7. What does overflow mean in the context of unsigned numbers?
Answers
Overflow in the context of unsigned numbers refers to the situation where the result of an arithmetic operation exceeds the maximum value that can be represented with the given number of bits. For example, if we add 255 to 1 using an 8-bit unsigned number system, the result would be 256, which is greater than the maximum value of 255.
This results in an overflow condition where the result is truncated to fit within the available bits, causing an incorrect result. Addition (+): The operation of finding the total of two or more numbers.
Subtraction (-): The operation of finding the difference between two numbers.
Multiplication (*): The operation of finding the product of two or more numbers.
Division (/): The operation of finding the quotient of two numbers, where the numerator is divided by the denominator.
Exponentiation (^ or **): The operation of finding the result of raising a number to a power.
These basic arithmetic operations form the foundation of many mathematical and scientific concepts, and are used in a wide variety of applications. In addition, they are the building blocks for more advanced
mathematical operations, such as logarithms, derivatives, and integrals.
Learn more about arithmetic operation here
https://brainly.com/question/30553381
#SPJ11
Related Questions
Usually, a problem is reduced by making the value of one or more parameters ________ with each recursive call.A) largerB) negativeC) smallerD) equal
Answers
Usually, a problem is reduced by making the value of one or more parameters smaller with each recursive call.
Recursive functions continuously call themselves until they reach a base case where the issue can be resolved without further intervention.
Recursive functions frequently accept one or more parameters as input, which are then used to select the subproblems that need to be solved.
Making the value of one or more parameters smaller with each recursive call is a typical strategy for reducing problems. This is frequently known as the "recursive leap of faith."
The issue is divided into more manageable subissues that can be resolved independently by reducing the parameters.
Eventually, the subproblems shrink to the point where they can be resolved instantly without further recursion.
The original problem is then resolved as a result of this procedure being repeated until all subproblems have been resolved.
Learn more about the recursive call :
https://brainly.com/question/29910412
#SPJ11
What is the output?
class car:
model = "
age = 0
myCar = car()
myCar.age= myCar.age + 10
print(myCar.age)
Output: ___
Answers
Answer:
10
Explanation:
# A class named car is created
# There are two variables in the class, model and age.
# model is a string holding value for the model of the car.
# age is an integer holding value for the age of the car.
class car:
model = '' # model is initialized as empty string
age = 0 # age is initialized as 0
myCar = car() # creating a car object named myCar
myCar.age= myCar.age + 10 # the value of the age is updated by adding 10. (Note that myCar was our object. If we want to access any properties of the object, we type the object name, . , and the property name. Initially, age was 0, we added 10 to it and it becomes 10)
print(myCar.age) #prints the age of the myCar object, 10
Which sentence uses a pair of synonyms? Because there was so much shouting, many of the protestors began screaming in order to be heard. Although we were tired after the long hike into the woods, we were still energetic enough to make camp. Despite all the exercise and the healthy eating habits, she still felt sick when she woke up in the morning. The children were too excited about the next day to settle down in their peaceful surroundings.
Answers
Answer:
Synonyms:Synonyms are words that are similar, or have a related meaning, to another word.
Antonyms:Antonyms are words that have an opposite meaning to an another word.
The sentence which uses a pair of synonyms are:Because there was so much shouting, many of the protestors began screaming in order to be heard.
Shouting and Screaming are synonyms.
In the other sentences, pairs of antonyms were used.
Second sentence: Tired × Energetic
Third sentence: Healthy × Sick
Fourth: Excited × Peaceful
Hope this helps you...
Hope you have a nice day ahead...
Answer:
The Answer Is A
Explanation:
if the windows server 2016 gui is installed, you can install the windows server backup feature using which dialog?
Answers
The Windows Server Backup feature can be installed using the Add Roles and Features dialog. To open this dialog, go to Server Manager and select the Manage menu.
From the Manage menu, select Add Roles and Features. On the Before you Begin page, click Next. On the Installation Type page, select Role-based or feature-based installation and click Next. On the Server Selection page, select the server to install the feature on and click Next. On the Features page, select the Windows Server Backup feature and click Next. On the Confirm Installation Selections page, review the selections and click Install.
Learn more about software: https://brainly.com/question/28266453
#SPJ4
Directions: Fill in the blanks with the appropriate word in each statement below.
Choose your answers from the given pool of words inside the box.
Place your answer in your SMAW activity notebook.
Toss
Calipers
Blades
Clean
Lubricant
Sharpened
Maintenance
Cleaning
Covered box
Flat Scraper
1.
are sharpened with a file or on an oilstone, forming a bevel on one
side only.
2. Store tools in a
dry storage area.
3.
is a substance introduce to lessen friction between moving
surfaces.
4.Never
scrapers into boxes or onto other tools when not in use.
Their edges will be dulled.
5. Sharpen
of cutting tools.
6.
are precision instruments and must be used and handled with
care at all times.
7.
Simple process applied to hand tools.
8. Some tools need to be
such as blades of knife, cold chisel,
punches, and many others.
9. Keep micrometers in a
on the job and wipe an anvil and spindle
with soft, slightly oiled rag each time after using
of hand tools and machines are both primordial concerns of a
10.
repair technician in the welding shops or in the welding product
Answers
Answer:
sbysgscd CD CD vdhdudiididjehgegeueuheve gf hdgowincobwbciehidgwdgiwigwdigxifqugwljvwvwxi2dvwvwxixwvwxvqvwivqi
xwv2digwxivwiw
wxvixbowowxowcohwco2ch2od
odhowhowcowcohwxohwdowdjeciwr
hiwdodwobwdvqoo230ie
9qhowwdhwdigwdoieexohxiefbeoc
hwdhefgdegedogex
Explanation:
9hwx9hex9hexobeb8xgx9jcr
jd2oh2ih2xi2dd2oxivqsg8xwohjgwxohdeohwxihwdoeciwxgiweiguofyoe5u5ew46w57lrroyvyreiyfe1ei2ei2idxwdooydyofpiwigpwxwduo1zuo1dif3o4y
2hupv2rxou2xu2du2d
ou1svxiexuowvouqdip2dpwcuowd2u
qxigqedouovqudipgqipwgipcwpi2di2ipegpi2efpi2dipe2ip1dgxip2ce1piecg1peix1ou2co2dpu1ecgip1eip1deg1euouoeupdeuofour68ditsoysrs27ro457uoeigpexupgeip3dpiwdguofoyiyyidiyufuouodyidyouoouupwd9dediwgip2sou2sg923ugo13uefcidyid57gdqigeobxri1eiyf2ipechkcyidouxtuxuocziycyiyyiyiy2idyigxyiyiyiydiyyiiyciyc2ouvyidyiyidydyidiyf7uo2vu1e
6. Describe an algorithm that takes as input a list of n in- tegers and finds the number of negative integers in the list.
Answers
This algorithm has a time complexity of O(n) since it iterates through each element in the list once. The space complexity is O(1) as it only uses a single variable to store the count.
Here is a simple algorithm that takes a list of n integers as input and finds the number of negative integers in the list:
Initialize a variable, let's call it count, to 0. This variable will keep track of the number of negative integers.
Iterate through each element in the list:
a. Check if the current element is less than 0.
b. If it is, increment the count variable by 1.
After iterating through all the elements in the list, the count variable will contain the number of negative integers.
Output the value of the count variable as the result.
Know more about space complexity here:
https://brainly.com/question/814829
#SPJ11
what does a technician need in order to make changes to software installed on the computer of a customer?
Answers
A technician needs the customer's permission before making any changes to a computer.
What kind of work does a level one technician at a call center typically do?A level one technician's main duty is to obtain information from the customer. All of the data must be accurately entered into the work order by the level one technician.
Which of the following software launches first when you turn on your laptop?computing device. When a computer is turned on, an operating system, a specific program, must be started. By handling the intricate logistics of hardware management, the operating system's job is to make other computer applications more functional.
To know more about technician visit:-
https://brainly.com/question/14290207
#SPJ1
address on the internet
Answers
A device on the internet or a local network can be identified by its IP address, which is a special address.The rules defining the format of data delivered over the internet or a local network are known as "Internet Protocol," or IP.
Which two kinds of Internet addresses are there?
picture of an address found online Internet Protocol (IP) addresses are used to connect your network with the Internet.IP addresses come in two varieties: static and dynamic.In order to help you choose between static and dynamic IP addresses, this article compares their main characteristics. Using one of the several IP lookup programs that are readily available online is the quickest approach to start learning someone's IP address.There are tools available to enter an IP address and search for its free public registry results on websites A network address and a host (or local) address are the components of an internet address.With this two-part address, a sender can identify both the network and a particular host on the network.Each network that connects to another Internet network receives a distinct, official network address. While IP addresses do identify your whereabouts, they do not provide as much detail as a home address.Additionally, IP addresses will never disclose your name, phone number, or any other specific personal details. "Internet protocol" is referred to as IP.For any device connected to your network, your router IP serves as an identification number.For the router to recognize it and send data packets to it, a device (such as a computer or smartphone) needs to have an IP address.Your internet is what it is because of the data packets.To learn more about IP address refer
https://brainly.com/question/21864346
#SPJ1
users complain that they receive an untrusted website warning in their web browsers when connecting to a https-enabled intranet web server, but not when they connect over http. what is the most likely reason this is happening?
Answers
HTTP does not require a PKI certificate to be installed on the server, but HTTPS does.
What is HTTP?The HTTP protocol, which is based on IP, is used to transfer data from server to client or vice versa. Client makes a request, which the server responds to. The server and client only interact during the current request and response cycle.HTTP offers a standard for communication between a web browser and a web server. It is a collection of guidelines for exchanging data between computers. On the World Wide Web, information like text, photos, and other multimedia files are shared. HTTP is indirectly used every time a web user launches their browser. For distributed, collaborative, hypermedia information systems, it is an application protocol.To learn more about HTTP refer to:
https://brainly.com/question/7462872
#SPJ4
Tools that can be used to do yardwork, mowing, or gardening are NOT a form of technology.
True
False
Answers
False
Explanation:
Answer:
False
Explanation:
Everything which reduces the human efforts and saves time are termed as technology.
Viruses that load from usb drives left connected to computers when computers are turned on are known as.
Answers
Answer:
Viruses that load from USB drives left connected to computers when computers are turned on are known as boot sector viruses
Explanation:
Software designed to close logical ports in your computer is know as firewall Which is NOT a tool hackers use to gain access to and take control of your computer
How can you make sure to save all annotations from a slide show?
When you exit the slide show, select Keep the Annotations.
O Before beginning the slide show, select Save All Annotations.
During the slide show, right-click and select Save Annotations.
O All annotations are automatically saved as a copy of the presentation.
Answers
Answer:
when you exit the slide show, select keep annotations
Explanation:
To save all annotations from a slide show, make sure that When you exit the slide show, select Keep the Annotations.
What is annotation?This is known to be a kind of a note that is said to be added through comment or explanation.
It is often used by writers. Note that the right thing to do is to To save all annotations from a slide show, make sure that When you exit the slide show, select Keep the Annotations.
Learn more about Annotations from
https://brainly.com/question/16177292
Some peer-to-peer networks have a server and some don't.
~True
OR
`False
Answers
Answer:
true
Explanation:
True because on peer-to-peer network the client computer act both as a server and workstation.
Answer:
True
Explanation:
what type of malware prevents you from accessing files
Answers
Write a program that checks matching words - First asks the user to enter 2 String variables word1 and word2 - Save these in two String variables. - Use string methods to answer below questions: o Are these words entered same (ignore case)? o Are these words entered same (case sensitive)? - Test for different inputs - Write a For loop to print each character of word1 on a separate line
Answers
The given program checks for matching words entered by the user and performs various comparisons and character printing. The program follows these steps:
Prompt the user to enter two string variables, word1 and word2, and save them as separate string variables.
Use string methods to answer the following questions:
a. Check if the words entered are the same, ignoring the case sensitivity.
b. Check if the words entered are the same, considering the case sensitivity.
Test the program with different inputs to verify its functionality.
Implement a For loop to iterate through each character of word1 and print each character on a separate line.
The program allows the user to compare two words and determine if they are the same, either ignoring or considering the case sensitivity. Additionally, it provides a visual representation of word1 by printing each character on separate lines using a For loop.
Learn more about variables here : brainly.com/question/31751660
#SPJ11
How many outcomes are possible in this control structure?
forever
A. One
B. Two
C. Four
D. Three
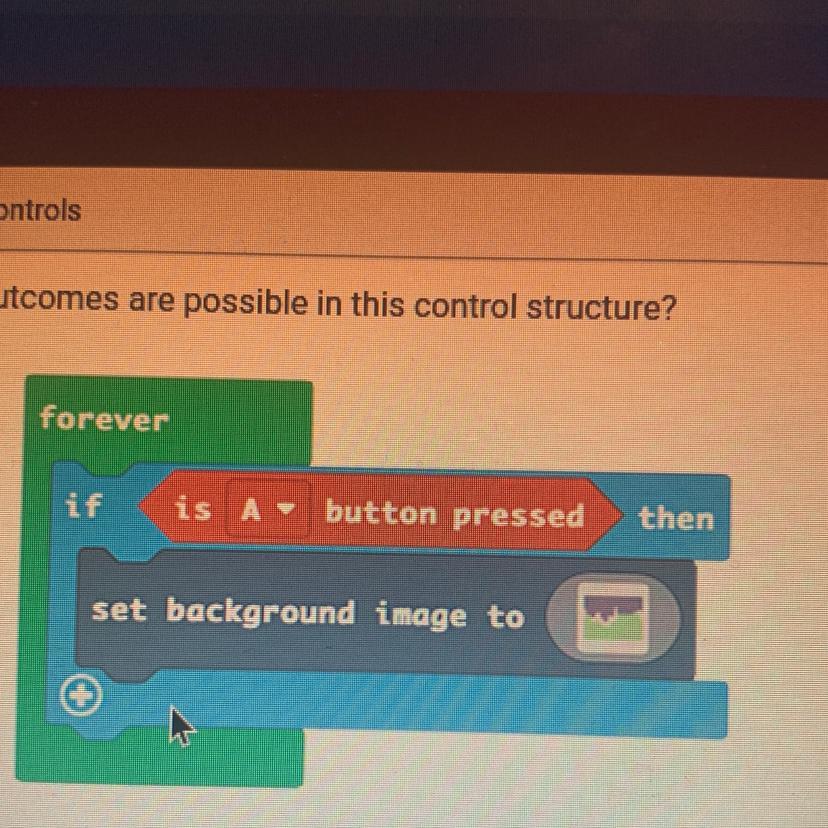
Answers
In this control system, just one conceivable outcome can occur.
What exactly is a control structure?
The sequence in which statements, instructions, or function calls are performed at the conclusion of a programme is known as the control structure. In computer programming, it is a fundamental idea that outlines how a programme will carry out its operations and choose which instructions to carry out. Control structures are used to particular specify the order in which operations in a system should be performed, to reactivities a predetermined number of times or until a predefined condition is satisfied, and to choose what operations to run based on preset criteria.
To know more about control structure
https://brainly.com/question/15008951
#SPJ1
Sami is creating a web page for her dog walking business. Which item will set the theme for her page? Background color Heading color Link color Text color
Answers
Answer:
A Background color
Explanation:
From the prespective of networking infrastrcutre, sound waves, such as the human voice, vary continuously over time and are considered what type of data?
Answers
From the perspective of networking infrastrcutre, sound waves, such as the human voice analog data, as it is a continuous electrical signal.
What is Analog data?Analog data is a type of data that is represented by continuous physical measurements. Analog data is typically represented by a physical quantity such as voltage, current, temperature, pressure, or sound. This type of data is typically converted into a digital form for storage, processing, and analysis. Analog data is often used in industries such as healthcare, manufacturing, and oil and gas. Analog data is used to represent data or information in a physical form, such as a waveform or electrical signal. These signals are created through analog-to-digital converters and are typically used for measurement and control systems. Analog data is typically used for analog-to-digital conversion, audio and video recording, and medical imaging. It is also used to measure temperature, pressure, humidity, and other physical properties.To learn more about analog data refer to:
https://brainly.com/question/28711451
#SPJ4
PLEASE HELP! ITS A COMPUTER MCQ
The character that is displayed at the end of the code for continuation.
a. :
b. ;
c. .
d. ,
Answers
Answer:
b. ;
Explanation:
PLEASE MARK ME AS BRAINLIEST
it important to have media images reflective of diverse communities? Why, or why not?
Answers
Answer:
Yes.
It is important because a POC would want to believe that they can achieve a goal in life because they set it, so by seeing themselves represented gives them confident.
the growing use of cell phones has helped shrink the digital divide more than anything else.
true/false
Answers
The statement is true because cell phones have significantly increased accessibility to digital resources, especially for people in developing countries and those with limited resources.
Mobile phones are more affordable than traditional computers, which has enabled more people to access the internet, communicate, and participate in the digital world. In addition, the proliferation of mobile apps and services has made it easier for users to access information, education, healthcare, and financial services.
By providing these essential services through cell phones, the digital divide has been reduced, allowing more people to benefit from digital advancements and contribute to the global economy.
Learn more about cell phones https://brainly.com/question/28041325
#SPJ11
- Analyzes the network over time to find what nodes are the most frequent transmitters (talkers) or recipients (listeners) of data.- Useful for finding...*Unexpected traffic patters,*Measuring normal traffic*Detecting potential bottlenecks.
Answers
The process of analyzing the network over time to identify the nodes that are the most frequent transmitters or recipients of data is known as network traffic analysis.
This technique can be useful in various ways such as identifying unexpected traffic patterns, measuring normal traffic, and detecting potential bottlenecks. By monitoring the network traffic, administrators can identify the sources of heavy traffic and take necessary actions to optimize network performance. Additionally, this approach can also help to detect any unusual activities or security threats on the network.
Discovering information about a system or its users by analyzing communication patterns. Analyzing traffic does not necessitate looking at the messages' content, which may or may not be readable.
A sophisticated method for examining and analyzing the data packets that make up network traffic in order to spot any unusual activity is network traffic analysis (NTA). It combines rule-based detection, behavior modeling, and machine learning.
To know more about traffic analysis. , click here:
https://brainly.com/question/21479413
#SPJ11
What number system is the basis for all of the powerful computers and electronic devices in the world?
Answers
Answer:
Binary
Explanation:
HURRY IT'S URGENT
How would you create a variable named myDog and give it the value "Karel"?
options:
var myDog = "Karel":
var myDog = Karel
var myDog = "Karel";
var my Dog = "Karel"
What JavaScript function do we use to print out a message to the user?
options:
printLn()
print()
print
println();
Answers
The variable myDog and the value "Karel" are illustrations of assigning values to variable
The statement that creates the variable is (c). var myDog = "Karel";The function to print in JavaScript is (b) print()How to create the variable?
To create a variable in JavaScript, you have to add the keyword "var".
Given that the variable name is myDog; So, we have:
var myDog
The value of the variable is "Karel".
Hence, the assignment statement is: C. var myDog = "Karel";
Function to print in JavaScriptTo print in JavaScript, we make use of the print() statement
Hence, the function to print in JavaScript is (b) print()
Read more about JavaScript at:
https://brainly.com/question/16698901
In the Space Invaders game that you created in the unit using Scratch, how does the spaceship know when it is hit?
A.
A sound will play when it has been hit.
B.
It should receive a message broadcast from the laser beam.
C.
It should receive a message that will be broadcast by the enemy.
D.
A message will pop up, forcing the player to quit.
Answers
How to fix the ""You exceeded your current quota please check your plan and billing details"" error?
Answers
The error message "You exceeded your current quota, please check your plan and billing details" usually indicates that you have reached the limit of the resources or usage included in your account plan. Here are some steps to fix this error:
Review your account plan and billing details to make sure you understand the limits of your subscription and what resources you are using.
Check if you are exceeding any usage limits for your account plan. You may need to upgrade to a higher plan or purchase additional resources to continue using the service.
Review your usage history and see if there are any spikes or unexpected increases in usage that could have caused you to exceed your limits.
If you believe there is an error or issue with your account, contact customer support for the service you are using to troubleshoot the issue.
If none of these steps work, you may need to consider finding an alternative service or solution that better fits your usage needs.
Overall, fixing this error requires understanding your account plan and usage, and taking appropriate steps to address any issues or limitations.
Learn more about error message click here:
brainly.com/question/30225833
#SPJ11
how can you add multiple adjustments to one account in a work sheet?
Answers
In the unadjusted trial balance, a new line can be added below the affected account.
What is a worksheet?In documents, the term Worksheet refers to a collection of cells organized in rows and columns. It is the working surface with which you interact to enter data.
Add multiple adjustments to one account in a worksheet by:
Determine the account.In the worksheet, add a new column next to account and label it "Adjustments."Enter the amounts of the adjustments as positive or negative numbers in the "Adjustments" column, depending on whether they increase or decrease the account balance.Adjustments are totaled in the "Adjustments" column.To calculate the adjusted balance, add the total adjustments to the account's current balance.Label the final balance "Adjusted Balance" and place it in the following column.Repeat the preceding steps for any other accounts that require adjustments.Thus, this way, one can add multiple adjustments to one account in a worksheet and arrive at an accurate adjusted balance for the account.
For more details regarding worksheet, visit:
https://brainly.com/question/13129393
#SPJ1
A Creative Commons license is applied to a copyright license to provide specific
guidelines for the use of content.
True
False
Answers
Answer:
CC licenses are an easy way to contractually regulate the use of copyright protected work. They are valid worldwide, which means they are applicable internationally. Creative Commons itself is neither a publisher of content nor a contracting party of authors and rights owners who distribute their content under CC-licensed agreements.
what is capable of performing several tasks and allows the user to select the task?
Answers
A versatile multi-purpose device, such as a smartphone or a computer, is capable of performing several tasks and allows the user to select the task.
These devices offer a wide range of functionalities, including communication, browsing the internet, playing games, accessing various applications, and more. They provide users with the flexibility to switch between tasks based on their needs and preferences, enhancing productivity and convenience. The user can choose to make calls, send messages, browse websites, check emails, run applications, or engage in other activities, making these devices highly adaptable and customizable to individual requirements.
Learn more about multi-purpose device here:
https://brainly.com/question/4197572
#SPJ11
To evaluate the performance of a security system, administrators must establish system performance _____________________
Answers
To evaluate the performance of a security system, administrators must establish system performance baselines.
What is a performance baseline?A baseline for any kind of performance measure is known to be one that often looks at the the average stages or level of the work that one is currently working on.
Note that it often compare future performance levels using test so as to see if performance has changes and as such to evaluate the performance of a security system, administrators must establish system performance baselines.
Learn more about security system from
https://brainly.com/question/25720881
#SPJ1