11) write a paragraph summarizing the advantages and disadvantages of internet media. do not simply list the points given in this lesson. discuss what you consider to be the most important benefits and weaknesses. then, explain whether or not the advantages outweigh the disadvantages. (counts as 10% of your lesson grade.)
Answers
In today's world, the Internet has become one of the most essential and influential tools in various areas of life. It's used for entertainment, communication, and business, among other things. Although there are many advantages to using the internet as a means of communication, there are also many drawbacks. This essay will go over the advantages and disadvantages of internet media, as well as the benefits and weaknesses that come with it.
Advantages of Internet Media: Internet media has several advantages that make it a preferred option in various industries. For starters, it provides access to a vast amount of data and information. The internet is a virtual library where you may obtain information on virtually any subject. Additionally, the internet has made it much simpler to communicate with people from all around the world. You can talk with anyone, anywhere, and at any time using email, social media, or instant messaging. Finally, the internet makes it much simpler to share data with others. People can now share documents, photographs, music, and video over the internet.
Disadvantages of Internet Media: As helpful as internet media may be, it also has its drawbacks. First and foremost, the internet can be harmful to your privacy and security. With all of the personal information we put online, we're at risk of having our identity stolen or other malicious activity happening. Second, the internet can be a source of misinformation. Anyone can put anything on the internet, making it difficult to know what's accurate and what isn't. Finally, the internet may be highly addictive. People may spend hours surfing the internet, unaware of how much time has passed.
Benefits and Weaknesses: While there are both advantages and disadvantages of internet media, I believe the benefits outweigh the weaknesses. The internet provides people with access to a wide range of information, which can be helpful for both personal and professional reasons. Additionally, the internet has enabled us to stay connected with people who are far away. This has been especially important during the pandemic when in-person interactions have been limited. The drawbacks of the internet, such as security concerns and the spread of misinformation, may be resolved by using it carefully and responsibly. Overall, the advantages of internet media outweigh the disadvantages, as long as people use it carefully and with caution.
#SPJ11
Related Questions
Takes a 3-letter String parameter. Returns true if the second and
third characters are “ix”
Python and using function
Answers
Answer:
def ix(s):
return s[1:3]=="ix"
Explanation:
Which of the below would provide information using data-collection technology?
Buying a new shirt on an e-commerce site
Visiting a local art museum
Attending your friend's baseball game
Taking photos for the school's yearbook
Answers
The following statement would provide the information by utilising data-collection technology: Buying a new shirt on an e-commerce site.
What is data collection?
The process of obtaining and analysing data on certain variables in an established system is known as data collection or data gathering. This procedure allows one to analyse outcomes and provide answers to pertinent queries. In all academic disciplines, including the physical and social sciences, the humanities, and business, data collecting is a necessary component of research. Although techniques differ depending on the profession, the importance of ensuring accurate and truthful collection does not change. All data gathering efforts should aim to gather high-caliber information that will enable analysis to result in the creation of arguments that are believable and convincing in response to the issues that have been addressed. When conducting a census, data collection and validation takes four processes, while sampling requires seven steps.
To learn more about data collection
https://brainly.com/question/25836560
#SPJ13
What is an IF statement used for?
Answers
The IF statement is a decision-making statement that guides a program to make decisions based on specified criteria. The IF statement executes one set of code if a specified condition is met (TRUE) or another set of code evaluates to FALSE.
Select the correct answer.
Which statement is true with respect to Java?
Answers
Answer:
where are the options ..... to select
random access memory (ram) access choices include:
Answers
Random access memory (RAM) access choices include sequential access, direct access, and random access. Random access provides the fastest access time compared to sequential and direct access methods.
random access memory (RAM) is a type of computer memory that allows data to be read or written in almost the same amount of time regardless of the physical location of the data inside the memory. RAM access choices refer to the different methods or techniques used to access data stored in RAM.
There are three common RAM access choices:
sequential access: This method involves accessing data in a sequential manner, where each data item is accessed one after the other. It is similar to reading a book from start to finish, where you have to go through each page before reaching the desired page.direct access: This method allows direct access to any data item in RAM, without the need to access the preceding data items. It is like using an index to quickly find a specific page in a book without having to read through the entire book.Random Access: This method allows direct access to any data item in RAM, similar to direct access, but without the need to access the preceding data items. It provides the fastest access time compared to sequential and direct access methods. It is like using a bookmark to quickly jump to a specific page in a book.Random access provides the fastest access time because it does not require accessing the preceding data items. This makes it efficient for retrieving and modifying data stored in RAM.
Learn more:About random access memory here:
https://brainly.com/question/32889752
#SPJ11
The choices for accessing Random Access Memory (RAM) include read and write operations.
RAM is a type of computer memory that provides fast and temporary storage for data that the computer's processor needs to access quickly. Accessing RAM involves performing read operations, which retrieve data from RAM for the processor to use, and write operations, which store data in RAM for temporary storage. These access choices allow the processor to interact with RAM effectively, facilitating the execution of programs and the manipulation of data in real-time. The speed and efficiency of RAM access significantly impact the overall performance of a computer system.
To know more about Random Access Memory (RAM) click here,
https://brainly.com/question/32142380
#SPJ11
Geraldo would like to compare two areas of text, Text1 and Text2, to each other. What steps should he take?
od
select Text1, hit F1, click. "Compare to another selection," select Text2
select Text1, hold Shift+F1, click "Compare to another selection," select Text2
hold Shift+F1, select Text1, hold Shift+F1 again, select Text2
Ohit F1, select Text1, hit F1 again, select Text2
Answers
Scrum masters are effective by using scrum methods, supporting safe principles and practices and what else?
- Serving as a customer proxy
- Writing stories and enablers
- Managing architectural runway
- Delivering through agile practices
Answers
In addition to using Scrum methods and supporting safe principles, Scrum Masters can be effective by A. serving as a customer proxy.
Acting as a customer proxy means that the Scrum Master represents the interests of the customer or product owner within the Scrum team. They facilitate communication and collaboration between the team and the customer, ensuring that the team understands the customer's requirements, priorities, and feedback.
By serving as a customer proxy, the Scrum Master helps bridge the gap between the development team and the customer, facilitating a clear understanding of the product vision and ensuring that the team delivers value that aligns with the customer's needs.
They may participate in meetings with stakeholders, gather requirements, help prioritize the product backlog, and provide insights into the customer's perspective during sprint planning and other Scrum ceremonies.
Ultimately, the Scrum Master's role as a customer proxy helps to ensure that the team builds the right product, delivers customer value, and maintains a strong customer focus throughout the development process.
Learn more about Scrum masters: https://brainly.com/question/17205862
#SPJ11
PLEASE HELP
Write a method that takes two rectangles and returns the (positive) difference between their areas.
This method must be named areaDiff() and have 2 Rectangle parameters. This method must return a double.
For example suppose two Rectangle objects were initialized as shown:
Rectangle rect1 = new Rectangle(2.0, 8.0);
Rectangle rect2 = new Rectangle(6.0, 3.0);
The method call areaDiff(rect1, rect2) should then return the value 2.0.
Answers
The program to define a method that computes the positive difference between the areas of two rectangles is found in the attached image.
The program defines a class Rectangle with a constructor, and a static method areaDiff. The static method areaDiff takes two rectangles (rect1 and rect2) and returns the positive difference between their areas.
The formula used by areaDiff is:
\(|(rect1.width \times rect1.height)-(rect2.width \times rect2.height)|\)
where
\(rect1,rect2=\text{the two rectangles}\\(rect.width\times rect.height)\text{ calculates the area of a rectangle object}\\|x|=\text{the absolute value function}\)
Another Python program that solves a geometry problem can be found here: https://brainly.com/question/19150697

Describe each of the principal factors risk factors in
information systems projects (20 marks)
Answers
The principal risk factors in information systems projects encompass various aspects such as project complexity, technology challenges, organizational factors, and external influences.
These factors contribute to the potential risks and uncertainties associated with the successful implementation of information systems projects.
Project Complexity: Information systems projects can be inherently complex due to factors such as scope, scale, and the integration of multiple components. The complexity may arise from intricate business processes, diverse stakeholder requirements, or the need for extensive data management. Complex projects pose risks in terms of project management, resource allocation, and potential delays or cost overruns.
Technology Challenges: Information systems projects often involve implementing new technologies, software systems, or infrastructure. Technological risks include compatibility issues, scalability limitations, security vulnerabilities, and the need for specialized expertise. These challenges may impact the project timeline, functionality, and long-term viability of the system.
Organizational Factors: The success of an information systems project depends on organizational factors such as leadership, communication, and stakeholder engagement. Risks in this domain include lack of management support, insufficient user involvement, resistance to change, inadequate training, and poor project governance. Failure to address these factors can lead to user dissatisfaction, low adoption rates, and project failure.
External Influences: External factors, such as changes in regulatory requirements, market dynamics, or economic conditions, can introduce risks to information systems projects. These factors may necessitate modifications to project scope, increased compliance efforts, or adjustments to business strategies. Failure to anticipate and adapt to external influences can disrupt project timelines and impact the project's overall success.
Understanding and managing these principal risk factors is crucial for effective project planning, risk mitigation, and successful implementation of information systems projects. Proper risk assessment, contingency planning, stakeholder involvement, and ongoing monitoring are essential to minimize the impact of these risks and ensure project success.
Learn more about information systems here:
https://brainly.com/question/13081794
#SPJ11
In a Windows domain, where is the centralized database kept?
A. domain controller
B. DNS server
C. DHCP server
D. client/server network
Answers
In a Windows domain, the centralized database is kept on the domain controller.
A domain controller is a server that is responsible for authenticating users, managing security policies, and maintaining the centralized database known as the Active Directory. The Active Directory database stores information about users, groups, computers, and other network resources within the domain.
The domain controller plays a crucial role in a Windows domain environment by providing authentication services, enforcing security policies, and allowing centralized management of network resources.
Therefore, the correct answer is A. domain controller.
Learn more about Domain Controller here -: brainly.com/question/30665178
#SPJ11
What is the best CPU you can put inside a Dell Precision T3500?
And what would be the best graphics card you could put with this CPU?
Answers
Answer:
Whatever fits
Explanation:
If an intel i9 or a Ryzen 9 fits, use that. 3090's are very big, so try adding a 3060-3080.
Hope this helps!
the goal of what type of threat evaluation is to better understand who the attackers are, why they attack, and what types of attacks might occur?
Answers
The goal of threat modeling is a threat evaluation is to better understand who the attackers are, why they attack, and what types of attacks might occur. The correct option is d.
What is threat modeling?The aim of threat modeling, a structured approach, are to identify security needs, identify security threats and probable vulnerabilities, assess the criticality of those threats and vulnerabilities, and rank remedial options.
Agile threat modeling primarily entails two distinct workshop days with your architectural and development teams, either on-site or remotely.
Therefore, the correct option is d. threat modeling.
To learn more about threat modeling, refer to the link:
https://brainly.com/question/28178975
#SPJ1
The question is incomplete. Your most probably complete question is given below:
a. threat mitigation
b. threat profiling
c. risk modeling
d. threat modeling
What is meant by the "E-Book Moment"and how is it relevant to
understand and appreciate Fintech?
Answers
The "E-Book Moment" refers to a pivotal point in technological advancements when digital books (e-books) gained widespread acceptance and disrupted the traditional publishing industry.
Understanding and appreciating the "E-Book Moment" is relevant to grasp the significance of Fintech (financial technology) and its potential to revolutionize the financial industry through digital innovations and disrupt traditional financial services.
The "E-Book Moment" signifies a transformative shift in consumer behavior and industry dynamics. It highlights the moment when e-books became widely adopted, challenging the dominance of digital books and transforming the publishing landscape. This moment represented the convergence of technology, consumer preferences, and market forces, leading to a fundamental change in the way people read and purchase books.
Drawing a parallel to Fintech, the "E-Book Moment" serves as an analogy to understand the potential impact of digital technologies on the financial industry. Fintech encompasses various technological innovations, such as mobile banking, digital payments, blockchain, and robo-advisors, which are reshaping traditional financial services. Similar to the "E-Book Moment," Fintech represents a disruptive force that is changing how financial transactions are conducted, improving accessibility, efficiency, and customer experience.
By understanding the "E-Book Moment" and its implications, we can appreciate the transformative power of technology in reshaping industries. It highlights the need for traditional financial institutions to adapt and embrace digital innovations to stay relevant in the evolving landscape of Fintech.
To learn more about digital books visit:
brainly.com/question/28964144
#SPJ11
While ________is the protocol used to view web pages, browsers also support protocols for functions such as transferring large files.
10 points
a HTML
b HTTP
c FTP
Answers
you have an error in your sql syntax; check the manual that corresponds to your mysql server version for the right syntax to use near
Answers
A simple grocery list, a photo gallery, or the enormous volume of data on a business network might all be examples. You require a database management system like MySQL Server in order to add, access, and process data kept in a computer database.
What is the error in MySQL syntax?Depending on the most likely reason of the MySQL 1064 problem, there are five different approaches you can try: retype commands that were mistyped, replacing outdated commands, Include missing data, designate reserved words, In compatibility mode, move WordPress databases.
Any time there is a problem with your SQL syntax, such as employing reserved terms, missing data in the database, or incorrectly typed/outdated commands, you will see the 1064 error.
There are two primary reasons and fixes for the issue "MySQL server has disappeared": Due to server timeout, the connection was cut off. Check to see if the wait timeout mysql variable in your my.cnf configuration file is large enough to handle your workload, for example wait
timeout = 28800. By replacing the semicolon with a colon, you may fix this incorrect syntax in Python.
To learn more about MySQL refer to :
https://brainly.com/question/17005467
#SPJ4
pls answer fast in five mins

Answers
The answer is true!! I hope this helps!!
OPERATION SHEET 6.2.2 Given the Neccesary tools materials and equipment identify the common faults and errors of computer when you detached the following Keyboard-PS/2 Mouse-PS/2 Hard disk- IDE cable Floppy disk drive-IDE cable Room disk-IDE CABLE

Answers
Answer: NO MORE TYPING! NO MORE CLICKING! NO MORE MEMORY! NO MORE OPERATING!
. [3] prove the correctness of the following recursive algorithm to multiply two natural numbers, for all integer constants c ≥ 2.
Answers
The recursive algorithm for multiplying two natural numbers is correct for all integer constants c ≥ 2.
To prove the correctness of the recursive algorithm for multiplying two natural numbers, we need to demonstrate that it produces the correct result for all possible input values. The algorithm follows a divide-and-conquer approach by recursively dividing the input numbers into smaller subproblems. In each recursive call, the algorithm divides the input numbers into halves and recursively multiplies these smaller subproblems. It then combines the results of the subproblems to obtain the final product. The base case of the recursion is reached when the input numbers become small enough to directly compute the multiplication. To prove the correctness of this algorithm, we can use mathematical induction.
By assuming that the algorithm works correctly for smaller inputs, we can demonstrate that it also produces the correct result for larger inputs. This can be done by analyzing the recursive steps, ensuring that they preserve the multiplication property. By considering these factors and verifying that the algorithm satisfies the defined properties and requirements, we can conclude that the recursive algorithm for multiplying two natural numbers is correct for all integer constants c ≥ 2.
Learn more about recursive algorithm here:
https://brainly.com/question/13104472
#SPJ11
Union Health Center (UHC) has used many various IT tools and staff resources to develop their education and self-management strategies among patients with chronic disease. UHC's has a couple different electronic strategies to help their patient centered care team model. The first being patient registries. UHC uses patient registries to identify patients with specific conditions to ensure those patients receive the right care, in the right place, at the right time (Wager et al., 2022). They also used this to target cases for chart reviews and assess illness management strategies. The next tool is a custom EHR template to support PCAs which free up clinicians for more specialized tasks and complex patients (Wager et al., 2022). It is a very important aspect because it allows clinicians to keep track of the patient's health and provide the best treatment possible. Working with medical neighbors is essential to UHC as it will provide information to them for various of different backgrounds. UHC had a couple different challenges and lessons that they learned through this process. The first is recruiting staff members with IT and clinical informatics backgrounds (Wager et al., 2022). It is challenging for any organization, but UHC struggled to find the right mix of staff with IT and clinical informatic skills. If the individuals are hired without the proper expertise, it will through off the entire system. With any new system that is put into place UHC With any new system that is put into place UHC struggled to have consistent data entry that led to the inability to create reports. UHC also realized that the time data reached the team they many no longer be current. UHC is looking to purchase a program that would create a faster process with the information.
Answers
Union Health Center (UHC) employs a variety of IT tools and human resources to develop education and self-management strategies for chronic disease patients.
These strategies, including patient registries and custom EHR templates, facilitate patient-centered care. However, UHC faces challenges in recruiting skilled IT and clinical informatics staff and ensuring consistent data entry for up-to-date information.
In detail, UHC uses patient registries to identify and manage patients with specific conditions, ensuring they receive the right care at the right time. Their custom EHR template supports clinicians by freeing up their time for more specialized tasks. These IT tools are vital for comprehensive and effective patient care. However, UHC's challenges lie in the recruitment of staff with a blend of IT and clinical informatics skills and maintaining consistent data entry to generate reliable reports. Additionally, there's a need for real-time data to keep the teams updated. UHC is considering an investment in software that can expedite the information process, thus meeting these challenges.
Learn more about self-management here:
https://brainly.com/question/33723761
#SPJ11
In this lab, you will complete the implementation of a medical device vulnerability scoring web page. the purpose of this web page is to return a score that numerically quantifies how vulnerable a specific vulnerability is to the particular attack. the properties of the system will be selected from a group of predetermined options, where each option is a styled radio button. once options are selected for all possible properties, the web page will display the vulnerability score (and hide the warning label).
implement a function called updatescore. this function must verify that one button from each property is selected.
using javascript, add a click or change event listener to each radio button (do not add the event listener to the button label). notice that the radio buttons are hidden using css.
Answers
To complete the implementation of the medical device vulnerability scoring web page, you can follow these steps:-
1. Define the `updateScore` function in JavaScript:
```javascript
function updateScore() {
// Check that one button from each property is selected
// Calculate the vulnerability score based on the selected options
// Display the vulnerability score and hide the warning label
}
```
2. Add a click or change event listener to each radio button using JavaScript:
```javascript
// Select all radio buttons
const radioButtons = document.querySelectorAll('input[type="radio"]');
// Add event listeners to each radio button
radioButtons.forEach((button) => {
button.addEventListener('change', updateScore);
});
```
Make sure to adapt this code to your specific HTML structure and predetermined options. The `updateScore` function should be modified to handle the selected options and calculate the vulnerability score accordingly.
Learn more about web page here:
https://brainly.com/question/9060926
#SPJ11
If a user wants to change one small section of the formatting of a document and leave the rest the same, which
process should be completed?
• importing a style
• overriding a style a
• modifying a style
exporting a style
Answers
in response to the write command, the file manager sends a command to the remote server to unlock the specified file. True/False
Answers
Answer:
True
Explanation:
Write a script in HTML for displaying your name in brown color.
Answers
Answer:
I don't quite understand the question. If you mean "create page in HTML", see image 2. If you mean "create script that is placed in the HTML page", see image 1
HTML is not a programming language. It is a markup language. You should write scripts in JavaScript or other programming languages.
1<!DOCTYPE html>
<html>
<head>
<meta charset="utf-8">
</head>
<body>
<h1>Hello world!</h1>
<*cript>
function paint() {
document.querySelector("h1").style.color = "brown";
}
setTimeout(paint, 2000)
</*cript>
</body>
</html>
2<!DOCTYPE html>
<html>
<head>
<meta charset="utf-8">
<style>
h1 {
color: brown;
}
</style>
</head>
<body>
<h1>Hello world!</h1>
</body>
</html>


Are the copper tape and aluminum foil switches analog or digital devices? How do you know?
Answers
In a digital sensor, you may use a microbit or a switch analog of copper tape or aluminum foil.
What are digital sensor?Digital sensor are defined as a sensor that is electronic or electrochemical that uses digital data processing and data transmission. The contemporary replacements for analog sensors are digital sensors.
Switch analog are defined as a piece of technology that selectively allows or disallows signal levels to pass from the input to the output. A sine-wave signal, for example, can be conducted by an analog switch in either direction.
Thus, in a digital sensor, you may use a microbit or a switch analog of copper tape or aluminum foil.
To learn more about digital sensor, refer to the link below:
https://brainly.com/question/3979742
#SPJ1
Choose all items that represent features of the job application process.
Answers
Answer:we need some options or we can’t help you
Explanation:
Which expression can be used to find the surface area of the following square pyramid?
10

Answers
Answer:
100+40+40+40+40
Explanation:
hopes this help :)
what protocol is responsible for assigning internet protocol (ip) addresses to hosts on many networks?
Answers
The DHCP protocol is commonly used to assign IP addresses (Dynamic Host Configuration Protocol). An internet service provider can use DHCP to give a specific device a public IP address.
What is meant by DHCP protocol?The Dynamic Host Configuration Protocol (DHCP) is a client/server protocol that automatically assigns an Internet Protocol (IP) host with its IP address and other necessary configuration data, such as the subnet mask and default gateway. The Dynamic Host Configuration Protocol (DHCP) is a network protocol used to set up network devices for IP network communication. A DHCP client utilizes the DHCP protocol to obtain configuration data from a DHCP server, such as an IP address, a default route, and one or more DNS server addresses.Your PC's ability to communicate with other Computers is governed by TCP/IP. We advise using automatic Dynamic Host Configuration Protocol to make managing TCP/IP settings easier (DHCP).To learn more about DHCP protocol, refer to:
https://brainly.com/question/14234787
PLEASE HELP! THIS IS FROM A BEGINNERS COMPUTER SCIENCE CLASS:
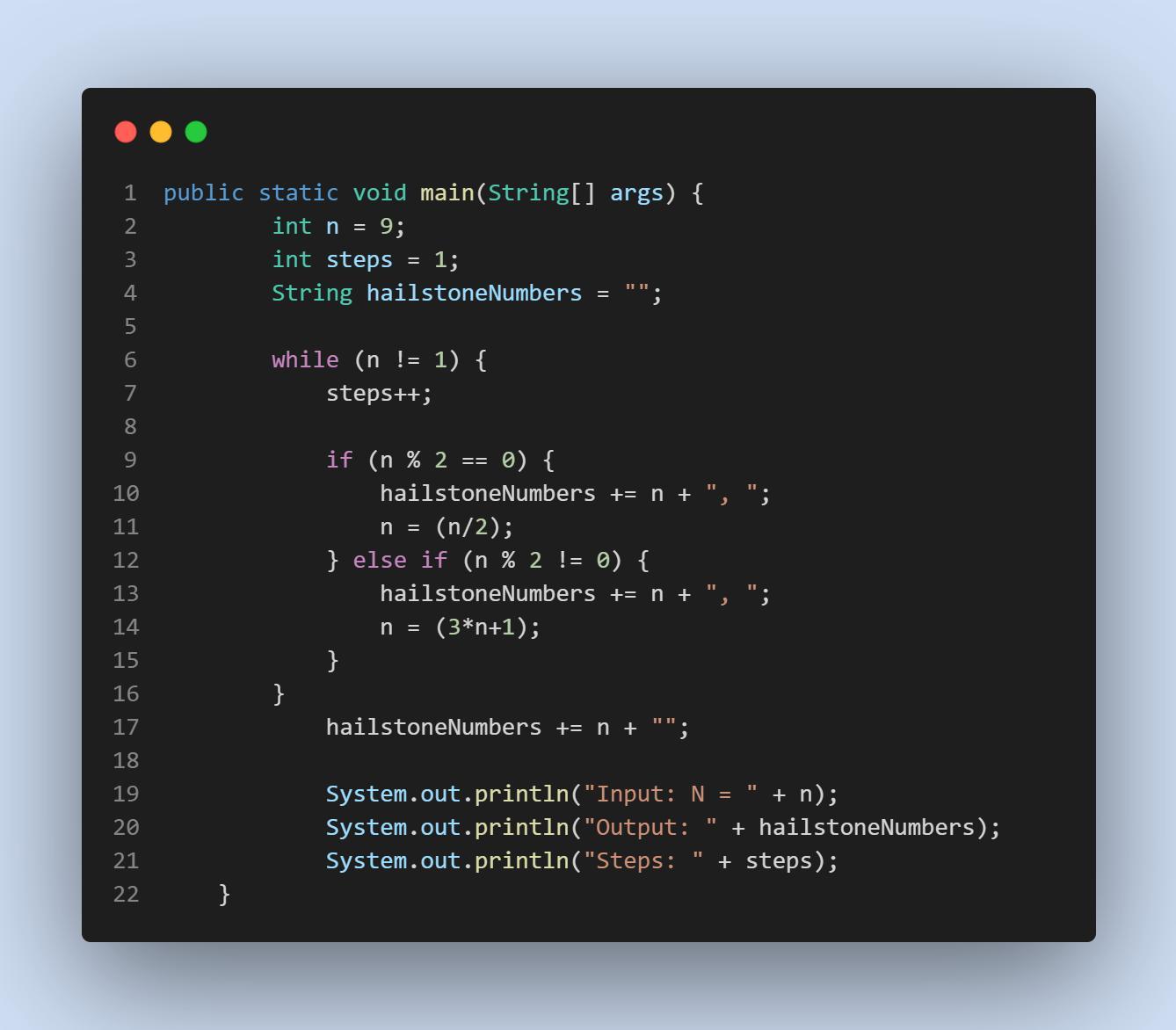
Write a program that generates the "Hailstone series" for any number from 1 to 1000. The Hailstone series is an interesting sequence of numbers, and can be calculated like this:
If the current value of n is even, the next number in the sequence will be n/2 (use integer division)
If the current value of n is odd, the next number in the sequence will be 3*n + 1
This process is repeated until you reach a value of 1. It is theorized that every integer will eventually end at 1. At the time of writing, this has been tested to be true for numbers up to ~1048, but it has never been proven!
Your program should print the Hailstone series for a particular number and the number of steps it took to reach 1.
Answers
Answer:
This is an iterative approach to the problem; you could also have done a recursive approach. This version is easier to think about in my opinion.
The most effective leaders treat everyone alike. True True False
Answers
Answer:
you have to have evidence they do that and on the question theirs no evidence so the answer would be false (as long as theirs no evidence)
Explanation:
Answer:
True
Explanation:
Assignment 6: Animation

Answers
Here is an example of an animated scene with a school-appropriate theme:
How to show the Programimport turtle
# Global variable to keep track of the score
score = 0
# Draw 5 circles
for i in range(5):
turtle.penup()
turtle.goto(i*30, 0)
turtle.pendown()
turtle.circle(20)
# Draw 5 polygons
for i in range(5):
turtle.penup()
turtle.goto(i*60, 50)
turtle.pendown()
for j in range(4):
turtle.forward(40)
turtle.right(90)
# Draw 5 lines
for i in range(5):
turtle.penup()
turtle.goto(i*90, -50)
turtle.pendown()
turtle.forward(100)
# Animate the scene
while True:
turtle.undo()
score += 1
turtle.write("Score: " + str(score), align="center",
font=("Arial", 14, "normal"))
This code creates an animated scene where five circles, five polygons, and five lines move across the screen, with the score increasing by 1 with each iteration of the while loop.
Read more about programs here:
brainly.com/question/26134656
#SPJ1