6.5 code practice edhesive
If anyone could help... thanks !
Answers
Edhesive is an online learning platform that offers computer science courses, including coding, for high school students. One of the courses they offer is AP Computer Science A, which covers topics such as programming in Java, object-oriented programming, and data structures and algorithms.
As part of this course, students work on a variety of coding projects and assignments, including the 6.5 Code Practice.
The 6.5 Code Practice assignment is a programming challenge that requires students to write a Java program that calculates and displays the area and perimeter of a rectangle. The program should prompt the user to enter the length and width of the rectangle, calculate the area and perimeter using the formulae A = length * width and P = 2 * (length + width), and then display the results to the user.
To complete this assignment, students should start by creating a new Java class and defining a main method. They should then use the Scanner class to prompt the user for input and store the values in variables. After that, they can use the formulae to calculate the area and perimeter and store the results in variables. Finally, they should use the System.out.println() method to display the results to the user.
To know more about platform visit:
https://brainly.com/question/29548334
#SPJ11
Related Questions
What is the next line? >>> myTuple = [10, 20, 50, 20, 20, 60] >>> myTuple.index(50) 1 2 4 3
Answers
Answer:
2
Explanation:
got right on edg.
Answer:
2
Explanation:
i got it wrong for the right answer
Select the correct navigational path to sort data using multiple levels. click the tab on the ribbon, and look in the gallery. select the rows or columns you wish to sort. select . add a level, and another, with the parameters needed, and click ok.
Answers
To sort data using multiple levels, follow these steps:Click on the tab on the ribbon that corresponds to the application you are using (e.g. Microsoft Excel).
Look for the "Sort & Filter" option in the gallery of options available on the ribbon.Select the rows or columns you wish to sort by clicking on them.Click on the "Sort & Filter" option and select "Custom Sort" from the drop-down menu.In the "Sort" dialog box, add a level by clicking on the "Add Level" button.Select the appropriate parameters for the first level of sorting (e.g. sort by "Last Name" in alphabetical order).Repeat step 5 and step 6 to add additional levels of sorting as needed.Click "OK" to apply the sorting to the selected rows or columns.By following these steps, you can sort data using multiple levels in a way that meets your specific needs and requirements.
To learn more about sort click on the link below:
brainly.com/question/29839923
#SPJ4
Answer:
1. Data. 2. Sort & Filter. 3. Sort.
Need answer ASAP
In which phrase does software coding and testing happen in the spiral model?
The spiral model does not have a separate testing phase. Both software coding and testing occurs during the _____ phase.
Answers
both software coding and testing occurs during Engineering phase
After thoroughly evaluating a supplier, many organizations summarize evaluations using a supplier ____ matrix-a type of weighted scoring model.
Answers
After thoroughly evaluating a supplier, many organizations summarize evaluations using a supplier evaluation matrix-a type of weighted scoring model.
What is evaluation matrix?This is a tool, used to measure proposals, submitted by suppliers. It is basically meant to rank proposals based on defined criteria so that the best can be chosen.
In evaluation matrix, a score is assigned to each criteria that was considered under different categories and then the supplier with the highest score is selected to do business with.
Using evaluation matrix assess the suitability of suppliers to the business, who can work with the business for a long time hence, an essential tool for planning and organizing an evaluation.
Learn more about evaluation matrix here: https://brainly.com/question/15071654
#SPJ1
program that shows if it's an integer or not
Answers
during a regional state of emergency, an internet service provider offered three months of free internet access to anyone affected by the crisis. this effort was intended to help reduce the impact of ___________.
Answers
During a regional state of emergency, an internet service provider offered three months of free internet access to anyone affected by the crisis. this effort was intended to help reduce the impact of Digital divide.
Explain what the digital divide is?The difference between demographic groups and geographic areas with unrestricted access to contemporary information and communications technology (ICT) is known as the "digital divide." The telephone, television, computers, and internet connectivity are examples of this technology.
Therefore, one can say that unfair access to digital devices including laptops, cellphones, tablets, and the internet is known as the "digital divide." The access to resources and information is divided and unequal due to the digital divide.
Learn more about Digital divide from
https://brainly.com/question/7478471
#SPJ1
Anyone know? I don’t know how to do this. Btw this is robotics and this is RPM

Answers
Answer:
it is the 2nd one
Explanation:
Users of a _____ database have access through their personal computers linked to local or wide area networks
Answers
Answer:
Company
Explanation:
A company database is a database of a firm or organization that contains the information about the firm's employees, their products, services, and as well their client's and customers' details.
This is often kept on the main database server and arranged and organized by a database administrator.
Hence, Users of a COMPANY database have access through their personal computers linked to local or wide area networks
how do these ideas connect?

Answers
Answer:they are connecting because they are showing adult good of either men or women
Explanation:
An example of documentary evidence that might be presented at trial for a cyber crime is:
A. None of these choices.
B. data retrieved from slack space on a hard drive.
C. a cellular telephone.
D. a photocopy of a hacker’s spreadsheet of telephone numbers and e-mail addresses.
Answers
An example of documentary evidence that might be presented at trial for cybercrime is a photocopy of a hacker’s spreadsheet of telephone numbers and e-mail addresses. Thus, option D is correct.
What is the evidence?
Evidence is really the data used to attempt to support anything in a court of justice. Evidence is gathered from people, artifacts, and records. The only means through which the court may draw conclusions and reach a ruling is via the use of evidence.
According to the definition of information, it is the demonstration of any claim to be true. A hard copy of a hacker's worksheet with contact information and e-mail accounts is an illustration of documented evidence that might be used in court to prove a cybercrime. Therefore, option D is the correct option.
Learn more about evidence, here:
https://brainly.com/question/14370298
#SPJ2
In Java I’m having trouble with variables. When I try to call a variable from my while loop it says, “finger cannot be resolved to a variable.” The error is on line 49.

Answers
You're declaring variable finger inside your while loop so it only exists inside your while loop. You're then trying to use your finger variable outside your while loop, which is impossible because finger only exists inside your while loop.
Try declaring total at the beginning of your program, adding finger to total before you break from your while loop and then adding randNum to your total at the end.
To better understand why you can't use finger outside your while loop, look up "java scope". This will explain why you can only use variable in the regions they're declared in.
what is role can ICT play in helping school take part in social responsibility
Answers
Answer:
The answer is below
Explanation:
Given that Social responsibility deals with ideas that individuals or groups of people are expected or bound to work in alliance with other individuals or groups of people in favor of the generality of society.
Hence, some of the role ICT can play in helping school take part in social responsibility are:
1. Helps students to have independent access to knowledge
2. It assists the students with special needs
3. It helps the teachers to teach outside the comfort of the classroom only.
4. It exposes teacher and students to more knowledge and opportunities
5. The school governing body can access people and the community's opinions about ways to improve the school better.
6. It exposes the school to more ideas and opportunities.
7. It can be used to assist the school in improving the quality of education, both for the teachers and students side.
help
If we are looking at the predictor "car type," which can take on the values "sedan" "coupe" "truck" "suv" "van" how many binary decision variables would we need to code this data into a usable format?
Answers
If we are looking at the predictor "car type," which can take on the values "sedan" "coupe" "truck" "suv" "van", we would need 4 binary decision variables to code this data into a usable format.
A binary decision variable is a variable with only two possible values: 1 or 0. The variable is referred to as a binary variable, a binary indicator, or a 0-1 variable .The binary variable is used to answer yes/no questions. the binary variable " the binary variable is set to 0.To code the car type data into a usable format, we can use the binary decision variables.
We can use four binary variables to code the data into a usable format. We can use one variable for each category of car type. The values of the binary variables for the different categories are as follows:Sedan - 1000Coupe - 0100Truck - 0010SUV - 0001Using this format, if a car is a sedan, its binary decision variable would be set to 1000. If a car is a coupe, its binary decision variable would be set to 0100, and so on.
To know more about sedan visit:
https://brainly.com/question/24286177
SPJ11
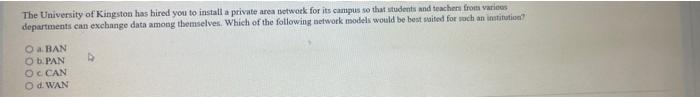
the university of kingston has hired you to install a private area network for its campus so that students and teachers from various departments can exchange data among themselves. which of the following network models would be best suited for such an institution?
Answers
The network models that would be best suited for such an institution is known as CAN.
How does a CAN network work?The CAN is known to be a kind of a peer-to-peer network. This is a term that connote that there is not any master that act to controls when the all the nodes have access to read as well as write data on the CAN bus.
Note that if a CAN node is said to be ready to transmit data, it looks to see if the bus is said to be busy and then it is one that often writes a CAN frame onto the network.
Note that network model is seen as a kind of database model that is set up as a flexible method to showing objects and their relationships
Therefore, The network models that would be best suited for such an institution is known as CAN.
Learn more about network models from
https://brainly.com/question/23369075
#SPJ1
Why should even small-sized companies be vigilant about security?
Answers
Answer:businesses systems and data are constantly in danger from hackers,malware,rogue employees, system failure and much more
Explanation:
Feasibility Analysis for Software Development (testing
software):
1. Operational
2. Technical
3. Schedule
4.Legal
5. Contractual and Political
Answers
Feasibility analysis is a critical step in software development, considering factors such as operational, technical, schedule, legal, contractual, and political aspects to ensure successful and effective software implementation while mitigating risks.
Conducting a feasibility analysis is essential in software development to assess the operational, technical, schedule, legal, contractual, and political factors.
Evaluating these factors helps determine whether the software can be effectively used in the business environment, built with available technology, completed within the proposed time, compliant with legal requirements, and aligned with contractual and political goals.
This analysis minimizes risks and ensures the success and effectiveness of the software. It enables the development team to make informed decisions and consider necessary adjustments or mitigations during the development process.
By addressing feasibility considerations, software development projects can increase their chances of meeting user requirements, delivering value, and achieving desired outcomes.
Learn more about software development: brainly.com/question/26135704
#SPJ11
when tejay started his new job, he found the step-by-step process for logging into the company server set forth in a laminated document by computer. what type of information is represented by this document?
Answers
This document represents a procedural guide, A Standard Operating Procedure (SOP), which outlines the steps needed to successfully log into the company server. It serves as a reference for employees and helps them understand the steps to complete the task.
When Tejay started his new job, he found the step-by-step process for logging into the company server set forth in a laminated document by computer. This document represents a Standard Operating Procedure (SOP).
A Standard Operating Procedure (SOP) is a comprehensive and step-by-step set of written instructions designed to serve as a guide for employees on how to perform routine or complex procedures or practices effectively and safely.
In any organization or business, Standard Operating Procedures (SOPs) are essential for consistent quality, efficient execution, and to meet regulatory requirements. They offer a step-by-step guide to facilitate consistency, reduce variability, and enhance productivity in various business operations.
For more such questions on Standard Operating Procedure (SOP) , Visit:
https://brainly.com/question/13530380
#SPJ11
what is the result for this expression?
4 + 8 * 3 / 4 + 5 % 2
HELP THIS IS IN JAVA
Answers
The result of the given expression (4 + 8 x 3 / 4 + 5 % 2) using PEDMAS is 29.
To solve this expression, follow the order of operations (PEMDAS/BODMAS), which stands for Parentheses/Brackets, Exponents/Orders, Multiplication and Division (from left to right), and Addition and Subtraction (from left to right).
Given expression: 4 + 8 x 3 / 4 + 5 % 2
Step 1: Perform multiplication and division from left to right:
8 x 3 = 24
4/4 = 1
5 % 2 = 1
Step 2: Substitute the results back into the expression:
4 + 24 / 1 + 1
Step 3: Perform addition:
4 + 24 + 1 = 29
So, the result of the given expression is 29.
Learn more about PEDMAS here:
https://brainly.com/question/24086845
#SPJ3
Symptoms of withdrawal may include
A)Difficulty breathing
B)Nausea, vomiting, or diarrhea
C)Racing heart or palpitations
D)All of the above.
PLEASE HELP
Answers
Answer:
B. Neusea, vomiting, or diarrhea
Answer:
d
Explanation:
Withdrawal is a nasty thing and someone shouldn't do drugs but if they're going through withdrawal they will have all of these symptoms.
which ics functional area tracks resources collects and analyzes information ?
Answers
The Intelligence, Surveillance, and Reconnaissance (ISR) functional area tracks resources, collects, and analyzes information. The Intelligence, Surveillance, and Reconnaissance (ISR) functional area is responsible for tracking resources, collecting information, and analyzing data.
This information is used to support military operations and decision-making. ISR operations can include activities such as reconnaissance, surveillance, and intelligence gathering using various means such as manned and unmanned aircraft, satellites, and ground-based sensors.
Learn more about functional area: https://brainly.com/question/29292490
#SPJ4
How do I do this in Access? Please list all steps in detail.
Create a new relationship between the EmployeeID field in the Professor table and the Advisor field in the Student table. Ensure that values in the Advisor field have a corresponding value in the EmployeeID field.
Answers
Steps in detail to do in Access here:
Open Micr0soft Access and open the database that contains the Professor and Student tables.In the Navigation Pane, right-click on the Student table and select "Design View" from the context menu.In the Design View, click on the Advisor field to select it.Go to the "Database Tools" tab in the Ribbon and click on the "Relationships" button.In the Relationships window, click on the "New" button.In the "Table/Query" field, select the Professor table. In the "Related Field" field, select the EmployeeID field.In the "Table/Query" field, select the Student table. In the "Related Field" field, select the Advisor field.Click on the "Enforce Referential Integrity" checkbox. This will ensure that any values in the Advisor field must have a corresponding value in the EmployeeID field.Click on the "Create" button to create the relationship.Click on the "Close" button to close the Relationships window.Save the changes to the Student table by clicking on the "Save" button in the Design View.Close the Design View of the Student table.You have now successfully created a new relationship between the EmployeeID field in the Professor table and the Advisor field in the Student table and ensured that values in the Advisor field have a corresponding value in the EmployeeID field.
ACCESS FOR VALUE RELATIONSHIPIn Access, you can set up connections between tables in one of three ways.
This is a one-to-many connection. An order tracking database might include two tables: one for Customers and another for Orders.A connection between multiple parties. The Products table's connection to the Orders table is up next.Individual interaction.Learn more about Access Relationship here:
https://brainly.com/question/20038736
#SPJ4
What special enterprise VPN supported by Cisco devices creates VPN tunnels between branch locations as needed rather than requiring constant, static tunnels
Answers
Answer:
Dynamic Multipoint VPN
Explanation:
in a basic program with 3 IF statements, there will always be _________ END IIF's.
a)2
b)3
c)4
Answers
Answer:
c)4
Explanation:
Hope it could helps you
Exercise 2. 4. 8: Greetings and Salutations5 points
Write a class called Salutations that prints various greetings and salutations.
The class should have one instance variable, a String called name to represent the person to whom the salutations are directed.
The class should have the following methods
A constructor that takes a String to initialize name with
public void addressLetter()
public void signLetter()
public void addressMemo()
public void signMemo()
addressLetter should print "Dear name", where name is replaced by the value of the instance variable name
signLetter() should print
"Sincerely,
name"
where name is replaced by the value of the instance variable name
addressMemo should print "To whom it may concern"
signMemo should print
"Best,
name
where name is replaced by the value of the instance variable name
Answers
Below is the implementation of the "Salutations" class in Java that meets the provided requirements:
public class Salutations {
private String name;
public Salutations(String name) {
this.name = name;
}
public void addressLetter() {
System.out.println("Dear " + name + ",");
}
public void signLetter() {
System.out.println("Sincerely,\n" + name);
}
public void addressMemo() {
System.out.println("To whom it may concern");
}
public void signMemo() {
System.out.println("Best,\n" + name);
}
public static void main(String[] args) {
Salutations salutations = new Salutations("John Doe");
salutations.addressLetter();
salutations.signLetter();
salutations.addressMemo();
salutations.signMemo();
}
}
Below is the implementation of the "Salutations" class in Java that meets the provided requirements:
java
Copy code
public class Salutations {
private String name;
public Salutations(String name) {
this.name = name;
}
public void addressLetter() {
System.out.println("Dear " + name + ",");
}
public void signLetter() {
System.out.println("Sincerely,\n" + name);
}
public void addressMemo() {
System.out.println("To whom it may concern");
}
public void signMemo() {
System.out.println("Best,\n" + name);
}
public static void main(String[] args) {
Salutations salutations = new Salutations("John Doe");
salutations.addressLetter();
salutations.signLetter();
salutations.addressMemo();
salutations.signMemo();
}
}
In the above class, we have an instance variable called "name" of type String, which represents the person to whom the salutations are directed. The class has a constructor that takes a String argument to initialize the "name" variable.
The class also includes the following methods as specified:
The "addressLetter" method prints "Dear name", where "name" is the value of the instance variable.
The "signLetter" method prints "Sincerely," on one line and then prints the "name" on the next line.
The "addressMemo" method prints "To whom it may concern".
The "signMemo" method prints "Best," on one line and then prints the "name" on the next line.
To test the functionality of the "Salutations" class, a "main" method is included that creates an instance of the class with a sample name "John Doe". It then calls the different methods to demonstrate the expected output.
Executing the main method will result in the following output:
Dear John Doe,
Sincerely,
John Doe
To whom it may concern
Best,
John Doe
Each method performs its respective task as described, utilizing the instance variable "name" in the output statements.
For more questions on Java
https://brainly.com/question/31569985
#SPJ11
what are the two types of screen modes in Qbasic graphics?
Answers
Answer:MDPA with Monochrome Display: Mode 0
The IBM Monochrome Display and Printer Adapter (MDPA) is used to connect only to a monochrome display. Programs written for this configuration must be text mode only.
CGA with Color Display: Modes 0, 1, and 2
The IBM Color Graphics Adapter (CGA) and Color Display are typically paired with each other. This hardware configuration permits the running of text mode programs, and both medium-resolution and high-resolution graphics programs.
EGA with Color Display: Modes 0, 1, 2, 7, and 8
The five screen modes 0, 1, 2, 7, and 8 allow you to interface to the IBM Color Display when it is connected to an IBM Enhanced Graphics Adapter (EGA). If EGA switches are set for CGA compatibility, programs written for modes 1 and 2 will run just as they would with the CGA. Modes 7 and 8 are similar to modes 1 and 2, except that a wider range of colors is available in modes 7 and 8.
The two screen modes of QBasic are SCREEN 1 that has 4 background colour attributes and SCREEN 2 is monochrome that has black background and white foreground.
There is also the:
(1) Immediate mode
(2) Program mode
A type of screen mode function are:SCREEN 1 that has 4 background colour attributes.
SCREEN 2 is monochrome that has black background and white foreground.
Learn more about screen modes from
https://brainly.com/question/16152783
How did tribes profit most from cattle drives that passed through their land?
A.
by successfully collecting taxes from every drover who used their lands
B.
by buying cattle from ranchers to keep for themselves
C.
by selling cattle that would be taken to Texas ranches
D.
by leasing grazing land to ranchers and drovers from Texas
Answers
The way that the tribes profit most from cattle drives that passed through their land is option D. By leasing grazing land to ranchers and drovers from Texas.
How did Native Americans gain from the long cattle drives?When Oklahoma became a state in 1907, the reservation system there was essentially abolished. In Indian Territory, cattle were and are the dominant economic driver.
Tolls on moving livestock, exporting their own animals, and leasing their territory for grazing were all sources of income for the tribes.
There were several cattle drives between 1867 and 1893. Cattle drives were conducted to supply the demand for beef in the east and to provide the cattlemen with a means of livelihood after the Civil War when the great cities in the northeast lacked livestock.
Lastly, Abolishing Cattle Drives: Soon after the Civil War, it began, and after the railroads reached Texas, it came to an end.
Learn more about cattle drives from
https://brainly.com/question/16118067
#SPJ1
In order to define dimensions of a Sketch of an Extrude properly we need to do the following: Select the references to locate the Sketch Select the Part Edges that may serve as a reference Create refe
Answers
To define dimensions of a Sketch of an Extrude properly we need to select the references to locate the Sketch and select the Part Edges that may serve as a reference.
A Sketch of an Extrude is a drawing that allows the representation of the features of an extrusion product. To define dimensions of a Sketch of an Extrude, we need to do the following steps:Step 1: Select the references to locate the Sketch.To create a sketch of an extrude, we need to select the plane that would serve as the surface for the sketch. After selecting the plane, we need to locate the sketch in the plane by selecting the references. References are the points on the surface that would be the base for the sketch. We need to locate these points in order to place the sketch accurately.
Step 2: Select the Part Edges that may serve as a reference. After selecting the references, we need to choose the part edges that may serve as a reference for the sketch. These part edges would define the thickness and other properties of the extrusion product. Therefore, selecting them accurately is crucial for the proper definition of dimensions of a Sketch of an Extrude.
Know more about Sketch, here:
https://brainly.com/question/15947065
#SPJ11
Write a description of the photograph to someone who cannot see the photograph. Be sure to include the title of the photograph and photographer credit in your response.
Answers
Answer:
I do not have a photo as a example but you could explain the feeling that it gives you and if its gloomy or happy go lucky you can also explain the main colors in the photo as well as the charters and/or type of object/s are in the photo
find a recurrence relation for the number of regions created by n mutually intersecting circles on a piece of paper (no three circles have a common intersection point).
Answers
Assume that the plane is divided into rn regions by n circles. The next step is to add a new circle, C, which non-trivially intersects all of the previous n circles.
You can begin anywhere on C and circle C while crossing one of the other n circles twice. The arc of C from p0 to p1 splits one of the original rnregions into two smaller regions if p0 and p1 are two successive crossings. You repeat this 2n times, which results in a recurrence. Since rn+1=rn+some basic n function, you can pretty easily convert this expression into an expression for rn that is simply a sum. If you do it correctly, you can evaluate the summation in closed form to obtain the rn formula fairly quickly.
Learn more about function here-
https://brainly.com/question/28939774
#SPJ4
what human-readable data
Answers
Explanation:
what?? there is no question
Answer: A human-readable medium or human-readable format is any encoding of data or information that can be naturally read by humans.