3. An engineer has planned to use Class B network 172.19.0.0 and a single subnet mask throughout the network. The answers list the masks considered by the engineer. Choose the mask that, among the answers, supplies the largest number of hosts per subnet, while also supplying enough subnet bits to support 1000 subnets.
Answers
Answer:
11 bits
Explanation:
A Class B network, such as the one described in the question, has an address range of 172.16.0.0 to 172.31.255.255. In order to use a single subnet mask throughout the network, the engineer must choose a mask that provides enough subnet bits to support 1000 subnets while also allowing for a large number of hosts per subnet.
The largest number of hosts per subnet is provided by a mask with the fewest number of subnet bits. However, this would not be sufficient to support 1000 subnets. Therefore, the engineer must choose a mask that provides a balance between the number of hosts per subnet and the number of subnet bits.
One possible mask that meets these criteria is 255.255.248.0. This mask provides 21 subnet bits, which is enough to support up to 2^21 = 2097152 subnets. It also provides 11 host bits, which allows for up to 2^11 = 2048 hosts per subnet. This is the largest number of hosts per subnet among the masks considered by the engineer, while also providing enough subnet bits to support 1000 subnets.
Related Questions
please answer fast computer picture above

Answers
Answer:embedded computers are found in cats, appliances like light switches and voic actived tvs, security cameras, dvd players and elevators
Explanation:
1.Create a function that accepts any number of numerical (int and
float) variables as positional arguments and returns the sum ofthose variables.
2.Modify the above function to accept a keyword argument
'multiplier'. Modify the function to return an additional variable
that is the product of the sum and the multiplier.
3.Modify the above function to accept an additional keyword
argument 'divisor'. Modify the function to return an additional
variable that is the quotient of the sum and the divisor.
Answers
Answer:
This function accepts any number of numerical variables as positional arguments and returns their sum:
python
Copy code
def sum_numbers(*args):
return sum(args)
This function accepts a multiplier keyword argument and returns the product of the sum and the multiplier:
python
Copy code
def sum_numbers(*args, multiplier=1):
total_sum = sum(args)
return total_sum * multiplier
This function accepts an additional divisor keyword argument and returns the quotient of the sum and the divisor:
python
Copy code
def sum_numbers(*args, multiplier=1, divisor=1):
total_sum = sum(args)
return total_sum * multiplier, total_sum / divisor
You can call these functions with any number of numerical arguments and specify the multiplier and divisor keyword arguments as needed. Here are some examples:
python
# Example 1
print(sum_numbers(1, 2, 3)) # Output: 6
# Example 2
print(sum_numbers(1, 2, 3, multiplier=2)) # Output: 12
# Example 3
print(sum_numbers(1, 2, 3, multiplier=2, divisor=4)) # Output: (8, 3.0)
Which of the following accurately describes a user persona? Select one.
Question 6 options:
A user persona is a story which explains how the user accomplishes a task when using a product.
A user persona should be based only on real research, not on the designer’s assumptions.
A user persona should include a lot of personal information and humor.
A user persona is a representation of a particular audience segment for a product or a service that you are designing.
Answers
A user persona is a fictionalized version of your ideal or present consumer. In order to boost your product marketing, personas can be formed by speaking with people and segmenting them according to various demographic and psychographic data and user.
Thus, User personas are very helpful in helping a business expand and improve because they reveal the various ways customers look for, purchase, and utilize products.
This allows you to concentrate your efforts on making the user experience better for actual customers and use cases.
Smallpdf made very broad assumptions about its users, and there were no obvious connections between a person's occupation and the features they were utilizing.
The team began a study initiative to determine their primary user demographics and their aims, even though they did not consider this to be "creating personas," which ultimately helped them better understand their users and improve their solutions.
Thus, A user persona is a fictionalized version of your ideal or present consumer. In order to boost your product marketing, personas can be formed by speaking with people and segmenting them according to various demographic and psychographic data and user.
Learn more about User persona, refer to the link:
https://brainly.com/question/28236904
#SPJ1
why it is important to follow the procedures and techniques inmaking paper mache?
pleaseee help i needed it right now
Answers
Answer:
otherwise it will go wrong
Wider channel bandwidth ________. increases transmission speed allows more channels to be used in a service band both increases transmission speed and allows more channels to be used in a service band neither increases transmission speed nor allows more channels to be used in a service band
Answers
Wider channel bandwidth decreases transmission speed.
What is Wider channel bandwidth?Wider WiFi channel widths is known to be a bandwidth that is made up of 40 MHz and 80 MHz width.
They are known to be used often in the 5 GHz frequency band. In this type pf band, there are said to have a lot of WiFi channels and also less overlapping channels and as such, Wider channel bandwidth decreases transmission speed.
Learn more about bandwidth from
https://brainly.com/question/4294318
I am trying to figure out pseudocode for displaying a person's BMI based on BMI = weight x 703 / height x height.
Answers
The faster an object is moving, the ________ the shutter speed needs to be in order to freeze motion.
Answers
Answer:
jkdsdjdshj,dfh.jhdfbhjf
Explanation:
bchSDCMHCXZ NHCXHBDSVCHDH,KC NBDBSDMJCBDBFD,JHCDSMNBBNCSCBFDNJCFJKC FMNSDNMSDFCH ĐS,CJDBS,CBSJBV,FJNDBFDSFDVBFĐDVFBVJFDCDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDHCD
You should use a shutter speed that is at least 1/500th of a second or higher. However, remember that fast shutter speeds may result in underexposed photographs.
Hope it helps you:)
simple explanation of how a satellite works
Answers
Answer:
A satellite is basically a self-contained communications system with the ability to receive signals from Earth and to retransmit those signals back with the use of a transponder —an integrated receiver and transmitter of radio signals.
Explanation:
Consider any tasks performed in real life, for example, driving a taxi. The task you pick involves many functions. Driving a taxi involves picking up customers, and quickly and safely transporting them to their destination. Go through the components of the AI cycle to automate the problem you choose. List the useful precepts available. Describe how you will represent your knowledge. Based on that, describe how you will use reasoning to make and execute a plan expected to achieve a goal or obtain maximum utility. (this is for artificial intelligence, but they did not have that option)
Answers
50 POINTS!!!!! WILL MARK BRAINLIEST!!!!!HURRY!!!!!
Your Python program has this code.
for n = 1 to 10:
position = position + 10 # Move the position 10 steps.
direction = direction + 90 # Change the direction by 90 degrees.
You decided to write your program in a block programming language.
What type of block do you need to accomplish what this line does?
direction = direction + 90 # Change the direction by 90 degrees.
A) event
B) voice and graphics
C) control
D) motion
Answers
Answer:
control
Explanation:
Repeat 10 times is a control block.

The type of block that would be needed to accomplish the line would be C. Control
What is Programming?This refers to the set of code that is given to the computer by a programmer to execute a task.
Hence, we can see that from the line of code that shows a sequence of numbers from 1 to 10 and to move and change the direction of the position and degree, to write this program in a block programming language, the type of block that is needed is a control block.
Read more about block programming here:
https://brainly.com/question/14525641
#SPJ2
In Java only please:
4.15 LAB: Mad Lib - loops
Mad Libs are activities that have a person provide various words, which are then used to complete a short story in unexpected (and hopefully funny) ways.
Write a program that takes a string and an integer as input, and outputs a sentence using the input values as shown in the example below. The program repeats until the input string is quit and disregards the integer input that follows.
Ex: If the input is:
apples 5
shoes 2
quit 0
the output is:
Eating 5 apples a day keeps you happy and healthy.
Eating 2 shoes a day keeps you happy and healthy
Answers
Answer:
Explanation:
import java.util.Scanner;
public class MadLibs {
public static void main(String[] args) {
Scanner input = new Scanner(System.in);
String word;
int number;
do {
System.out.print("Enter a word: ");
word = input.next();
if (word.equals("quit")) {
break;
}
System.out.print("Enter a number: ");
number = input.nextInt();
System.out.println("Eating " + number + " " + word + " a day keeps you happy and healthy.");
} while (true);
System.out.println("Goodbye!");
}
}
In this program, we use a do-while loop to repeatedly ask the user for a word and a number. The loop continues until the user enters the word "quit". Inside the loop, we read the input values using Scanner and then output the sentence using the input values.
Make sure to save the program with the filename "MadLibs.java" and compile and run it using a Java compiler or IDE.
Steps taken when hacking a person using the fake WAP technique
Answers
Answer:
simply, tiss unknown and has to true answer
Which of the following is a potential concern with having an online profile (1 point)
on your instant messaging service that contains personal information like
your address or favorite hobbies?
A.Your friends may not agree with what you write there.
B.You might misrepresent yourself.
C.You might become a target of users who wish to make inappropriate contact with you.
D.Your personal information might change.
Answers
Answer:
C. You may become a target of users who wish to make inappropriate contact with you.
Explanation:
In "PUBATTLEGROUNDS” what is the name of the Military Base island?
Answers
Answer:
Erangel
Explanation:
Answer:
Erangel
Explanation:
The Military Base is located on the main map known as Erangel. Erangel is the original map in the game and features various landmarks and areas, including the Military Base.
The Military Base is a high-risk area with a significant amount of loot, making it an attractive drop location for players looking for strong weapons and equipment. It is situated on the southern coast of Erangel and is known for its large buildings, warehouses, and military-themed structures.
The Military Base is a popular destination for intense early-game fights due to its high loot density and potential for player encounters.
Hope this helps!
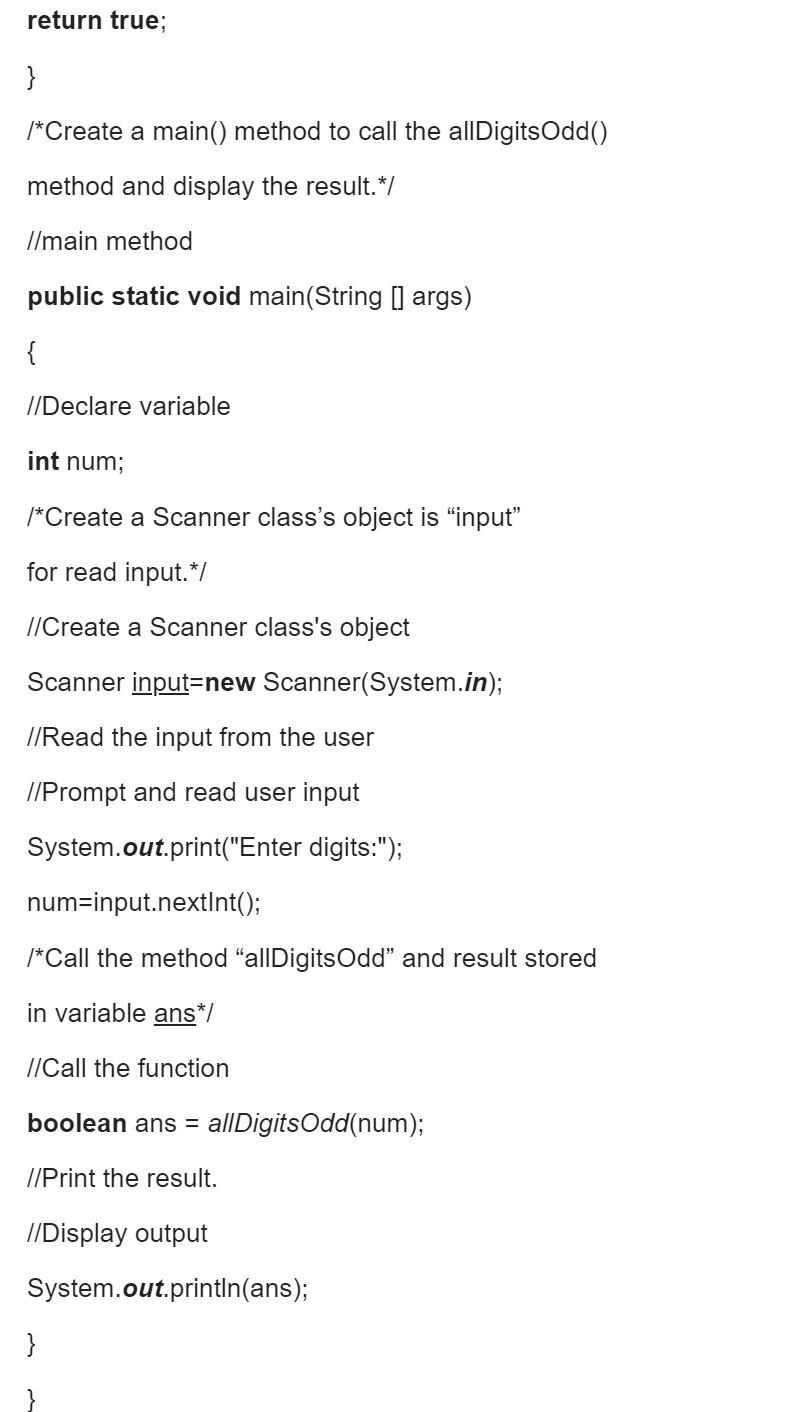
Write a method called allDigitsOdd that returns whether every digit of a positive integer is odd. Return true if the number consists entirely of odd digits (1, 3, 5, 7, 9) and false if any of its digits are even (0, 2, 4, 6, 8). For example, the call allDigitsOdd(135319) returns true but allDigitsOdd(9145293) returns false.
Answers
Answer:
Sample output:
Enter integer 3232423
true
Enter integer 12131231
false
Explanation:
Above is the output of the program and for the solution check the screenshots attach to understand clearly the program.
Thanks



Which of the following did you include in your notes?
Check all that apply.
how you will keep costs down
how you will offer a better product
how you will be innovative in what you offer
Id
Economía

Answers
Answer:
How you will be innovative in what you offer
Explanation:
personally I think all 3 but it is what it is
PLEASE FILL IN THE BLANK
With a bit depth of __ I can support 8 grayscale variations of black and white images.
Answers
Answer: Thre correct answer is 3 bit
Explanation:
Using binary, a 3-bit value can support 8 variations in grayscale:
1 000
2 001
3 010
4 011
5 100
6 101
7 110
8 111
Write a program that asks a user for 5 numbers. Provide a menu of options of 5 things that can be done with these numbers
Answers
Use a for loop to continually iterate through a series (that is either a list, a tuple, a dictionary, a set, or a string). This performs less like the for keyword seen in other programming languages and more like an iterator method used in other object-oriented programming languages.
How to write a program that asks a user for 5 numbers.?input = a ()
initial = int (a)
second = int and b = input() (b)
Third = int(c), and fourth = input ()
four = integer (d)
If a > b, a > c, or a > d,
print ('the largest number' + a),
and then elif a b, a, b > c, or b > d:
print ("the largest number")
elif b a> b or d > b or d > C:
print ("The greatest number is")
elif d >= a, b, or c:
print ('the smallest numbet is'+ d)
else:
num = 0
while num< 100:
num = num + 5
print(str(num))
print(’Done looping!’)
The complete question is : Write a program that asks the user to type in 5 numbers , and that outputs the largest of these numbers and the smallest of these numbers. So for example if the user types in the numbers 2456 457 13 999 35 the output will be as follows : the largest number is 2456 the smallest number is 35 in python ?
To learn more about loop refer to:
https://brainly.com/question/19344465
#SPJ1
The COOJA simulator is a utility to simulate wireless sensor systems. It serves as tool
to verify the operability of applications on target systems without having physical
access to these systems. Starting COOJA is as simple as double-clicking the COOJA
symbol on the virtual machine's desktop.
Compiling and running Contiki OS code in COOJA works by creating virtual sensor devices whose behavior can be specified by pointing COOJA to the .c files that
contain the corresponding program code.
a) Create a new simulation in COOJA (Menu item: File → New simulation... ). Enter a name of your choice, leave the default settings unchanged, and click Create. Next, add some motes with the hello-world
implementation to your simulation. To this end, navigate to the following menu item: Motes → Add motes → Create new mote type → Z1
mote. In the appearing window, navigate to the hello-world.c file in
the /home/student/contiki-ng/examples/hello-world directory and click
Compile, then Create. Increase the number of nodes to create to 20, and
keep the option for random positioning. Finally, click Add motes.
Unless already active, activate the Mote IDs option under the View menu
of the simulator's Network window. Twenty numbered circles will now occur, each one representing a single node with the given firmware. The number
in the circle specifies the node address. Furthermore, activate the Radio environment option in the View menu and then click on one of the nodes;
a green circle will appear around it. Click on the start button in the Simulation control window next, let the application run for about ten seconds
while taking note of the speed value displayed in the same window, then
click pause.
b) State an approximate average value of the observed simulation speed. Can
you think of what a speed over 100% might mean, and what speed values below 100% indicate?
c) Deduce from the observations in the Network window what the green circles
around nodes (after having clicked on the node) indicate. Try to drag-and-drop
nodes around to see if/how the circles change. Explain your observations.
d) Create a new simulation in COOJA. This time, load one node with the
udp-server from /home/student/contiki-ng/examples/rpl-udp and five
nodes with the udp-client from the same directory. Run the simulation to
verify that nodes exchange data with each other. For this purpose, set the required options under the View menu.
Using your mouse, drag one of the receiver motes in the Network window
far away from the remaining nodes such that its green and gray circles contain
no other nodes (you may need to enlarge the Network window to this end
and/or move other nodes to accomplish this task). In the Timeline window,
locate the entry for this particular node (hint: Look for the entry with the ID
of the node which you can find in the Network window).
Compare this node's activity (represented by the colors in the timeline and the
log output) with the activity of all other nodes. What are your observations?
Can you explain them? Hint: you may find it useful to enable further event
Answers
a) The simulation speed in COOJA refers to the speed at which the simulation is running compared to real-time. The average value of the observed simulation speed will vary depending on the specifications of the computer being used to run the simulation. A simulation speed over 100% means that the simulation is running faster than real-time. On the other hand, speed values below 100% indicate that the simulation is running slower than real-time.
What is the simulator about?b) The green circles around nodes in the Network window indicate the range of the radio signal of each node. The green circle represents the area where other nodes can be reached by a node with the corresponding radio signal. By dragging and dropping nodes, you can observe how the green circle changes to show the new range of the node's radio signal.
c) To verify that nodes are exchanging data with each other, a new simulation was created and one node was loaded with the udp-server and five nodes with the udp-client. By observing the Timeline window, it is possible to locate the activity of each node and compare it to the activity of all other nodes. When a node is dragged far away from the other nodes, the activity of this node (represented by the colors in the timeline and the log output) will be different compared to the activity of the other nodes. This observation can be explained by the fact that the node is now out of range of the radio signals of the other nodes, and therefore cannot exchange data with them.
d) To understand the observations, it is important to keep in mind that COOJA is a tool used to simulate wireless sensor systems, and the data exchange between nodes is simulated according to the specifications defined in the code. The observed differences in activity between nodes can be attributed to differences in the range of their radio signals, as well as other factors such as the timing of the data exchange between nodes.
Learn more about simulator form
https://brainly.com/question/24912812
#SPJ1
Please help I have no idea what to do :(
Write a program that simulates a coin flipping. Each time the program runs, it should print either “Heads” or “Tails”.
There should be a 0.5 probability that “Heads” is printed, and a 0.5 probability that “Tails” is printed.
There is no actual coin being flipped inside of the computer, and there is no simulation of a metal coin actually flipping through space. Instead, we are using a simplified model of the situation, we simply generate a random probability, with a 50% chance of being true, and a 50% chance of being false.
Answers
A Java Script program that simulates a coin flipping, so that each time the program runs, it should print either “Heads” or “Tails” along with the other details given is stated below.
Code for the above coin simulationvar NUM_FLIPS = 10;
var RANDOM = Randomizer.nextBoolean();
var HEADS = "Heads";
var TAILS = "Tails";
function start(){
var flips = flipCoins();
printArray(flips);
countHeadsAndTails(flips);
}
// This function should flip a coin NUM_FLIPS
// times, and add the result to an array. We
// return the result to the caller.
function flipCoins(){
var flips = [];
for(var i = 0; i < NUM_FLIPS; i++){
if(Randomizer.nextBoolean()){
flips.push(HEADS);
}else{
flips.push(TAILS);
}
}
return flips;
}
function printArray(arr){
for(var i = 0; i < arr.length; i++){
println("Flip Number " + (i+1) + ": " + arr[i]);
}
}
function countHeadsAndTails(flips){
var countOne = 0;
var countTwo = 0;
for(var i = 0; i < flips.length; i++){
if(flips[i] == HEADS){
countOne+=1;
}
else {
countTwo+=1;
}
}
println("Number of Heads: " + countOne);
println("Number of Tails: " + countTwo);
}
Learn more about Java Script:
https://brainly.com/question/18554491
#SPJ1
Anyone has any ideas for a gaming setup i can buy for christmas. Something with high framing rates (monitor included) for about 400 dollars. This is a social question for my class about computers and we need to find something for the class to use to)
Answers
Answer:
The one I am providing isn't a pre-built, but it does match your budget.
PARTS:
CPU AMD Ryzen 3 3200G AMD Ryzen 3 3200G $99
Motherboard Gigabyte B450M DS3H Gigabyte B450M DS3H $72
Memory G.Skill Aegis 16GB (2 x 8GB) DDR4-3200 CL16 G.Skill Aegis 16GB DDR4-3200 $61
Storage Crucial P1 500GB M2 NVMe SSD Crucial P1 500 GB M.2 $62
PC Case Cooler Master MasterBox Q300L TUF Edition Cooler Master Q300L TUF $47
Power Supply Thermaltake Smart BX1 RGB 550W 80+ Bronze Thermaltake Smart BX1 RGB 550W Power Supply 80 Plus Bronze $59
Total $398
Assume the variable s is a String and index is an int. Write an if-else statement that assigns 100 to index if the value of s would come between "mortgage" and "mortuary" in the dictionary. Otherwise, assign 0 to index.
Answers
Using the knowledge in computational language in python it is possible to write a code that Assume the variable s is a String and index is an int.
Writting the code:Assume the variable s is a String
and index is an int
an if-else statement that assigns 100 to index
if the value of s would come between "mortgage" and "mortuary" in the dictionary
Otherwise, assign 0 to index
is
if(s.compareTo("mortgage")>0 && s.compareTo("mortuary")<0)
{
index = 100;
}
else
{
index = 0;
}
See more about JAVA at brainly.com/question/12975450
#SPJ1

Image below please help

Answers
Answer:
Open original documentPlace cursorHighlight textCtrl+CSwitch to new documentCtrl+Vwhat is document formatting?
Answers
Answer:
Document formatting refers to the process of designing and arranging the content, layout, style, and structure of a document to make it more readable, visually appealing, and professional-looking. Document formatting involves applying different formatting techniques such as setting margins, adding page numbers, adjusting font size and style, indenting paragraphs, adding headings and subheadings, using bullet points and numbered lists, and incorporating images, tables, and charts to enhance the presentation of the document.
Explanation:
What is an online payment gateway?
Answers
Answer:
it is the key component of the electronic payment processing system, or through which type of payment you are giving through.
Explanation:
brainiliest
which service is a major commercial cloud platform?
a. Microsoft SQL Services
b. SAP Cloud Services
c. Amazon Web Services
d. Oracle Enterprise Services
Answers
Answer: Amazon Web Service
Explanation:
The service that's a major commercial cloud platform is the Amazon Web Service.
Amazon Web Services offers global cloud based products which include databases, storage, networking, IoT, developer tools, analytics, mobile, develo management tools, security applications etc.
The services are of immense benefit to organizations as they help them in achieving their goals as it helps in lowering IT costs, increase speed, enhance efficiency and revenue.
The parameter passing mechanisn used in C is
Answers
Answer:
Hope you understand this answer

Pass by value is the answer
Please send a response to this email! This is for an assignment on appropriately answering to negative feedback at work. "Your report on SHG is, frankly, substandard. We can’t send it out the door when it lacks last month’s sales figures, and it is even missing the data on user interactions. This is just not acceptable, and I don’t see how you can continue to work here if you can’t complete the simplest of your job duties."
Answers
Answer:
Explanation:
Receiving negative feedback about your work can be challenging, but it's important to approach it with professionalism and a willingness to improve. Here is a possible response to the feedback:
Thank you for bringing your concerns to my attention. I understand that the report I submitted on SHG was not up to the standards expected by the team, and I apologize for any inconvenience this may have caused. I appreciate your feedback and take full responsibility for the errors in the report.
I understand that the missing sales figures and user interaction data are critical components of the report, and I will work diligently to ensure that this information is included in any future reports. I am committed to improving my performance and ensuring that my work meets the expectations of the team.
Please let me know if there are any specific areas in which I need to improve or any additional resources that I can access to help me do my job better. I value your input and look forward to working with you to improve the quality of my work.
Thank you again for your feedback, and I am committed to doing my best to address any concerns you may have.
Write a command that will list the names of all executable files in the working directory, sorted by file size.
Answers
Answer:
The answer is "ls command".
Explanation:
The Is command is often used in Linux to sort the system files according to their size:
#ls – F | grep ‘*$’ -s
And the other regulation they can use is
#ls -Fla | grep ‘^\S*x\S*’
Its name collections of all non-executable files throughout the working directory could be accomplished with the command as follows:
find ! -term+|||-type s-t |find ! - term + ||| - type f-tr
Write a program that inputs numbers and keeps a
running difference. When the difference is less than 0,
output the difference as well as the count of how many
numbers were entered.
Sample Run
Enter a number: 100
Enter a number: 15
Enter a number: 62
Enter a number: 25
Difference: -2
Numbers Entered: 4
Hint: If you get an EOF error while running the code
you've written, this error likely means you're asking for
too many inputs from the user.
Answers
I've included my code in the picture below. Best of luck.
