15. What are programming languages used for other than to build application software, systems software, embedded systems, and Web sites?
Answers
Answer:
Well you have python (AI), SQL, C++, and probably Java.
Application software is widely used in business to complete specific tasks. These programs are designed for the users by the application developers. An example of Applications software is Microsoft Offices (Word, Excel, PowerPoint).
Which software controls the interaction between the user and the hardware?The function of the Operating system (OS) is that it is a kind of a software that helps to controls as well as handle and coordinates the computer hardware devices and it also function by helping to runs other software as well as applications on a computer.
The system software controls the interactions between hardware and user applications. Application Programming Interface (API) is a set of commands, functions, protocols, and objects that programmers can use to create software or interact with an external system. It provides developers with standard commands for performing common operations so they do not have to write the code from scratch.
Therefore, Application software is widely used in business to complete specific tasks. These programs are designed for the users by the application developers. An example of Applications software is Microsoft Offices
Learn more about Application software on:
https://brainly.com/question/29353277
#SPJ2
Related Questions
1. Give the binary equivalents for the numbers 15, 24, 102?
Answers
Answer:1111,15<11000,24>1100110,102
Explanation:
which of the following cannot be copyrighted? a. books b. inventions c. videos d. music
Answers
Inventions cannot be copyrighted.
The correct answer is B.
Given, copyrighted items.
Copyright protects original works of authorship, such as books, videos, and music. It gives the creator exclusive rights to reproduce, distribute, and display their work. However, inventions are protected by patents, not copyrights.
a. Books can be copyrighted.
c. Videos can be copyrighted.
d. Music can be copyrighted.
b. Inventions cannot be copyrighted; they are protected by patents.
Therefore the correct option is B .
Know more about copyright,
https://brainly.com/question/14704862
#SPJ6
Write a program that prompts the user for the name of two files each containing a single line that represents a decimal integercall them m and n, keep in mind that theseintegerscould be very largein absolute value, so they might not be stored neither as along nor intvariables. You should:a)Handle erroneous input graciously.b)Include a class named BigIntegerwhere you define an integer as a linked list, along with integer operations such as addition and subtraction [multiplication and division will grant you extra points] c)Test your program for each operation and store the result of each operation as a single decimal number in a separate file containing only one line\
Answers
Answer:
The output is seen bellow
Explanation:
public class BigInteger {
public class Node{
private char data;
private Node next;
public Node(char d){
this.setData(d);
this.setNext(null);
}
public char getData() {
return data;
}
public void setData(char data) {
this.data = data;
}
public Node getNext() {
return next;
}
public void setNext(Node next) {
this.next = next;
}
}
private Node root;
public BigInteger(String s){
this.root=null;
for(int i=s.length()-1;i>=0;i--){
Node node=new Node(s.charAt(i));
node.setNext(root);
root=node;
}
}
public String toString(){
String str="";
Node cur=this.root;
int i=0;
while(cur!=null){
if(i==0 && cur.getData()=='0'){
}
else{
i=1;
str+=cur.getData();
}
cur=cur.getNext();
}
return str;
}
public String reverse(String s){
String ret="";
for(int i=s.length()-1;i>=0;i--){
ret+=s.charAt(i);
}
return ret;
}
public BigInteger add(BigInteger s){
String f=this.reverse(this.toString());
String l=this.reverse(s.toString());
int max=(f.length()>l.length())?f.length():l.length();
String ret="";
int carry=0;
for(int i=0;i<max;i++){
int sum=carry;
if(i<f.length()){
sum+=(f.charAt(i)-'0');
}
if(i<l.length()){
sum+=(l.charAt(i)-'0');
}
ret+=(char)(sum%10+'0');
carry=(sum/10);
}
if(carry!=0){
ret+='1';
}
BigInteger bi=new BigInteger(this.reverse(ret));
return bi;
}
public boolean bigNum(String s1,String s2){
if(s1.length()>s2.length()){
return true;
}
else{
if(s1.length()<s2.length()){
return false;
}
else{
for(int i=0;i<s1.length();i++){
if(s1.charAt(i)!=s2.charAt(i)){
if(s1.charAt(i)>s2.charAt(i)){
return true;
}
else{
return false;
}
}
}
}
}
return false;
}
public BigInteger subtraction(BigInteger s){
String f=this.toString();
String l=s.toString();
boolean b=this.bigNum(f, l);
if(b==false){
String tmp=f;
f=l;
l=tmp;
}
f=this.reverse(f);
l=this.reverse(l);
int max=(f.length()>l.length())?f.length():l.length();
String ret="";
int borrow=0;
for(int i=0;i<max;i++){
int sum=borrow;
if(i<f.length()){
sum+=(f.charAt(i)-'0');
}
if(i<l.length()){
sum-=(l.charAt(i)-'0');
}
if(sum<0){borrow=-1;sum=10+sum;}
else{borrow=0;}
ret+=(char)(sum%10+'0');
}
if(b==false){
ret+="-";
}
BigInteger bi=new BigInteger(this.reverse(ret));
return bi;
}
public BigInteger multiplication(BigInteger s){
String f=this.toString();
String l=s.toString();
int len=l.length();
BigInteger bi=new BigInteger("");
for(int i=len-1;i>=0;i--){
//System.out.println(l.charAt(i));
BigInteger r=new BigInteger(f);
for(int j=(l.charAt(i)-'0');j>1;j--){
r=r.add(new BigInteger(f));
//System.out.print(r+" " );
}
//System.out.println();
bi=bi.add(r);
f=f+"0";
}
return bi;
}
public BigInteger division(BigInteger s){
BigInteger t=this;
BigInteger bi=new BigInteger("");
int i=0;
t=t.subtraction(s);
String str=t.toString();
while(str.charAt(0)!='-' && i<40){
//System.out.println(str+" "+(i+1));
bi=bi.add(new BigInteger("1"));
t=t.subtraction(s);
str=t.toString();
i++;
}
return bi;
}
}
-------------------
import java.io.BufferedReader;
import java.io.FileNotFoundException;
import java.io.FileReader;
import java.io.FileWriter;
import java.io.IOException;
import java.io.PrintWriter;
import java.util.Scanner;
public class Driver {
public static void main(String [] args){
Scanner sc=new Scanner(System.in);
String str1="";
String str2="";
System.out.print("Enter file name 1 :");
String file1=sc.next();
//String file1="datafile1.txt";
BufferedReader reader1;
try {
reader1 = new BufferedReader(new FileReader(file1));
while((str1=reader1.readLine())!=null){
break;
}
reader1.close();
} catch (FileNotFoundException e) {
// TODO Auto-generated catch block
e.printStackTrace();
} catch (IOException e) {
// TODO Auto-generated catch block
e.printStackTrace();
}
System.out.print("Enter file name 2 :");
String file2=sc.next();
//String file2="datafile2.txt";
BufferedReader reader2;
try {
reader2 = new BufferedReader(new FileReader(file2));
while((str2=reader2.readLine())!=null){
break;
}
reader2.close();
} catch (FileNotFoundException e) {
// TODO Auto-generated catch block
e.printStackTrace();
} catch (IOException e) {
// TODO Auto-generated catch block
e.printStackTrace();
}
Happy Thanksgiving!!!!

Answers
Yoo, you too, bro!
Have a nice time with your family
Question 4
Fill in the blank to complete the “increments” function. This function should use a list comprehension to create a list of numbers incremented by 2 (n+2). The function receives two variables and should return a list of incremented consecutive numbers between “start” and “end” inclusively (meaning the range should include both the “start” and “end” values). Complete the list comprehension in this function so that input like “squares(2, 3)” will produce the output “[4, 5]”.
Answers
The increment function will be written thus:
ef increments(start, end):
return [num + 2 for num in range(start, end + 1)]
print(increments(2, 3)) # Should print [4, 5]
print(increments(1, 5)) # Should print [3, 4, 5, 6, 7]
print(increments(0, 10)) # Should print [2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12]
How to explain the functionThe increments function takes two arguments, start and end, which represent the inclusive range of numbers to be incremented.
The goal is to create a list of numbers incremented by 2 (n+2) using a list comprehension.
Learn more about functions on
https://brainly.com/question/10439235
#SPJ1
given a list of distinct integers from 0 to a value max value, write a function to produce a string that describes the ranges of numbers missing from the list. the items in the result should be sorted in ascending order and separated by commas. when a gap spans only one number, the item is the number itself; when a gap is longer, the item comprises the start and the end of the gap, joined with a minus sign.
Answers
Essentially, it is a variant of Insertion Sort. In insertion sort, we only shift items one place forward. Many moves are required when an element must be pushed far ahead.
The goal of Shell Sort is to enable the interchange of distant goods. For a big value of h, we use Shell sort to sort the array. We keep decreasing the value of h until it equals one. If all sub lists of every hitch element are sorted, an array is said to be h-sorted.
SHELL SORT IS A PROCEDURE (ARRAY, N)
WHILE GAP LENGTH(ARRAY) /3: GAP = (INTERVAL * 3) + 1 END WHILE LOOP WHILE GAP > 0: FOR (OUTER = GAP; OUTER LENGTH(ARRAY); OUTER++): INSERTION VALUE = ARRAY[OUTER] INNER = OUTER; WHILE INNER > GAP-1 AND ARRAY[INNER - GAP]
ARRAY[INNER] = ARRAY[INNER - GAP] = INSERTION VALUE
INNER - GAP END = INNER WHILE LOOP
ARRAY[INNER] = INSERTION VALUE END FOR LOOP GAP = (GAP -1) /3; END FOR LOOP GAP = (GAP -1) /3; END
FOR LOOP GAP = (G SHELL SORT WHILE LOOP END
Learn more about ARRAY from here;
https://brainly.com/question/19570024
#SPJ4
How does a computer work?
Answers
Answer:
A computer is a Device that can run multiple applications at a time and access the internet where you can find online stores and more also used to make video calls and more.
During the projects for this course, you have demonstrated to the Tetra Shillings accounting firm how to use Microsoft Intune to deploy and manage Windows 10 devices. Like most other organizations Tetra Shillings is forced to make remote working accommodations for employees working remotely due to the COVID 19 pandemic. This has forced the company to adopt a bring your own device policy (BYOD) that allows employees to use their own personal phones and devices to access privileged company information and applications. The CIO is now concerned about the security risks that this policy may pose to the company.
The CIO of Tetra Shillings has provided the following information about the current BYOD environment:
Devices include phones, laptops, tablets, and PCs.
Operating systems: iOS, Windows, Android
Based what you have learned about Microsoft Intune discuss how you would use Intune to manage and secure these devices. Your answer should include the following items:
Device enrollment options
Compliance Policy
Endpoint Security
Application Management
Answers
I would utilise Intune to enrol devices, enforce compliance regulations, secure endpoints, and manage applications to manage and secure BYOD.
Which version of Windows 10 is more user-friendly and intended primarily for users at home and in small offices?The foundation package created for the average user who primarily uses Windows at home is called Windows 10 Home. It is the standard edition of the operating system. This edition includes all the essential tools geared towards the general consumer market, including Cortana, Outlook, OneNote, and Microsoft Edge.
Is there employee monitoring in Microsoft Teams?Microsoft Teams helps firms keep track of their employees. You can keep tabs on nearly anything your staff members do with Teams, including text conversations, recorded calls, zoom meetings, and other capabilities.
To know more about BYOD visit:
https://brainly.com/question/20343970
#SPJ1
Which of the following statements are applicable to Random Access Memory (RAM)?
Select the two answers that apply.
A: this memory can only be read from not written to
B: this memory is volatile and is erased when the computer is restarted or shut down
C: this memory is used to store the data the user is currently working on or accessing
D: this memory is used to store the startup instructions of a computer
Answers
The two statements that are applicable to Random Access Memory (RAM) are:
B: This memory is volatile and is erased when the computer is restarted or shut downC: This memory is used to store the data the user is currently working on or accessing.Why are these correct?A: This statement is incorrect. RAM is a type of memory that allows both read and write operations. It is used by the computer to temporarily store data and instructions that are currently being used by the CPU.
B: This statement is correct. RAM is a volatile type of memory, which means that its contents are erased when the computer is restarted or shut down. This is in contrast to non-volatile memory, such as hard disk drives, which can retain data even when the power is turned off.
Read more about RAM here:
https://brainly.com/question/28483224
#SPJ1
In Java only please:
4.15 LAB: Mad Lib - loops
Mad Libs are activities that have a person provide various words, which are then used to complete a short story in unexpected (and hopefully funny) ways.
Write a program that takes a string and an integer as input, and outputs a sentence using the input values as shown in the example below. The program repeats until the input string is quit and disregards the integer input that follows.
Ex: If the input is:
apples 5
shoes 2
quit 0
the output is:
Eating 5 apples a day keeps you happy and healthy.
Eating 2 shoes a day keeps you happy and healthy
Answers
Answer:
Explanation:
import java.util.Scanner;
public class MadLibs {
public static void main(String[] args) {
Scanner input = new Scanner(System.in);
String word;
int number;
do {
System.out.print("Enter a word: ");
word = input.next();
if (word.equals("quit")) {
break;
}
System.out.print("Enter a number: ");
number = input.nextInt();
System.out.println("Eating " + number + " " + word + " a day keeps you happy and healthy.");
} while (true);
System.out.println("Goodbye!");
}
}
In this program, we use a do-while loop to repeatedly ask the user for a word and a number. The loop continues until the user enters the word "quit". Inside the loop, we read the input values using Scanner and then output the sentence using the input values.
Make sure to save the program with the filename "MadLibs.java" and compile and run it using a Java compiler or IDE.
Scrabble is a word game in which words are constructed from letter tiles, each letter tile containing a point value. The value of a word is the sum of each tile's points added to any points provided by the word's placement on the game board. Write a program using the given dictionary of letters and point values that takes a word as input and outputs the base total value of the word (before being put onto a board). Ex: If the input is: PYTHON the output is: 14
Answers
Complete question:
Scrabble is a word game in which words are constructed from letter tiles, each letter tile containing a point value. The value of a word is the sum of each tile's points added to any points provided by the word's placement on the game board. Write a program using the given dictionary of letters and point values that takes a word as input and outputs the base total value of the word (before being put onto a board). Ex: If the input is: PYTHON
the output is: 14
part of the code:
tile_dict = { 'A': 1, 'B': 3, 'C': 3, 'D': 2, 'E': 1, 'F': 4, 'G': 2, 'H': 4, 'I': 1, 'J': 8, 'K': 5, 'L': 1, 'M': 3, 'N': 1, 'O': 1, 'P': 3, 'Q': 10, 'R': 1, 'S': 1, 'T': 1, 'U': 1, 'V': 4, 'W': 4, 'X': 8, 'Y': 4, 'Z': 10 }
Answer:
Complete the program as thus:
word = input("Word: ").upper()
points = 0
for i in range(len(word)):
for key, value in tile_dict.items():
if key == word[i]:
points+=value
break
print("Points: "+str(points))
Explanation:
This gets input from the user in capital letters
word = input("Word: ").upper()
This initializes the number of points to 0
points = 0
This iterates through the letters of the input word
for i in range(len(word)):
For every letter, this iterates through the dictionary
for key, value in tile_dict.items():
This locates each letters
if key == word[i]:
This adds the point
points+=value
The inner loop is exited
break
This prints the total points
print("Points: "+str(points))
Answer:
Here is the exact code, especially if you want it as Zybooks requires
Explanation:
word = input("").upper()
points = 0
for i in range(len(word)):
for key, value in tile_dict.items():
if key == word[i]:
points+=value
break
print(""+str(points))
For each of these conditions— deadlock, race, and starvation—give at leasttwo “real life” examples (not related to a computer system environment) ofeach of these concepts. Then give your own opinion on how each of these sixconditions can be resolved.
Answers
Answer:
Explanation:
Deadlock:
Two cars are approaching an intersection from different directions, both needing to turn left but the traffic is too heavy, and neither can proceed until the other does.
Two friends borrow each other's books and refuse to return them until the other returns their book first.
To resolve deadlock, techniques such as detecting deadlock and breaking the circular wait by releasing resources can be used. For example, in the case of the intersection, a traffic management system can detect the deadlock and break the deadlock by directing one car to move first.
Race:
Two kids are competing to finish their homework first and get a reward.
Several runners in a marathon race are competing to reach the finish line first.
To resolve race conditions, techniques such as locking mechanisms, synchronization, and mutual exclusion can be used. For example, in the case of the homework, the teacher can use a timer to ensure that both kids finish their homework at the same time.
Starvation:
A busy restaurant has a limited number of tables, and some customers may have to wait for a long time to get a table.
In a large company, some employees may never get a promotion or a pay raise despite their hard work and dedication.
To resolve starvation, techniques such as fair scheduling, prioritization, and resource allocation can be used. For example, in the case of the restaurant, a reservation system can be implemented to ensure that customers are served in an orderly and timely manner.
In general, resolving these conditions requires careful planning, design, and implementation of systems and processes to ensure fairness, efficiency, and effectiveness. It is important to identify and address these conditions early on to avoid negative impacts on productivity, customer satisfaction, and organizational success.
why should technology be used?
Answers
Answer: Okay
Explanation:
Technology is important because it makes you feel more secure with every area in life for both personal and business reasons. With technology advancing more people are able to have access to supplies such as fresh water and food because technology can help deliver those items to people that otherwise couldn't get it.
Which key(s) will launch the Spelling Checker dialog box? F8 F7 Ctrl+H F2
Answers
Answer:
F7
Explanation:
Mostly in MS Office products, although a lot of other products will mimic the same well known key sequences as a way of enticing you to their platform.
Answer:The answer to your question is F7
Explanation:
An articulated robot has a T-type wrist axis that can be rotated a total of 2 rotations (each rotation is a full 3600 ). It is desired to be able to position the wrist with a control resolution of 0.250 between adjacent addressable points. (a) Determine the number of bits required in the binary register for that axis in the robot's control memory. (b) Using this number of bits, what is the actual control resolution of the joint
Answers
Write a printAllBooks function to display the contents of your library. This function should:
Have two parameters in this order:
array books: array of Bookobjects.
int: number of books in the array (Note: this value might be less than the capacity of 50 books)
This function does notreturn anything
If the number of books is 0 or less than 0, print "No books are stored"
Otherwise, print "Here is a list of books" and then each book in a new line
Answers
Answer:
void printAllBooks(Book [] listOfBooks, int numberOfBooks){
bool flag = false;
if(numberOfBooks == 0){
cout<< "No books are stored";
} else{
cout<< "Here is a list of the books \n";
for (int i =0; i < numberOfBooks; ++i){
cout<< listOfBooks[i];
}
}
}
Explanation:
The void keyword in the "printAllBooks" function is used for a function that has no return statement. The function accepts two parameters, "listOfBooks" which is the array of book objects, and "numberOfBooks" which is the size of the array of objects. The function uses a for loop statement to print out the book in the array if the numberOfBooks variable is greater than zero.
Assignment
Write the algorithm for solving the
f problems
1. Perimeter of a rectangle
2 Average of five (5) numbers
Answers
B.Add both lengths
C.Add both widths
D.sum up the value had on both length and width
1.ShoppingBay is an online auction service that requires several reports. Data for each auctioned
item includes an ID number, item description, length of auction in days, and minimum required bid.
Design a flowchart or pseudocode for the following:
-a. A program that accepts data for one auctioned item. Display data for an auction only if the
minimum required bid is more than $250.00
Answers
The pseudocode for the program: Announce factors for the unloaded thing information, counting:
auction_id (numbers)
item_description (string)
auction_length (numbers)
minimum_bid (drift)
Incite the client to enter the auction_id, item_description, auction_length, and minimum_bid.
What is the pseudocode?The program acknowledges information for one sold thing, counting the auction_id, item_description, auction_length, and minimum_bid. It at that point checks in case the minimum_bid for the unloaded thing is more prominent than or rise to to $250.00.
The pseudocode for the program pronounces factors for the sold thing information and prompts the client to enter the information. At that point it employments an in the event that articulation to check in case the minimum_bid is more noteworthy than or break even with to 250.00.
Learn more about pseudocode from
https://brainly.com/question/24953880
#SPJ1

You join Mountain Water Co – an expanding bottled water company as an information security officer. The company wants to do a lot of advertising of its bottled water products through its website. The CEO asks you to review the company website and report if it is secure. After talking to the webmaster you find out the following:
The Web server accepts all connections
No authentication is required
Self-registration is allowed
The web server is connected to the Internet
Is the situation secure? Select all that apply.
a.
Yes. There is no threat to a bottled water company so it is secure.
b.
There is insufficient information available to answer this question.
c.
No. Anything that is connected to the Internet is insecure.
d.
No. The system is allowing everyone to register. Only individuals who are associated with the company should be able to register.
e.
No. If there is no authentication, then anyone with access to the website online can access it. For good security only individuals with certain authorized roles should access a website.
Answers
In regards to the above case, My response is c. No. Anything that is connected to the Internet is insecure.
What is meant by computer security?Computer security is known to be a term that can be called cybersecurity. This is seen as a form of protection of computer systems as well as information from any kind of harm, theft, as well as any form of unauthorized use.
Note that Computer hardware is seen to be protected by the same ways or methods that one uses to protect other valuable things.
In the above, there is no method of authentication and as such, In regards to the above case, My response is c. No. Anything that is connected to the Internet is insecure.
Learn more about Computer security from
https://brainly.com/question/25720881
#SPJ1
At which stage should Joan discuss the look and feel of her website with her website designer?
At the
stage, Joan should discuss the look and feel of her website with her website designer.

Answers
Answer:
Development stage: It is great to talk with the website designer during the development stages to understand the goalsAnswer:
At the planning stage maybe?
Explanation:
I'm not positive but in plato it discusses this in the Website Development Proccess lesson.
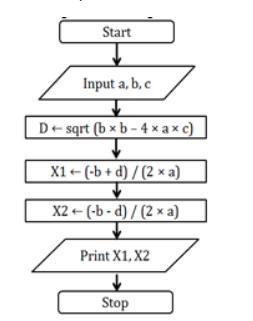
1 Design a flowchart to compute the following selection
(1) Area of a circle
(2) Simple interest
(3) Quadratic roots an
(4) Welcome to INTRODUCTION TO COMPUTER PROGRAMM INSTRUCTION
Answers
A flowchart exists as a graphic illustration of a function. It's a chart that displays the workflow needed to achieve a task or a set of tasks with the help of characters, lines, and shapes.
What is a flowchart?A flowchart exists as a graphic illustration of a function. It's a chart that displays the workflow needed to achieve a task or a set of tasks with the help of characters, lines, and shapes. Flowcharts exist utilized to learn, enhance and communicate strategies in different fields.
Step Form Algorithm:
Start.
Declare the required variables.
Indicate the user to enter the coefficients of the quadratic equation by displaying suitable sentences using the printf() function.
Wait using the scanf() function for the user to enter the input.
Calculate the roots of the quadratic equation using the proper formulae.
Display the result.
Wait for the user to press a key using the getch() function.
Stop.989
Pseudo Code Algorithm:
Start.
Input a, b, c.
D ← sqrt (b × b – 4 × a × c).
X1 ← (-b + d) / (2 × a).
X2 ← (-b - d) / (2 × a).
Print x1, x2.
Stop.
Flowchart:
A flowchart to calculate the roots of a quadratic equation exists shown below:
import math
days_driven = int(input("Days driven: "))
while True:
code = input("Choose B for class B, C for class C,D for class D, or Q to Quit: ")
# for class D
if code[0].lower() == "d":
print("You chose Class D")
if days_driven >=8 and days_driven <=27:
amount_due = 276 + (43* (days_driven - 7))
elif days_driven >=28 and days_driven <=60:
amount_due = 1136 + (38*(days_driven - 28))
else:
print("Class D cannot be rented for less than 7 days")
print('amount due is $', amount_due)
break
elif code[0].lower() == "c":
print("You chose class C")
if days_driven \gt= 1 and days_driven\lt=6:
amount_due = 34 * days_driven
elif days_driven \gt= 7 and days_driven \lt=27:
amount_due = 204 + ((days_driven-7)*31)
elif days_driven \gt=28 and days_driven \lt= 60:
amount_due = 810 + ((days_driven-28)*28)
print('amount due is $', amount_due)
# for class b
elif code[0].lower() == "b":
print("You chose class B")
if days_driven >1 and days_driven<=6:
amount_due = 27 * days_driven
elif days_driven >= 7 and days_driven <=27:
amount_due = 162 + ((days_driven-7)*25)
elif days_driven >=28 and days_driven <= 60:
amount_due = 662 + ((days_driven-28)*23)
print('amount due is $', amount_due)
break
elif code[0].lower() == "q":
print("You chose Quit!")
break
else:
print("You must choose between b,c,d, and q")
continue
To learn more about computer programs refer to:
https://brainly.com/question/21612382
#SPJ9
Which example best demonstrates an impact computing has had on the arts?
OA. A student bullies another student on social media by posting
embarrassing pictures.
OB. A group of friends who have never met each other in person play
an online game together.
OC. A music producer searches for samples of Caribbean percussion
instruments to add to a song.
OD. A teacher uses a computer-scored test to grade assignments
more quickly.
Answers
Answer:
the answer is C because music is art
Please help. Which ones would it be?
Answers
There are a number of roles held by various users of online digital media, including contributors, conversationalists,
critics, organizers, spectators, and joiners. Often, people who have a strong presence online will hold two or more roles.
Describe at least three of these roles. Of the roles you described, why might someone act on two of them at the same
time? That is, what kind of online activity would result in a person taking on those two roles?
Answers
Answer:
The mass media is a huge phenomenon. Through the various different platforms, print or broadcast, the media is able to reach millions of people like no other force. Without the media, powerful speeches by politicians would affect no one, local events would remain local, and performances by great actors would be seen only by the people in the immediate audience. The media overcomes distances, and builds a direct relationship with the audience. Many sociologist
I hope she/he helps !
Explanation:
Dance dance1 = new Dance("Tango","Hernandos Hideaway");
Dance dance2 = new Dance("Swing","Hound Dog");
System.out.println(dance1.toString());
System.out.println(dance2.toString());
class Dance
{
private String name;
private String song;
public Dance(String name, String s)
{
this.name = name;
song = s;
}
public String toString()
{
return name + " " + song;
}
}
What is printed when the program is executed?
a
null null
null null
b
Hernandos Hideaway null
Hound Dog null
c
null null
Swing Hound Dog
d
Tango Hernados Hideaway
Swing Hound Dog
e
null Hernandos Hideaway
null Hound Dog
Answers
Answer:
The output of the program is (d)
Tango Hernados Hideaway
Swing Hound Dog
Explanation:
Analyzing the given code segment
In class Dance,
A method named dance was defined with an instance of two string variables/values
which are name and song
public Dance(String name, String s)
In the main of the program,
The first line creates an instance of Dance as dance1
dance1 is initialized with the following string values: "Tango","Hernandos Hideaway"
- The first string value "Tango" will be passed into the name variable of the Dance method
- The second string value "Hernandos Hideaway" will be passed into the song variable of the Dance method
Next, another instance of Dance is initialized as dance2
dance2 is initialized with the following string values: "Swing","Hound Dog"
- The first string value "Swing" will be passed into the name variable of the Dance method
- The second string value "Hound Dog" will be passed into the song variable of the Dance method
On line 3 of the main: System.out.println(dance1.toString());
The values of dance1, which are "Tango","Hernandos Hideaway" are printed
On line 4 of the main: System.out.println(dance2.toString());
The values of dance1, which are "Swing","Hound Dog" are printed
Hence, option d answers the question
Use the drop-down menus to complete statements about how to use the database documenter
options for 2: Home crate external data database tools
options for 3: reports analyze relationships documentation
options for 5: end finish ok run

Answers
To use the database documenter, follow these steps -
2: Select "Database Tools" from the dropdown menu.3: Choose "Analyze" from the dropdown menu.5: Click on "OK" to run the documenter and generate the desired reports and documentation.How is this so?This is the suggested sequence of steps to use the database documenter based on the given options.
By selecting "Database Tools" (2), choosing "Analyze" (3), and clicking on "OK" (5), you can initiate the documenter and generate the desired reports and documentation. Following these steps will help you utilize the database documenter effectively and efficiently.
Learn more about database documenter at:
https://brainly.com/question/31450253
#SPJ1
Click or tap on any word or words that should not be followed by a comma. If the sentence doesn't contain any errors, click the "No Errors" button.
It is a requirement at many colleges that, instructors administer their own end-of-semester reviews, yet, many students also post instructor reviews anonymously online.
Answers
Any word or words that don't belong after a comma should be clicked or touched. Click "No Mistakes" button if sentence is error-free. however, (should not be followed by a comma) (should not be followed by a comma).
What do you mean by extra commas?A number of phrase structures use extraneous commas, which is a common grammatical mistake. For instance, a comma never belongs between a subject and its verb. Constantly, unnecessary commas cause this: False: Jim's is the last doughnut. It's accurate: Jim's is the last donut.
Which example uses commas correctly?When any of the following seven coordinating conjunctions is used to unite independent clauses: and, but, for, or, nor, so, yet, use commas to separate them.
To know more about comma visit:-
https://brainly.com/question/29993310?
#SPJ1
HTML question please help

Answers
Answer:
background-color: (Color)
Explanation:
This is actually CSS coding, as you would code it like:
Body {
background-color: (Color)
}
Describe what test presentation and conclusion are necessary for specific tests in IT testing such as
-resource availability
-environment legislation and regulations (e.g. disposal of materials)
- work sign off and reporting
Answers
For specific tests in IT testing, the following elements are necessary.
What are the elements?1. Test Presentation - This involves presenting the resources required for the test, ensuring their availability and readiness.
2. Conclusion - After conducting the test, a conclusion is drawn based on the results obtained and whether the objectives of the test were met.
3. Resource Availability - This test focuses on assessing the availability and adequacy of resources required for the IT system or project.
4. Environment Legislation and Regulations - This test evaluates compliance with legal and regulatory requirements related to environmental concerns, such as proper disposal of materials.
5. Work Sign Off and Reporting - This includes obtaining formal approval or sign off on the completed work and preparing reports documenting the test outcomes and findings.
Learn more about IT testing at:
https://brainly.com/question/13262403
#SPJ1
A browser is a program that allow
A. users transfer messages and files through internet.
B. users search for relevant information on the WWW.
C. users to access and view web pages on the internet.
D. users exchange real-time messages or files with another online user
Answers
C. users to access and view web pages on the internet.