A binary one-to-many (1:N) relationship in an E-R diagram is represented by adding the primary key attribute (or attributes) of the entity on the one side of the relationship as a(n) ________ in the relation that is on the many side of the relationship.
Unique key
Foreign key
Primary key
Index
Answers
A binary one-to-many (1:N) relationship in an E-R diagram is represented by adding the primary key attribute (or attributes) of the entity on the one side of the relationship as a foreign key in the relation that is on the many side of the relationship. Option B is asnwer.
In an E-R (Entity-Relationship) diagram, a binary one-to-many relationship occurs when one entity is associated with multiple instances of another entity. To represent this relationship, the primary key attribute(s) of the entity on the one side are added as a foreign key in the relation on the many side.
This foreign key establishes a connection between the two entities, ensuring that each instance on the many side is linked to the corresponding instance on the one side. The foreign key acts as a reference to the primary key of the related entity, allowing for data consistency and integrity.
Option B is asnwer.
You can learn more about foreign key at
https://brainly.com/question/13437799
#SPJ11
Related Questions
What may be done to speed the recovery process and ensure that all cfc, hcfc, or hfc refrigerant has been removed from a frost-free refrigerator?
Answers
The thing that may be done to speed the recovery process and ensure that all cfc, hcfc, or hfc refrigerant has been removed from a frost-free refrigerator is that the person need to Turn on the defrost heater to bring up the refrigerant's temperature and then it can be able to vaporize any liquid.
How do you define the term temperature?Temperature is known to be a form of measure that is often used to know the hotness or coldness of a thing or person and it is said to be usually in terms of any of a lot of scales, such as Fahrenheit and Celsius.
Note that Temperature tells the direction of heat energy that will spontaneously flow and as such, The thing that may be done to speed the recovery process and ensure that all cfc, hcfc, or hfc refrigerant has been removed from a frost-free refrigerator is that the person need to Turn on the defrost heater to bring up the refrigerant's temperature and then it can be able to vaporize any liquid.
Learn more about Refrigerant's temperature from
https://brainly.com/question/26395073
#SPJ1
When code is compiled it
A) is read directly from the program.
B)is made into a smaller version.
C) runs slower.
D) is converted into binary code.
Answers
Answer:
A compiler takes the program code (source code) and converts the source code to a machine language module (called an object file). Another specialized program, called a linker, combines this object file with other previously compiled object files (in particular run-time modules) to create an executable file. In short, it's A or D.
Answer:
D - is coverted to binary code
Explanation:
A compiler takes the program code (source code) and converts the source code to a machine language module (called an object file). Another specialized program, called a linker, combines this object file with other previously compiled object files (in particular run-time modules) to create an executable file.
Which of the following might an audio technician do to music in a recording studio? (select all that apply)
a) write it
b) mix it
c) perform it
d) master it
Answers
Answer
perform it
master it
mix it
Explanation:
That's the Answer
which of the following should go in the place of /* missing line */ to get this input from the user and store it in the variable favoritemeal?
Answers
favoriteMeal = scan.nextLine(); should be used to get an input from the user and store it in the variable favoriteMeal.
What is a variable?A variable can be defined as a specific name which refers to a location in computer memory and it is typically used for storing a value such as an integer.
This ultimately implies that, a variable refers to a named location that is used to store data in the memory of a computer. Also, it is helpful to think of variables as a container which holds data that can be changed in the future.
In Computer technology, there are two main methods for passing variables to functions and these include the following:
Pass-by-value.Pass-by-reference.Based on the given lines of code, favoriteMeal = scan.nextLine(); should be used to get an input from the user and store it in the variable favoriteMeal.
Read more on variable here: brainly.com/question/12978415
#SPJ1
Complete Question:
The following code is to be used to get the favorite meal from the user.
Scanner scan = new Scanner(System.in);
String favoriteMeal;
System.out.println("Enter favorite meal");
/ missing line /
Which of the following should go in the place of /* missing line */ to get this input from the user and store it in the variable favoriteMeal?
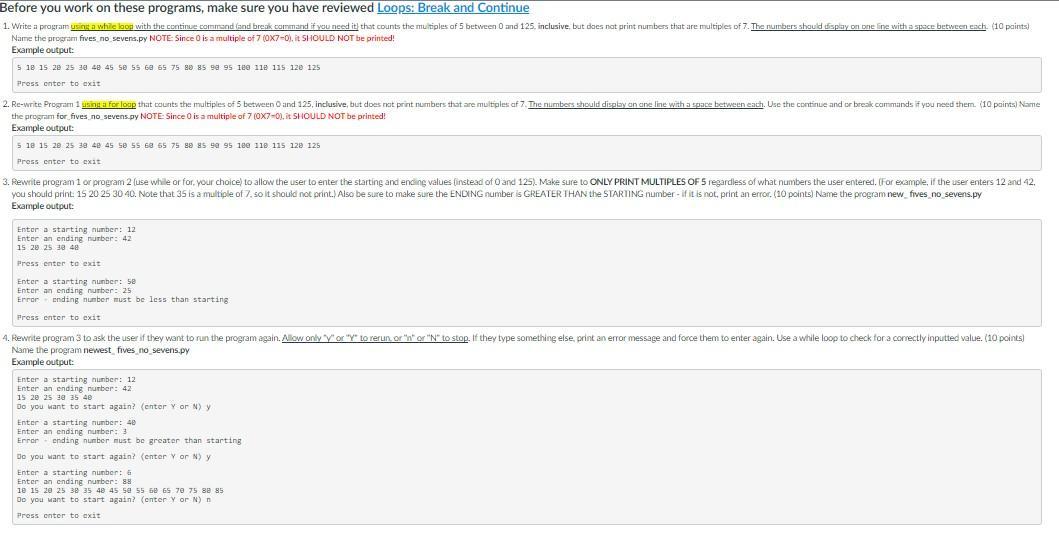
Write a program using a while loop with the continue command (and break command if you need it) that counts the multiples of 5 between 0 and 125, inclusive, but does not print numbers that are multiples of 7. The numbers should display on one line with a space between each. (10 points) Name the program fives_no_sevens.py NOTE: Since 0 is a multiple of 7 (0X7=0), it SHOULD NOT be printed!
Example output:
5 10 15 20 25 30 40 45 50 55 60 65 75 80 85 90 95 100 110 115 120 125
Press enter to exit
Re-write Program 1 using a for loop that counts the multiples of 5 between 0 and 125, inclusive, but does not print numbers that are multiples of 7. The numbers should display on one line with a space between each. Use the continue and or break commands if you need them. (10 points) Name the program for_fives_no_sevens.py NOTE: Since 0 is a multiple of 7 (0X7=0), it SHOULD NOT be printed!
Example output:
5 10 15 20 25 30 40 45 50 55 60 65 75 80 85 90 95 100 110 115 120 125
Press enter to exit
Rewrite program 1 or program 2 (use while or for, your choice) to allow the user to enter the starting and ending values (instead of 0 and 125). Make sure to ONLY PRINT MULTIPLES OF 5 regardless of what numbers the user entered. (For example, if the user enters 12 and 42, you should print: 15 20 25 30 40. Note that 35 is a multiple of 7, so it should not print.) Also be sure to make sure the ENDING number is GREATER THAN the STARTING number - if it is not, print an error. (10 points) Name the program new_ fives_no_sevens.py
Example output:
Enter a starting number: 12
Enter an ending number: 42
15 20 25 30 40
Press enter to exit
Enter a starting number: 50
Enter an ending number: 25
Error - ending number must be less than starting
Press enter to exit
Rewrite program 3 to ask the user if they want to run the program again. Allow only "y" or "Y" to rerun, or "n" or "N" to stop. If they type something else, print an error message and force them to enter again. Use a while loop to check for a correctly inputted value. (10 points) Name the program newest_ fives_no_sevens.py
Example output:
Enter a starting number: 12
Enter an ending number: 42
15 20 25 30 35 40
Do you want to start again? (enter Y or N) y
Enter a starting number: 40
Enter an ending number: 3
Error - ending number must be greater than starting
Do you want to start again? (enter Y or N) y
Enter a starting number: 6
Enter an ending number: 88
10 15 20 25 30 35 40 45 50 55 60 65 70 75 80 85
Do you want to start again? (enter Y or N) n
Press enter to exit
Answers
Each solution is a bit lengthy. In order to conserve space, they have been added to the answer as screenshot images as follows;
solution1 (list all multiples of fives that are not multiples of seven from 0 to 125 using a while loop)solution2 (list all multiples of fives that are not multiples of seven from 0 to 125 using a for loop)solution3 (allow the user to enter starting and ending values, then list all multiples of fives that are not multiples of seven in that range using a for loop)solution4 (give the user the choice to rerun the program)Each program uses a loop to generate multiples of five. However, in order to avoid printing numbers that are multiples of both five and seven, an if statement is used to check if the current multiple of five is also a multiple of seven. If so, the loop continues with the next iteration without trying to print anything.
Each successful multiple of five is added to a list called output multiples. Then to print out the list using space as the delimiter, and without the square brackets, add an asterisk to the list as shown in the code.
See another python program on loops in the link: https://brainly.com/question/12736327




Within the creditcard selection list add the following options and values: Credit Card Type (leave the value as an empty text string), American Express (value="amex"), Discover (value="disc"), MasterCard (value="master"), and Visa (value="visa").
Make the selection list and cardname field required.
Make the cardnumber field required and add the regular expression pattern indicated in the comment section of the HTML file to help ensure that a valid card number is used.
Within the cardmonth selection list add options for each month starting with the text Month and a value of a blank text string followed by the option text January (01) through December (12) with the corresponding values 01 through 12. Make the selection list required.
Within the cardyear selection list add options for each year starting with the text Year and a value of a blank text string followed by the option text 2020 through 2024 with the corresponding values 2020 through 2024.
Make the cardcsc field required with a maximum character length of 3 characters following the regular expression pattern: ^\d{3}$ .
Open the code7-3_valid.css file and add the following style rules to the file:
Display any input or select element that has the focus with a yellow background color.
Display any input element with invalid data in a red font, surrounded by a red border, and red box shadows that are offset 0 pixels horizontally and vertically with a shadow blur of 5 pixels.
Answers
Answer:
input:focus {
background-color: yellow;
}
input:invalid {
color: red;
border: 1px solid red;
box-shadow: 0 0 5px red;
}
The Link Layer in the TCP/IP Model corresponds to the and Layers of the OSI Reference Model. A) Transport; Physical. B) Physical; Data Link.
Answers
The link layer in the TCP/IP Model corresponds to the Transport and Physical layer of the OSI Model.
What is link layer?The Internet protocol suite, or IOS, is the networking architecture of the Internet, and the link layer is the lowest layer in computer networking. The set of procedures and communication standards specific to the link to which a host is actually connected is known as the link layer.
The link is the logical and physical network component that connects hosts or nodes in the network, and a link protocol is a set of guidelines and rules that only apply to the next-to-next network nodes in a network segment.
The link layer is sometimes described as a combination of the OSI's data link layer (layer 2) and physical layer, despite the fact that the Internet protocol suite and OSI model have different definitions of layering (layer 1).
Learn more about link layer
https://brainly.com/question/29486384
#SPJ4
To generate integers between and including -10 to 10 you would use:
random.randint(-10, 10)
random.random()*20 + -10
random.random(-10, 10)
randint(-10, 10)
I will give Brainliest
Answers
Answer:
random.randint(-10,10)
Explanation:
A speed limit sign that says "NIGHT" indicates the _____ legal speed between sunset and sunrise.
Answers
Answer:
Maximum
Explanation:
Speed limits indicate the maximum speed you are legally allowed to drive.
Please provide an idea for both a personal project and a group
project. The scope needs to be reasonable in size, as the time to
complete the project and the resources will be limited. (you can
provid
Answers
A personal project idea is to create a personal finance tracker to track income and expenses. A group project idea is to create a community garden in a public space, requiring planning, planting schedules, and recruiting volunteers to provide fresh produce for the community.
Personal Project Idea:
Create a personal finance tracker: This project involves creating a spreadsheet or using a personal finance app to track income and expenses. The tracker should include categories for expenses such as rent, food, utilities, entertainment, and savings, as well as a budget for each category. The tracker can be customized to meet individual needs and can be used to identify areas where spending can be reduced and savings can be increased.
Group Project Idea:
Community garden project: This project involves creating a community garden in a public space such as a park or schoolyard. The project would require planning and organizing planting schedules, obtaining necessary supplies such as soil, seeds, and gardening tools, and recruiting volunteers to help with planting, maintenance, and harvesting. The garden can be used to provide fresh produce for the community and can also serve as an educational resource for local schools.
To know more about personal projects, visit:
brainly.com/question/32301757
#SPJ11
in a basic program with 3 IF statements, there will always be _________ END IIF's.
a)2
b)3
c)4
Answers
Answer:
c)4
Explanation:
Hope it could helps you
Calvin needs to design a simple yet professional interface for his users. Which option should he implement?
Answers
Answer:
switchboard
Explanation:
The option that he should implement would be a switchboard interface design. These design structures for graphic user interfaces use a single main page, large icons/buttons, a fixed navigation menu, and all the necessary functionality right in front of the user. This design is made with simplicity in mind in order to make it as easy as possible for a new user to pick up and efficiently and intuitively navigate the user interface. Therefore, since Calvin needs a simple yet professional design, this would be the best implementation.
Answer:
switchboards is the correct answer
Explanation:
just did the test
Describe how to use the most current procedural coding system.
Answers
The most current procedural coding system is the Current Procedural Terminology (CPT) system that is used to report medical procedures and services.
The following steps can be taken to use this coding system:
1. Familiarize yourself with the CPT codebook: Get the latest CPT codebook and familiarize yourself with the layout and organization of the codes.
2. Select the appropriate code: Identify the procedure or service that was performed and select the appropriate code from the codebook. This code should accurately describe the procedure or service that was provided.
3. Determine the level of service: CPT codes are divided into five levels of service, ranging from basic to complex.
4. Follow coding guidelines: Follow the coding guidelines provided in the codebook to ensure accurate and consistent coding which includes following specific rules for each section of the codebook, such as using modifiers to provide additional information about a procedure or service.
Overall, using the most current procedural coding system involves familiarizing yourself with the CPT codebook, selecting the appropriate code, determining the level of service, following coding guidelines, and checking for updates.
Learn more about Current Procedural Terminology (CPT) here;
https://brainly.com/question/28296339
#SPJ2
Suppose we are using a three-message mutual authentication protocol, andAlice initiates contact with Bob. Suppose we wish Bob to be a stateless server, and thereforeit is inconvenient to require him to remember the challenge he sent to Alice. Lets modify theexchange so that Alice sends the challenge back to Bob, along with the encrypted challenge. So the protocol is:Step 1: Alice send a message [I’m Alice] to Bob. Step 2: Bob sends a random number, R. Step 3: Alice sends a message [R,KAlice−Bob{R}]. Is this protocol secure?
Answers
No, this protocol is not secure. A secure mutual authentication protocol must, among other things, support mutual authentication, which allows both parties to confirm the identities of one another.
Due to the fact that Bob cannot recall the challenge he gave to Alice, he is unable to confirm Alice's identity using this protocol. As a result, an attacker can read Alice and Bob's messages and then pretend to be Alice to Bob by simply playing back the message that Alice originally sent.
This problem can be resolved by changing the protocol so that Bob sends a challenge along with the random number R, and Alice must respond with the challenge as well. This way, Bob can verify Alice's identity by checking if the challenge in Alice's response matches the one he sent earlier.
For such more question on protocol:
https://brainly.com/question/8156649
#SPJ11
How can I search all columns of a table in SQL Server?
Answers
To search all columns of a table in SQL Server, you can use the LIKE keyword along with the wildcard character %. Here's the syntax:
sql
Copy code
SELECT *
FROM your_table
WHERE column1 LIKE '%search_value%'
OR column2 LIKE '%search_value%'
OR column3 LIKE '%search_value%'
-- add more columns as needed
Replace your_table with the actual name of your table.
Replace column1, column2, column3, etc., with the names of the columns you want to search in.
Replace search_value with the value you want to search for.
The % wildcard character is used to represent any sequence of characters. Placing % before and after the search value ensures that it can match any part of the column value.
The LIKE keyword is used for pattern matching, allowing you to search for values that partially match the specified pattern.
By using the LIKE keyword with wildcard characters %, you can search all columns of a table in SQL Server for a specific value or pattern. This method allows you to perform a broad search across multiple columns, looking for matches in any part of the column values.
To know more about SQL visit
https://brainly.com/question/23475248
#SPJ11
hris has received an email that was entirely written using capitalization. He needs to paste this text into another document but also ensure that the capitalization is removed.
What should Chris do?
Answers
_______ are malicious programs that come into a computer system disguised as something else such as a free computer game or screen saver.
Answers
Answer:
Trojan horses
Explanation:
palermo theater group is headquartered inphoenix, arizona. founded in 2005, they had a mission to open 12 cinema locations in 15 have achieved their goal, but it has become necessary for palermo to update how they handle their business process and track their data.palermo does not just offer movies. each location has a full bar and kitchen. guests can eat and drink either at the bar or in a theater while watching a film.palermo uses the aloha system to run most of the scheduling and accounting as those are location specific, but they need a separate database to track customer checks and information for their loyalty program so they can centralize the process of all the locations. guests at the palermo theaters purchase tickets for their movies before they arrive, and seats in the theater are assigned. each theater location has at least eight screens. bar guests do not need tickets or of palermo's locations has a theme based on a movie, and the decor of each location follows a different number one movie theme. the themes vary as follows:
Answers
Palermo Theater Group is a cinema chain headquartered in Phoenix, Arizona, founded in 2005, which aimed to open 12 movie locations in 15 years. Palermo provides not only movies, but also a full bar and kitchen at each site.
The guests can eat and drink in the bar or in a theater while enjoying a movie.Palermo relies on the Aloha system to handle most of the scheduling and accounting, which is location-specific. However, they need a separate database to manage client checks and information for their loyalty program to centralize the operation of all locations. The guests purchase tickets for their films ahead of time, and the seats in the cinema are designated. Each theater location has at least eight screens. Bar guests do not need tickets or reservations.The decor of each Palermo location follows a theme based on a popular movie. Each site has a different number one movie theme, and the themes differ from one another. Palermo needs to upgrade how they handle their business processes and track their data to suit their growing operations. The company has already achieved its initial aim of opening 12 movie locations in 15 years. The organization may streamline its operations and centralize customer check and loyalty program details by implementing a centralized database system. The centralization process will benefit all of the locations and make the data more accessible to everyone.
To know more about Palermo Theater Group visit:
https://brainly.com/question/14452807
#SPJ11
who are your favorite You tubers mine are the Dobre Brothers
Answers
Answer:
mine are H2O delerious and Lazar beam
Explanation:
I enjoy watching watching whatever comes up on my recommended page :)
You have two Windows Server 2016 computers with the Hyper-V role installed. Both computers have two hard drives, one for the system volume and the other for data. One server, HyperVTest, is going to be used mainly for testing and what-if scenarios, and its data drive is 250 GB. You estimate that you might have 8 or 10 VMs configured on HyperVTest with two or three running at the same time. Each test VM has disk requirements ranging from about 30 GB to 50 GB. The other server, HyperVApp, runs in the data center with production VMs installed. Its data drive is 500 GB. You expect two VMs to run on HyperVApp, each needing about 150 GB to 200 GB of disk space. Both are expected to run fairly disk-intensive applications. Given this environment, describe how you would configure the virtual disks for the VMs on both servers.
Answers
The virtual disk configuration for the VMs on both servers in this environment is shown below.
In the Hyper V Test,
Since there will be two or three virtual machines running at once, each of which needs between 30 and 50 GB of the total 250 GB of disk space available,
What is virtual disks?Setting up 5 virtual disks, each 50 GB in size.
2 VMs each have a 50 GB virtual drive assigned to them.
The above setup was chosen because running three VMs with various virtual disks assigned to them will not pose an issue when two or three VMs are running concurrently and sharing the same virtual disk. This is because the applications are disk-intensive.
To learn more about virtual disks refer to:
https://brainly.com/question/28851994
#SPJ1
Given this environment, the virtual disk configuration for the VMs on both servers is shown below. Because two or three VMs will be running at the same time, and each VM has disk requirements ranging from 30 to 50 GB of total disk space of 250 GB.
What is Hyper V Test?While there are several methods for testing new virtual machine updates, Hyper-V allows desktop administrators to add multiple virtual machines to a single desktop and run tests. The Hyper-V virtualization technology is included in many versions of Windows 10. Hyper-V allows virtualized computer systems to run on top of a physical host. These virtualized systems can be used and managed in the same way that physical computer systems can, despite the fact that they exist in a virtualized and isolated environment. To monitor the utilization of a processor, memory, interface, physical disk, and other hardware, use Performance Monitor (perfmon) on a Hyper-V host and the appropriate counters. On Windows systems, the perfmon utility is widely used for performance troubleshooting.Therefore,
Configuration:
Creating 5 Virtual disks of 50 GB each.
1 virtual disk of 50 GB is assigned to 2 VM.
The above configuration is because since two or three VM will be running at the same time and using the same virtual disk will cause a problem since the applications are disk intensive, running three VMs with different virtual disks assigned to them, will not cause a problem.
For Hyper V App,
Two VM will run at the same time, and the disk requirement is 150 - 200 GB of 500 GB total disk space.
Configuration:
Creating 2 virtual disks of 200 GB each with dynamic Extension and assigning each one to a single VM will do the trick.
Since only two VMs are run here, the disk space can be separated.
To learn more about Hyper V Test, refer to:
https://brainly.com/question/14005847
#SPJ1
Which API is used to create and deploy templates or migrate workbooks from test to production data sources?
Answers
The API used to create and deploy templates or migrate workbooks from test to production data sources is the Tableau REST API.
The Tableau REST API is a powerful tool that allows developers to programmatically interact with Tableau Server or Tableau Online. One of its key functionalities is the ability to create and deploy templates, which are pre-configured workbooks or dashboards that can be used as starting points for new projects.
With the Tableau REST API, developers can automate the process of creating templates and migrating workbooks from test to production data sources. This API provides methods and endpoints to manage and manipulate Tableau resources, such as workbooks, data sources, projects, and users, enabling seamless integration and automation of deployment processes.
You can learn more about Tableau at
https://brainly.com/question/31359330
#SPJ11
Different Betweens in SRAM and DRAM !
Thank!
\( \: \: \: \)
Answers
Answer:
Explanation:
Application Differences:
SRAM
SRAM stands for Static Random Access Memory DRAM stands for Dynamic Random Access Memory
Faster access is due to the usage of transistors to store single bit of data
SRAMs are used for cache memories due to faster access time
DRAM
DRAM stands for Dynamic Random Access Memory
DRAMs are used for main memories due to comparatively slower access time.
DRAMs use capacitor to store bits where each capacitor holds a single bit
Parameter differences
Speed: SRAMs are faster due to presence of transistors. DRAMs are slower due to presence of capacitors
Size: Due to complexity involved in the internal circuits, SRAMs are smaller in capacity for same size of the chip. DRAMs are larger as compared to SRAMs since their capacity for a given physical size is more.
Cost: SRAMs are costlier and the per bit storage cost is more than that of the DRAMs. DRAMs are cheaper and the per bit storage cost is less than that of the SRAMs
how can we use fork() to specify different behavior for the child process, even if its code is a duplicate of the parent's?
Answers
Process creation is done using the system function fork(). It gives back a process ID and requires no arguments. Forking is a method used to start a new process.
In CodePen, how do you copy pens?Fork. On CodePen, you may copy any prototype. Both your own pens or other people's prototypes fall under this category. Click on Fork button at the top right to make a copy of a pen.
What does CodePen's debug mode do?The only mode on CodePen in which you can see a sample of the code with only an editor is Debug View.
To know more about Codepen fork visit:
https://brainly.com/question/1365308
#SPJ4
800,000= 180,000(P/AD, i,5) + 75,000(P/F,i,5) I want to find interest rate (i)
Would you let me know how to calculate this using Excel?
Answers
here is how to compute the above using Excel.
How to calculate the aboveOpen a new Excel spreadsheet and enter the following values in the cells:
Cell A1: 800,000 (Total amount)
Cell A2: 180,000 (Payment at the end of each period)
Cell A3: 75,000 (Payment at the beginning of each period)
Cell A4: 5 (Number of periods)
In cell A5, enter an initial guess for the interest rate (i). For example, you can start with 0.1 (10%).
In cell B1, enter the formula =A2*PMT(A5,A4,0) to calculate the present value of the periodic payments at the end of each period.
In cell B2, enter the formula =A3*PMT(A5,A4-1,0) to calculate the present value of the periodic payments at the beginning of each period.
In cell B3, enter the formula =A1 - B1 - B2 to calculate the remaining balance.
In cell B4, enter the formula =RATE(A4, B2, B1) to calculate the interest rate.
Learn more about Excel Formula at:
https://brainly.com/question/29280920
#SPJ1
what is an overview of your opinion of Digital Etiquette? Do not look it up bc I will know!
Answers
Answer:
I think digital etiquette is good and it should be know all around the world.
Explanation:
In the context of networks, the term "topology" refers to the order and arrangement of the elements of a communications network.
a. True
b. False
Answers
The statement is true. Network topology describes the physical and logical relationships between nodes in a network, as well as the schematic arrangement of links and nodes, or some hybrid of the two.
Network topology is used to define the layout, structure, and shape of a network, both physically and logically. A network can have a single physical topology and multiple logical topologies at the same time. The physical connections of devices such as wires, cables, and others are referred to as network layout. The geometric arrangement of links and nodes in a computing network is referred to as network topology. Network topology, on the other hand, may describe how data is transferred between these nodes. Network topologies are classified into two types: physical and logical.
Learn more about topology here-
https://brainly.com/question/13186238
#SPJ4
Write a program code in the python programming language to find simple interest given the
formula SI = (P*R*T)/100.
Read P(Principal), R (Rate), T (Time) from the keyboard and Calculate Simple Interest (SI).
Answers
Answer:
p = float(input('Principal: '))
r = float(input('Rate: '))
t = float(input('Time: '))
si = (p * r * t) / 100
print(si)
The "float" before the input in the first 3 lines is so you're able to input decimals. If you're not using decimals, you can switch the "float" to "int". However, if you input a decimal number after you switched to int, you will receive an error
Suppose we compute a depth-first search tree rooted at u and obtain a tree t that includes all nodes of g.
Answers
G is a tree, per node has a special path from the root. So, both BFS and DFS have the exact tree, and the tree is the exact as G.
What are DFS and BFS?An algorithm for navigating or examining tree or graph data structures is called depth-first search. The algorithm moves as far as it can along each branch before turning around, starting at the root node.
The breadth-first search strategy can be used to look for a node in a tree data structure that has a specific property. Before moving on to the nodes at the next depth level, it begins at the root of the tree and investigates every node there.
First, we reveal that G exists a tree when both BFS-tree and DFS-tree are exact.
If G and T are not exact, then there should exist a border e(u, v) in G, that does not belong to T.
In such a case:
- in the DFS tree, one of u or v, should be a prototype of the other.
- in the BFS tree, u and v can differ by only one level.
Since, both DFS-tree and BFS-tree are the very tree T,
it follows that one of u and v should be a prototype of the other and they can discuss by only one party.
This means that the border joining them must be in T.
So, there can not be any limits in G which are not in T.
In the two-part of evidence:
Since G is a tree, per node has a special path from the root. So, both BFS and DFS have the exact tree, and the tree is the exact as G.
The complete question is:
We have a connected graph G = (V, E), and a specific vertex u ∈ V.
Suppose we compute a depth-first search tree rooted at u, and obtain a tree T that includes all nodes of G.
Suppose we then compute a breadth-first search tree rooted at u, and obtain the same tree T.
Prove that G = T. (In other words, if T is both a depth-first search tree and a breadth-first search tree rooted at u, then G cannot contain any edges that do not belong to T.)
To learn more about DFS and BFS, refer to:
https://brainly.com/question/13014003
#SPJ4
To create documents that consist primarily of text, you need a word processor software. A. Trueb. False
Answers
The given statement "To create documents that consist primarily of text, you need a word processor software" is true. Here's why:Documents, in general, are data created to support, establish or verify facts, opinions, or findings of an individual or an organization.
In the business and academic environment, document creation and management is an essential task that demands an efficient, accurate, and user-friendly tool to create a document in an organized way.A word processor is an application software that allows users to create, modify, and format a text document.
It offers a range of tools that includes formatting options such as margins, fonts, layout, styles, spacing, headings, numbering, and many others, which helps users to create, edit and format a document to look professional, readable, and attractive.Therefore, to create documents that primarily consist of text, a word processor software is required. It's a must-have tool for anyone who wants to create professional and organized documents with ease.
TO know more about software visit:
https://brainly.com/question/26649673
#SPJ11
Which of the following activities Best describes the use of marketing as a form of digital communication
OA An online discount clothing company sends an email about its upcoming sale,
OB. A teacher posts a list of assignments online for students to access
OG A doctor's office emails a patient to remind them about an upcoming appointment
OD. A friend downloads a new song by her favorite artist to her phone.
Reset
Next
Answers
the answer for this question is:
OA. An online discount clothing company sends an email about its upcoming sale.
hope this helps you!