help
Answers
The most appropriate use for a business report from a manufacturer would be to share quarterly earnings with investors
Write a short note on business reports.Business reports are formal documents that present information and data about a specific business topic or issue. They are often used to analyze business operations, evaluate performance, and make informed decisions. Business reports typically follow a standard format and include an introduction, methodology, results, and conclusions.
The purpose of business reports may vary, including providing information to stakeholders, informing business decisions, identifying areas for improvement, or documenting processes and procedures. Business reports may include various types of data such as financial information, market trends, customer feedback, or performance metrics.
Business reports can be generated for internal or external audiences and can be presented in different formats such as written reports, presentations, or visual aids. Overall, business reports are an important tool for businesses to communicate information and data effectively and make informed decisions.
To learn more about business report, visit:
https://brainly.com/question/4025229
#SPJ1
What happens on a phone or tablet if it runs out of RAM to run processes? Is there additional storage?
Answers
Answer:
Ur phone/tablet starts to become laggy
Explanation:
how can you ensure the confidentiality, integrity, and availability (cia) of the web application and service?
Answers
To ensure the confidentiality, integrity, and availability (CIA) of a web application and service, you can implement various security measures such as using encryption for data transmission, employing access controls and authentication mechanisms, conducting regular security audits, and implementing robust backup and disaster recovery plans.
To ensure the confidentiality, integrity, and availability (CIA) of a web application and service, you can implement various security measures such as using encryption for data transmission, employing access controls and authentication mechanisms, conducting regular security audits, and implementing robust backup and disaster recovery plans.
Confidentiality refers to protecting sensitive information from unauthorized access. Encryption can be used to secure data transmission and storage, ensuring that only authorized users can access and decipher the data.
Integrity involves ensuring that the data and resources of the web application are accurate and unaltered. Implementing access controls, authentication mechanisms, and employing secure coding practices can help prevent unauthorized modifications or tampering of data.
Availability refers to the accessibility and uptime of the web application and service. Regular security audits, monitoring systems, and implementing robust backup and disaster recovery plans can help mitigate risks and ensure continuous availability of the application.
By combining these security measures and best practices, you can establish a secure environment for the web application, safeguarding the confidentiality of sensitive information, maintaining the integrity of data, and ensuring the availability of the service to authorized users.
To know more about confidentiality, integrity, and availability (CIA) click here,
https://brainly.com/question/29789398
#SPJ11
What type of edge does UML use to denote interface implementation? Group of answer choices A dotted arrow from the interface to the class terminated with a triangular tip. A dotted arrow from the interface to the class terminated with an open arrow tip. A dotted arrow from the class to the interface terminated with an open arrow tip. A dotted arrow from the class to the interface terminated with a triangular tip.
Answers
Answer:
A. A dotted arrow from the class to the interface terminated with a triangular tip
Explanation:
In your implementation of the ALU there is no need to detect or handle overflow, even though try to think when an overflow can occur.
When adding numbers with different signs, overflow cannot occur, since the sum must be no larger than one of the numbers.
What happens when the signs of the numbers are the same? What happens in case of subtraction?
How to detect when an overflow does occur?
Answers
Overflow can occur when adding or subtracting numbers with the same signs in an ALU. To detect overflow, we examine the carry-out from the most significant bit (MSB) of the ALU's result during addition or subtraction operations.
When adding two numbers with the same sign, if the carry-out from the MSB is different from the carry-in to the MSB, an overflow has occurred. Similarly, during subtraction, if the carry-out from the MSB is different from the expected carry-out, an overflow has occurred. Overflow indicates that the result of the operation cannot be accurately represented using the available number of bits. Handling overflow typically involves setting a specific flag in the ALU's status register to indicate the occurrence.
learn more about Overflow here
brainly.com/question/13014271
#SPJ11
pls help. this is for my keyboarding and applications class.


Answers
Answer:
Answer is listed below
Explanation:
icons - pictures that represents applications, files, or folders
Quick Launch - place where frequently used programs can be opened
Start menu - list of items that can be opened by clicking on their names
system tray - shows the programs that are always running
taskbar - displays open applications or files
Which type of computer processing is used to find a word on a web page?
Comparing
Counting
Finding a match
If-then
Answers
Finding a match is used to find a word on a web page.
Computer processingProcessing is the transformation of the input data to a more meaningful form (information) in the CPU. Output is the production of the required information, which may be input in future.
There are four common types of processing:
if/then (conditionals), finding a match (searching) counting and comparing.Find out more on computer processing at: https://brainly.com/question/474553
Explain the difference between ‘data’ and ‘information’ and
why data is considered
as a ‘fragile asset’?
Answers
The difference between 'data' and 'information' is that 'data' is a collection of raw figures and facts, whereas 'information' is data that has been processed and interpreted for a specific purpose. Data is a fragile asset, meaning that it needs to be properly stored and protected to prevent loss or corruption.
Data is a collection of raw, unprocessed figures and facts, such as numbers, symbols, or characters, that do not have any meaning on their own. Data is meaningless until it is processed, organized, and interpreted to make it useful, this processed and interpreted data is referred to as information. Information is useful for decision-making and problem-solving. Data and information are both important assets to an organization, but data is a fragile asset because it can be lost or corrupted if it is not properly stored and protected. Data loss can occur due to a variety of reasons, including hardware failure, power outages, and human error. Organizations must take measures to ensure that their data is backed up regularly and stored securely to prevent loss or corruption of data.
Know more about 'data' and 'information, here:
https://brainly.com/question/14547207
#SPJ11
what is the purpose of using protocol-dependent modules in eigrp?
Answers
Protocol-dependent modules (PDMs) in EIGRP are used to adapt and integrate EIGRP with different network layer protocols, enabling efficient routing information exchange and neighbor relationships.
In the context of Enhanced Interior Gateway Routing Protocol (EIGRP), protocol-dependent modules (PDMs) serve an important purpose. EIGRP is a routing protocol used in computer networks to exchange routing information and determine the best paths for data transmission.
When EIGRP operates in a network environment that includes multiple network layer protocols (such as IP, IPv6, IPX), it needs to adapt and integrate with each specific protocol. This is where PDMs come into play.
The purpose of using PDMs in EIGRP is to handle the protocol-specific details of different network layer protocols. Each PDM is responsible for understanding and interacting with a particular protocol. It ensures that EIGRP can effectively communicate with and establish neighbor relationships with routers running different protocols.
By incorporating PDMs, EIGRP can support and seamlessly operate in heterogeneous network environments, where multiple protocols are being used. This adaptability allows for efficient routing information exchange, synchronization of routing tables, and establishment of neighbor relationships across various network layer protocols.
In summary, PDMs in EIGRP facilitate the integration and interoperability between EIGRP and different network layer protocols, enabling efficient routing operations in diverse network environments.
Learn more about EIGRP here:
https://brainly.com/question/32543807
#SPJ11