1. In Cybersecurity, the two important goals are confidentiality and message integrity. The former is the protection of data from unwanted disclosures, while the latter is the transmission of data without being altered in transit.
A. Give an example when Confidentiality is protected but Integrity is not, and vice versa.
Answers
Confidentiality and message integrity are two essential goals in cybersecurity. Confidentiality ensures data protection from unauthorized disclosure, while message integrity ensures data is transmitted without being altered. Examples can be provided where one goal is protected while the other is compromised.
A. An example where confidentiality is protected but integrity is not can be seen in a scenario where sensitive information is encrypted and securely transmitted between two parties. The encryption ensures that the content of the message remains confidential and cannot be accessed by unauthorized individuals. However, if the message is intercepted by an attacker during transmission and they tamper with the encrypted data, the integrity of the message is compromised. The recipient may receive the message thinking it is unchanged, but in reality, the content has been altered by the attacker. This situation highlights the importance of not only protecting confidentiality through encryption but also ensuring the integrity of the message through measures such as digital signatures or message authentication codes.
On the other hand, an example where integrity is protected but confidentiality is not can occur in situations where data integrity checks are in place to detect any unauthorized modifications during transmission. While the data's integrity is verified, the content itself may not be encrypted or protected from unauthorized access. This means that even if the data remains unchanged during transmission, it can be accessed and disclosed by unauthorized individuals, compromising its confidentiality. This emphasizes the need to implement measures such as encryption or access controls to protect the confidentiality of sensitive information, in addition to ensuring message integrity.
Learn more about encryption here:
https://brainly.com/question/30225557
#SPJ11
Related Questions
write a web application that allows the customer to enter the letter of the plan the customer has purchased (a, a, b, b, or c, c) and the number of minutes that were used in a month, validates user input, calculates and displays the monthly charge in the browser. it also displays the amount of money the customer would save if a different plan could be chosen.
Answers
Web application in python to calculate the monthly charge according to the plan selected by the client. Flask is used as a development framework. An image of the code and output of the algorithm is attached.
Python codefrom flask import Flask
from flask import request, escape
app = Flask(__name__)
app. route("/")
def index():
val = request. args. get("val", "")
num = request. args. get("num", "")
return (
"""<p>**Calculates the monthly charge, and the amount of money the customer would save if a different plan could be chosen**"</p>"""
"""<form>Package A: ($9.95/month and 10 hours of access)<br/>
Package B: ($13.95/month and 20 hours of access)<br/>Package C: ($19.95/month and unlimited access)<br/>
</form>"""
"""<form action="" method="get">
Enter the letter of the plan the customer has purchased: <input type="text" name="val"><br/>
Enter the number of hours that were used: <input type="number" name="num"><br/>
<input type="submit" value="Calculate">
</form>"""
+ "Monthly charge: "
+ calculate(val, num)
)
app. route("/")
def calculate(val, num):
"""Calculates the monthly charge"""
try:
if val == "a":
if (int(num) < 10):
result = 9.95
else:
result = (int(num) - 10)*2 + 9.95
elif val == "b":
if (int(num) < 20):
result = 13.95
else:
result = (int(num) - 20) + 13.95
elif val == "c":
result = 19.95
return str(result)
except ValueError:
return "invalid input"
if __name__ == "__main__":
app. run(host="0.0.0.0", port=81, debug=True)
To learn more about Web application in python see: https://brainly.com/question/27993804
#SPJ4


In an answer of at least two well-developed paragraphs, explain how the government
is involved in the circular flow of money and the circular flow of products.
Answers
The government is also involved in the circular flow of products by creating policies and regulations that affect the production, distribution, and consumption of goods and services. For example, the government can set standards for the quality and safety of products, which affects the production and distribution processes. The government can also provide subsidies and tax incentives to promote the production and consumption of certain products. Additionally, the government can impose tariffs and trade barriers to protect domestic industries and regulate imports and exports, which affects the flow of products in the economy. Overall, the government's involvement in the circular flow of money and the circular flow of products is crucial in promoting economic stability, growth, and development.
Design a 4-to-16-line decoder with enable using five 2-to-4-line decoder.
Answers
a 4-to-16-line decoder with enable can be constructed by combining five 2-to-4-line decoders. This cascading arrangement allows for the decoding of binary inputs into a corresponding output signal, controlled by the enable line. The circuit diagram illustrates the configuration of this decoder setup.
A 4-to-16-line decoder with enable can be created using five 2-to-4-line decoders. A 2-to-4-line decoder is a combinational circuit that transforms a binary input into a signal on one of four output lines.
The output lines are active when the input line corresponds to the binary code that is equivalent to the output line number. The enable line of the 4-to-16-line decoder is used to control the output signal. When the enable line is high, the output signal is produced, and when it is low, the output signal is not produced.
A 4-to-16-line decoder can be created by taking five 2-to-4-line decoders and cascading them as shown below:
Begin by using four of the 2-to-4-line decoders to create an 8-to-16-line decoder. This is done by cascading the outputs of two 2-to-4-line decoders to create one of the four outputs of the 8-to-16-line decoder.Use the fifth 2-to-4-line decoder to decode the two most significant bits (MSBs) of the binary input to determine which of the four outputs of the 8-to-16-line decoder is active.Finally, use an AND gate to combine the output of the fifth 2-to-4-line decoder with the enable line to control the output signal.The circuit diagram of the 4-to-16-line decoder with enable using five 2-to-4-line decoders is shown below: Figure: 4-to-16-line decoder with enable using five 2-to-4-line decoders
Learn more about line decoder: brainly.com/question/29491706
#SPJ11
Network administration is concerned with which tasks?
the installation and maintenance of network hardware and software
the installation and maintenance of computer operating systems
the diagnosis and repair of some types of computer hardware
the monitoring of users’ activity on a social networking site
Answers
Network administration is concerned with option A: the installation and maintenance of network hardware and software.
What are the tasks of a network administrator?The Network Administrator's role is known to be one that makes sure that there is a stable operation of the computer networks.
Note that This is made up of planning, developing, installing, configuring, and others,
Network administration are known to be people that help to manage, monitor, maintain, a firms network.
Hence., Network administration is concerned with option A: the installation and maintenance of network hardware and software.
Learn more about Network administration from
https://brainly.com/question/5860806
#SPJ1
please help me with computing!
the question is:
solve the following algorithm in pseudocode "the algorithm is required to prepare a teacher's payroll. For them, the hours worked and the price per hour are taken into account. place the input data and the output data.
Answers
Answer:
ok i help
Explanation:
Some one help pls will mark brainless !!!!!
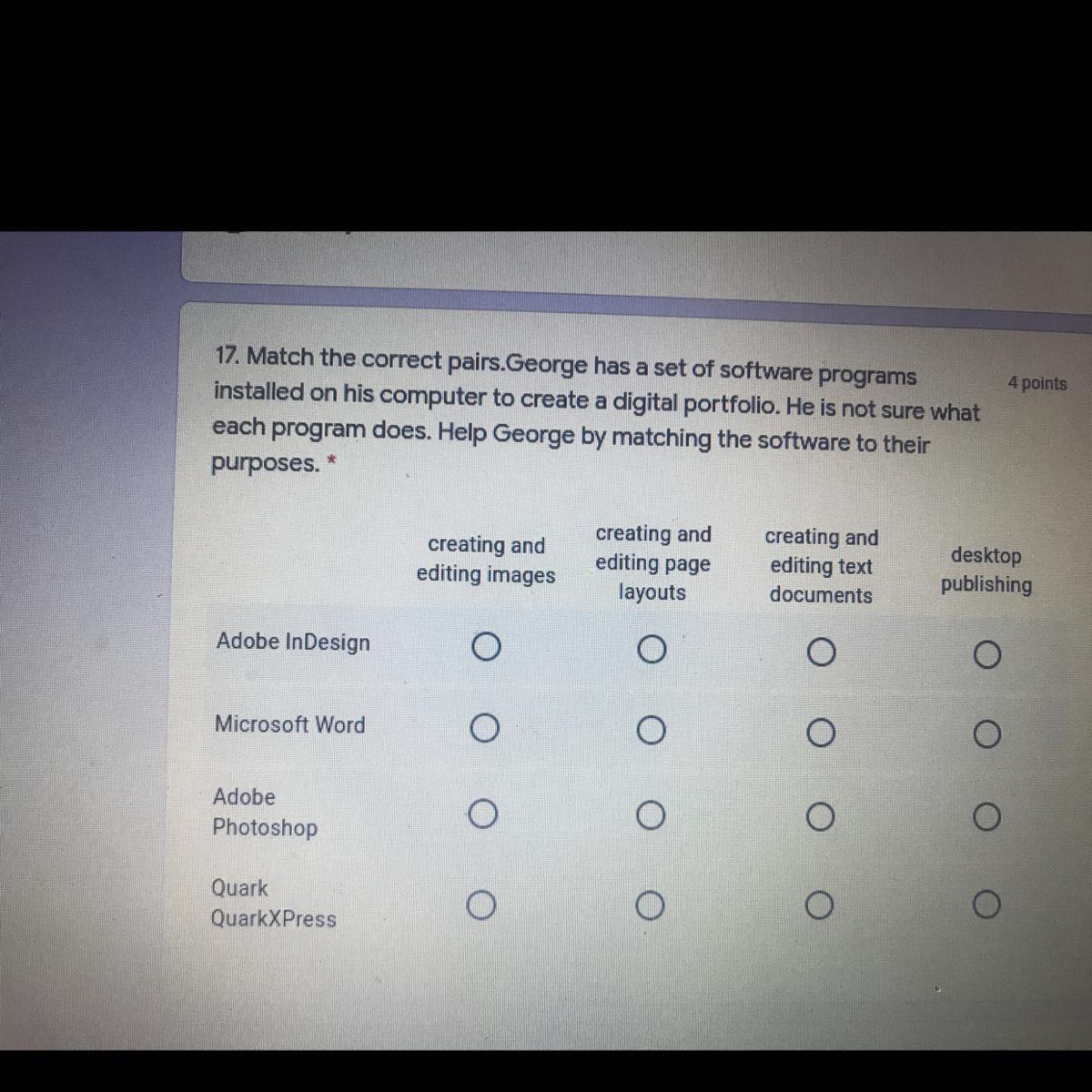
Answers
microsoft word- creating and editing word documents
adobe indesign- layouts
qaurk- publishing
!!!!!16 POINTS!!!!Can a computer evaluate an expression to something between true and false? Can you write an expression to deal with a "maybe" answer?
DO NOT JUST ASWERE FOR POINTS OR YPU WILL BE REPORTED AND BLOCKED. IF YOU HAVE ANY QUESTION PLEASE ASK THE IN THE COMMENTS AND DO NOT ASWERE UNLESS YOU KNOW THE ANSWER TO THE PROBLEM, thanks.
Answers
Answer:
Yes a computer can evaluate between a true or false. x < 1, and if the condition is met, the value is true, else its false. A computer itself cannot handle any "maybe" expression, but with the influence of human opinion, in theory its possible. Chocolate cake < Vanilla cake, is an example. Entirely on opinion.
antivirus programs are an example of which type of software
Answers
Antivirus programs are an example of security software.
Antivirus programs are a kind of software that aims to safeguard a computer against malware. This software is used to detect, prevent, and eliminate malware from a computer. Antivirus programs are used to protect computers from worms, viruses, Trojan horses, adware, spyware, and other malware. Antivirus programs are critical for maintaining a computer's security and privacy. They also safeguard data stored on a computer, preventing it from being compromised.
Antivirus programs are a critical type of security software that are used to protect computers from a wide range of malware. These programs can detect, prevent, and eliminate malware from a computer, making them an essential tool for maintaining a computer's security and privacy. With the help of antivirus programs, computers can be protected from a wide range of threats, which is critical for ensuring that data stored on the computer remains secure.
To know more about programs visit,
https://brainly.com/question/28224061
#SPJ11
combining strings. assign secretid with firstname, a space, and lastname. ex: if firstname is barry and lastname is allen, then output is: barry allen java
Answers
To combine strings in the given format of firstname, followed by a space, and then lastname, you can concatenate the strings and assign the result to secretid. For example, if firstname is "Barry" and lastname is "Allen," the output would be "Barry Allen."
To achieve the desired output format, you can use string concatenation in your programming language of choice. The specific implementation may vary depending on the programming language you are using, but the general approach remains the same.
Here's an example using Java:
String firstname = "Barry";
String lastname = "Allen";
String secretid = firstname + " " + lastname;
System.out.println(secretid);
In this Java example, we declare two string variables, firstname and lastname, with the respective values "Barry" and "Allen". Then, we concatenate the strings using the + operator, along with a space enclosed in double quotes, to separate the firstname and lastname. The result is assigned to the secretid variable. Finally, we print the secretid, which outputs "Barry Allen" as the combined string.
Learn more about Java here: https://brainly.com/question/12972062
#SPJ11
Suppose that a list of numbers contains values [-4, -1, 1, 5, 2, 10, 10, 15, 30]. Which of the following best explains why a binary search should NOT be used to search for an item in this list?
Answers
The binary search algorithm starts in the center of the sorted list and continuously removes half of the elements until the target data is known or all of the items are removed.
What is the exact number of elements?A list of 500 elements would be chopped in half up to 9 times (with a total of 10 elements examined). Suppose that a list of numbers contains values [-4, -1, 1, 5, 2, 10, 10, 15, 30].
The particular prerequisites with 500 items and are decreased to 250 elements, then 125 aspects, then 62 elements, 31 aspects, 15 aspects, 7 aspects, 3 aspects, and ultimately 1 element.
Therefore, The binary search algorithm starts in the center of the sorted list and continuously removes half of the elements until the target data is known or all of the items are removed.
Learn more about the binary search on:
brainly.com/question/20712586
#SPJ1
Text,Audio and graphic is entered into the computer using
a)A cpu
b)Output
C)Input
ICT Question asap pls help
Answers
Answer:
I think it's input, not sure tho
Computerized spreadsheets that consider in combination both the
risk that different situations will occur and the consequences if
they do are called _________________.
Answers
Both answers are correct
The given statement refers to computerized spreadsheets that consider in combination both the risk that different situations will occur and the consequences if they do which are called decision tables.
A decision table is a form of decision aid. It is a tool for portraying and evaluating decision logic. A decision table is a grid that contains one or more columns and two or more rows. In the table, each row specifies one rule, and each column represents a condition that is true or false. The advantage of using a decision table is that it simplifies the decision-making process. Decision tables can be used to analyze and manage complex business logic.
In conclusion, computerized spreadsheets that consider in combination both the risk that different situations will occur and the consequences if they do are called decision tables. Decision tables can help simplify the decision-making process and can be used to analyze and manage complex business logic.
To know more about spreadsheets visit:
https://brainly.com/question/31511720
#SPJ11
How long is a flight to Chicago to Orlando?
Answers
Answer:
2h 34m
The duration of a nonstop flight to Orlando Airport from Chicago is typically 2h 34m. The journey crosses a distance of 994 miles.
Explanation:
It takes 2 hours, 35 minutes to fly from Chicago to Orlando. 2 hours and 9 minutes are spent in the air. 1005 miles separate Chicago and Orlando in a direct trip.
By air, how far is it from Orlando to Chicago?It takes 2 hours, 53 minutes to fly from Orlando to Chicago. 2 hours and 24 minutes are spent in the air. From Orlando to Chicago, it takes a plane to go 1005 miles.
From Chicago to Orlando, how long is the drive?Including stops in Indianapolis, Louisville, Lexington, Nashville, Gatlinburg, Knoxville, Bryson City, Birmingham, Gainesville, Daytona Beach, Orlando, and the Great Smoky Mountains, the 1,320-mile drive from Chicago to Orlando will take a driver 22 hours.
To learn more about Chicago and Orlando here:
https://brainly.com/question/15000862
#SPJ4
Choose the term so achieve the output shown.
>>>import math
>>>math. ___ (36)
6.0
•Sqr
•Root
•sqrt
Answers
Answer:
sqrt
Explanation:
Answer:
sqrt
Explanation:
sqrt= square root
sqrt of 36 is 6
__________, a level beyond vulnerability testing, is a set of security tests and evaluations that simulate attacks by a malicious external source (hacker).
Answers
According to security evaluation, Penetration testing is a level beyond vulnerability testing, a set of security tests and evaluations that simulate attacks by a malicious external source (hacker).
Penetration testing is often considered or described as ethical hacking. It involves the process of securing a firm or organization's cyber defenses.
The process of penetration testing or security testing includes assessing for exploitable vulnerabilities in networks, web apps, and user security.
Hence, in this case, it is concluded that the correct answer is Penetration testing.
Learn more about penetration testing here: https://brainly.com/question/13137421
Which of the following best describes tactical-level decisions?
A) decisions undertaken at the highest level by the leaders of an organization
B) programmed decisions that involve routine transactions and deal directly with customers
C) decisions that impact the entire organization and sometimes, even the industry
D) mid-level decisions undertaken by managers on issues like product development and membership drives
Answers
Option D correctly describes tactical-level decisions as mid-level decisions undertaken by managers
Tactical-level decisions refer to the decisions made by mid-level managers within an organization. These decisions are focused on the implementation of strategies and plans developed by top-level executives. They involve operational details and are concerned with achieving specific objectives or targets.
Option D correctly describes tactical-level decisions as mid-level decisions undertaken by managers. These decisions are typically related to day-to-day operations, such as product development, marketing campaigns, resource allocation, and membership drives. They involve translating the broader strategic goals into actionable steps and ensuring that the organization's resources and activities are aligned towards achieving those goals.
Learn more about aligned here:
https://brainly.com/question/14396315
#SPJ11
Your consulting job at Driverless Cars is going very well! You're earning $1,000/day based on your extensive knowledge of Agile methods and how well you've been able to help the company understand how to optimize those methods for the automatic parking application. Your next task is to help the developers and management at Driverless Cars understand how to use Scrum for this application.
For this assignment, you will have the following deliverables:
-Provide an overall description of the Scrum process and roles.
-Explain the planning process for Sprint 1. Who is involved? What are the work products? What are the roles and deliverables of each participant? Who delivers what and when?
-Describe what happens, day to day, during Sprint 1. Who is involved? What are the work products?
-Describe what happens at the end of Sprint 1. Who is involved? What are the work products?
-How does the team measure progress?
-How and when can the team adjust priorities? Who sets the priorities? When can changes be made?
Answers
Overall Description of the Scrum Process and Roles:
Scrum is an Agile framework used for managing complex projects, particularly software development. It emphasizes iterative and incremental development, flexibility, and collaboration within self-organizing teams. The Scrum process involves several key roles, including the Product Owner, Scrum Master, and Development Team.
The Product Owner:
Represents the stakeholders and is responsible for maximizing the value of the product.
Defines the product vision, creates and prioritizes the product backlog, and ensures alignment with customer needs.
Works closely with the Development Team to clarify requirements and make decisions.
The Scrum Master:
Facilitates the Scrum process and ensures that the team follows Scrum principles.
Helps remove any obstacles or impediments that may hinder the team's progress.
Guides the team in self-organization and continuous improvement.
The Development Team:
Consists of professionals who perform the work of delivering a potentially releasable product increment.
Collaboratively estimates and selects items from the product backlog for each sprint.
Responsible for designing, developing, and testing the product increment.
Planning Process for Sprint 1:
The Product Owner works with stakeholders to define the goals and objectives for Sprint 1.
The Development Team estimates and selects the product backlog items they believe they can deliver within the sprint.
The Scrum Master facilitates the planning meeting, where the team discusses and breaks down the selected items into actionable tasks.
Day-to-Day Activities during Sprint 1:
The Development Team conducts daily stand-up meetings to discuss progress, plans for the day, and any obstacles.
They work collaboratively on the identified tasks, developing and testing the product increment.
The Scrum Master ensures that the team is following the Scrum process and helps address any issues that arise.
End of Sprint 1:
The Development Team presents the completed product increment during the sprint review.
The Product Owner provides feedback and accepts or rejects the work based on whether it meets the defined criteria.
The team reflects on their performance and identifies areas for improvement during the sprint retrospective.
Measuring Progress:
The team measures progress based on the completion of product backlog items and the delivery of a potentially releasable product increment at the end of each sprint.
Key metrics such as velocity (the amount of work completed in each sprint) and burn-down charts (tracking remaining work) are used to assess progress.
Adjusting Priorities:
Priorities can be adjusted at the beginning of each sprint during the sprint planning meeting.
The Product Owner, in collaboration with stakeholders, determines the priorities based on changing requirements, market conditions, and customer feedback.
Learn more about software here
https://brainly.com/question/32393976
#SPJ11
PLSSS HELP!!!! 30 POINTS!!
You are running your program. What happens when your program is compiled?
When your program is compiled, Python converts your program into-----
A. binary only
B. Bytecode only
C. bytecode and then binary
Answers
Answer: The original program file, as well as the preprocessor and the output of the compiler, are all text files. When you try to start a program, the operating system generates a new process (complete resource), load the image executable in memory and then run the process.
Explanation: B
When the program is compiled, Python converts the program into Bytecode only. Hence, Option B is correct.
What is Python?Python is a programming language that is concerned with computers. It is a high-level programming language or it is used for general purposes. Also, Python is designed according to a philosophy that emphasizes readability and significance.
Python is a high-level programming language with dynamically typed types and garbage collection support. One of the benefits of using Python is that it supports multiple programming languages.
Guido van Rossum designed it, and it first appeared in 1991. At the time of programme compilation, with the help of Python, it becomes easy to convert the programmed into bytecode.
Therefore, Option B is correct.
Learn more about Python from here:
https://brainly.com/question/13437928
#SPJ2
Mail merge is a feature in ms word to make ______ documents from a single template.
Answers
Mail merge is a feature in MS Word to make multiple documents from a single template.
What is Mail Merge?
Mail merge is a feature in MS Word that enables the creation of personalized letters, envelopes, labels, or emails in bulk, which are all based on a single template document. To personalize each item in the group, the mail merge feature pulls information from a data source like an Excel spreadsheet or an Access database.
Mail Merge Feature
Mail Merge is a beneficial feature of MS Word that allows users to produce many of the same documents. It's commonly used for creating letters, labels, and envelopes. Mail merge lets users use a single template and a list of data entries to generate the necessary number of identical documents. The process helps users save time and eliminates the possibility of typing the same content again and again.
Single Template
Single Template is a document that contains the formatting and other features of the desired end product. The document is designed in such a way that, when merged with the list of data entries, it produces the required number of identical documents. A template makes things easy by keeping the formatting consistent and allowing for easy data entry. In a nutshell, we can say that single template refers to a master document that needs to be merged with the data source to create identical copies of the document.
Learn more about Mail merge at https://brainly.com/question/14923358
#SPJ11
The box on a slide that has a dotted or hatch-marked border and that contains the insertion point is a text ____.
Answers
it is known as a text placeholder
Combining a desktop's power with a clean look, ________ computers are popular with companies. However, their inability to expand makes them less popular with serious gamers.
Answers
It should be noted that combining a desktop's power with a clean look, all in one computers are popular with companies.
When a computer has a good desktop's power it will be easier to operate fast and deliver output at fast rate.
What is a computer desktop's power?This is the the power that makes the computer to be excellent in performing the required task for better operation.
Learn more about computer at;
https://brainly.com/question/9759640
1...difference between repeater and hub .
2... difference between bridge and router .
Answers
Answer:
Explanation:I don't say you have to mark my ans as brainliest but if you think it has really helped you plz don't forget to thank me..


1. A repeater amplifies and extends signals, while a hub is a multi-port device that broadcasts data to all connected devices, creating a shared collision domain.
2. A bridge connects network segments at the data link layer and forwards packets based on MAC addresses, while a router connects networks at the network layer and forwards packets based on IP addresses.
1. Difference between a Repeater and a Hub:
Repeater:
Operates at the physical layer (Layer 1) of the network.
Regenerates and amplifies network signals to extend their reach and overcome signal degradation.
Does not inspect or manage network traffic.
All devices connected to a repeater share the same collision domain.
Transparent to network protocols and does not interpret data.
Hub:
Operates at the physical layer (Layer 1) of the network.
Multi-port device that broadcasts incoming data to all connected devices.
Creates a single collision domain, causing devices to contend for network bandwidth.
Lacks intelligent traffic management and filtering capabilities.
Limited in terms of network performance and scalability due to shared bandwidth
2. Difference between a Bridge and a Router:
Bridge:
Operates at the data link layer (Layer 2) of the network.
Connects and joins separate network segments or LANs to form a single logical network.
Forwards data packets based on MAC addresses.
Builds and maintains a table (MAC table) of MAC addresses and associated network interfaces.
Bridges are commonly used to reduce network congestion and improve performance within smaller networks.
Does not perform IP address-based routing.
Router:
Operates at the network layer (Layer 3) of the network.
Connects multiple networks and routes data packets between them based on IP addresses.
Determines the best path for packet delivery using routing tables and protocols (e.g., RIP, OSPF, BGP).
Performs network address translation (NAT) and offers features like firewall and network traffic management.
Enables communication between networks with different IP address schemes.
To learn more on Bridge and Router click here:
https://brainly.com/question/13486343
#SPJ4
What is constructive criticism?
Advice and possible solutions intended to help or improve something
Information given to others as a way to make them feel unintelligent
Reports about decreasing profits
Statements and no possible solutions aimed at showing problem areas
Answers
Answer:
Constructive cristsism is a helpful way of giving feedback that provides specific, actionable suggestions. Or, its a nice way of criticizing someone and telling them what to do better
Answer:
Advice and possible solutions intended to help or improve something
Explanation:
I took the test and Got it Correct!
escribe un texto argumentativo donde expreses tu opinión acerca del acoso cibernético
Answers
El acoso cibernético es uno de los problemas menos tratados por la sociedad y a la vez uno muy recurrente. Este tipo de acoso rastrea a la persona a través de redes sociales y la investiga con fines degradantes para el afectado, sin embargo, para prevenir este se deben tomar medidas de seguridad como no compartir toda tu vida en el internet y así evitar estos casos que generalmente terminan con abuso sexual o secuestro.
what kind of table compares classification predicted by models with the actual class labelwhat kind of table compares classification predicted by models with the actual class label
Answers
The table that compares classification predicted by models with the actual class label is known as a confusion matrix.
This matrix helps to evaluate the accuracy of a model by showing the number of true positives, false positives, true negatives, and false negatives. A true positive is when the model correctly predicts a positive result, a false positive is when the model incorrectly predicts a positive result, a true negative is when the model correctly predicts a negative result, and a false negative is when the model incorrectly predicts a negative result. The confusion matrix provides valuable information about the performance of a model and helps to identify any areas where the model may need improvement. It is a commonly used tool in machine learning and data analysis.
learn more about confusion matrix here:
https://brainly.com/question/30764998
#SPJ11
the person who receives an e-mail
Answers
6. A small design agency you are consulting for will be creating client websites and wants to purchase a web server so they can host the sites themselves. How will you advise them on this purchase?
Answers
Answer:
Explanation:
The best way to advise the agency in this matter would be to help them completely understand the total cost of ownership of the server. This includes the server itself but many other factors as well. Such as any and all server software and application software that they will need, an IT server manager, facility costs, security costs, backup features. These are some of the main costs that they will be incurring but there may be more unforeseen costs. Therefore the best way to advise them is by providing all of this information so that they can make the most informed decision possible.
What can you add to your presentation from the Insert tab?
Animations
Pictures
Variants
Transitions
Answers
Answer:
B. PICTURES
Explanation:
Answer:
I know its late but pictures is the answer.
Explanation:
I took the test and got it right.
PLATO ANSWERS PLS!!
Type the correct answer in the box. Spell all words correctly.
What should the timing of transition slides be per minute?
Maintain the flow of the presentation to
Reset
slides per minute.
Answers
The timing of transition slides per minute can vary depending on the content and pace of the presentation.
What is transition slide?A slide transition is the visual effect that happens as you switch from one slide to the next during a presentation. The pace, sound, and appearance of transition effects can all be adjusted.
Depending on the presentation's content and pacing, the number of transition slides every minute may change.
It is advised to keep the presentation's pace at roughly 1-2 minutes each slide as a general rule.
As a result, if your presentation lasts for 10 minutes, you should aim for 5–10 slides.
But, it's crucial to put the presentation's flow first and to refrain from speeding or dragging out slides in order to stick to a strict time limit. The timing of transition slides should ultimately be changed to better serve the presentation's content and purpose.
Thus, this is the timing of transition slides be per minute.
For more details regarding transition slide, visit:
https://brainly.com/question/19217934
#SPJ9
a quickbooks online user wants credit memos to automatically apply to open invoices. where must the automatically apply credits setting be turned on?
Answers
Automatically apply credits setting must be turned on from the company settings to allow QuickBooks Online users to apply credit memos to open invoices automatically.
Quick Books Online users can turn on the automatically apply credits setting to ensure credit memos are applied automatically to open invoices. This feature is available in the company settings. To turn on this feature, QuickBooks Online users can navigate to the company settings, click on the "Advanced" option, and then select the "Automation" option. From there, they can turn on the "Automatically apply credits" option. Once this feature is turned on, QuickBooks Online users will no longer need to apply credit memos manually. Instead, QuickBooks Online will automatically apply any available credit memos to open invoices. This can help save time and ensure accuracy when managing invoices and credit memos.
Contracts can be used to make invoices. Eligible transactions that are billed to the projects and tasks associated with each contract line are processed. When you either submit the process to generate invoices or manually create an invoice for a contract, the amounts of those invoices are calculated.
Know more about invoices automatically, here:
https://brainly.com/question/32570394
#SPJ11